We need to go deeper: bypass the script that bypasses the adblock

A little Friday post. Recently, I noticed that there is an advertisement that immediately breaks through 2 (!) Extensions blocking it. And usually this is a very low-quality and intrusive advertisement. I decided to find out how it was, and maybe even try to overcome this rubbish. Who cares - please under the cat (carefully, a lot of pictures).
And what hinders that?
I am an ardent supporter of ad blocking. Especially - low quality. If I don’t want to watch ads on a specific site, then such ads are a waste of money for the advertiser (useless display), disrespect towards me, and zero profit for anyone at all. I will make a reservation right away - there are sites on which I deliberately cut down adbloki (the same habr, for example). These are sites that choose thematic advertising, and not “IPHONES FROM THE WAREHOUSE 70% DISCOUNT!”.
And here the other day on one friendly site for me (the news portal in my city) appears well sooo low-level advertising in the style of "electricians have been hiding for a long time - to save electricity you just have to ...". At first, I thought that they had been hacked, but then it turned out that the admin of this site just got involved in some kind of affiliate program that runs on top of the adblock. And not only that such an advertisement is just a shame, so she also broke the layout in some places. Close it has become a matter of principle.
Attempt 1 - stupid, or ...
... "pff, yes I'll write a custom filter for the adblock." We write the filter, save, test ... And the page then breaks, straight at all. And cosmetic filters (blocking by css) also do not work. How so? But, apparently, therefore, there was no such filter out of the box. As it turns out later, our “malware” is cunning and in-line, and chrome browsers do not allow extensions to block inline scripts. Well well…
')
Attempt 2 - change adblock
The word "adblock" has long become a household name, like a jeep or copier. So in fact, I don’t have adblock but ublock (I hope this will not be considered an advertisement?). Therefore, to begin with, we will test the work of various blockers from the issuance top, who promised to hide from sly-assured scripts, and even block them. Exhaust, in fact, it did not, and part of the advertising continued to creep in (although not all, but still).
Attempt 3 - look the enemy in the eye
And no, I do not mean the admin resource :) Let's get down to the most interesting. We climb to watch the source of the page, in the hope of finding our crap. And ... Bingo!
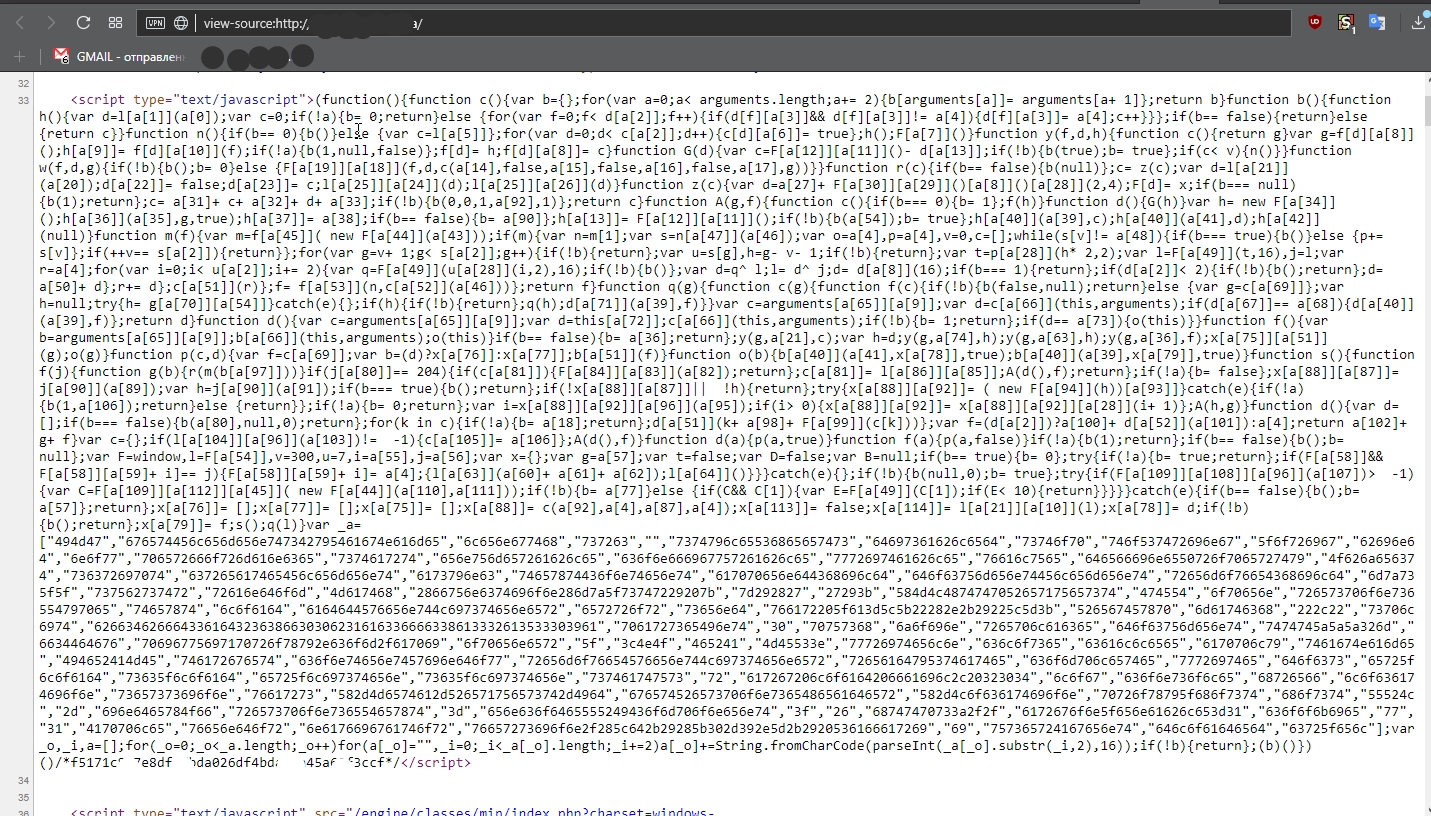
A huge obfuscated codin, which is clearly not surprising. We look at similar sites (in terms of advertising) - yes, this is clearly it. And obfustsirovanno soundly, not banal packer th.
Unpack a little to understand where the dog is buried. If you look at the monster, you will notice that this is a self-invoking function, within which there are three main parts - a large function, some kind of array with numbers and a small processing of it, and a call to the first function. Copy the array and its processing, run, look output.

