Information security in the process control system: attack vector man-machine interface

“About three decades ago, we, industrial automation specialists, faced a task for which we were poorly prepared. We began to implement an automated process control system with the ability to graphically display the course of processes in real time. However, initially the screens were empty, and we had to fill them with information. We did not have manuals in which we could read about what “good” graphics are. We did everything we could, or rather, we knew everything — and we knew a little. The result was predictable - we created an inefficient paradigm of human-machine interfaces (HMI or English: HMI, humane machine interface), or rather, how they should look. Inertia of thinking did the rest. Basically, for the sake of ease of implementation, we decided to depict the processes in the form of a P & ID (from the English: process & instrumentation diagram), functional diagrams supplemented with numerical values. We adhered to this paradigm even when the graphics capabilities of DCS / SCADA systems improved, and simply migrated the old screens to newer systems. ”
Bill Hollifield, for InTech.
Historically
According to research, the mistakes of operators, observing and controlling technological processes, cause about 42% of accidents. This is due to the development of production and increased automation. In this case, the operator, not being close to the real equipment, is not able to assess his physical condition at the present time in the current operating conditions. Today in the modern world, this function is performed by SCADA-systems, the main component of which is the human-machine interface (HMI).
Historically, HMI (man-machine interface) was understood as a dial gauge, buttons, switches, and switches. At the moment, there are still requirements, according to which the emergency shutdown button and the accident indicator lamp must be real physical objects. Modern operator panel consists of virtual buttons, graphs, analog and digital indicators.
')
Abandoning physical devices is not completely possible due to compliance with safety standards. Because it allows you to organize a physical break in the control circuit and control the situation if the virtual interface has failed.
It is important to understand that the operator panel and human-machine interface (HMI) are not the same. The panel is just an interface for a simplified understanding of the process technology. Most of its modern capabilities and “intellectual abilities” are determined by software. Thus, the evolution of HMI is always a parallel process of development of hardware and software (software).
As practice shows, operators and dispatchers do not participate in the process of creating a human-machine interface of SCADA-systems. This factor affects the efficiency of the operators and the number of mistakes made by them during the process control at the facilities.
The passive approach in the development of HMI, due to the desire of designers to create interfaces for the already used samples. This problem is well illustrated by the fact of the use at the moment in the territory of the Russian Federation of the GOST 21480-76 “System“ Man-Machine ”. Mnemonic Schemes General Ergonomic Requirements ”, reissued in November 1986. Obviously, over the past 30 years, radical changes have occurred in the level and volume of automation of technological processes, as well as in the capabilities of SCADA systems. There are standards IEC 60447-93 "Man-machine interface (ICM), GOST R IEC 60447-2000" Man-machine interface. The principles of actuation ”,” but they do not reflect the approach to optimizing HMI.
As a result, today thousands of operators control production worth tens of billions, looking at primitive images developed at a time when they had no idea about the effectiveness of the HMI.
How to improve HMI
How to achieve the greatest return from a human machine interface is to provide information that is important and in the form that it is intuitively understandable. High performance HMIs display information — data in a specific context that makes it useful. HMIs should not only display the values of certain process variables, but also show whether these values are “good” or “bad”. Abnormal indicators should stand out clearly. Providing information in a graphical form of processes allows you to maximize the efficiency of operators. Processes should be presented in the most informative and conducive to immediate action form.
In 2009, the Electric Power Research Institute or EPRI conducted a large-scale study of HMI. As a result of the study, a report was created, which was called the Operator’s Graphic Fuegle, ID 1017637.
There was a special simulator that was used for more than 10 years. During the test, several operators discovered and resolved critical situations, using both existing, familiar to them control screens, and new ones, organized using the principles of high-performance HMIs. The latter have significantly improved the efficiency of operators in several important ways.
Prior to this test, it had never occurred to anyone to develop specialized screens for such scenarios, with all the management tools necessary to complete the task. The test results showed that the new approach to the organization of HMI is much more efficient. Complex control systems, as a rule, have ineffective and problematic HMIs created by people without special knowledge. Operator efficiency can be greatly improved with HMI using the right principles. High performance HMIs are very practical, they are easy to implement, and their price is quite affordable.
Current trends and aspirations of HMI
No matter how modern the process control system of making key decisions is, it is always up to the person. Convenience, reliability and functionality largely determine the success of the entire work of the process control system.
Other requirements for automation are associated with the complexity of the process technology itself, which employs many different devices from different manufacturers. For consumers, the ease of integrating HMI with all various devices, support for open communication protocols (most often Ethernet), as well as the possibility of transferring information to a system whiter than a high level and scalability of the presented solutions come first.
