IPSec between Cisco ISR and RUH2 3G router using dynamically allocated IP
Task. It is necessary to organize data exchange with remote networks, without resorting to the service of a cellular operator (hereinafter referred to as OpSoS) “Static white IP”, due to its high cost.
The diagram is shown in the following figure:

It is worth noting that the RUH2 router (manufactured by the Radiofid system company) is currently out of production, but since several of these routers are already involved in the organization of data exchange, I decided to optimize their work.
The router is based on Linux OS and for IPSec tunnels it has a Racoon module, which is configured via the web interface.
')
The enterprise LAN has a Cisco router (in my case CISCO1921 / K9) with a static external address (abcd).
For RUH2 devices, OpSoC issues dynamic addresses, each time a connection is established, it is not possible to know in advance from which address the connection will be established. Moreover, when restarting the router, this address is likely to be different.
In an IPSec session, device authentication can be performed using predefined keys, but since it is not known in advance what address the device will contact, it is necessary to write a line in the router like this:
Those. the key is valid for all addresses, and this is not safe, since if a key is compromised, an attacker can set up an encrypted channel and gain access to the enterprise network.
In this case, it is recommended to use X.509 certificates. It is necessary to configure a certificate authority on the router that will issue certificates for RUH2 routers. Strictly speaking, a certification authority may not necessarily be on a CISCO router, the main thing is for this center to issue certificates to devices for establishing a connection. Details on setting up a certification authority on CISCO routers can be found here .
To establish a connection on the router, you must configure the trustpoint, which will be issued a certificate by a certification authority. In enable mode, type the following command:
Where VPN-key is the name of the key pair to be used at the trustpoint, modulus 2048 is the key dimension.
Next, configure the trustpoint, give the command:
Next, the router enters the trustpoint configuration mode, in this mode we give the following commands:
The path to the certification authority to request a certificate and to check the list of revoked certificates.
Do not include the serial number of the router in the certificate.
Do not include a custom domain name in the certificate.
Do not include the router's IP address in the certificate.
The subject name of the certificate is specified according to the X.500 format. Description of some fields:
CN: Common Name - arbitrary name
O: Organization - the name of the organization
L: Location - location, city
C: Country - Country
Method for checking the list of revoked certificates.
How quickly you need to clear the cache after checking the list of revoked certificates.
The name of the key pair to use.
After these settings have been entered, it is necessary to exit the configuration mode of the trustpoint into the global configuration mode (exit) and give the command:
The CISCO router will request the root certificate of the certification server and will offer to confirm:
We answer yes, cisco will confirm that the root certificate is accepted:
Next, we will request the server to issue us a certificate:
During the request process, the router will request a password for the certificate and request confirmation. Enter the password (optional) and confirm the creation of the request.
After that, a request will appear on the certification server:
You can view the request on the certification server (if it is on CISCO) with the following command:
To confirm the issuance of a certificate, you must issue the following command:
After a while, trustpoint will automatically receive the issued certificate:
The next step is to issue a certificate to the RUH2 router, signed by the same certification authority.
Unlike CISCO, RUH2 is not able to automatically automatically request a certificate, so we’ll do it manually.
For all manipulations when creating a certificate for a router, I use the library utility OpenSSL.
First, create a private key:
The file private.key appeared in the c: \ keys folder with the following contents:
Further, on the basis of this key, we will create a request to a certification authority:
The OpenSSL utility will ask a series of questions regarding this certificate:
These fields are analogous to the fact that in cisco we set the subject in the trustpoint with the subject-name command.
After entering the values in the c: \ keys folder, a certificate request file appears as follows:
You need to copy it to the clipboard, and on the CISCO, where the certification authority is running, enter the command:
CISCO will issue a request
Next, you need to copy the request from the clipboard, at the end type quit
Now you can see the created query:
We will see a query with fields defined by the OpenSSL utility.
Confirm the issuance of a certificate for this request, the router will immediately issue it to us in the terminal window:
You need to copy the certificate to the clipboard and save it to a file. Attention: you need to copy everything, including the first and last lines, in which BEGIN CERTIFICATE and END CERTIFICATE are written.
