BlackOasis APT: a new campaign with a new zerodem
We at Kaspersky Lab work closely with third-party software developers. As soon as we find another vulnerability, we immediately inform the manufacturer to close the hole in hot pursuit. And on October 10, 2017, our system to counter the exploit discovered a new zerodey for Adobe Flash, which was used to attack our customers.
The exploit was delivered to the victim through a Microsoft Office document, and its ultimate goal was to install the latest version of the FinSpy Trojan. We reported a bug in Adobe, which assigned it the index CVE-2017-11292 and just yesterday rolled out the patch .

')
So far, we have seen only one use of the exploit against our clients, from which we can conclude that it is used in piece target attacks.
After analyzing the malware involved in this attack, we discovered its clear connection with the group we call BlackOasis. We are confident that this team is behind attacks using another zerodey (CVE-2017-8759), discovered by FireEye in September 2017. The FinSpy Trojan, involved in the new attack via CVE-2017-11292, accesses the same control server as the Trojan downloaded via CVE-2017-8759.
For the first time, BlackOasis activity was recorded by us in May 2016, during the study of another zerodey for Adobe Flash. On May 10, Adobe announced a CVE-2016-4117 vulnerability affecting Flash Player version 21.0.0.226 and earlier versions for Windows, Macintosh, Linux and Chrome OS. As it turned out, this hole was actively used by hackers.
Our researchers have found a sample that exploits this vulnerability. The caught sample was downloaded to the multiscanner service on May 8, 2016. The sample, in the form of an RTF file, used CVE-2016-4117 to download and install the program from a remote server. And on the server of this program is no longer there, but there were many installers FinSpy.
