Serious vulnerability in the popular encryption library undermines the security of millions of crypto keys
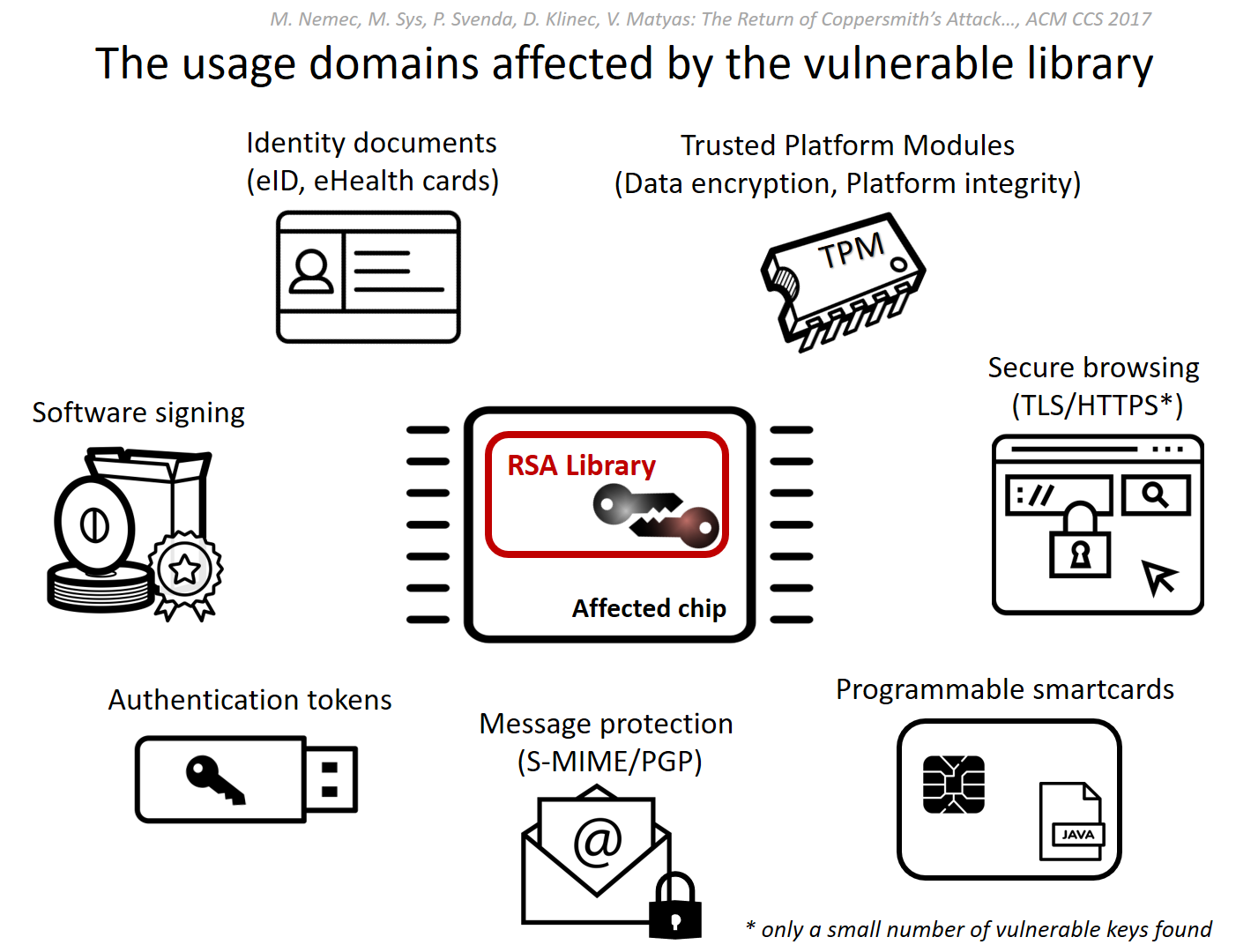
Image: crocs.fi.muni.cz
An international team of information security researchers from the UK, Slovakia, the Czech Republic and Italy discovered a critical vulnerability in Infineon's popular RSA Library v1.02.013 encryption library. An error in the algorithm for generating RSA primes makes the encryption keys generated using the Infineon library susceptible to factorization - this allows attackers to reveal the secret part of the key.
')
The vulnerable library is used to ensure the security of national ID-cards in several countries, as well as in many popular software products used by both government agencies and businesses.
What is the problem
The weakness of the factorization mechanism allows an attacker to calculate the secret part of any vulnerable encryption key using only the corresponding public key. Having obtained the secret key, an attacker can impersonate the key owner, decrypt sensitive data, download the malicious code into the software signed with the key and overcome the protection on stolen computers.
The vulnerable encryption library was developed by the German chip maker Infineon - an error has existed since 2012. The fact that the library is used by two international security standards makes it critical for the problem — so many corporations and government organizations around the world use it.
First effects
The researchers checked the national ID cards of four countries, and quickly found out that at least the maps of two countries - Estonia and Slovakia - use vulnerable keys with a length of 2048 bits to ensure security. The Estonian authorities confirmed the presence of the vulnerability , stating that since 2014, about 750,000 vulnerable cards have been issued. In 2015, one of the journalists of the Ars Technica edition received the card of the “Estonian e-resident” - an experiment showed that the key used in it is factorable.
In addition, Microsoft , Google and Infineon warned that the weakness of the factorization mechanism could seriously affect the effectiveness of the built-in protection mechanisms for TPM products. Ironically, such cryptochips are used just to provide additional security for users and organizations that hackers often attack.
The researchers also tested 41 models of various laptops using TPM chips - 10 of them use the library from Infineon. The vulnerability is particularly serious in the case of TPM version 1.2, since the keys that the system uses to control the operation of the Microsoft BitLocker are subject to factorization. This means that anyone who steals or takes possession of a vulnerable computer will be able to overcome the protection of the hard disk and the bootloader.
In addition, the researchers were able to find 237 factorized keys that were used to sign the software published on GitHub - among which are quite popular software packages.
Among other finds are 2892 PGP keys used to encrypt email correspondence, 956 of which turned out to be factorizable. According to experts, most of the vulnerable PGP keys were generated using the Yubikey 4 USB product. However, other functions of the USB key, including U2F authentication, did not contain vulnerabilities.
Finally, the researchers found 15 factorizable keys used for TLS. Most of them in the description line contained the word SCADA.
How to protect
Researchers will present a detailed report on their findings at the ACM computer security conference . To give users time to replace keys, a detailed analysis of the factorization method used will not be presented prior to the presentation.
In this case, the researchers published a tool to determine whether a particular key was generated using the vulnerable library. Details are provided in their blog post . In addition, Infineon has released a firmware update that closes the vulnerability, TPM manufacturers are now working on their own patches.
Also, the researchers contacted the administration of GitHub, the service now notifies users about the need to replace keys to sign the software. In turn, the Estonian authorities closed their public key database, but no announcements about possible replacements of vulnerable ID-cards have yet been published.
Source: https://habr.com/ru/post/340230/
All Articles