OSX / Proton backdoor distributed with Trojanized Elmedia Player
On October 19, our specialists noticed that Eltima , the developer of the popular free Elmedia Player, distributes an OSX / Proton- infected version of the application from the official website. We contacted Eltima as soon as the problem was confirmed, and the company employees remained in touch throughout the incident.

We publish a post, despite the fact that the study is not completed. Information is preliminary and may be updated as new data becomes available.
')
October 19: Trojansized package confirmed
03:35 (MSK): sent a message to Eltima
07:25 (MSK): Eltima has started troubleshooting
08:10 (MSK): Eltima confirmed that the infrastructure has been cleared and distribution of legitimate applications has been resumed
The 20th of October
14:12 (MSK): a message has been posted on the Eltima website about the elimination of trojanized versions of Elmedia Player and Folx
ESET advises anyone who has recently downloaded Elmedia Player software to check the system for compromise. An infection is indicated by the presence of any of the listed files or directories:
The presence of at least one file or directory means that the Elmedia Player application has been executed in the system and, with a high degree of probability, OSX / Proton is already running.
If you downloaded Elmedia Player on October 19 before 08:15 (MSK) and started it, your system is compromised.
According to our information, only the player version downloaded from the official Eltima website was compromised. The built-in automatic update mechanism was probably not affected.
OSX / Proton - backdoor with extensive data theft. It may collect the following data:
As in any incident with a compromised administrator account, the only reliable way to get rid of malware is to completely reinstall the operating system. It is necessary to take into account that the data listed in the previous section are likely to be compromised.
In 2016, Transmission, a Bittorrent client for Mac, was used twice to distribute malware. The OSX / KeRanger encryption featured in the first incident, and the OSX / Keydnap password theft tool in the second. This year the Handbrake application for coding video on Mac was infected with OSX / Proton .
Now we have found that another popular Mac software, Elmedia Player, is used to distribute OSX / Proton, which, by the way, has reached 1 million users this summer.

Source: twitter.com/Elmedia_Player/status/895995031802261504
OSX / Proton - Remote Access Trojan (RAT) Trojan sold on underground forums. He was briefly described by Sixgill at the beginning of this year, then it was examined by Thomas Reed from MalwareBytes, Amit Serper from CyberReason and Patrick Wardle from Objective-See.
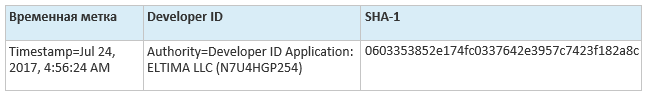
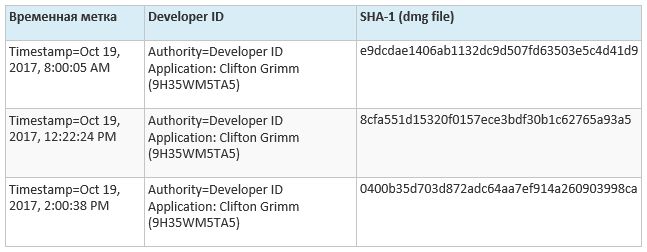
In our case, the attacker created a signed shell around the legitimate Elmedia Player and Proton. In fact, we observed that shells were repackaged and re-signed in real time, all with the same valid Apple Developer ID. (Certificate withdrawn by Apple.)
Clean application
(time stamps - EDT, EST)
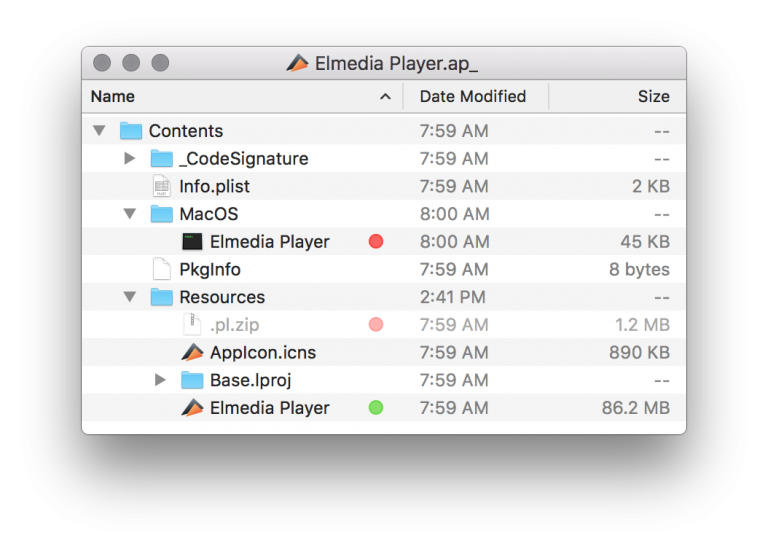
Triple Application
First, the shell launches the real Elmedia Player, stored in the application’s Resources folder:
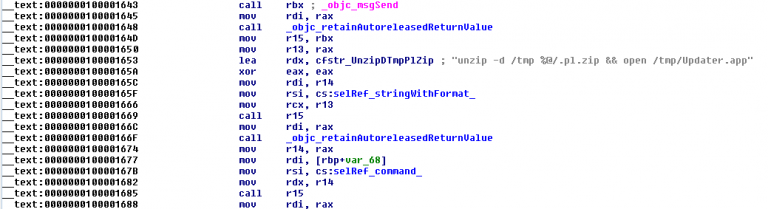
Next, extracts and launches OSX / Proton:
As you can see from the previous cases, OSX / Proton shows a fake login window for admin rights:

OSX / Proton provides persistence by adding LaunchAgent to all users when an administrator enters their password. It creates the following files on the system:
As already mentioned, OSX / Proton is a backdoor with a wide range of data theft functions. The backdoor components studied can execute the following commands:
Proton uses the domain of the management server that mimics the Eltima legitimate domain - the same principle as in the Handbrake case:
The URL that distributes the trojan application at the time of detection:
eltima [.] in / 5.196.42.123 (domain registered October 15, 2017)


We publish a post, despite the fact that the study is not completed. Information is preliminary and may be updated as new data becomes available.
')
Chronology:
October 19: Trojansized package confirmed
03:35 (MSK): sent a message to Eltima
07:25 (MSK): Eltima has started troubleshooting
08:10 (MSK): Eltima confirmed that the infrastructure has been cleared and distribution of legitimate applications has been resumed
The 20th of October
14:12 (MSK): a message has been posted on the Eltima website about the elimination of trojanized versions of Elmedia Player and Folx
Is my computer infected?
ESET advises anyone who has recently downloaded Elmedia Player software to check the system for compromise. An infection is indicated by the presence of any of the listed files or directories:
/tmp/Updater.app/ /Library/LaunchAgents/com.Eltima.UpdaterAgent.plist /Library/.rand/ /Library/.rand/updateragent.app//tmp/Updater.app/ /Library/LaunchAgents/com.Eltima.UpdaterAgent.plist /Library/.rand/ /Library/.rand/updateragent.app//tmp/Updater.app/ /Library/LaunchAgents/com.Eltima.UpdaterAgent.plist /Library/.rand/ /Library/.rand/updateragent.app//tmp/Updater.app/ /Library/LaunchAgents/com.Eltima.UpdaterAgent.plist /Library/.rand/ /Library/.rand/updateragent.app/
The presence of at least one file or directory means that the Elmedia Player application has been executed in the system and, with a high degree of probability, OSX / Proton is already running.
If you downloaded Elmedia Player on October 19 before 08:15 (MSK) and started it, your system is compromised.
According to our information, only the player version downloaded from the official Eltima website was compromised. The built-in automatic update mechanism was probably not affected.
OSX / Proton Functions
OSX / Proton - backdoor with extensive data theft. It may collect the following data:
- Operating system information: equipment serial number (IOPlatformSerialNumber), current user's full name, node name, System Integrity Protection
csrutil status(csrutil status), gateway information (route -n get default | awk '/gateway/ { print $2 }') , current time and time zone - Information from browsers Chrome, Safari, Opera and Firefox: history, cookies, bookmarks, logins and passwords, etc.
- Cryptocurrency wallets: Electrum: ~ / .electrum / wallets; Bitcoin Core: ~ / Library / Application Support / Bitcoin / wallet.dat; Armory: ~ / Library / Application Support / Armory
- SSH confidential data (all .ssh content)
- MacOS keychain data using a modified chainbreaker version
- Tunnelblick VPN Configuration (~ / Library / Application Support / Tunnelblick / Configurations)
- GnuPG data (~ / .gnupg)
- Data 1Password (~ / Library / Application Support / 1Password 4 and ~ / Library / Application Support / 1Password 3.9)
- List of installed applications
How to clean the system?
As in any incident with a compromised administrator account, the only reliable way to get rid of malware is to completely reinstall the operating system. It is necessary to take into account that the data listed in the previous section are likely to be compromised.
Supply-chain attack on Mac
In 2016, Transmission, a Bittorrent client for Mac, was used twice to distribute malware. The OSX / KeRanger encryption featured in the first incident, and the OSX / Keydnap password theft tool in the second. This year the Handbrake application for coding video on Mac was infected with OSX / Proton .
Now we have found that another popular Mac software, Elmedia Player, is used to distribute OSX / Proton, which, by the way, has reached 1 million users this summer.