The variable "a" we keep the entire set of words that could not be replaced with one-letter. And in the first part we see a lot of fragments of the form a [42], a [69], etc. Obfuscation was not so difficult. We make a replacement that does not guarantee us a working code, but it will greatly facilitate reading.

Already seen more or less readable code. We skip through the beautifier, and find the desired piece of code (I deleted the unimportant code to fit in one screenshot).
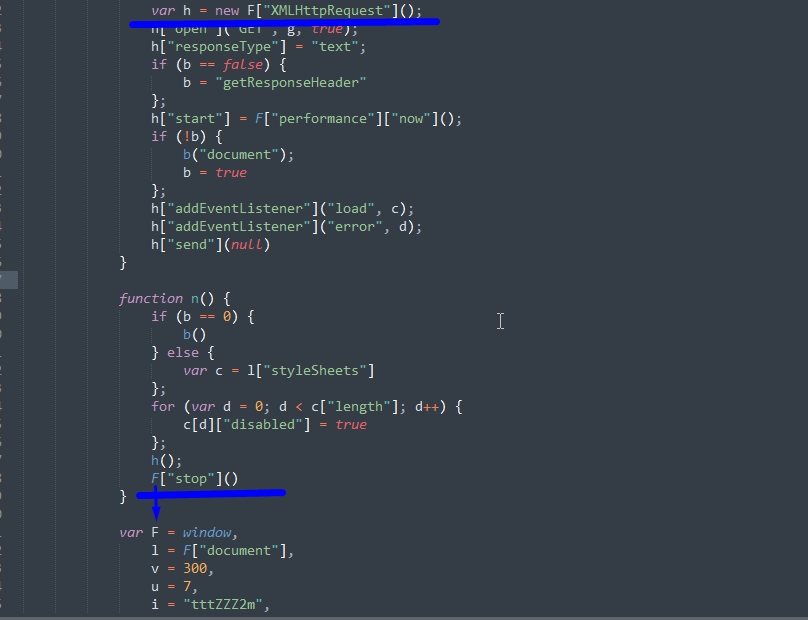
This infection makes a request for a specific legal entity, and in the case of a heap (falling into an adblock filter, for example), it calls window.stop (), which breaks the entire page. Pretty clever, and the built-in functionality of the adblock is, like, not solvable. And blocking the whole script does not allow chrome, for inline.
What to do?
After some thought, I got a browser extension (another one, yes, yes) that deals purely with blocking this advertisement. So far it has been sharpened specifically for this network, because I don’t know others. If anyone wants - fork, throw pull requests, or write in the comments - add a field to add your addresses.
It works as follows - we intercept a request for a “verification” address, with the help of
Expansion did not fill up anywhere, because you need a paid account, this is a proof-of-concept, today is Friday, and another 1000 and 1 minor excuse. So the githab code.
UPD. Questions have arisen in the comments, so the thesis is:
Why not block all inline scripts - because it will break the logic of many sites, does not fit
Why not return 200 (to deceive) - because chrome does not know how. Either 500 or skip
Why not redefine window.stop right away - because you need to catch a time when the DOM head block already exists, but the Ajax has not yet returned. This is an extensions API restriction.
Source: https://habr.com/ru/post/340562/
All Articles