After digging into the data from the Kaspersky Security Network, our analysts identified two similar use cases of the exploit group (at that time - zerodeev) applied by BlackOasis in June 2015. These are CVE-2015-5119 and CVE-2016-0984, which were patched in June 2015 and February 2016, respectively. They also led to the installation of FinSpy.
Having discovered the network of exploits created by BlackOasis, we began to monitor their activities in order to better understand tactics and the choice of targets. Since then, we have seen a couple dozen attacks from this group.
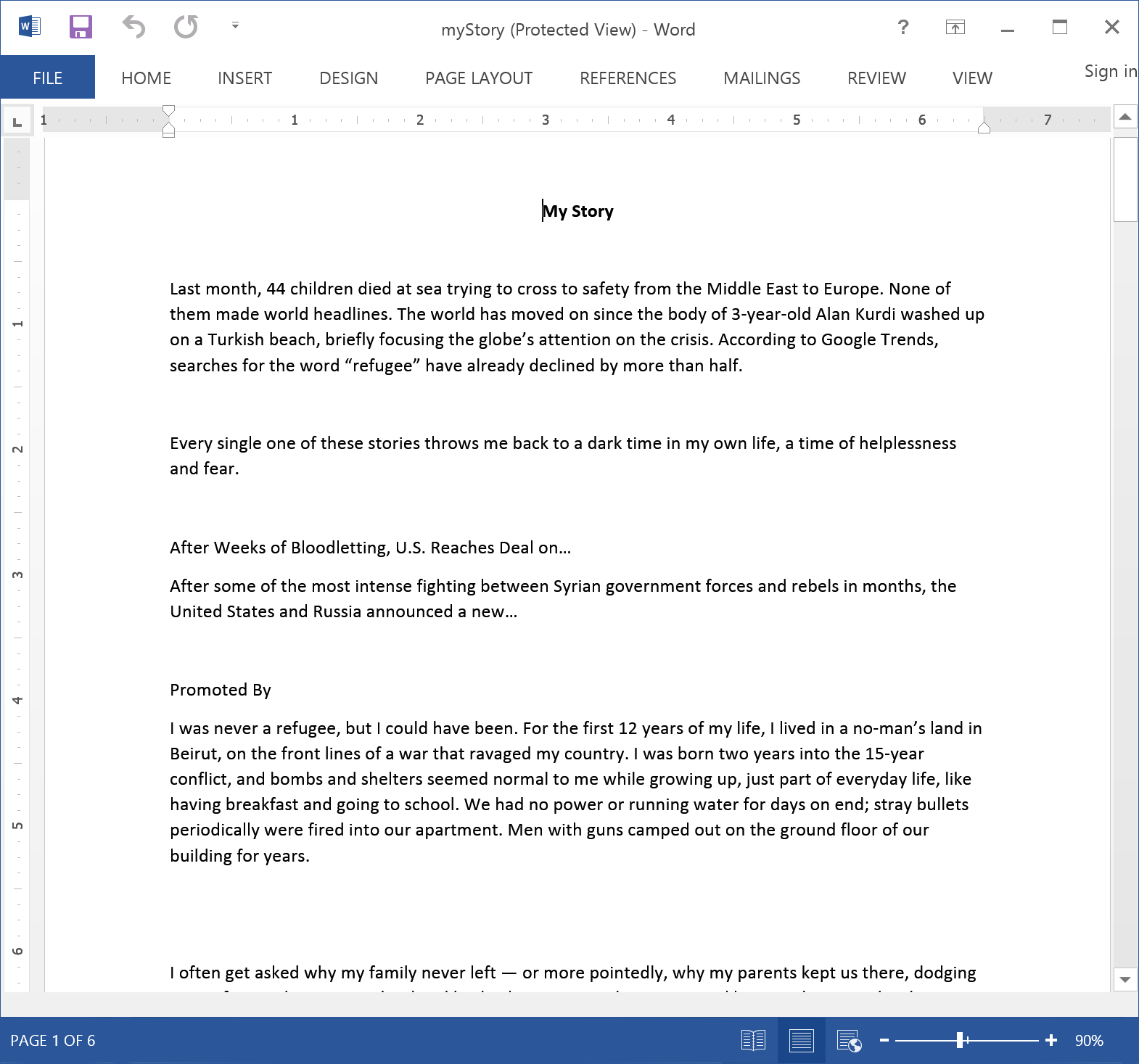
Here are some documents used as bait, for example:
As a result, we observed how BlackOasis applied at least 5 zerodeev since June 2015:
The attack begins with delivery to the victim of the Office document, in this case, presumably via email. The document contains an ActiveX object containing an exploit for Flash.
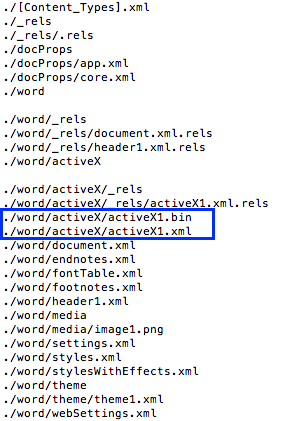
Flash object in .docx file saved in uncompressed format
The Flash object contains ActionScript, which extracts the exploit using a self-made wrapper.
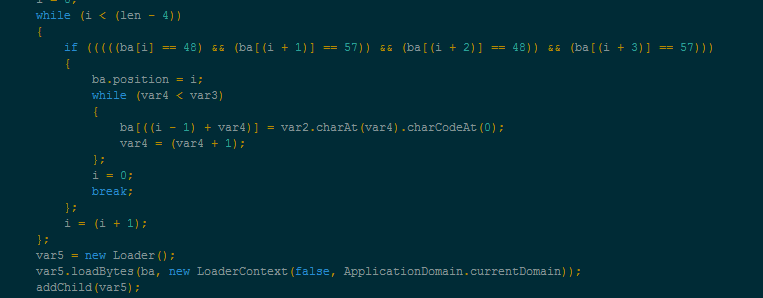
Unpacking procedures for SWF-exploit
The exploit exploits a memory corruption vulnerability found in the class “com.adobe.tvsdk.mediacore.BufferControlParameters”. If the exploit worked, it gets read and write access to the memory, which allows you to run the shellcode for the second stage of the attack.
The first stage shell code contains an interesting set of NOP instructions, interspersed with other instructions. Most likely, this is done in order to avoid antivirus detection, which is triggered by large blocks of NOP instructions inside flash files.
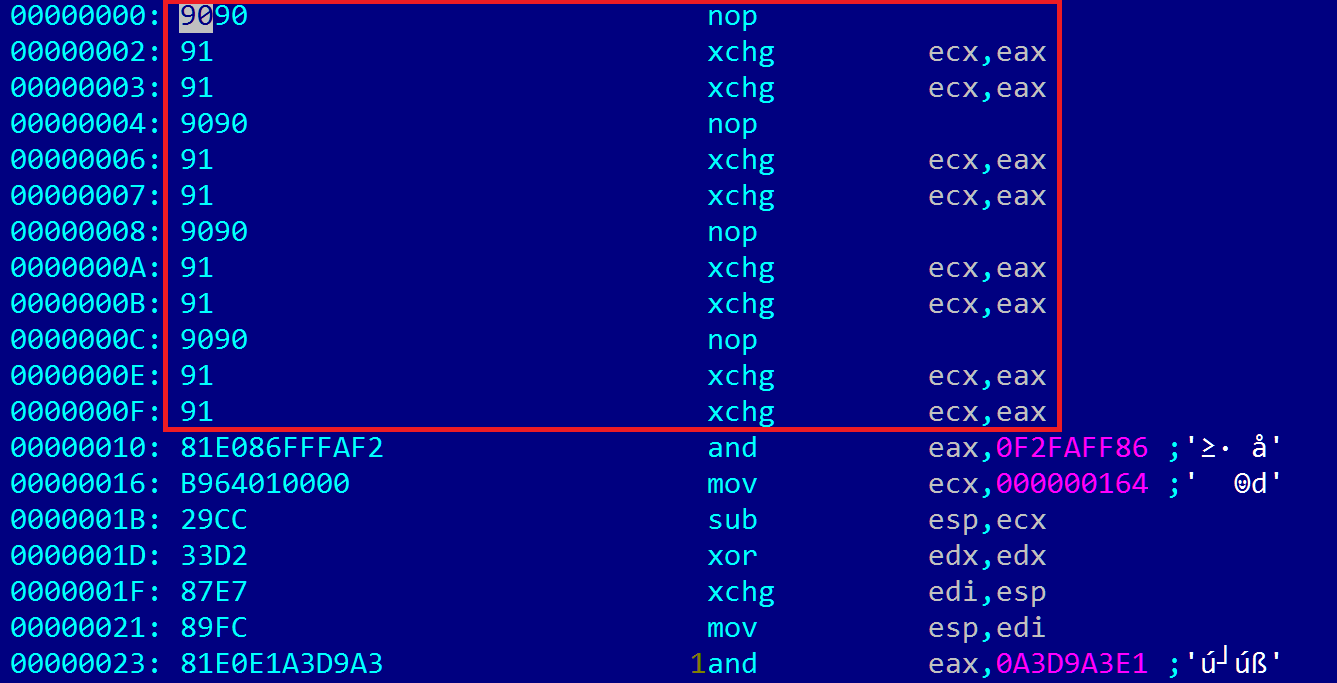
NOP array of instructions 0x90 and 0x91
The primary task of the initial shell code is to download the second stage shell code from the server hxxp: //89.45.67 [.] 107 / rss / 5uzosoff0u.iaf.

