Why IT and Business Network Factory and Cisco SD-Access
The article analyzes the typical difficulties facing the corporate IT service today, and suggests a modern approach to their solution based on the Cisco Software-Defined Access network factory (SD-Access).
It discusses the key components and technologies underlying the Cisco SD-Access, as well as the principles of their work.
On the example of specific typical scenarios, the advantages offered to IT and business by the SD-Access factory are analyzed in detail.
Corporate IT service is "between the hammer and the anvil."
')
On the one hand, the business requires high availability of the network and expects that the network should always work - 24x7, with no exceptions! It is obvious. In IT, it is difficult to find something that worries a business more than the inaccessibility of business processes . But with the development of digital technology, the dependence of business processes on the network is only growing.
On the other hand, users (and in fact, the same business) require the support of new services, new types of devices, new types of users (including guests, partners), etc. They all need to ensure proper support from the network, and quickly. In addition, it is necessary to take into account the requirements of the information security service.
But the requirements of introducing new services and ensuring high availability, as a rule, contradict each other. After all, high availability implies first of all network stability, which is known as from specialized literature (for example, Piedad, Floyd, and Michael Hawkins. High availability: design, techniques, and processes. Upper Saddle River, NJ: Prentice Hall PTR, 2001. Print), and from general principles, for example, KISS (Keep it Simple Stupid), “it works — don't touch it”, etc.
And the introduction of new network services, by definition, violates its stability, since it introduces something new into the network and requires changes. These changes are often complex and extensive - for example, the introduction of solutions for collaborative multimedia work and QoS mechanisms, security technologies and segmentation. Even solving “transport” problems can be difficult, such as ensuring connectivity at Layer 2 between points A and B in different parts of the campus network.
As a result, the introduction of services complicates the network and requires a lot of time, and sometimes not at all.
There is another side to the contradiction between ensuring high availability and solving everyday business problems. Business tasks usually require from the network not just the transfer of packets from point A to point B, but the implementation of various kinds of policies. Policies are translated into specific requirements, for example, how to ensure security, how to route traffic from different applications, how to handle it, and so on. Any nontrivial policy increases the complexity of the implementation and operation of the network.
In addition, policies are not enough to implement. It is also necessary to keep them up to date, to make changes to them. Such changes in the scale of the corporate network, especially manual ones, are usually resource-intensive, long-lasting and highly vulnerable to errors. As a result, network availability again tends to decrease, and operating costs increase.
Thus, in a typical, “classic” corporate network
These challenges IT services face everywhere. But business is not interested in the difficulties of IT. Business is interested in business processes to work reliably, and implemented - quickly.
How to solve these conflicting challenges facing IT? A well-proven method for solving complex problems is to break one task into several simpler ones, and then solve them. The well-known examples are the seven-level OSI model or the four-level DoD model in solving the problem of network interaction.

Fig. 1. The concept of a network factory (overlay)
In our case, the concept of a network factory, or overlay, comes to the rescue (see Figure 1). An overlay is a logical topology built on top of some underlying topology (underlay) of the core network. Overlay uses any type of traffic encapsulation for transmission over the core network. The concept of overlay is well known to network administrators. Laying any tunnel in the network, the administrator creates an overlay. Typical examples are IPSec, GRE, CAPWAP, VXLAN, OTV, etc.
Why does the network factory help to overcome the above difficulties, which cannot be solved in the “classical network”?
In the “classical network” these difficulties are not solved for the principal reason - because contradictory requirements are placed on the same object.
In the case of a network factory, the object to which the requirements are imposed is divided into two. One network topology is divided into two.
The first, underlying topology provides reliable transport based on the routed network. This is her only task. It does not implement services and policies - it is not intended for this.
The task of implementing services and policies is solved by a second, overlay network topology. It is separated from the underlying topology, as, for example, the protocols of different layers of the OSI model are separated from each other.
The emergence of two network topologies and provides a denouement of conflicting requirements. This is the fundamental difference between the “classical network” and the network factory. This is what allows the network factory to overcome the difficulties that the “classical network” cannot handle.
The implementation of the network factory concept is already in many corporate networks. For example, the idea of a factory based on CAPWAP tunnels has long been implemented in the centralized architecture of corporate wireless LANs. Another example is a factory in data center networks in a Cisco Application Centric Infrastructure (ACI) solution. Factories are spreading in geographically distributed networks in the form of SD-WAN technologies, in particular, Cisco IWAN.
It is time for the network factory to appear in campus networks (see Figure 2).
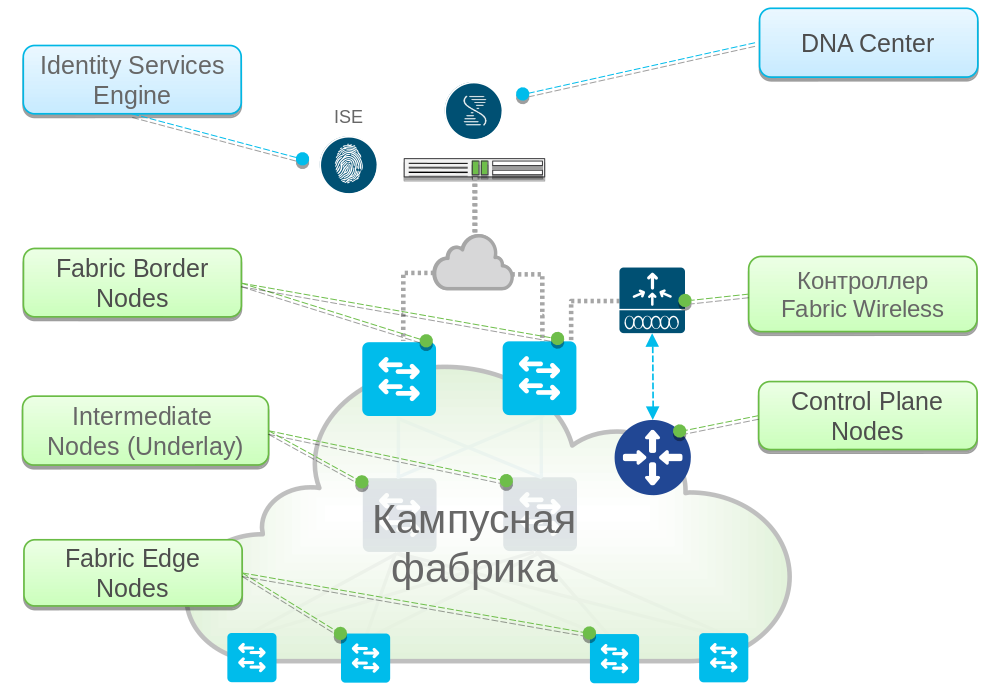
Fig. 2. Cisco SD-Access Network Factory Architecture
Cisco Software-Defined Access (SD-Access) is a Cisco implementation of a network fabric concept for a campus network with centralized management, automation and orchestration, as well as monitoring and analytics.