Source: twitter.com/Elmedia_Player/status/895995031802261504
Technical analysis
OSX / Proton - Remote Access Trojan (RAT) Trojan sold on underground forums. He was briefly described by Sixgill at the beginning of this year, then it was examined by Thomas Reed from MalwareBytes, Amit Serper from CyberReason and Patrick Wardle from Objective-See.
In our case, the attacker created a signed shell around the legitimate Elmedia Player and Proton. In fact, we observed that shells were repackaged and re-signed in real time, all with the same valid Apple Developer ID. (Certificate withdrawn by Apple.)
Clean application
(time stamps - EDT, EST)

Triple Application

First, the shell launches the real Elmedia Player, stored in the application’s Resources folder:

Next, extracts and launches OSX / Proton:

As you can see from the previous cases, OSX / Proton shows a fake login window for admin rights:

Persistence
OSX / Proton provides persistence by adding LaunchAgent to all users when an administrator enters their password. It creates the following files on the system:
- /Library/LaunchAgents/com.Eltima.UpdaterAgent.plist
- /Library/.rand/updateragent.app
$ plutil -p /Library/LaunchAgents/com.Eltima.UpdaterAgent.plist
{
"ProgramArguments" => [
0 => "/Library/.rand/updateragent.app/Contents/MacOS/updateragent"
]
"KeepAlive" => 1
"RunAtLoad" => 1
"Label" => "com.Eltima.UpdaterAgent"
}Backdoor Commands
As already mentioned, OSX / Proton is a backdoor with a wide range of data theft functions. The backdoor components studied can execute the following commands:
- archive - archive files in zip
- copy - copy file locally
- create - locally create a directory or file
- delete - locally delete the file
- download - download file from URL
- file_search - search for files (executes find / -iname \ "% @ \" 2> / dev / null)
- force_update - self-update with digital signature verification
- phonehome
- remote_execute - execute a binary file inside a zip-archive or a given shell command
- tunnel — create an SSH tunnel through port 22 or 5900
- upload - upload a file to the C & C server
C & C server
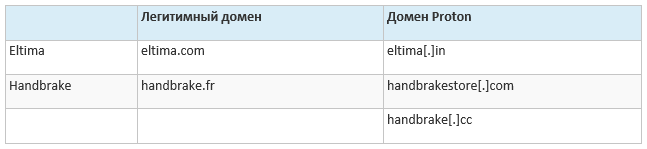
Proton uses the domain of the management server that mimics the Eltima legitimate domain - the same principle as in the Handbrake case:

Indicators of compromise
The URL that distributes the trojan application at the time of detection:
- hxxps: // mac [.] eltima [.] com / download / elmediaplayer.dmg
- hxxp: //www.elmedia-video-player.com/download/elmediaplayer.dmg
C & C Servers:
eltima [.] in / 5.196.42.123 (domain registered October 15, 2017)
Hashes

Source: https://habr.com/ru/post/340616/
All Articles