Fake cryptocurrency trading applications from Google Play were stolen by data
Users of the popular cryptocurrency exchange Poloniex have become the target of a new fraudulent campaign on Google Play. Under the guise of legitimate software exchanges in the store distributed two applications for data theft. Fakes allow you to intercept logins and passwords from your Poloniex account, as well as from your Gmail account.

Poloniex is one of the leading exchanges with the ability to trade more than 100 cryptocurrencies. The popularity of the site attracts all sorts of scams. In this incident, the attackers took advantage of the lack of an official mobile app exchange.
')
Against the background of the HYIP around cryptocurrencies, fraudsters are testing different methods - from the hidden use of the computing power of user machines to mine cryptocurrencies in the browser and infection of unpatched devices to phishing schemes.
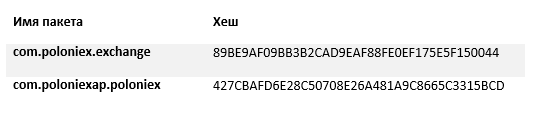
The first malicious application has penetrated into Google Play called Poloniex from the developer Poloniex. From August 28 to September 19, it was installed by up to 5,000 users, despite conflicting assessments and negative reviews.
The second POLONIEX EXCHANGE app from POLONIEX COMPANY appeared on Google Play on October 15 and has been installed 500 times. After an ESET warning, the forgery was removed from the store.
In addition to Google, we reported on scammers at Poloniex.