These tools are provided by the Cisco DNA Center Controller, a key component of the solution. DNA Center provides a web-based admin interface and APIs.
In addition, the DNA Center implements analytics services, obtaining and analyzing service information and telemetry from factory devices. The DNA Center solves the problem of converting a mass of disparate data into concrete conclusions and practical recommendations. Such conclusions and recommendations relate to the current state of the network, its services and applications, and current incidents. Based on data analysis taking into account context knowledge, DNA Center provides analytics on the likely impact of incidents on network services, recommends specific measures to eliminate incidents, analyzes trends, and gives recommendations on network capacity planning. This is a very important feature for monitoring, quick troubleshooting. Ultimately, it helps ensure high availability of business processes running on top of the factory.
DNA Center works in conjunction with the Cisco Identity Service Engine (ISE) access control server. ISE provides the factory with authentication, authorization, and access control (AAA) services, provides dynamic placement of factory users into groups, and controls policies for the interaction between groups. ISE is required to implement an organization's security policy in a factory.
From a network infrastructure point of view, a factory consists of devices that perform the following key roles.
Control Plane Nodes keep track of the current location of client devices within the factory. This is necessary for the free movement of users within the factory while preserving the policies assigned to the user and ensuring their mobility.
Fabric Border Nodes are needed to connect the factory to the outside world, i.e. to networks that are not part of the factory. For example, it can be a data center network and other parts of the corporate network that are not built on the basis of the SD-Access factory, the Internet, etc.
Fabric Edge Nodes provide connectivity to the factory of client devices, as well as radio access points.
The Fabric Wireless Controller is a wireless LAN controller operating as part of a factory.
Intermediate Nodes provide communication between the devices listed above. They do not perform any overlay functions, but only implement the underlying, underlying network topology.
In terms of technology, the data plane of the Cisco SD-Access factory is based on the Virtual Extensible LAN (VXLAN) encapsulation. The control plane overlay uses the Locator / ID Separation Protocol (LISP). Policies are implemented based on Cisco TrustSec Scalable Group Tag (SGT) tags. Finally, the overlay runs on top of the routed core network. Consider these technologies in more detail.
The Cisco SD-Access data plane is built on the basis of VXLAN encapsulation with the Group Policy Option (VXLAN-GPO). An important advantage of VXLAN is that it retains the original Ethernet frame header. As a result, the mobility of factory hosts is ensured, not only at Level 3, but also at Level 2. This provides a flexible and versatile transport. Whatever the requirements of the applications, the factory is able to provide them with any type of transport - Levels 3 and 2 - regardless of the direction of interaction between the hosts and their location in the factory.

Fig. 3. Encapsulation in the network SD-Access factory
Factory data plane traffic (Layer 2 frames) is encapsulated in VXLAN packets and sent over the network over UDP and IP (see Figure 3). From the point of view of factory intermediate devices, these are standard IP packets with embedded UDP segments addressed to port 4789. The UDP source port number is determined by the hash of the Layers 2, 3, and 4 source packets and is thus dynamically changing. This is important for proper Cisco Express Forwarding (CEF) load balancing in the core network. In load balancing, the CEF full method uses a hash value from the IP addresses and ports of the transport layer to select a specific communication channel. Therefore, the variable value of UDP source-ports leads to the distribution of the load between different communication channels even without the use of additional methods of dealing with CEF polarization .
VXLAN tunnels do not require pre-connection, i.e. are stateless tunnels.
An overlay causes additional headers due to the use of a core network (underlay) for transport. These are the 8-byte VXLAN header, the 8-byte UDP header, the 20-byte IP header, and the 14-byte MAC header (with optional additional 4 bytes) —the total is from 50 to 54 bytes.
Traffic encapsulation in VXLAN packets and back in the Cisco SD-Access solution is performed by factory edge devices. For external traffic, this is Fabric Border Nodes, for wired clients traffic - Fabric Edge Nodes.
SD-Access also integrates wireless networks into the factory (Figure 4). This mode of operation is called Fabric Enabled Wireless (FEW). Unlike the centralized WLAN architecture, in the FEW mode, the traffic of WLAN users is not tuned to the WLAN controller in CAPWAP packets, but to the Edge Node access switch in VXLAN packets. Thus, traffic to both wired and wireless clients goes directly to the Edge Node switches.
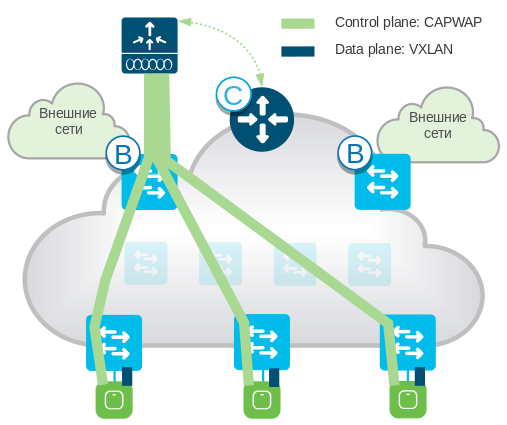
Fig. 4. Wireless LAN Integration into Cisco SD-Access Factory (B - Border Node, C - Control Plane Node)
As a result, the same traffic processing of wired and wireless users is ensured, optimization of WLAN traffic transmission paths, elimination of potential bottlenecks characteristic of the WLAN controller and wired network.
The Control & management plane of the wireless LAN in FEW mode remains centralized on the Fabric Wireless controller. The controller uses LISP to communicate with Control Plane Nodes about the current location of wireless clients in the factory. Radio access points communicate with the controller via the CAPWAP protocol.
Thus, the wireless network architecture, when integrated into the factory, gets the “best of two worlds”.
Host mobility at Levels 2 and 3 is an integral property of the factory. In terms of data plane, mobility is provided by VXLAN technology, and the Locator / ID Separation Protocol (LISP) is used as the control plane.
To ensure that hosts can be moved within a factory without changing addresses, the factory needs to track the location of each individual host. To solve this problem using traditional routing protocols, it would be necessary to work with host specific routes with / 32 or / 128 prefixes (for IPv4 and IPv6, respectively). The requirement to work with host specific routes by definition excludes aggregation of routes, which would lead to increased memory consumption of factory switches. In addition, every transfer of a host between switches in a factory would generate an update of the routing protocol, creating an additional load on the CPU of all switches regardless of whether this route needs this route or not.
As a result, the implementation of the mobility of the hosts would lead to high requirements for the resources of the control plane. And these requirements would concern the boundary switches of the factory - access switches, which, as a rule, do not have a powerful control plane.
The Cisco SD-Access factory uses the LISP protocol to solve this problem. This is a very efficient protocol optimized for host mobility. The factory contains a centralized Host Tracking Database (HTDB) user database running on Control Plane Nodes role devices. HTDB stores client host compliance information (Endpoint ID) to the current location within the factory, as well as a number of additional attributes.