However, there are general requirements for HMI, which are characteristic for both machine and process automation. First, it is the ease of customization and adaptation to the needs of production. Secondly, the ability to create your own, including dynamic, objects and replicate them. Third, a clear and clear display of information, regardless of environmental conditions and other factors. Finally, fourthly, the ability to quickly and accurately manage the system, regardless of its current state, environmental conditions and other factors.
In the era of smartphones and tablets, any screen is perceived not only as an information output device, but also as an input device.
As noted above, many of the innovative capabilities of the operator panels are associated with the evolution of software. It is on the characteristics of the software depend on the speed of application development, configuration flexibility.
Typically, HMI hardware does not have strong industry specificity and is determined by the availability of certificates from various classification societies, such as IEC, UL, CSA, EAC, marine BV, GL, and ATEX.
You can also adapt HMI to industry-specific tasks by using ready-made architectures - TVDA (Technical validated documented architecture). Thanks to TVDA, there is no need to write bulky programs, just enter the parameters for ready-made architectures.
Significantly expand the capabilities of the software for configuring the panels by supporting the scripted programming language JavaScript, which allows you to implement almost any logic.
One of the key trends in the HMI market in recent years is the ability to control production processes not only with fixed panels, but also with the help of mobile devices. This function is required where there is a need to monitor remote equipment.
The expanded version allows the technical manager or development engineer to create additional screens on his mobile device that are not associated with the operator panel screen. With their help, you can change the settings that are not available on normal workstations.
Also, modern operator panels can interact with the user at a distance by sending him SMS or emails.
Industrial computers are supplied with installed Windows operating systems, SCADA systems (dispatcher control and data collection systems) for installing applications, or HMI systems or a web interface depending on the user's needs.
HMI tools remain an integral part of an automation system, and must be easily integrated with any of its components, often with top-level systems (ERP and MES).
Vulnerability and accessibility
It would seem that the networks in production are usually isolated from public networks and the internal networks of the enterprise, the equipment and software in them are significantly different from conventional networks - not to mention the fact that all processes are clearly regulated and strictly controlled.
The SCADA HMI market is very active, but often not as safe as necessary. The largest HMI suppliers in this industry are Siemens, Advantech and GE, but there are also many smaller players in many other countries. In some cases, a small company is bought before the release of its product patch, which makes it difficult to track the state of vulnerability in the disclosure process.
In addition, suppliers of SCADA systems, as a rule, focus on industrial equipment, and not on the software that manages them. Because they make a profit from the sale of equipment.
When it comes to the actual codes that underlie SCADA systems, most do not use basic protection — in-depth, such as address space allocation randomization (ASLR), SafeSEH, or stack cookies. This may be due to the erroneous belief that these solutions will work in a completely isolated environment.
Despite the obvious risks of unauthorized access to critical systems, the development branch of SCADA systems is aimed at producing equipment and less at software. The lack of global standards for HMI software further exacerbates the security problems in this field.
Information from publicly available sources, such as vulnerability knowledge bases ( ICS-CERT, NVD, CVE, Siemens Product CERT, Positive Research Center, Trend Micro, Zero Day Iniciative (ZDI) ), manufacturer notifications, exploit collections , reports of scientific conferences, publications on specialized sites and blogs.
As a result, 743 vulnerabilities were revealed in the automated process control systems detected from 2005 to 2012, and from 2009 to 2012 the number of detected vulnerabilities in the automated process control system u increased 20 times (from 9 to 192). In recent years (2012–2015), the number of vulnerabilities found annually remains stable (about 200). According to the data of 2015, only 14% of vulnerabilities were eliminated within three months, 34% were eliminated more than three months, and the remaining 52% of errors were either not corrected at all, or the manufacturer does not report the time of elimination.
As of 2016, 158,087 ICS components available on the Internet were detected. The largest number of components of the automated process control system is available via HTTP, Modbus (RTU and TCP / IP) and Profibus / Profinet, BACnet, accounting for approximately 33% each, OPC (25%). However, the number of vulnerabilities detected depends on the prevalence of the product and whether the manufacturer adheres to the policy of responsible disclosure.
The greatest number of vulnerabilities was detected in SCADA components, as well as in components of human-machine interfaces. However, currently only 5% of known vulnerabilities have published exploits. This figure dropped significantly compared with 2012: then it was possible to find exploits for 35% of vulnerabilities.