Shell code of the second stage
Shell code of the second stage of the attack performs the following actions:
As already mentioned, inside mo.exe (MD5: 4a49135d2ecc07085a8b7c5925a36c0a) is the latest version of the FinSpy Trojan from Gamma International. It is usually sold to government agencies and is used to legally monitor suspects. The latest version is filled with anti-analytic tricks, including a homemade packer and a virtual machine for executing code, which makes analysis very difficult.
The virtual machine P-code is packed using aPLib.

Part of the packaged P-code
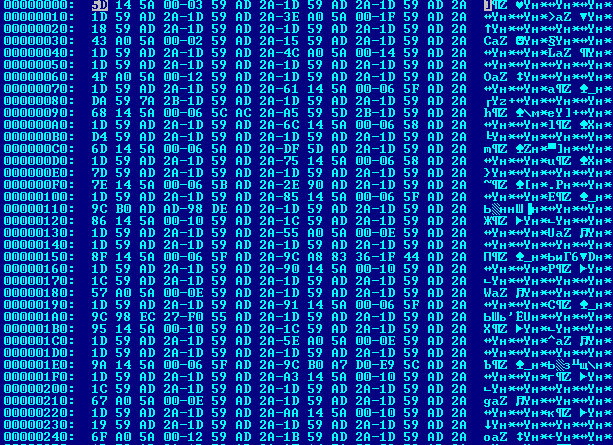
Uncompressed P-code
After unpacking the virtual machine, the P-code is decrypted:

Decrypted P-code
The virtual machine used in the Trojan supports 34 instructions:

An example of an interpreted P-code
In this example, the instruction “1b” starts the native code placed in the parameter field.
As soon as the malware is successfully launched, it continues to copy files along these paths:
“AdapterTroubleshooter.exe” —a completely legitimate binary that is used for an attack like Search Order Highjacking — slips a maliciously crafted DLL module with the name of the present. “D3d9.dll” is a malicious module that injects FinSpy into the Winlogon process.
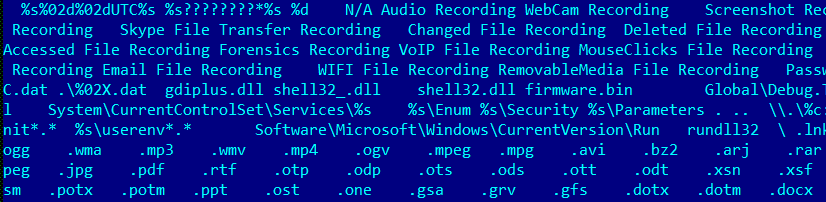
Part of the code embedded in the winlogon process
The malware then accesses the three management servers for new instructions and for sending the extracted data. Two of them have already been used before when using FinSpy. One - most recently, in September, in the attack described by FireEye, using CVE-2017-8759. The IP addresses of these servers and the malware samples are closely related to the part of BlackOasis that is tied to using FinSpy.
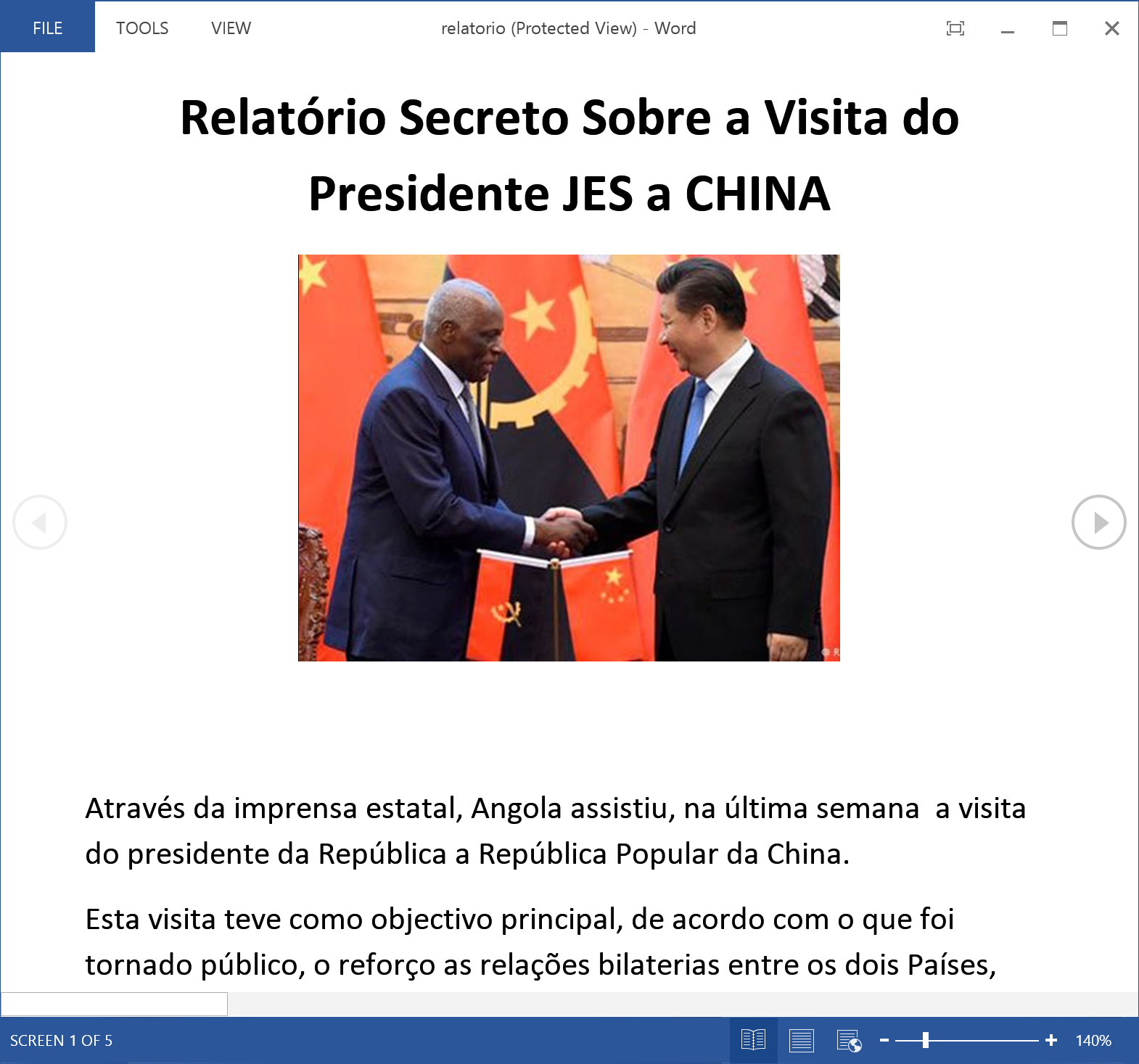
The interests of BlackOasis are very broad - the group is interested in figures involved in Middle Eastern politics and organizations that have weight in this region. Among their goals are prominent UN figures, opposition bloggers, political activists and regional journalists. In 2016, we also noted BlackOasis’s particular interest in Angola. This was clearly visible from the bait documents used in the attacks: they were intended for purposes allegedly related to oil, money laundering and other illegal activities. In addition, BlackOasis was interested in international activists and research centers.
The geography of interests of BlackOasis is very extensive. Their victims are in Russia, Iraq, Afghanistan, Nigeria, Libya, Jordan, Tunisia, Saudi Arabia, Iran, the Netherlands, Bahrain, Great Britain and Angola.