Factory edge devices, using the LISP protocol, request the HTDB base when they need to send a packet to a client host with an unknown location, and store this information in the local cache.
Information enters the database from the border devices of the factory as the client hosts connect and move.
Thus, Cisco SD-Access allows hosts to move freely within the factory without changing addresses, ensures their mobility.
The factory offers flexible and scalable tools for implementing resource access control policies, as well as user segmentation and microsegmentation.
Historically, access control lists (ACLs) based on IP addresses have been used to solve access control problems. This happened because the IP packet header does not contain any other data that could be used to establish a logical connection between the IP packet and the user.
Such a solution requires large-scale implementation of ACLs in many places on the network, as well as keeping them up to date, making changes. And there are a lot of possible reasons for such changes - for example, new security policy requirements, changes in the composition of users, resources, network topology, user mobility in wired and wireless networks. Therefore, this approach requires a significant investment of time and effort of the staff. In addition, he is very vulnerable to errors. As a result, the security and scalability of the network, the speed of IT response to business needs, the availability of business processes are affected.
User segmentation has been implemented for a long time using virtual topologies collected from VLANs, VRFs, MPLS VPNs, tunnels and other similar means. This approach is also very resource-intensive and works the worse, the more dynamics in the segmentation environment and the more granular such segmentation is needed.
Therefore, virtual topologies are particularly poorly suited for microsegmentation of users, and it is precisely this that is required more and more often in connection with the digitalization of modern business and the evolution of security threats (including the mass distribution of network crypto-worms).
To address the challenges of access control and user segmentation, Cisco has developed TrustSec technology. TrustSec uses the Scalable Group Tag (SGT) label instead of the IP address as a criterion for a package to belong to a group of users. This approach allows you to separate addressing from access control, use specialized SGACL access control lists to implement access control policies, give the network flexibility and automate the application of security policies.
The basic method of transferring tags within the TrustSec domain (inline method) is to encapsulate tags in frames or traffic headers (in the Cisco Meta Data field). And in the Cisco SD-Access factory, the label value is transferred as part of the VXLAN overlay headers. The VXLAN header contains the VN ID and Segment ID fields (24- and 16-bit, respectively), see fig. 3. These fields are used to transfer information about the package ownership of a certain virtual network VN (addressed over 16 million VRF) and the SGT group of TrustSec technology (addressed over 64 thousand tags). Thus, TrustSec is initially integral to the factory. In addition, the encapsulation of the SGT tag in the VXLAN header makes it easier to implement TrustSec - after all, the intermediate backbone devices are not required to work with the tags.
The Cisco SD-Access factory allows you to implement two levels of user segmentation: VRF for coarse segmentation at a high level (for example, for separating organizations or their divisions) and SGT groups for fine segmentation (for example, at the level from organization to small workgroups). In the first release, the SD-Access SGT factories are unique within VN, but in principle, so-called VN-Agnostic groups are also possible, present in different VNs, since SGT is independent of IP addresses or VRF.
The term SGT itself deserves a separate explanation. He appeared in the process of developing technology TrustSec and was originally called the Source Group Tag. Through the efforts of marketers, the term has come to mean the Security Group Tag. In the case of TrustSec, this was justified, because SGT was used to implement security policies. Still, SGT is just a label, a number to distinguish between packets. And this number is suitable for the implementation of any policies, not only security, which is done in Cisco SD-Access. As a result, SGT now means Scalable Group Tag.
Access control, configuration and implementation of access policies is performed on the Cisco ISE server integrated into the Cisco SD-Access solution. As a result, SD-Access offers ready-made automated means of implementing an organization’s access control policy, as well as segmentation and micro-segmentation of users.
The main task of the core network from the point of view of the factory is to ensure the transfer of traffic overlay. The overlay network is transparent for the overlay. Therefore, any modern corporate network can be used as a backbone network, providing an adequate level of availability and performance. It should provide factory edge devices, such as Fabric Edge Node, Border Node, Control Plane Node, IP communications.
In general, the core network can be built on the basis of any combination of Layer 2 and 3 technologies, although Cisco recommends building a fully routable network (with routing to access switches) and communication channels that have a point-to-point configuration. The routing protocol can also be any, the recommended option is IS-IS, which has become the de facto standard in the core networks of factories due to its independence from Level 3 addresses, fast convergence and availability of TLV parameters.
In connection with VXLAN encapsulation of overlay, Cisco recommends that jumbo frames with a MTU value of at least 9,100 bytes be transmitted on the core network. Packet transfer delay (RTT) within the factory must not exceed 100 ms.
Refer to the Cisco SD-Access Design Guide for details on the core network requirements.
As the core network equipment, any equipment that meets these requirements, from both Cisco and other manufacturers, is suitable. You can use an existing corporate network. This provides protection for investments in equipment of the existing network, even if it is not supported by the factory. In this case, the core network will be Manual Underlay, i.e. controlled autonomously from the factory.
There is also the possibility of automating the control of the core network using factory tools in the case of using appropriate Cisco equipment (Cisco SD-Access 1.0 provides automation of the core network built on the basis of Catalyst 3850/3650 and 9000 series switches). This is an Automated Underlay script. In this case, provisioning of the core network will be performed by the DNA Center functionality. The controller downloads pre-tested configurations based on Cisco Validated Design recommendations to devices on the core network. Manual editing of device configurations in the Automated Underlay mode at the time of this writing is not allowed, but this possibility is expected in the future.
In addition to protecting investments, the flexibility of the SD-Access requirements to the core network makes it easier to implement - you can start with a pilot project, create a small factory that uses an existing core network as a transport, and gradually migrate to a full-scale solution.
We looked at the key components and principles of the Cisco SD-Access solution. Now let's analyze the practical value of the solution for IT and business using specific scenarios.
Consider a number of tasks typical for IT, and compare two conditional networks: the “classical” and the network based on the SD-Access factory (hereinafter referred to as the SD-Access network).
In this comparison, the classic network will be understood as a campus network with a switched access level and a routable kernel. Suppose that access control in such a network is implemented using access control lists (ACLs), and most of the configuration and troubleshooting is done manually. The network uses a RADIUS server to control user access.
The SD-Access network is a network built on the basis of the Cisco SD-Access factory, which includes the network infrastructure, the DNA Center controller and the Cisco ISE access control server.
One of the typical tasks of IT is associated with the commissioning of new parts of the network or networks at new sites, as well as with the modernization of existing networks.
The solution of this problem in the case of the classical network is often implemented by a complex combination of manual labor and heterogeneous automation tools.
With this approach, it is difficult to ensure consistent configurations of equipment during implementation, and especially during operation, when changes inevitably arise. The process is poorly protected from errors due to the "human factor". And finally, it does not allow flexibility to adapt to business changes — in the course of implementation work, including design and configuration development, equipment ordering and physical delivery, styling and configuration introduction — changes in business needs may occur and the implemented configuration will be outdated. before the network is commissioned!