Among all the operating systems used with the APCS, Microsoft Windows leads by a large margin. Most often, the global network contains various components of SCADA systems (including HMI). They account for 70% of all detected objects.
The availability in the public domain of a ready-made tool for exploiting a vulnerability or information about it greatly increases the likelihood of a successful attack.
As a rule, the number of published vulnerabilities correlates with the number of published exploits. In the period from the beginning of 2011 to September 2012, 50 exploits were published - six times more than in six years from 2005 to 2010.
However, the lack of a known method for implementing an attack reduces the likelihood of an attack, but does not completely exclude it, since cyber attacks on industrial facilities are carried out with the assistance of experienced high-level specialists who often simply do not need "exploit packs" and other popular tools.
Vulnerabilities for which there is already an exploit, but a patch has not yet been released, pose the greatest danger, since an attacker does not need in-depth knowledge and lengthy preparation to penetrate the system.
HMI vulnerabilities report for 2016
The developers of SCADA solutions often have little experience in building a user interface (UI). This is due to the fact that developers do not know what the final operating environment for systems will be. This forces developers to make assumptions that are often incorrect. Without the full life cycle of code development, programs contain vulnerabilities. SCADA developers continue to make the same mistakes that application and OS developers made ten years ago.
Trend Micro experts analyzed the ICS-CERT warnings for the period from 2015 to 2016 related to HMI vulnerabilities, and came to disappointing conclusions.
This study examines the current SCADA HMI security status. Analyzing all publicly disclosed vulnerabilities in SCADA software that have been fixed since 2015 and 2016, including 250 vulnerabilities acquired through the Zero Day Initiative (ZDI) program. Almost a third of vulnerabilities (36%) are related to buffer overflow (Buffer Overflow). This security problem allows an attacker not only to cause a program crash or “freeze” the program, which leads to a denial of service, but also to execute arbitrary code on the target system.
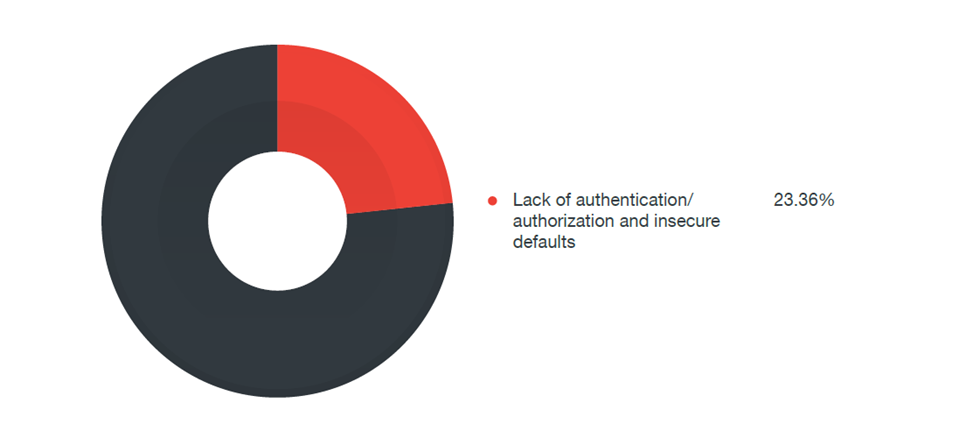
If you add up all types of vulnerabilities, the exploitation of which allows a hacker to launch code execution (for example, buffer overflow, remote code execution), you will get about 40% of all vulnerabilities. It is worth noting a large number of problems with authentication and key management (Authentication / Key Management) - almost 23%.
All these errors can be prevented by using safe code development techniques. Finally, we observe the average time between the disclosure of an error to the SCADA provider and the release of the patch, it reaches 150 days, another 30 days will be required for software deployment.
This means that on average five months before the SCADA vulnerabilities are fixed. For some manufacturers, this may take only one or two weeks, while for larger ones it takes up to 200 days.
The US Department of Homeland Security, ICS-CERT, is tasked with reducing risks within all critical infrastructure sectors through collaboration with law enforcement and intelligence and pooling efforts.
There is such an interesting ZDI program that buys people into vulnerabilities that they found in various products. After purchasing a vulnerability, they analyze this vulnerability with all similar products of a particular company in whose code there are errors. Thereafter, contact the company and represents the vulnerability. In fact, it turns into a business. When the ZDI program acquires vulnerabilities that affect SCADA, ICS-CERT is reported to resolve this issue. In 2015, ICS-CERT responded to 295 incidents and handled 486 vulnerability disclosures.