You also need to request your own trustpoint certificate (in global configuration mode):
The router will issue the root certificate of the certification server and the trustpoint certificate. Each must be saved in a separate file.
Next, on the router with which you need to establish a connection (and where the trustpoint is configured), configure ipsec.
Everything is done in global configuration mode.
Set up the 1st phase:
The last command sets the type of certificate authentication, it acts by default and may not be displayed when viewing the configuration on the CISCO.
Create a certificate card. It is necessary to accept connections from devices with certain attributes of certificates:
The last line says that only certificates containing the string ruh2.esko.local correspond to this certificate card.
Create an isakmp profile.
Next, configure the 2nd phase:
The last command sets the tunnel mode and is the default command. It may not be displayed when viewing the router configuration.
Now create a dynamic crypto map:
Now let's link the dynamic crypto map to the static one:
And apply a static crypto card on the interface that looks towards the Internet:
The configuration of the cisco router is over. Getting started configuring RUH2. To do this, go to the web interface of the router, in the Configuration section, then in the IPSec section.
The settings are as follows:
After setting the settings, click Apply and check the established connection.
Check the 1st phase.
On CISCO we give the command
Among other things you can see:
In my case, RUH2 is visible from the Internet under the address 188.170.72.35.
Checking the 2nd phase
Check ping:
For ping use the internal interface, looking in the building. network.
This completes the configuration of the routers.
PS: Naturally, to pass IPSec traffic on the external interface, the appropriate protocols must be allowed and the ports open. In my case, this is done using the following access-list:
The diagram is shown in the following figure:

It is worth noting that the RUH2 router (manufactured by the Radiofid system company) is currently out of production, but since several of these routers are already involved in the organization of data exchange, I decided to optimize their work.
The router is based on Linux OS and for IPSec tunnels it has a Racoon module, which is configured via the web interface.
')
The enterprise LAN has a Cisco router (in my case CISCO1921 / K9) with a static external address (abcd).
For RUH2 devices, OpSoC issues dynamic addresses, each time a connection is established, it is not possible to know in advance from which address the connection will be established. Moreover, when restarting the router, this address is likely to be different.
In an IPSec session, device authentication can be performed using predefined keys, but since it is not known in advance what address the device will contact, it is necessary to write a line in the router like this:
crypto isakmp key cisco123 address 0.0.0.0 0.0.0.0 no-xauthThose. the key is valid for all addresses, and this is not safe, since if a key is compromised, an attacker can set up an encrypted channel and gain access to the enterprise network.
In this case, it is recommended to use X.509 certificates. It is necessary to configure a certificate authority on the router that will issue certificates for RUH2 routers. Strictly speaking, a certification authority may not necessarily be on a CISCO router, the main thing is for this center to issue certificates to devices for establishing a connection. Details on setting up a certification authority on CISCO routers can be found here .
To establish a connection on the router, you must configure the trustpoint, which will be issued a certificate by a certification authority. In enable mode, type the following command:
ESKO-main-gw(config)#crypto key generate rsa general-keys label VPN-key modulus 2048Where VPN-key is the name of the key pair to be used at the trustpoint, modulus 2048 is the key dimension.
Next, configure the trustpoint, give the command:
R1(config)#crypto pki trustpoint VPN-eskoNext, the router enters the trustpoint configuration mode, in this mode we give the following commands:
enrollment url http://abcd:80The path to the certification authority to request a certificate and to check the list of revoked certificates.
serial-number noneDo not include the serial number of the router in the certificate.
fqdn noneDo not include a custom domain name in the certificate.
ip-address noneDo not include the router's IP address in the certificate.
subject-name cn=ESKO-main-gw.esko.local,o=esko,l=spb,c=ruThe subject name of the certificate is specified according to the X.500 format. Description of some fields:
CN: Common Name - arbitrary name
O: Organization - the name of the organization
L: Location - location, city
C: Country - Country
revocation-check crlMethod for checking the list of revoked certificates.
crl cache delete-after 5How quickly you need to clear the cache after checking the list of revoked certificates.
rsakeypair VPN-keyThe name of the key pair to use.