It would seem that the abundance of centralized management tools and additional tools should solve this problem. But the data from Cisco, for which about 90% of changes in corporate networks are still done manually, suggest the opposite.
The SD-Access network offers tools for streamlining and automating the process. Cisco DNA Center allows you to centrally define the hierarchical structure of organization sites linked to a geographic location. For hierarchy objects, you can centrally specify parameter values, such as the addresses of AAA servers, NTP, DNS, NetFlow data collectors, Syslog and SNMP, passwords, etc. These parameters can be inherited hierarchically by networks of other sites, and can be set individually. Further, DNA Center allows you to create configuration templates for further approval and implementation in the network. In addition, the DNA network offers the Plug and Play toolkit (PnP) for automated connection of new devices to the factory with the possibility of linking them to hierarchy sites and centralized distribution of configurations across network devices.
As a result, the SD-Access network provides:
The trend of digitalization leads to a significant increase in the number and types of devices connected to the network. These are desktops and laptops, smartphones and tablets, printers, security cameras, sensors and other Internet of Things (IoT) devices, etc.
You need to make sure that the network’s IP addressing plan is ready to connect all the required devices, but also to apply the appropriate security policies.
Traditional network requires considerable effort to solve this problem. First, since IP addresses are usually used not only for addressing, but also as a criterion for applying policies, the addressing plan becomes more complicated, and making changes to addressing becomes very difficult. Secondly, the complexity of implementing policies often leads to the fact that the internal perimeter of the wired network is not protected, and security policies are not applied to the connected devices or, in the best case, the basic 802.1x functionality is used.
The SD-Access network has a centralized functionality for managing pools of IP addresses, incl. with integration with Infoblox services. This greatly simplifies the work with network addressing. In addition, the architecture of the network factory itself contributes to a significant simplification of IP addressing, because it allows the use of addresses only for their intended purpose. There is no longer a need to bind policies to the addresses of hosts and subnets. In addition, even if due to the requirements of applications or any client devices, an IP subnet stretched across campus is needed, the overlay allows you to solve this problem without disrupting the design of the routed backbone network, without the risks of broadcast storms and other troubles of Level 2 domains. As a result, the SD-Access network is ready to connect the maximum number of devices of different types with minimum requirements for the number of subnets.
Protection of the internal network perimeter is realized through integration with the Cisco ISE service and the Active Directory directory service, ensuring dynamic and granular application of security policies without being bound to IP addresses.
Thus, the SD-Access network offers:
— , , , .
. . , , , , . , ( , , ..), «» ( , , Internet of Things (IoT). .
, , . . ( , ), ( , , , ), ( ).
, . — , , IoT ..
Other examples - phones or computers with multimedia applications running on a wireless LAN may require roaming at Layers 2 and 3. Considerations of the requirements of applications or accessing resources may necessitate the presence of the same IP subnet on different parts of a corporate campus .
The slow introduction of new services can mean lost business opportunities and, ultimately, lost market share. Therefore, network services and policies that are important for business processes should be implemented the sooner the better. The question arises - how to ensure the launch of new services and policies that meet the requirements of the business, and do it quickly and throughout the network?
The classical network in modern conditions requires more and more time and effort to launch new services and adapt to changes in policies, because it is a set of devices that are autonomous from each other. In addition, classic network devices may have different operating systems, different ways of implementing the necessary functionality, different ways of setting it up in the command line interface.
Centralized management tools do not always help. Although they provide opportunities to automate many IT processes, the creation of a unified, coordinated policy requires orchestration functionality, which in practice is absent in the classical network.
— «» , . , , . , Cisco 2016 ., 90% . , , , - « ».
SD-Access - Cisco DNA Center. , . , DNA Center.
, , «-». DNA Center «-» — , , , .., . south bound APIs — Netconf/YANG, REST, CLI.
, north bound REST API , API.
SD-Access , , .
, .. 3, 2.
:
, , , .
3 2, , ?
. VLAN' , , , , MPLS VPN, .
. , . -, .
SD-Access , . VXLAN 3, 2. Fabric Enabled Wireless (FEW). , (Edge Nodes), , . (Edge Node) SD-Access control plane LISP L3 Anycast Gateway. SD-Access IP-, .
, SD-Access :
, , .
, 40 . Target, .
-, WannaCry, Petya .., .
, . , .
(, VLAN, VRF, MPLS VPN ..) / (ACL). , . . , , ACL « », , . .
SD-Access . . — (Virtual Networks) VRF. — (Scalable Groups) Cisco TrustSec.
VRF , . , . — , .
TrustSec , , . TrustSec Cisco ISE. SGT SGACL.
TrustSec . .
TrustSec Cisco SD-Access. , TrustSec , SD-Access.
, SGT VXLAN, TrustSec control plane, SXP. TrustSec , .
, SD-Access TrustSec .
SD-Access :
— , , (QoS) ..
, .
.
SD-Access , DNA Center . , .
. — — IP- .
, IP- , , . IP- .
The policy implemented on the basis of IP addresses becomes not centralized, but distributed across the network in device configurations. Thousands of line ACLs appear. Users and devices are grouped by VLANs. Subnets are used to group users and devices according to any feature. Virtual network topologies are created for traffic segmentation. IP addresses are simply overloaded with meaning.
As a result, such an approach to the implementation of policies leads to a great investment of time and effort, as well as an increased probability of error.
, IP- : , VLAN', . , , — , , , , .
IP- , . .
The SD-Access network makes it possible to implement a single holistic policy, using as a criterion for applying the policy, not the IP address, but the SGT (Scalable Group Tag) group, information about which is encapsulated in the VXLAN header of the network factory. Assigning users to an SGT group can be done centrally and dynamically with respect to the Cisco Identity Services Engine (ISE) access control server database, as well as Active Directory. Assignment to an SGT group is made in light of additional context, such as profiling and posture.
As a result, the SD-Access network provides a holistic, consistent, dynamic policy across the entire network, independent of IP addresses.
(QoS) , , DiffServ. DiffServ .
QoS . , , .
Cisco QoS DNA Center. (push) QoS .
QoS . (, UADP) IOS-XE QoS. , NBAR2 .
, SD-Access QoS .
, (traffic engineering) .
, Policy Based Routing (PBR), MPLS Traffic Engineering (MPLS TE), SPAN ..
SD-Access Path Preference Traffic Copy Contracts, DNA Center .
, -.
, . . Cisco, 85% , . , , . , . .
SD-Access DNA Center. , , . .
DNA Center , , . , .
, DNA Center .
SD-Access :
The Cisco Software-Defined Access (SD-Access) factory is a new approach to building corporate networks and makes a big step forward compared to classic campus networks. In importance, this step can be compared with the transition from computers with a command line interface to computers with a graphical user interface.