To determine which vulnerabilities prevail in the HMI, consider the results of ICS-CERT detection for 2015 and 2016, and corrections over the past two years. This data was combined with more than 250 zero-day vulnerabilities purchased by the ZDI program. This information was also compared with the listed CWE vulnerabilities to determine the total number.
As it turned out, 20% of the exploited vulnerabilities were caused by memory damage (buffer overflow, read / write vulnerability outside the field (out-of-bounds read / write), etc.).
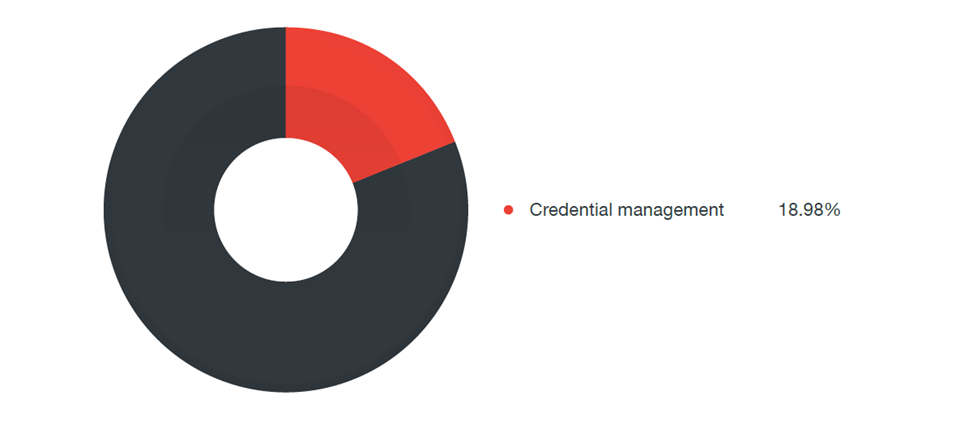
23% of vulnerabilities arose due to the lack of authorization mechanisms, 19% of problems were associated with credentials (stitched passwords, hidden accounts with full rights, storing passwords in clear text), 9% of problems allowed the introduction of code.

Figure 1: Vulnerability Categories
Although some cross-site scripting (XSS) and Cross-Site Request Forgery (CSRF) problems were expected, most of the HMI problems are problems with Windows, not web applications. Some XSS and CSRF errors exist in the “Others” category, although they are few.
Memory corruption issues
Problems with memory damage account for 20% of the vulnerabilities identified. Weaknesses in this category are classic code protection problems, such as stack buffer and heap overflows beyond the limits of read / write boundaries. Memory corruption can occur in the HMI when the contents of a memory cell are inadvertently altered due to errors somewhere in the code.
This can also be called a security breach of memory. When the contents of corrupted memory are used later in this program, the failure or execution of code that is not intended to run.
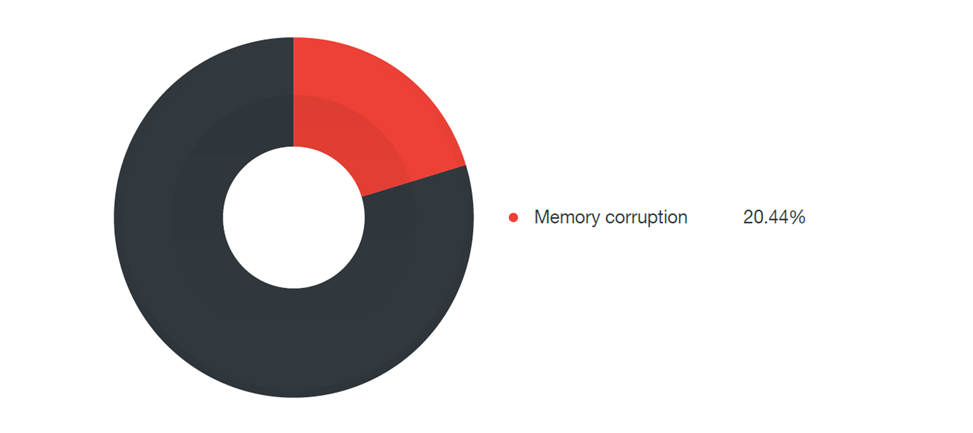
Memory damage 20.44%
Example: Advantech WebAccess HMI Solution
At some point, ZDI received 100 separate reports using the Advantech WebAccess HMI product in one day. Most of these cases turned out to be buffer overflows, most of which are similar to the example below.