After these settings have been entered, it is necessary to exit the configuration mode of the trustpoint into the global configuration mode (exit) and give the command:
R1(config)#crypto pki authenticate VPN-eskoThe CISCO router will request the root certificate of the certification server and will offer to confirm:
Certificate has the following attributes:
Fingerprint MD5: 4CDFCBCA 7807C4C9 5B054FA5 329301DB
Fingerprint SHA1: E0E35CC8 75C3639C 445D12D8 4BA298AB 2E4E7004
% Do you accept this certificate? [yes / no]:
We answer yes, cisco will confirm that the root certificate is accepted:
Trustpoint CA certificate accepted.
Next, we will request the server to issue us a certificate:
R1(config)#crypto pki enroll VPN-esko% Start certificate enrollment ...
% Create a challenge password. You will need to verbally provide this
password for your certificate.
For security reasons your password will not be saved in the configuration.
Please make a note of it.
Password:
Re-enter password:
% Cc = ESKO-main-gw.esko.local, o = esko, l = spb, c = ru
% The fully qualified domain name is not included in the certificate
Request certificate from CA? [yes / no]: yes
% Certificate request sent to Certificate Authority
% The 'show crypto pki certificate verbose VPN-esko' commandwill show the fingerprint.
During the request process, the router will request a password for the certificate and request confirmation. Enter the password (optional) and confirm the creation of the request.
After that, a request will appear on the certification server:
* Oct 15 13: 53: 45.367: CRYPTO_PKI: Certificate Request Fingerprint MD5: F70432EB 59E791A6 48F301C4 B59C67EB
* Oct 15 13: 53: 45.371: CRYPTO_PKI: Certificate Request Fingerprint SHA1: 18AA1D1A 1DD7BED2 FEA666FF 1D32F8BA B559FA07
You can view the request on the certification server (if it is on CISCO) with the following command:
R1#sh crypto pki server CA-eskoEnrollment Request Database:
Subordinate CA certificate requests:
ReqID State Fingerprint SubjectName
- RA certificate requests:
ReqID State Fingerprint SubjectName
- Router certificates requests:
ReqID State Fingerprint SubjectName
- 1 pending F70432EB59E791A648F301C4B59C67EB cn = ESKO-main-gw.esko.local, o = esko, l = spb, c = ru
To confirm the issuance of a certificate, you must issue the following command:
R1#crypto pki server CA-esko grant 1After a while, trustpoint will automatically receive the issued certificate:
* Oct 15 14: 03: 01.303:% PKI-6-CERTRET: Certificate received from Certificate Authority
The next step is to issue a certificate to the RUH2 router, signed by the same certification authority.
Unlike CISCO, RUH2 is not able to automatically automatically request a certificate, so we’ll do it manually.
For all manipulations when creating a certificate for a router, I use the library utility OpenSSL.
First, create a private key:
C:\OpenSSL\bin>Openssl genrsa -out c:\keys\private.key 2048Generating RSA private key, 2048 bit long modulus
.................................................. .......... +++
.................................................. .................................................. .................................................. ........... +++
e is 65537 (0x10001)
The file private.key appeared in the c: \ keys folder with the following contents:
----- BEGIN RSA PRIVATE KEY -----
MIIEogIBAAKCAQEAz1vjlthggHHmSBWVgcNf7aDDGPgik9xKZuJjEBgREr8x5RUa
...
GzmSg7cOhrzzTBWOUqTggMD5uKV4Cgei3cA + TKRXv2dRjfVCL3s =
----- END RSA PRIVATE KEY -----
Further, on the basis of this key, we will create a request to a certification authority:
C:\OpenSSL\bin>openssl.exe req -new -key c:\keys\private.key -out c:\keys\request.csr
The OpenSSL utility will ask a series of questions regarding this certificate:
You are included
into your certificate request.
What is a Distinguished Name or a DN?
You can leave some blank
For some fields there will be a default value,
If you enter '.', The field will be left blank.