We believe that the attack on HackingTeam in mid-2015 led to a shortage of surveillance tools in the market, and this gap is now being filled by other companies. One of them is Gamma International, which offers customers a package of FinFisher tools. However, Gamma International itself was also hacked in 2014 by the same hacker named Phineas Fisher, although then the consequences were not as serious as in the case of the Hacking Team. In addition, Gamma International had two years to recover from the attack. Apparently, the number of attacks using FinFisher and zero-day vulnerabilities will continue to grow.
How to do and how to protect against such attacks?
In the case of CVE-2017-11292 and similar vulnerabilities, it is possible at the level of your organization to use the Killbit technology to block Flash elements in specific applications. Unfortunately, it’s not so simple to do this at the system level: potentially Flash objects can be loaded via applications that Killbit cannot stop. In addition, sometimes quite necessary tools depend on Flash, which as a result of blocking can also become inoperative. In addition, there are no guarantees that BlackOasis will not switch to the use of exploits for other software products.
It is best to apply a multi-level approach using access policies, antiviruses, network monitoring, and white lists. Our products detect BlackOasis tools as PDM: Exploit.Win32.Generic, HEUR: Exploit.SWF.Generic and HEUR: Exploit.MSOffice.Generic.
Infection Indicators:
4a49135d2ecc07085a8b7c5925a36c0a
89.45.67 [.] 107
Many thanks to the Adobe Product Security Incident Response Team (PSIRT) for helping to analyze the vulnerability and fix it quickly.
The exploit was delivered to the victim through a Microsoft Office document, and its ultimate goal was to install the latest version of the FinSpy Trojan. We reported a bug in Adobe, which assigned it the index CVE-2017-11292 and just yesterday rolled out the patch .