 Figure 2: Advantech WebAccess Toolbar
Figure 2: Advantech WebAccess ToolbarOne interesting point is that, at present, this is a SCADA solution, but it is also advertised as a solution for Internet of Things (IoT). The solution contains the webvrpcs.exe service, which runs in the context of a local administrative user. The service listens to the Transmission Control Protocol (TCP) port 4592 and can be accessed via the Remote Procedure Call Protocol (RPC) -based protocol.
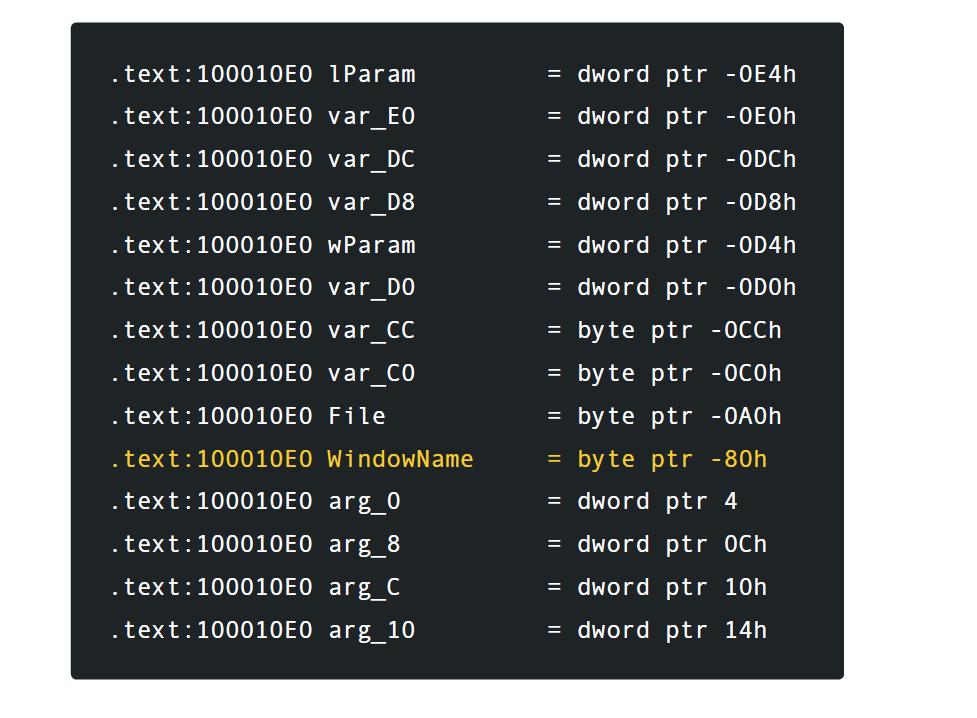
Service calls from the application are designed to resemble Microsoft Windows DeviceIoControl functions. Each service call contains an input / output value (IOCTL) that allows you to use conversion tables to use hundreds of service types. In this example, the parameter is the name window, which is copied using the _sprintf function to the stack buffer, which is 0x80 characters.

The area marked in yellow is the IOCTL code, followed by the buffer length (in and out) - 0x8 bytes in size followed by a terminating zero. Because the attack puts 0x8c bytes of data into a buffer of 0x80 bytes in length, the predicted overflow results. Viewing the vulnerable code shows the classic _sprintf call, which allows overflow conditions.

Checking the stack layout shows that WindowName is set to -80 with 0 as the return address. Since then, it was not installed during the compilation stage, there is no stack of cookies installed for protection.
The lack of stack cookies, as well as other protections such as ASLR and SafeSEH, is probably due to the fact that the original code was written prior to the existence of these encoding methods. However, the use of prohibited (API) and the lack of deep security measures means that the attacker simply needs to rewrite the return address to the beginning of the attacking return link (ROP).
Without ASLR, no difficulty is required to execute malicious code controlled by an attacker with elevated privileges. Analysis of the patch for this vulnerability also shows some interesting options for cleaning up the code of aging databases. The original _sprintf function was included in the list of API-banned by Microsoft released in 2007. ZDI researchers expected Advantech to implement a list of banned APIs and remove known bad functions from its code. Instead, the patch for this error changed the _sprintf function to the _snprintf function.