- Country Name (2 letter code) [RU]:
State or Province Name (full name) []:
City [SPB]:
Organization Name (eg, company) [ESKO]:
Organizational Unit Name (eg, section) []:
Common Name []: RUH2.esko.local
email []:
Please enter the following extra attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
These fields are analogous to the fact that in cisco we set the subject in the trustpoint with the subject-name command.
After entering the values in the c: \ keys folder, a certificate request file appears as follows:
----- BEGIN CERTIFICATE REQUEST -----
MIICiTCCAXECAQAwRDELMAkGA1UEBhMCUlUxDDAKBgNVBAcMA1NQQjENMAsGA1UE
...
Q3H / EtMGltY1QS / 9DsEnta + k7oCKPTeei3S2v9Y =
----- END CERTIFICATE REQUEST -----
You need to copy it to the clipboard, and on the CISCO, where the certification authority is running, enter the command:
R1#crypto pki server CA-esko request pkcs10 terminal
CISCO will issue a request
PKCS10 request in base64 or pem
% Enter Base64 encoded or PEM formatted PKCS10 enrollment request.
% End with a blank line or "quit" on a line by itself.
Next, you need to copy the request from the clipboard, at the end type quit
Now you can see the created query:
R1#sh crypto pki server CA-esko requestsEnrollment Request Database:
Subordinate CA certificate requests:
ReqID State Fingerprint SubjectName
- RA certificate requests:
ReqID State Fingerprint SubjectName
- Router certificates requests:
ReqID State Fingerprint SubjectName
- 2 pending 4468493FA262890CC75EEF18AC5AF6DF cn = RUH2.esko.local, o = ESKO, l = SPB, c = RU
We will see a query with fields defined by the OpenSSL utility.
Confirm the issuance of a certificate for this request, the router will immediately issue it to us in the terminal window:
R1#crypto pki server CA-esko grant 2% Granted certificate:
----- BEGIN CERTIFICATE -----
MIIEQjCCAiqgAwIBAgIBAzANBgkqhkiG9w0BAQQFADBBMQswCQYDVQQGEwJydTEM
...
jhHvAo / 0oVfLPZ9dPdj9Y1efawXI4a / zGf0GTmEi + v7d8Psl9Wk =
----- END CERTIFICATE -----
You need to copy the certificate to the clipboard and save it to a file. Attention: you need to copy everything, including the first and last lines, in which BEGIN CERTIFICATE and END CERTIFICATE are written.
You also need to request your own trustpoint certificate (in global configuration mode):
R1(config)#crypto pki export VPN-esko pem terminal% CA certificate:
----- BEGIN CERTIFICATE -----
MIIFYDCCA0igAwIBAgIBATANBgkqhkiG9w0BAQQFADBBMQswCQYDVQQGEwJydTEM
...
uQVU8GLro73NQ9Jo2JXt2qfZY9SFsomiqJugxReyM4umZ9oX
----- END CERTIFICATE -----
% General Purpose Certificate:
----- BEGIN CERTIFICATE -----
MIIEVzCCAj + gAwIBAgIBAjANBgkqhkiG9w0BAQUFADBBMQswCQYDVQQGEwJydTEM
...
a0G + T + rXEYq2ywc =
----- END CERTIFICATE -----
The router will issue the root certificate of the certification server and the trustpoint certificate. Each must be saved in a separate file.
Next, on the router with which you need to establish a connection (and where the trustpoint is configured), configure ipsec.
Everything is done in global configuration mode.
Set up the 1st phase:
crypto isakmp policy 30
encr aes
hash sha256
group 14
lifetime 3600
authentication rsa-sigThe last command sets the type of certificate authentication, it acts by default and may not be displayed when viewing the configuration on the CISCO.
Create a certificate card. It is necessary to accept connections from devices with certain attributes of certificates:
crypto pki certificate map RUH2-cert-map 10
subject-name co ruh2.esko.localThe last line says that only certificates containing the string ruh2.esko.local correspond to this certificate card.
Create an isakmp profile.
crypto isakmp profile RUH2-isapr
self-identity address
ca trust-point VPN-esko
match certificate RUH2-cert-map
local-address GigabitEthernet0/0Description of the commands used
The router ID will be the IP address.