The factory offers the IT service new powerful opportunities in the field of design, implementation, operation of the corporate network, implementation of policies, and troubleshooting. These capabilities enable IT to fulfill business requirements quickly and efficiently. It is possible to minimize the routine work, allocate more time to more strategic, important tasks that have higher value for the employer, as well as giving competitive advantages in the labor market.
Business, in turn, receives significant advantages in speed of implementation of initiatives and solving problems based on the network. Ultimately, this helps to expand the market share, increase revenue. Cisco SD-Access also offers businesses a significant reduction in the risks of business process disruptions associated with the "human factor" and a fundamentally new level of information security.
It discusses the key components and technologies underlying the Cisco SD-Access, as well as the principles of their work.
On the example of specific typical scenarios, the advantages offered to IT and business by the SD-Access factory are analyzed in detail.
1. What problem is solved and why?
Corporate IT service is "between the hammer and the anvil."
')
On the one hand, the business requires high availability of the network and expects that the network should always work - 24x7, with no exceptions! It is obvious. In IT, it is difficult to find something that worries a business more than the inaccessibility of business processes . But with the development of digital technology, the dependence of business processes on the network is only growing.
On the other hand, users (and in fact, the same business) require the support of new services, new types of devices, new types of users (including guests, partners), etc. They all need to ensure proper support from the network, and quickly. In addition, it is necessary to take into account the requirements of the information security service.
But the requirements of introducing new services and ensuring high availability, as a rule, contradict each other. After all, high availability implies first of all network stability, which is known as from specialized literature (for example, Piedad, Floyd, and Michael Hawkins. High availability: design, techniques, and processes. Upper Saddle River, NJ: Prentice Hall PTR, 2001. Print), and from general principles, for example, KISS (Keep it Simple Stupid), “it works — don't touch it”, etc.
And the introduction of new network services, by definition, violates its stability, since it introduces something new into the network and requires changes. These changes are often complex and extensive - for example, the introduction of solutions for collaborative multimedia work and QoS mechanisms, security technologies and segmentation. Even solving “transport” problems can be difficult, such as ensuring connectivity at Layer 2 between points A and B in different parts of the campus network.
As a result, the introduction of services complicates the network and requires a lot of time, and sometimes not at all.
There is another side to the contradiction between ensuring high availability and solving everyday business problems. Business tasks usually require from the network not just the transfer of packets from point A to point B, but the implementation of various kinds of policies. Policies are translated into specific requirements, for example, how to ensure security, how to route traffic from different applications, how to handle it, and so on. Any nontrivial policy increases the complexity of the implementation and operation of the network.
In addition, policies are not enough to implement. It is also necessary to keep them up to date, to make changes to them. Such changes in the scale of the corporate network, especially manual ones, are usually resource-intensive, long-lasting and highly vulnerable to errors. As a result, network availability again tends to decrease, and operating costs increase.
Thus, in a typical, “classic” corporate network
- requirements for increasing the availability and implementation of services contradict each other;
- implementation of policies is difficult;
- the task of implementing policies and keeping them up to date makes it difficult to ensure high availability of the network.
These challenges IT services face everywhere. But business is not interested in the difficulties of IT. Business is interested in business processes to work reliably, and implemented - quickly.
2. Network factory: combining incompatible
How to solve these conflicting challenges facing IT? A well-proven method for solving complex problems is to break one task into several simpler ones, and then solve them. The well-known examples are the seven-level OSI model or the four-level DoD model in solving the problem of network interaction.

Fig. 1. The concept of a network factory (overlay)
In our case, the concept of a network factory, or overlay, comes to the rescue (see Figure 1). An overlay is a logical topology built on top of some underlying topology (underlay) of the core network. Overlay uses any type of traffic encapsulation for transmission over the core network. The concept of overlay is well known to network administrators. Laying any tunnel in the network, the administrator creates an overlay. Typical examples are IPSec, GRE, CAPWAP, VXLAN, OTV, etc.
Why does the network factory help to overcome the above difficulties, which cannot be solved in the “classical network”?
In the “classical network” these difficulties are not solved for the principal reason - because contradictory requirements are placed on the same object.
In the case of a network factory, the object to which the requirements are imposed is divided into two. One network topology is divided into two.
The first, underlying topology provides reliable transport based on the routed network. This is her only task. It does not implement services and policies - it is not intended for this.
The task of implementing services and policies is solved by a second, overlay network topology. It is separated from the underlying topology, as, for example, the protocols of different layers of the OSI model are separated from each other.
The emergence of two network topologies and provides a denouement of conflicting requirements. This is the fundamental difference between the “classical network” and the network factory. This is what allows the network factory to overcome the difficulties that the “classical network” cannot handle.
3. What is Cisco SD-Access?
The implementation of the network factory concept is already in many corporate networks. For example, the idea of a factory based on CAPWAP tunnels has long been implemented in the centralized architecture of corporate wireless LANs. Another example is a factory in data center networks in a Cisco Application Centric Infrastructure (ACI) solution. Factories are spreading in geographically distributed networks in the form of SD-WAN technologies, in particular, Cisco IWAN.
It is time for the network factory to appear in campus networks (see Figure 2).

Fig. 2. Cisco SD-Access Network Factory Architecture
Cisco Software-Defined Access (SD-Access) is a Cisco implementation of a network fabric concept for a campus network with centralized management, automation and orchestration, as well as monitoring and analytics.
These tools are provided by the Cisco DNA Center Controller, a key component of the solution. DNA Center provides a web-based admin interface and APIs.
In addition, the DNA Center implements analytics services, obtaining and analyzing service information and telemetry from factory devices. The DNA Center solves the problem of converting a mass of disparate data into concrete conclusions and practical recommendations. Such conclusions and recommendations relate to the current state of the network, its services and applications, and current incidents. Based on data analysis taking into account context knowledge, DNA Center provides analytics on the likely impact of incidents on network services, recommends specific measures to eliminate incidents, analyzes trends, and gives recommendations on network capacity planning. This is a very important feature for monitoring, quick troubleshooting. Ultimately, it helps ensure high availability of business processes running on top of the factory.
DNA Center works in conjunction with the Cisco Identity Service Engine (ISE) access control server. ISE provides the factory with authentication, authorization, and access control (AAA) services, provides dynamic placement of factory users into groups, and controls policies for the interaction between groups. ISE is required to implement an organization's security policy in a factory.
From a network infrastructure point of view, a factory consists of devices that perform the following key roles.
Control Plane Nodes keep track of the current location of client devices within the factory. This is necessary for the free movement of users within the factory while preserving the policies assigned to the user and ensuring their mobility.
Fabric Border Nodes are needed to connect the factory to the outside world, i.e. to networks that are not part of the factory. For example, it can be a data center network and other parts of the corporate network that are not built on the basis of the SD-Access factory, the Internet, etc.
Fabric Edge Nodes provide connectivity to the factory of client devices, as well as radio access points.