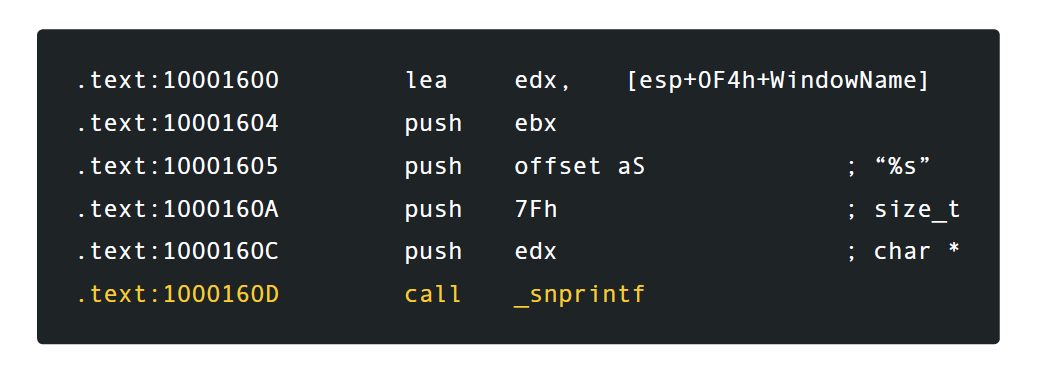
However, _snprintf is also on the list of prohibited APIs. Although _snprintf provides greater overflow tolerance than _sprintf, it cannot complete (with a null character) if there are too many characters.
This means that when the stack is not cleared (a rare situation), it is possible for attackers to use string manipulations on this WindowName to trick the program, counting a buffer of 0x80 characters long, when in reality the buffer is longer because it does not complete zero.
Of the 75 fixes released by Advantech, all were point fixes. In other words, the supplier fixed the bug, but did not eliminate the global problem functions. Thousands The functions _sprintf and _snprintf remain in the code base for today. Advantech did not release patches for the remaining 25 questions that were reported by ZDI researchers. These questions were subsequently disclosed to the public in accordance with the policies of the ZDI program.
Credential Management Issues
Identity management problems account for 19% of the vulnerabilities identified. Vulnerabilities in categories are cases such as the use of hard-coded passwords, saving passwords in a recoverable format (for example, clear text) and insufficient credential protection.
Hidden GE MDS PulseNET account
General Electric (GE) MDS PulseNET is used to monitor industrial communication devices and networks deployed in the energy, water and wastewater sectors around the world. The ZDI program reports that "affected products contain a hard-coded account with full privileges." A full investigation led to the disclosure of CVE-2015-6456 with a general system vulnerability score (CVSS) rating of 9.0.
Take a look at the user control panel, it indicates the existence of only two accounts in the system (operator and administrator). However, as noted by Andrea Micalizzi (who is also known by the nickname "rgod"), there is a hidden third user account with administrator rights.
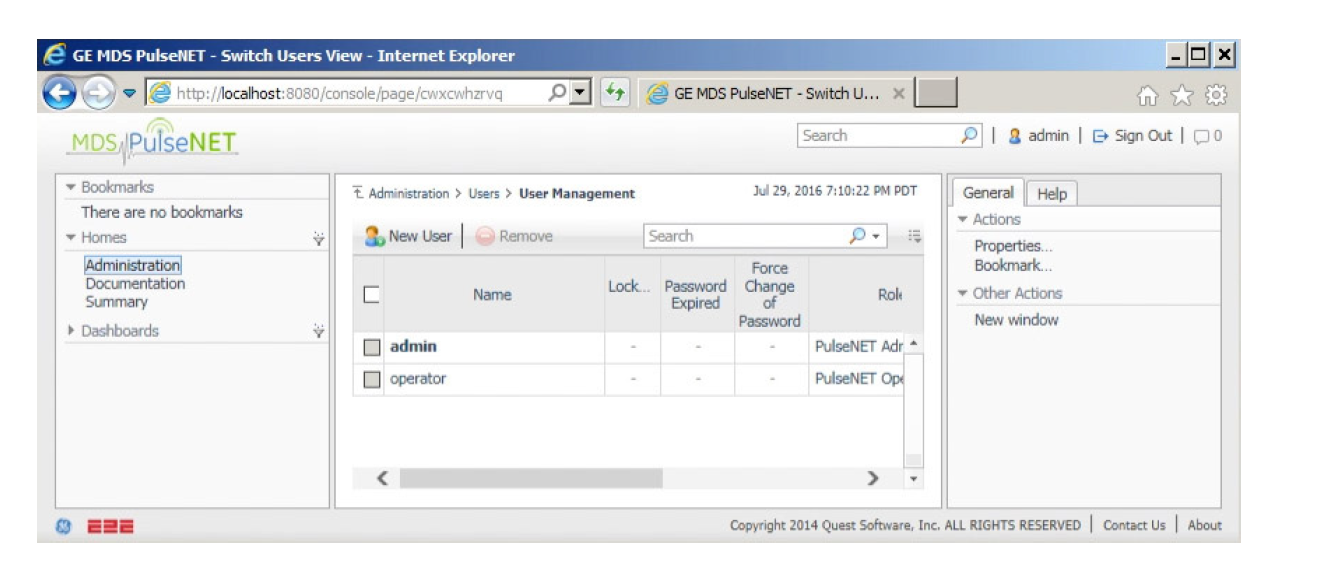
Figure 3: GE MDS PulseNET User Control Panel
Using HeidiSQL to extract information from the database provides an account "ge_support" with a password hash <! [HDATA [MD5 $ 8af7e0cd2c76d2faa98b71f8ca7923f9. The decrypt is MD5 hash, the password is displayed as “Pu1seNET”.