Trustpoint used for authentication
Indicates a certificate map to determine the devices with which to establish a connection.
Clarifying command to determine the IP address of the CISCO router
self-identity addressThe router ID will be the IP address.
ca trust-point VPN-eskoTrustpoint used for authentication
match certificate RUH2-cert-mapIndicates a certificate map to determine the devices with which to establish a connection.
local-address GigabitEthernet0/0
Clarifying command to determine the IP address of the CISCO router
Next, configure the 2nd phase:
R1(config)#crypto ipsec transform-set RUH2-ts esp-aes esp-sha-hmac
R1 (cfg-crypto-trans)#mode tunnelThe last command sets the tunnel mode and is the default command. It may not be displayed when viewing the router configuration.
Now create a dynamic crypto map:
crypto dynamic-map RUH2-dyncm 1000
set security-association lifetime seconds 28800
set transform-set RUH2-ts
set pfs group2
set isakmp-profile RUH2-isapr
reverse-routeDescription of the commands used
set security-association lifetime seconds 28800
Establishing the lifetime of the session of the 2nd phase, i.e. how often the encryption key will change.
Indicates transform-set, i.e. how to encrypt traffic
For more security. Not mandatory. Indicates an additional encryption key generation mode.
Indicates which isakmp profile to use.
An important team. The router will add a route to the routing table to send packets to the remote network.
Establishing the lifetime of the session of the 2nd phase, i.e. how often the encryption key will change.
set transform-set RUH2-tsIndicates transform-set, i.e. how to encrypt traffic
set pfs group2For more security. Not mandatory. Indicates an additional encryption key generation mode.
set isakmp-profile RUH2-isaprIndicates which isakmp profile to use.
reverse-routeAn important team. The router will add a route to the routing table to send packets to the remote network.
Now let's link the dynamic crypto map to the static one:
R1(config)#crypto map ISP-statcm 500 ipsec-isakmp dynamic RUH2-dyncm
And apply a static crypto card on the interface that looks towards the Internet:
R1(config)#interface GigabitEthernet0/0
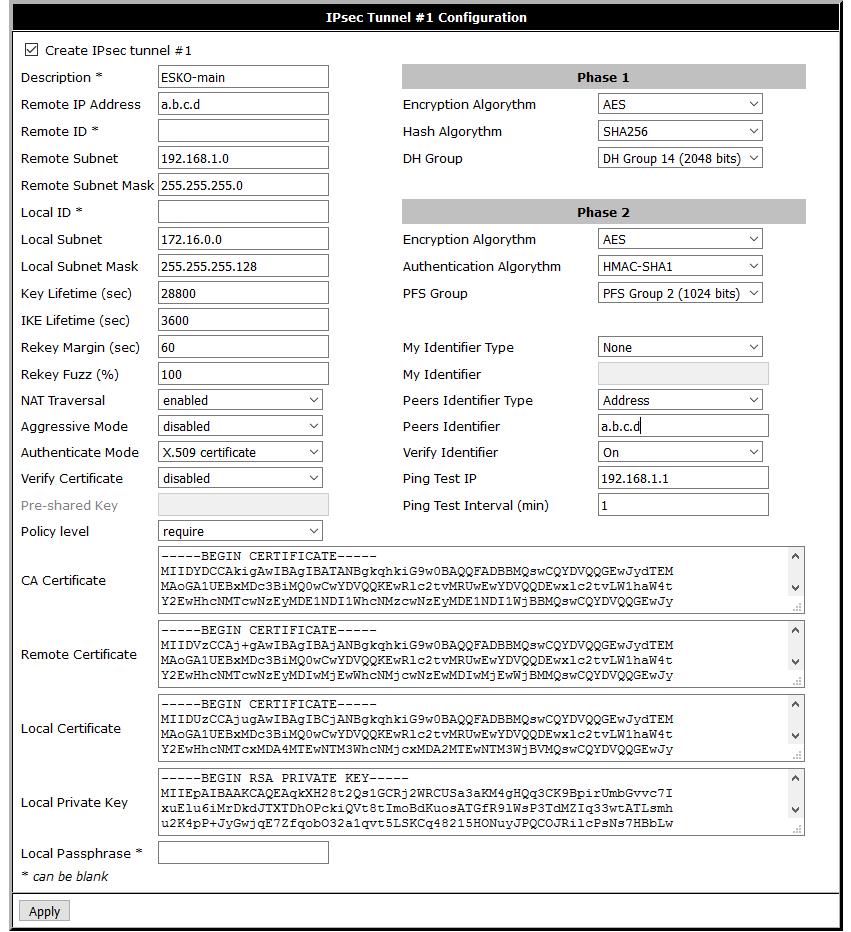
R1(config-if)#crypto map ISP-statcmThe configuration of the cisco router is over. Getting started configuring RUH2. To do this, go to the web interface of the router, in the Configuration section, then in the IPSec section.