')
So far, we have seen only one use of the exploit against our clients, from which we can conclude that it is used in piece target attacks.
After analyzing the malware involved in this attack, we discovered its clear connection with the group we call BlackOasis. We are confident that this team is behind attacks using another zerodey (CVE-2017-8759), discovered by FireEye in September 2017. The FinSpy Trojan, involved in the new attack via CVE-2017-11292, accesses the same control server as the Trojan downloaded via CVE-2017-8759.
BlackOasis History
For the first time, BlackOasis activity was recorded by us in May 2016, during the study of another zerodey for Adobe Flash. On May 10, Adobe announced a CVE-2016-4117 vulnerability affecting Flash Player version 21.0.0.226 and earlier versions for Windows, Macintosh, Linux and Chrome OS. As it turned out, this hole was actively used by hackers.
Our researchers have found a sample that exploits this vulnerability. The caught sample was downloaded to the multiscanner service on May 8, 2016. The sample, in the form of an RTF file, used CVE-2016-4117 to download and install the program from a remote server. And on the server of this program is no longer there, but there were many installers FinSpy.
After digging into the data from the Kaspersky Security Network, our analysts identified two similar use cases of the exploit group (at that time - zerodeev) applied by BlackOasis in June 2015. These are CVE-2015-5119 and CVE-2016-0984, which were patched in June 2015 and February 2016, respectively. They also led to the installation of FinSpy.
Having discovered the network of exploits created by BlackOasis, we began to monitor their activities in order to better understand tactics and the choice of targets. Since then, we have seen a couple dozen attacks from this group.
Here are some documents used as bait, for example:


As a result, we observed how BlackOasis applied at least 5 zerodeev since June 2015:
- CVE-2015-5119 - June 2015
- CVE-2016-0984 - July 2015
- CVE-2016-4117 - May 2016
- CVE-2017-8759 - September 2017
- CVE-2017-11292 - October 2017
Attacks using CVE-2017-11292
The attack begins with delivery to the victim of the Office document, in this case, presumably via email. The document contains an ActiveX object containing an exploit for Flash.


Flash object in .docx file saved in uncompressed format
The Flash object contains ActionScript, which extracts the exploit using a self-made wrapper.

Unpacking procedures for SWF-exploit
The exploit exploits a memory corruption vulnerability found in the class “com.adobe.tvsdk.mediacore.BufferControlParameters”. If the exploit worked, it gets read and write access to the memory, which allows you to run the shellcode for the second stage of the attack.
The first stage shell code contains an interesting set of NOP instructions, interspersed with other instructions. Most likely, this is done in order to avoid antivirus detection, which is triggered by large blocks of NOP instructions inside flash files.

NOP array of instructions 0x90 and 0x91
The primary task of the initial shell code is to download the second stage shell code from the server hxxp: //89.45.67 [.] 107 / rss / 5uzosoff0u.iaf.