Figure 4: GE MDS PulseNET User Control Panel after Login
Even after logging in with the “ge_support” account, the third username is not displayed to the user in the control panel.
/
23% SCADA. , , ActiveX, .
: Siemens SINEMA Server
, HMI, , (ACL) Windows Program Files .
Instead of properly protecting these top-level directories, they are writable by default, and the directory tree includes utility source solution files. This allows any local user to attach a new binary file that will be executed as a system service in the directory. This problem manifested itself on the Siemens SINEMA server and was reviewed using CVE-2016-6486. The product itself is installed in a directory tree with a weak ACL. By default, Microsoft installs the Program Files directory — as protected with ACLs.
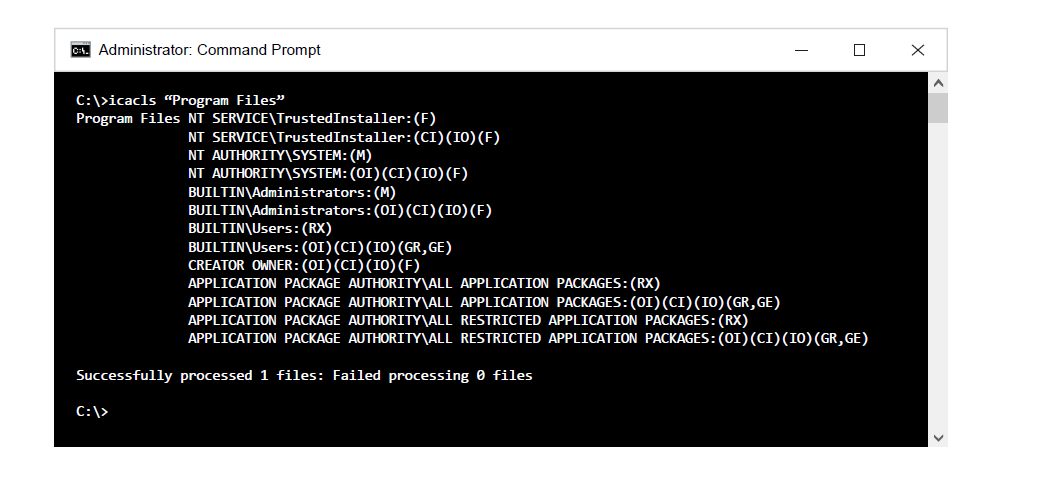
Figure 5: Command line showing standard Program Files permissions
, . . , , , Program Files, Siemens .
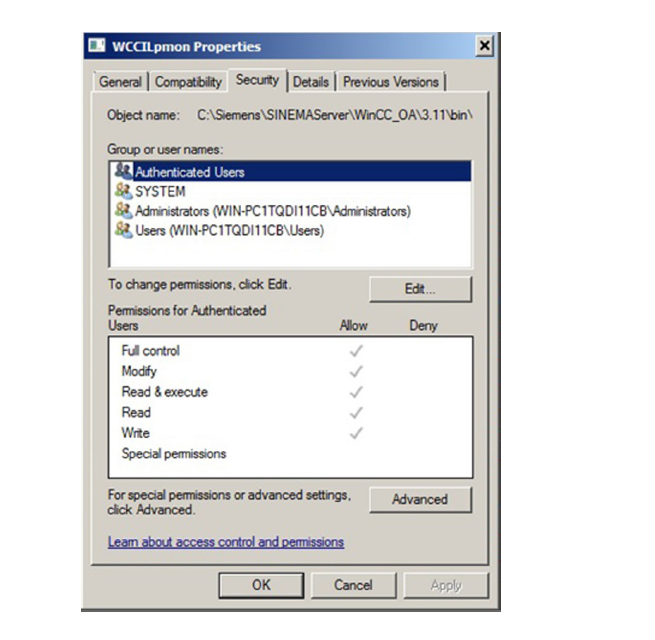
6: Siemens SINEMA Server
, , . , - . , , , .