The settings are as follows:

Description of the fields specified in the router
Description
The name of the tunnel. Maybe any.
Remote IP Address
Address of the CISCO remote router.
Remote Subnet and Remote Subnet Mask
Indicates the traffic for which network will be sent to the tunnel.
Local Subnet and Local Subnet Mask
This information RUH2 transmits to a remote CISCO router, so that he understands what traffic should be sent to the tunnel.
Key Lifetime (sec)
The key's “lifetime” is what the CISCO is set by the parameter set security-association lifetime seconds.
IKE Lifetime (sec)
The lifetime of the 1st phase (isakmp), what on CISCO is set by the lifetime parameter in the isakmp policy.
NAT Traversal
Enables the NAT-T mode, which is required if RUH2 works for the OPCoC NAT.
Authenticate Mode
Authentication method. Select the mode of X.509 certificates.
Verify Certificate
Certificate verification mode. Need to disable. Otherwise, RUH2 gives errors about the absence of the AltSubjectName field, and it can be specified in CISCO only in the self-signed trustpoint. In turn, you cannot use self-signed trustpoint, because it is necessary that all certificates were issued by one certificate authority.
Encryption Algorythm
Hash algorythm
DH Group
The settings of the 1st phase on RUH2, should coincide with the settings of the isakmp policy in CISCO.
Encryption Algorythm
Authentication Algorythm
PFS Group
The settings for Phase 2 on RUH2 should match the settings of the transform-set and pfs group in the CISCO.
My Identifier Type
Indicates how to identify RUH2 on the remote side, does not matter, because There is a certificate verification.
Peers Identifier Type
Indicates how to identify the remote side. Use the IP address of the CISCO router.
Verify Identifier
Indicates whether to validate the remote side. Can be enabled for more security.
Ping Test IP and Ping Test Interval (min)
It is important to include, because A tunnel is created if there is traffic, and CISCO cannot initiate a connection if there is traffic on the network, because RUH2 has a dynamic IP address.
CA Certificate
The certificate of the certificate authority must be copied from the saved file.
Remote Certificate
The trustpoint certificate of the remote router must be copied from the saved file.
Local Certificate
Certificate RUH2 issued by a certificate authority must be copied from a saved file.
Local private key
The private key must be copied from the saved file.
The name of the tunnel. Maybe any.
Remote IP Address
Address of the CISCO remote router.
Remote Subnet and Remote Subnet Mask
Indicates the traffic for which network will be sent to the tunnel.
Local Subnet and Local Subnet Mask
This information RUH2 transmits to a remote CISCO router, so that he understands what traffic should be sent to the tunnel.
Key Lifetime (sec)
The key's “lifetime” is what the CISCO is set by the parameter set security-association lifetime seconds.
IKE Lifetime (sec)
The lifetime of the 1st phase (isakmp), what on CISCO is set by the lifetime parameter in the isakmp policy.
NAT Traversal
Enables the NAT-T mode, which is required if RUH2 works for the OPCoC NAT.
Authenticate Mode
Authentication method. Select the mode of X.509 certificates.
Verify Certificate
Certificate verification mode. Need to disable. Otherwise, RUH2 gives errors about the absence of the AltSubjectName field, and it can be specified in CISCO only in the self-signed trustpoint. In turn, you cannot use self-signed trustpoint, because it is necessary that all certificates were issued by one certificate authority.