The Fabric Wireless Controller is a wireless LAN controller operating as part of a factory.
Intermediate Nodes provide communication between the devices listed above. They do not perform any overlay functions, but only implement the underlying, underlying network topology.
In terms of technology, the data plane of the Cisco SD-Access factory is based on the Virtual Extensible LAN (VXLAN) encapsulation. The control plane overlay uses the Locator / ID Separation Protocol (LISP). Policies are implemented based on Cisco TrustSec Scalable Group Tag (SGT) tags. Finally, the overlay runs on top of the routed core network. Consider these technologies in more detail.
3.1. Data plane overlay: VXLAN
The Cisco SD-Access data plane is built on the basis of VXLAN encapsulation with the Group Policy Option (VXLAN-GPO). An important advantage of VXLAN is that it retains the original Ethernet frame header. As a result, the mobility of factory hosts is ensured, not only at Level 3, but also at Level 2. This provides a flexible and versatile transport. Whatever the requirements of the applications, the factory is able to provide them with any type of transport - Levels 3 and 2 - regardless of the direction of interaction between the hosts and their location in the factory.

Fig. 3. Encapsulation in the network SD-Access factory
Factory data plane traffic (Layer 2 frames) is encapsulated in VXLAN packets and sent over the network over UDP and IP (see Figure 3). From the point of view of factory intermediate devices, these are standard IP packets with embedded UDP segments addressed to port 4789. The UDP source port number is determined by the hash of the Layers 2, 3, and 4 source packets and is thus dynamically changing. This is important for proper Cisco Express Forwarding (CEF) load balancing in the core network. In load balancing, the CEF full method uses a hash value from the IP addresses and ports of the transport layer to select a specific communication channel. Therefore, the variable value of UDP source-ports leads to the distribution of the load between different communication channels even without the use of additional methods of dealing with CEF polarization .
VXLAN tunnels do not require pre-connection, i.e. are stateless tunnels.
An overlay causes additional headers due to the use of a core network (underlay) for transport. These are the 8-byte VXLAN header, the 8-byte UDP header, the 20-byte IP header, and the 14-byte MAC header (with optional additional 4 bytes) —the total is from 50 to 54 bytes.
Traffic encapsulation in VXLAN packets and back in the Cisco SD-Access solution is performed by factory edge devices. For external traffic, this is Fabric Border Nodes, for wired clients traffic - Fabric Edge Nodes.
SD-Access also integrates wireless networks into the factory (Figure 4). This mode of operation is called Fabric Enabled Wireless (FEW). Unlike the centralized WLAN architecture, in the FEW mode, the traffic of WLAN users is not tuned to the WLAN controller in CAPWAP packets, but to the Edge Node access switch in VXLAN packets. Thus, traffic to both wired and wireless clients goes directly to the Edge Node switches.

Fig. 4. Wireless LAN Integration into Cisco SD-Access Factory (B - Border Node, C - Control Plane Node)
As a result, the same traffic processing of wired and wireless users is ensured, optimization of WLAN traffic transmission paths, elimination of potential bottlenecks characteristic of the WLAN controller and wired network.
The Control & management plane of the wireless LAN in FEW mode remains centralized on the Fabric Wireless controller. The controller uses LISP to communicate with Control Plane Nodes about the current location of wireless clients in the factory. Radio access points communicate with the controller via the CAPWAP protocol.
Thus, the wireless network architecture, when integrated into the factory, gets the “best of two worlds”.
3.2. Control plane overlay: LISP
Host mobility at Levels 2 and 3 is an integral property of the factory. In terms of data plane, mobility is provided by VXLAN technology, and the Locator / ID Separation Protocol (LISP) is used as the control plane.
To ensure that hosts can be moved within a factory without changing addresses, the factory needs to track the location of each individual host. To solve this problem using traditional routing protocols, it would be necessary to work with host specific routes with / 32 or / 128 prefixes (for IPv4 and IPv6, respectively). The requirement to work with host specific routes by definition excludes aggregation of routes, which would lead to increased memory consumption of factory switches. In addition, every transfer of a host between switches in a factory would generate an update of the routing protocol, creating an additional load on the CPU of all switches regardless of whether this route needs this route or not.
As a result, the implementation of the mobility of the hosts would lead to high requirements for the resources of the control plane. And these requirements would concern the boundary switches of the factory - access switches, which, as a rule, do not have a powerful control plane.
The Cisco SD-Access factory uses the LISP protocol to solve this problem. This is a very efficient protocol optimized for host mobility. The factory contains a centralized Host Tracking Database (HTDB) user database running on Control Plane Nodes role devices. HTDB stores client host compliance information (Endpoint ID) to the current location within the factory, as well as a number of additional attributes.
Factory edge devices, using the LISP protocol, request the HTDB base when they need to send a packet to a client host with an unknown location, and store this information in the local cache.
Information enters the database from the border devices of the factory as the client hosts connect and move.
Thus, Cisco SD-Access allows hosts to move freely within the factory without changing addresses, ensures their mobility.
3.3. Access Control Policies and Segmentation: TrustSec
The factory offers flexible and scalable tools for implementing resource access control policies, as well as user segmentation and microsegmentation.
Historically, access control lists (ACLs) based on IP addresses have been used to solve access control problems. This happened because the IP packet header does not contain any other data that could be used to establish a logical connection between the IP packet and the user.
Such a solution requires large-scale implementation of ACLs in many places on the network, as well as keeping them up to date, making changes. And there are a lot of possible reasons for such changes - for example, new security policy requirements, changes in the composition of users, resources, network topology, user mobility in wired and wireless networks. Therefore, this approach requires a significant investment of time and effort of the staff. In addition, he is very vulnerable to errors. As a result, the security and scalability of the network, the speed of IT response to business needs, the availability of business processes are affected.
User segmentation has been implemented for a long time using virtual topologies collected from VLANs, VRFs, MPLS VPNs, tunnels and other similar means. This approach is also very resource-intensive and works the worse, the more dynamics in the segmentation environment and the more granular such segmentation is needed.
Therefore, virtual topologies are particularly poorly suited for microsegmentation of users, and it is precisely this that is required more and more often in connection with the digitalization of modern business and the evolution of security threats (including the mass distribution of network crypto-worms).
To address the challenges of access control and user segmentation, Cisco has developed TrustSec technology. TrustSec uses the Scalable Group Tag (SGT) label instead of the IP address as a criterion for a package to belong to a group of users. This approach allows you to separate addressing from access control, use specialized SGACL access control lists to implement access control policies, give the network flexibility and automate the application of security policies.