Shell code of the second stage
Shell code of the second stage of the attack performs the following actions:
- Downloads FinSpy at hxxp: //89.45.67 [.] 107 / rss / mo.exe
- From the same IP downloads the bait document.
- Runs the Trojan and displays the document.
Malicious load mo.exe
As already mentioned, inside mo.exe (MD5: 4a49135d2ecc07085a8b7c5925a36c0a) is the latest version of the FinSpy Trojan from Gamma International. It is usually sold to government agencies and is used to legally monitor suspects. The latest version is filled with anti-analytic tricks, including a homemade packer and a virtual machine for executing code, which makes analysis very difficult.
The virtual machine P-code is packed using aPLib.

Part of the packaged P-code

Uncompressed P-code
After unpacking the virtual machine, the P-code is decrypted:

Decrypted P-code
The virtual machine used in the Trojan supports 34 instructions:

An example of an interpreted P-code
In this example, the instruction “1b” starts the native code placed in the parameter field.
As soon as the malware is successfully launched, it continues to copy files along these paths:
- C: \ ProgramData \ ManagerApp \ AdapterTroubleshooter.exe
- C: \ ProgramData \ ManagerApp \ 15b937.cab
- C: \ ProgramData \ ManagerApp \ install.cab
- C: \ ProgramData \ ManagerApp \ msvcr90.dll
- C: \ ProgramData \ ManagerApp \ d3d9.dll
“AdapterTroubleshooter.exe” —a completely legitimate binary that is used for an attack like Search Order Highjacking — slips a maliciously crafted DLL module with the name of the present. “D3d9.dll” is a malicious module that injects FinSpy into the Winlogon process.

Part of the code embedded in the winlogon process
The malware then accesses the three management servers for new instructions and for sending the extracted data. Two of them have already been used before when using FinSpy. One - most recently, in September, in the attack described by FireEye, using CVE-2017-8759. The IP addresses of these servers and the malware samples are closely related to the part of BlackOasis that is tied to using FinSpy.
BlackOasis Victims and Goals
The interests of BlackOasis are very broad - the group is interested in figures involved in Middle Eastern politics and organizations that have weight in this region. Among their goals are prominent UN figures, opposition bloggers, political activists and regional journalists. In 2016, we also noted BlackOasis’s particular interest in Angola. This was clearly visible from the bait documents used in the attacks: they were intended for purposes allegedly related to oil, money laundering and other illegal activities. In addition, BlackOasis was interested in international activists and research centers.
The geography of interests of BlackOasis is very extensive. Their victims are in Russia, Iraq, Afghanistan, Nigeria, Libya, Jordan, Tunisia, Saudi Arabia, Iran, the Netherlands, Bahrain, Great Britain and Angola.
findings
We believe that the attack on HackingTeam in mid-2015 led to a shortage of surveillance tools in the market, and this gap is now being filled by other companies. One of them is Gamma International, which offers customers a package of FinFisher tools. However, Gamma International itself was also hacked in 2014 by the same hacker named Phineas Fisher, although then the consequences were not as serious as in the case of the Hacking Team. In addition, Gamma International had two years to recover from the attack. Apparently, the number of attacks using FinFisher and zero-day vulnerabilities will continue to grow.
How to do and how to protect against such attacks?
In the case of CVE-2017-11292 and similar vulnerabilities, it is possible at the level of your organization to use the Killbit technology to block Flash elements in specific applications. Unfortunately, it’s not so simple to do this at the system level: potentially Flash objects can be loaded via applications that Killbit cannot stop. In addition, sometimes quite necessary tools depend on Flash, which as a result of blocking can also become inoperative. In addition, there are no guarantees that BlackOasis will not switch to the use of exploits for other software products.
It is best to apply a multi-level approach using access policies, antiviruses, network monitoring, and white lists. Our products detect BlackOasis tools as PDM: Exploit.Win32.Generic, HEUR: Exploit.SWF.Generic and HEUR: Exploit.MSOffice.Generic.
Infection Indicators:
4a49135d2ecc07085a8b7c5925a36c0a
89.45.67 [.] 107
Many thanks to the Adobe Product Security Incident Response Team (PSIRT) for helping to analyze the vulnerability and fix it quickly.
Source: https://habr.com/ru/post/340256/
All Articles