Encryption Algorythm
Hash algorythm
DH Group
The settings of the 1st phase on RUH2, should coincide with the settings of the isakmp policy in CISCO.
Encryption Algorythm
Authentication Algorythm
PFS Group
The settings for Phase 2 on RUH2 should match the settings of the transform-set and pfs group in the CISCO.
My Identifier Type
Indicates how to identify RUH2 on the remote side, does not matter, because There is a certificate verification.
Peers Identifier Type
Indicates how to identify the remote side. Use the IP address of the CISCO router.
Verify Identifier
Indicates whether to validate the remote side. Can be enabled for more security.
Ping Test IP and Ping Test Interval (min)
It is important to include, because A tunnel is created if there is traffic, and CISCO cannot initiate a connection if there is traffic on the network, because RUH2 has a dynamic IP address.
CA Certificate
The certificate of the certificate authority must be copied from the saved file.
Remote Certificate
The trustpoint certificate of the remote router must be copied from the saved file.
Local Certificate
Certificate RUH2 issued by a certificate authority must be copied from a saved file.
Local private key
The private key must be copied from the saved file.
After setting the settings, click Apply and check the established connection.
Check the 1st phase.
On CISCO we give the command
R1#sh crypto isakmp saAmong other things you can see:
abcd 188.170.72.35 QM_IDLE 1014 ACTIVE
In my case, RUH2 is visible from the Internet under the address 188.170.72.35.
Checking the 2nd phase
R1#sh crypto ipsec sa interface g0/0results
interface: GigabitEthernet0 / 0
Crypto map tag: ISP-statcm, local addr abcd
protected vrf: (none)
local ident (addr / mask / prot / port): (192.168.1.0/255.255.255.0/0/0)
remote ident (addr / mask / prot / port): (172.16.0.0/255.255.255.128/0/0)
current_peer 188.170.72.35 port 48015
PERMIT, flags = {}
#pkts encaps: 133, #pkts encrypt: 133, #pkts digest: 133
#pkts decaps: 135, #pkts decrypt: 135, #pkts verify: 135
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 8
local crypto endpt .: abcd, remote crypto endpt .: 188.170.72.35
path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0 / 0
current outbound spi: 0xEC8D5EF (248042991)
PFS (Y / N): Y, DH group: group2
inbound esp sas:
spi: 0x1231809D (305234077)
transform: esp-aes esp-sha-hmac,
in use settings = {Tunnel UDP-Encaps,}
conn id: 2019, flow_id: Onboard VPN: 19, sibling_flags 80000046, crypto map: ISP-statcm
sa timing: remaining key lifetime (k / sec): (4506190/27680)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xEC8D5EF (248042991)
transform: esp-aes esp-sha-hmac,
in use settings = {Tunnel UDP-Encaps,}
conn id: 2020, flow_id: Onboard VPN: 20, sibling_flags 80000046, crypto map: ISP-statcm
sa timing: remaining key lifetime (k / sec): (4506229/27680)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
Checking the routing table:
R1 # sh ip route
Among other things, there are such lines:
172.16.0.0/25 is subnetted, 1 subnets
S 172.16.0.0 [1/0] via 188.170.72.35
Check ping:
R1#ping 172.16.0.1 source g0/1Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.0.1, timeout is 2 seconds:
Packet sent with a source address of 192.168.1.1
!!!
Success rate is 100 percent (5/5), round-trip min / avg / max = 324/357/388 ms
For ping use the internal interface, looking in the building. network.
This completes the configuration of the routers.
PS: Naturally, to pass IPSec traffic on the external interface, the appropriate protocols must be allowed and the ports open. In my case, this is done using the following access-list:
ip access-list extended IPSEC-acl
permit esp any any
permit ahp any any
permit udp host abcd eq isakmp any
permit udp host abcd eq non500-isakmp any
permit udp any host abcd eq isakmp
permit udp any host abcd eq non500-isakmp
Source: https://habr.com/ru/post/340340/
All Articles