The basic method of transferring tags within the TrustSec domain (inline method) is to encapsulate tags in frames or traffic headers (in the Cisco Meta Data field). And in the Cisco SD-Access factory, the label value is transferred as part of the VXLAN overlay headers. The VXLAN header contains the VN ID and Segment ID fields (24- and 16-bit, respectively), see fig. 3. These fields are used to transfer information about the package ownership of a certain virtual network VN (addressed over 16 million VRF) and the SGT group of TrustSec technology (addressed over 64 thousand tags). Thus, TrustSec is initially integral to the factory. In addition, the encapsulation of the SGT tag in the VXLAN header makes it easier to implement TrustSec - after all, the intermediate backbone devices are not required to work with the tags.
The Cisco SD-Access factory allows you to implement two levels of user segmentation: VRF for coarse segmentation at a high level (for example, for separating organizations or their divisions) and SGT groups for fine segmentation (for example, at the level from organization to small workgroups). In the first release, the SD-Access SGT factories are unique within VN, but in principle, so-called VN-Agnostic groups are also possible, present in different VNs, since SGT is independent of IP addresses or VRF.
The term SGT itself deserves a separate explanation. He appeared in the process of developing technology TrustSec and was originally called the Source Group Tag. Through the efforts of marketers, the term has come to mean the Security Group Tag. In the case of TrustSec, this was justified, because SGT was used to implement security policies. Still, SGT is just a label, a number to distinguish between packets. And this number is suitable for the implementation of any policies, not only security, which is done in Cisco SD-Access. As a result, SGT now means Scalable Group Tag.
Access control, configuration and implementation of access policies is performed on the Cisco ISE server integrated into the Cisco SD-Access solution. As a result, SD-Access offers ready-made automated means of implementing an organization’s access control policy, as well as segmentation and micro-segmentation of users.
3.4. Core network
The main task of the core network from the point of view of the factory is to ensure the transfer of traffic overlay. The overlay network is transparent for the overlay. Therefore, any modern corporate network can be used as a backbone network, providing an adequate level of availability and performance. It should provide factory edge devices, such as Fabric Edge Node, Border Node, Control Plane Node, IP communications.
In general, the core network can be built on the basis of any combination of Layer 2 and 3 technologies, although Cisco recommends building a fully routable network (with routing to access switches) and communication channels that have a point-to-point configuration. The routing protocol can also be any, the recommended option is IS-IS, which has become the de facto standard in the core networks of factories due to its independence from Level 3 addresses, fast convergence and availability of TLV parameters.
In connection with VXLAN encapsulation of overlay, Cisco recommends that jumbo frames with a MTU value of at least 9,100 bytes be transmitted on the core network. Packet transfer delay (RTT) within the factory must not exceed 100 ms.
Refer to the Cisco SD-Access Design Guide for details on the core network requirements.
As the core network equipment, any equipment that meets these requirements, from both Cisco and other manufacturers, is suitable. You can use an existing corporate network. This provides protection for investments in equipment of the existing network, even if it is not supported by the factory. In this case, the core network will be Manual Underlay, i.e. controlled autonomously from the factory.
There is also the possibility of automating the control of the core network using factory tools in the case of using appropriate Cisco equipment (Cisco SD-Access 1.0 provides automation of the core network built on the basis of Catalyst 3850/3650 and 9000 series switches). This is an Automated Underlay script. In this case, provisioning of the core network will be performed by the DNA Center functionality. The controller downloads pre-tested configurations based on Cisco Validated Design recommendations to devices on the core network. Manual editing of device configurations in the Automated Underlay mode at the time of this writing is not allowed, but this possibility is expected in the future.
In addition to protecting investments, the flexibility of the SD-Access requirements to the core network makes it easier to implement - you can start with a pilot project, create a small factory that uses an existing core network as a transport, and gradually migrate to a full-scale solution.
4. Why Cisco SD-Access Business: Typical Scenarios
We looked at the key components and principles of the Cisco SD-Access solution. Now let's analyze the practical value of the solution for IT and business using specific scenarios.
Consider a number of tasks typical for IT, and compare two conditional networks: the “classical” and the network based on the SD-Access factory (hereinafter referred to as the SD-Access network).
In this comparison, the classic network will be understood as a campus network with a switched access level and a routable kernel. Suppose that access control in such a network is implemented using access control lists (ACLs), and most of the configuration and troubleshooting is done manually. The network uses a RADIUS server to control user access.
The SD-Access network is a network built on the basis of the Cisco SD-Access factory, which includes the network infrastructure, the DNA Center controller and the Cisco ISE access control server.
4.1. How to quickly launch the network into operation?
One of the typical tasks of IT is associated with the commissioning of new parts of the network or networks at new sites, as well as with the modernization of existing networks.
The solution of this problem in the case of the classical network is often implemented by a complex combination of manual labor and heterogeneous automation tools.
With this approach, it is difficult to ensure consistent configurations of equipment during implementation, and especially during operation, when changes inevitably arise. The process is poorly protected from errors due to the "human factor". And finally, it does not allow flexibility to adapt to business changes — in the course of implementation work, including design and configuration development, equipment ordering and physical delivery, styling and configuration introduction — changes in business needs may occur and the implemented configuration will be outdated. before the network is commissioned!
It would seem that the abundance of centralized management tools and additional tools should solve this problem. But the data from Cisco, for which about 90% of changes in corporate networks are still done manually, suggest the opposite.
The SD-Access network offers tools for streamlining and automating the process. Cisco DNA Center allows you to centrally define the hierarchical structure of organization sites linked to a geographic location. For hierarchy objects, you can centrally specify parameter values, such as the addresses of AAA servers, NTP, DNS, NetFlow data collectors, Syslog and SNMP, passwords, etc. These parameters can be inherited hierarchically by networks of other sites, and can be set individually. Further, DNA Center allows you to create configuration templates for further approval and implementation in the network. In addition, the DNA network offers the Plug and Play toolkit (PnP) for automated connection of new devices to the factory with the possibility of linking them to hierarchy sites and centralized distribution of configurations across network devices.
As a result, the SD-Access network provides:
- Significantly accelerate network deployment through automation.
- Reducing the risks associated with the "human factor", due to the automated maintenance of consistent and up-to-date device configurations.
4.2. How to connect client devices quickly and safely?
The trend of digitalization leads to a significant increase in the number and types of devices connected to the network. These are desktops and laptops, smartphones and tablets, printers, security cameras, sensors and other Internet of Things (IoT) devices, etc.
You need to make sure that the network’s IP addressing plan is ready to connect all the required devices, but also to apply the appropriate security policies.
Traditional network requires considerable effort to solve this problem. First, since IP addresses are usually used not only for addressing, but also as a criterion for applying policies, the addressing plan becomes more complicated, and making changes to addressing becomes very difficult. Secondly, the complexity of implementing policies often leads to the fact that the internal perimeter of the wired network is not protected, and security policies are not applied to the connected devices or, in the best case, the basic 802.1x functionality is used.