Figure 1. Fake apps on Google Play
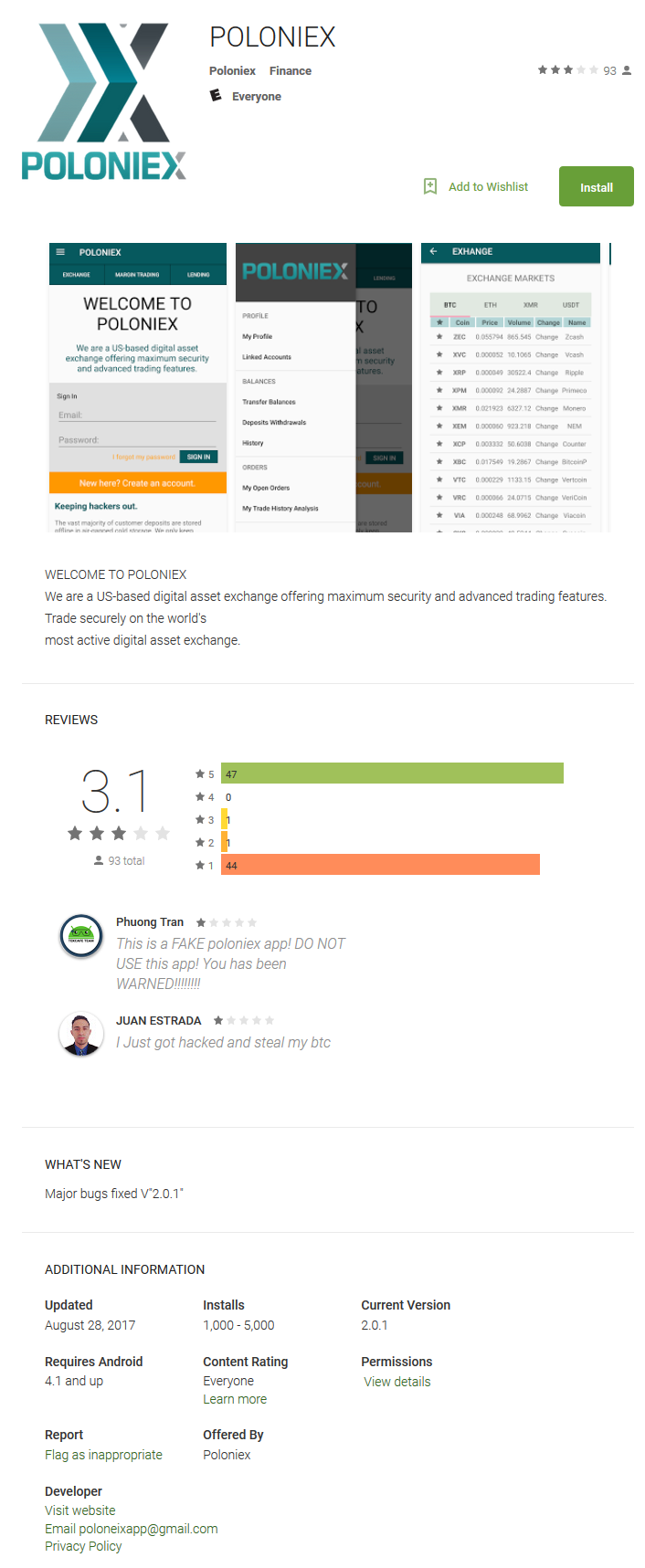
Figure 2. Feedback on one of the applications.
To successfully capture an account on the Poloniex exchange with a malicious application, attackers first need to get credentials. Next - access to the mail account associated with the compromised account on the stock exchange to manage notifications about logins and transactions. Finally, the attacker needs to make sure that the fake application looks convincing and does not arouse suspicion.
Both applications use the same methods to solve these problems.
Theft of credentials is made immediately after launching the application. The screen displays a fake Poloniex credential entry form (Figure 3). If the user enters a username and password and presses the Sign In button, the data will be sent to the attackers.
If the user does not use two-factor authentication in Poloniex, attackers gain access to the account. They will be able to carry out transactions on their own, change settings and prohibit user access to the account by changing the password.
If the user still uses two-factor authentication, his account is protected from hacking. Poloniex provides 2FA through Google Authenticator. Random passwords to log in to your account are sent via text messages, voice or Google Authenticator application, to which the attackers do not have access.
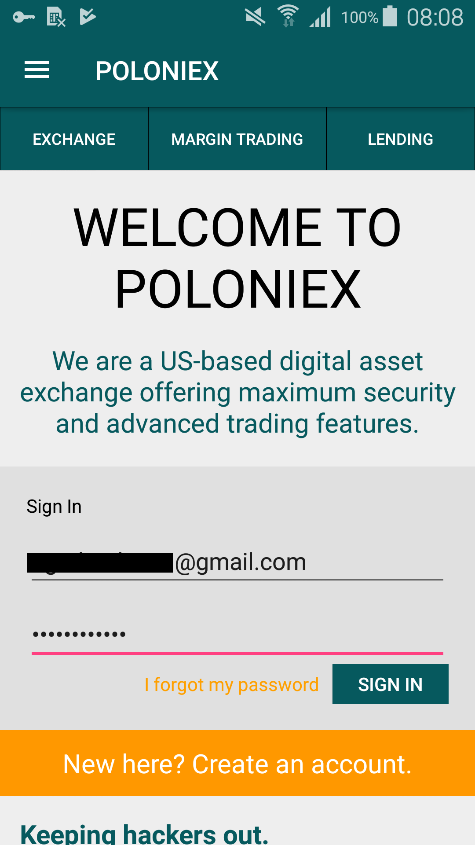
Figure 3. Fake entry form to steal Poloniex credentials
Having intercepted the username and password from Poloniex, the attackers are trying to gain access to their Gmail account. The user sees activity, at first glance, from Google, during which they are required to log in to their Gmail account for a “two-step security check” (Figure 4). When a user clicks on the login button, the malicious application will request permission to view email messages, settings, and basic profile information (Figure 5). If the user gives these permissions, the application gets access to incoming emails.
By accessing the Poloniex account and the linked Gmail account, attackers can conduct transactions on behalf of users and remove any notifications about unauthorized logging and transactions from incoming emails.
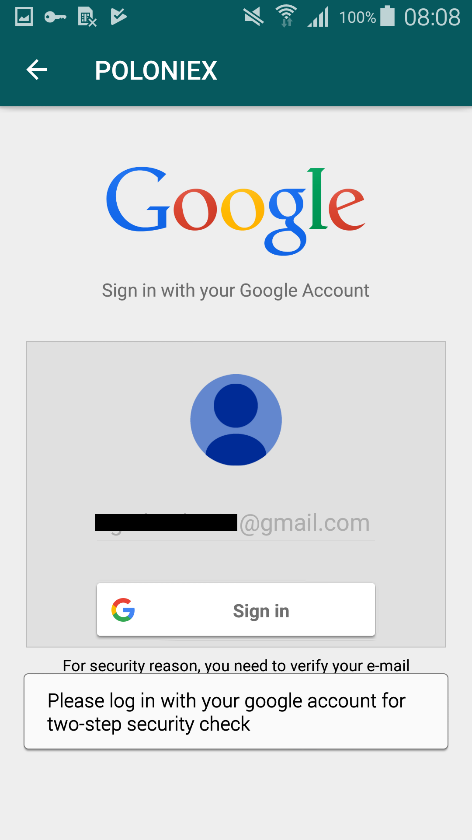
Figure 4. Gmail account login request
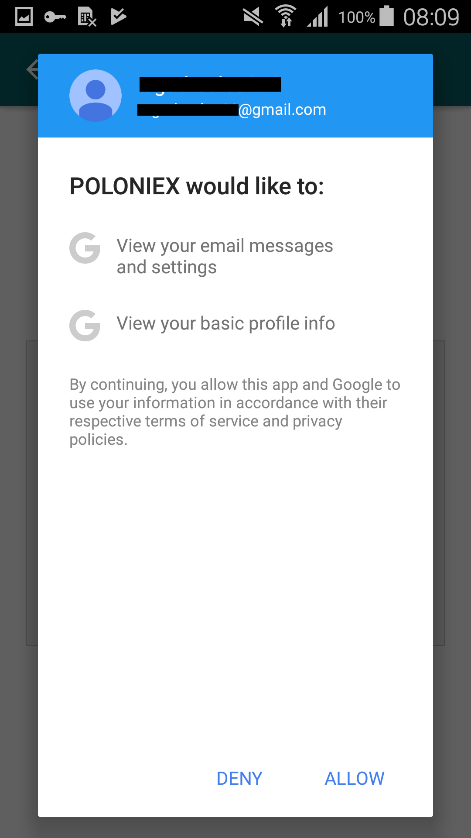
Figure 5. Malicious application requesting access to mail
Finally, to ensure the visibility of normal operation, the application redirects the user to the mobile version of the legitimate Poloniex site. The site requires the user to log in (Figure 6). After logging in, the user can start working with the Poloniex exchange. The application will open a legitimate site every time it starts.