The SD-Access network has a centralized functionality for managing pools of IP addresses, incl. with integration with Infoblox services. This greatly simplifies the work with network addressing. In addition, the architecture of the network factory itself contributes to a significant simplification of IP addressing, because it allows the use of addresses only for their intended purpose. There is no longer a need to bind policies to the addresses of hosts and subnets. In addition, even if due to the requirements of applications or any client devices, an IP subnet stretched across campus is needed, the overlay allows you to solve this problem without disrupting the design of the routed backbone network, without the risks of broadcast storms and other troubles of Level 2 domains. As a result, the SD-Access network is ready to connect the maximum number of devices of different types with minimum requirements for the number of subnets.
Protection of the internal network perimeter is realized through integration with the Cisco ISE service and the Active Directory directory service, ensuring dynamic and granular application of security policies without being bound to IP addresses.
Thus, the SD-Access network offers:
- Readiness for mass connection of devices of different types due to simplicity of IP addressing management, efficient use of addresses and flexible Layer 2 and 3 transport.
- Significant optimization of time and effort for managing IP-addressing.
- Secure device deployment through the simplicity of applying dynamic, granular security policies without being bound to IP addresses.
4.3. How to quickly adapt existing services and policies to new business requirements?
— , , , .
. . , , , , . , ( , , ..), «» ( , , Internet of Things (IoT). .
, , . . ( , ), ( , , , ), ( ).
, . — , , IoT ..
Other examples - phones or computers with multimedia applications running on a wireless LAN may require roaming at Layers 2 and 3. Considerations of the requirements of applications or accessing resources may necessitate the presence of the same IP subnet on different parts of a corporate campus .
The slow introduction of new services can mean lost business opportunities and, ultimately, lost market share. Therefore, network services and policies that are important for business processes should be implemented the sooner the better. The question arises - how to ensure the launch of new services and policies that meet the requirements of the business, and do it quickly and throughout the network?
The classical network in modern conditions requires more and more time and effort to launch new services and adapt to changes in policies, because it is a set of devices that are autonomous from each other. In addition, classic network devices may have different operating systems, different ways of implementing the necessary functionality, different ways of setting it up in the command line interface.
Centralized management tools do not always help. Although they provide opportunities to automate many IT processes, the creation of a unified, coordinated policy requires orchestration functionality, which in practice is absent in the classical network.
— «» , . , , . , Cisco 2016 ., 90% . , , , - « ».
SD-Access - Cisco DNA Center. , . , DNA Center.
, , «-». DNA Center «-» — , , , .., . south bound APIs — Netconf/YANG, REST, CLI.
, north bound REST API , API.
SD-Access , , .
4.4. 3 2? ?
, .. 3, 2.
:
- , - , , ;
- , , , ;
- , IT- ;
- , 2 IP-.
, , , .
3 2, , ?
. VLAN' , , , , MPLS VPN, .
. , . -, .
SD-Access , . VXLAN 3, 2. Fabric Enabled Wireless (FEW). , (Edge Nodes), , . (Edge Node) SD-Access control plane LISP L3 Anycast Gateway. SD-Access IP-, .
, SD-Access :
- , 3 2.
- .
- , 3 2.
4.5. ?
, , .
, 40 . Target, .
-, WannaCry, Petya .., .
, . , .
(, VLAN, VRF, MPLS VPN ..) / (ACL). , . . , , ACL « », , . .
SD-Access . . — (Virtual Networks) VRF. — (Scalable Groups) Cisco TrustSec.
VRF , . , . — , .
TrustSec , , . TrustSec Cisco ISE. SGT SGACL.
TrustSec . .
TrustSec Cisco SD-Access. , TrustSec , SD-Access.
, SGT VXLAN, TrustSec control plane, SXP. TrustSec , .
, SD-Access TrustSec .
SD-Access :
- - - « » , VRF TrustSec.
- .
- .
4.6. , , ?
— , , (QoS) ..
, .
.
SD-Access , DNA Center . , .
4.6.1. Security policy
. — — IP- .
, IP- , , . IP- .
The policy implemented on the basis of IP addresses becomes not centralized, but distributed across the network in device configurations. Thousands of line ACLs appear. Users and devices are grouped by VLANs. Subnets are used to group users and devices according to any feature. Virtual network topologies are created for traffic segmentation. IP addresses are simply overloaded with meaning.
As a result, such an approach to the implementation of policies leads to a great investment of time and effort, as well as an increased probability of error.
, IP- : , VLAN', . , , — , , , , .
IP- , . .
The SD-Access network makes it possible to implement a single holistic policy, using as a criterion for applying the policy, not the IP address, but the SGT (Scalable Group Tag) group, information about which is encapsulated in the VXLAN header of the network factory. Assigning users to an SGT group can be done centrally and dynamically with respect to the Cisco Identity Services Engine (ISE) access control server database, as well as Active Directory. Assignment to an SGT group is made in light of additional context, such as profiling and posture.
As a result, the SD-Access network provides a holistic, consistent, dynamic policy across the entire network, independent of IP addresses.
4.6.2. Quality of Service (QoS) Policy
(QoS) , , DiffServ. DiffServ .
QoS . , , .
- QoS .
- QoS.
- QoS ( ) , .
- - (, ) (, NBAR2, DPI, DNS-AS, ).
Cisco QoS DNA Center. (push) QoS .
QoS . (, UADP) IOS-XE QoS. , NBAR2 .
, SD-Access QoS .
4.6.3.
, (traffic engineering) .
, Policy Based Routing (PBR), MPLS Traffic Engineering (MPLS TE), SPAN ..
SD-Access Path Preference Traffic Copy Contracts, DNA Center .
4.7. ? ?
, -.
, . . Cisco, 85% , . , , . , . .
SD-Access DNA Center. , , . .
DNA Center , , . , .
, DNA Center .
SD-Access :
- .
- .
- -.
- -.
5.
The Cisco Software-Defined Access (SD-Access) factory is a new approach to building corporate networks and makes a big step forward compared to classic campus networks. In importance, this step can be compared with the transition from computers with a command line interface to computers with a graphical user interface.
The factory offers the IT service new powerful opportunities in the field of design, implementation, operation of the corporate network, implementation of policies, and troubleshooting. These capabilities enable IT to fulfill business requirements quickly and efficiently. It is possible to minimize the routine work, allocate more time to more strategic, important tasks that have higher value for the employer, as well as giving competitive advantages in the labor market.
Business, in turn, receives significant advantages in speed of implementation of initiatives and solving problems based on the network. Ultimately, this helps to expand the market share, increase revenue. Cisco SD-Access also offers businesses a significant reduction in the risks of business process disruptions associated with the "human factor" and a fundamentally new level of information security.
Links
- Learn more about the Cisco SD-Access solution.
- Webinar Cisco Software-Defined Access - a new architecture for Cisco corporate campus networks
- Webinar Cisco SD-Access Architecture for Wireless Corporate Networks
- Webinar How to deploy your corporate LAN / WLAN network within the Cisco SD-Access architecture? - Live solution demonstration
Source: https://habr.com/ru/post/340576/
All Articles