Figure 6. Mobile version of the legitimate Poloniex site opened by a malicious application.
If you are a Poloniex user and have installed the above applications, delete them. Be sure to change the passwords to your Poloniex and Gmail accounts, if possible enable two-factor authentication.
Just in case, here are the classic recommendations for the prevention of infection:
ESET anti-virus products detect fake applications like Android / FakeApp.GV.

Poloniex is one of the leading exchanges with the ability to trade more than 100 cryptocurrencies. The popularity of the site attracts all sorts of scams. In this incident, the attackers took advantage of the lack of an official mobile app exchange.
')
Against the background of the HYIP around cryptocurrencies, fraudsters are testing different methods - from the hidden use of the computing power of user machines to mine cryptocurrencies in the browser and infection of unpatched devices to phishing schemes.
Malicious applications
The first malicious application has penetrated into Google Play called Poloniex from the developer Poloniex. From August 28 to September 19, it was installed by up to 5,000 users, despite conflicting assessments and negative reviews.
The second POLONIEX EXCHANGE app from POLONIEX COMPANY appeared on Google Play on October 15 and has been installed 500 times. After an ESET warning, the forgery was removed from the store.
In addition to Google, we reported on scammers at Poloniex.

Figure 1. Fake apps on Google Play

Figure 2. Feedback on one of the applications.
Work principles
To successfully capture an account on the Poloniex exchange with a malicious application, attackers first need to get credentials. Next - access to the mail account associated with the compromised account on the stock exchange to manage notifications about logins and transactions. Finally, the attacker needs to make sure that the fake application looks convincing and does not arouse suspicion.
Both applications use the same methods to solve these problems.
Theft of credentials is made immediately after launching the application. The screen displays a fake Poloniex credential entry form (Figure 3). If the user enters a username and password and presses the Sign In button, the data will be sent to the attackers.
If the user does not use two-factor authentication in Poloniex, attackers gain access to the account. They will be able to carry out transactions on their own, change settings and prohibit user access to the account by changing the password.
If the user still uses two-factor authentication, his account is protected from hacking. Poloniex provides 2FA through Google Authenticator. Random passwords to log in to your account are sent via text messages, voice or Google Authenticator application, to which the attackers do not have access.

Figure 3. Fake entry form to steal Poloniex credentials
Having intercepted the username and password from Poloniex, the attackers are trying to gain access to their Gmail account. The user sees activity, at first glance, from Google, during which they are required to log in to their Gmail account for a “two-step security check” (Figure 4). When a user clicks on the login button, the malicious application will request permission to view email messages, settings, and basic profile information (Figure 5). If the user gives these permissions, the application gets access to incoming emails.
By accessing the Poloniex account and the linked Gmail account, attackers can conduct transactions on behalf of users and remove any notifications about unauthorized logging and transactions from incoming emails.

Figure 4. Gmail account login request

Figure 5. Malicious application requesting access to mail
Finally, to ensure the visibility of normal operation, the application redirects the user to the mobile version of the legitimate Poloniex site. The site requires the user to log in (Figure 6). After logging in, the user can start working with the Poloniex exchange. The application will open a legitimate site every time it starts.

Figure 6. Mobile version of the legitimate Poloniex site opened by a malicious application.
How to protect yourself?
If you are a Poloniex user and have installed the above applications, delete them. Be sure to change the passwords to your Poloniex and Gmail accounts, if possible enable two-factor authentication.
Just in case, here are the classic recommendations for the prevention of infection:
- make sure that the service really has its own mobile application (referring to it from the official site)
- check application ratings and user reviews
- Pay attention to the notifications and windows associated with Google, which appear when working with third-party applications (fraudsters often enjoy the trust of users to the “corporation of good”)
- use two-factor authentication as an additional (and often key) level of security
- use reliable mobile security solution
ESET anti-virus products detect fake applications like Android / FakeApp.GV.
Indicators of compromise

Source: https://habr.com/ru/post/340782/
All Articles