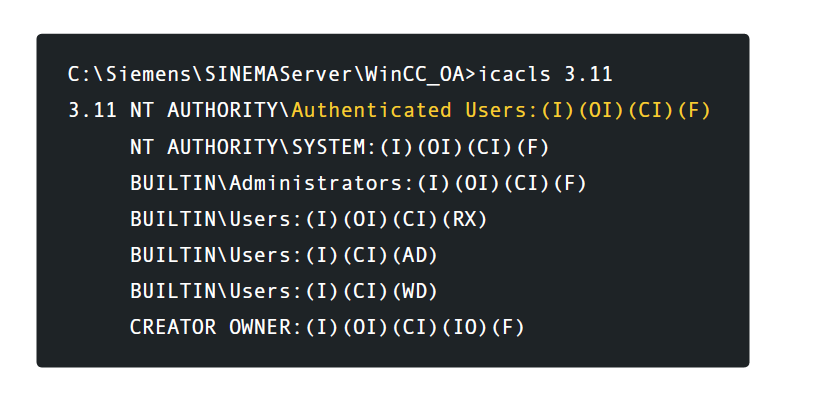
As noted by the highlighted line, Authenticated Users have full control. To join a verified user group, the user only needs to authenticate in the Windows domain. In essence, this means that almost everyone in the system will be in the Authenticated Users group. An examination of the source code in this directory shows similar results.
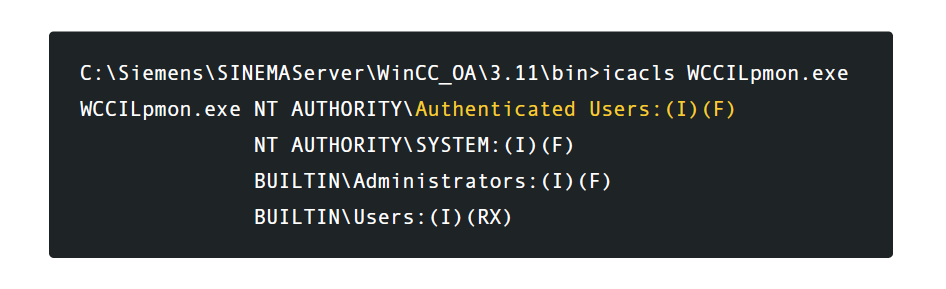
It is important to note that this particular source file starts a service that runs at the local system level.
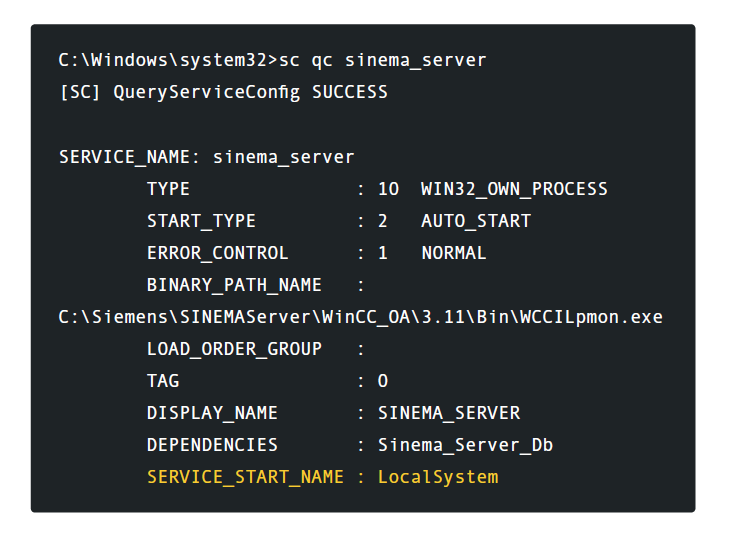
The end result of this unsafe default installation allows any authenticated user to replace the original file at will. In addition, this new attacker-driven binary is executed in the context of the local system after the next reboot.
Example: Advantech WebAccess
Advantech WebAccess provides cross-platform, cross-browser data access and a user interface based on HTML5 technology. The ZDI program received an error message that allowed you to view other passwords when changing your password.
The ICS-CERT report on this error "A properly authenticated administrator can view passwords for other administrators." We should note that this does not mean a system administrator. This refers to the administrator of SCADA systems. As part of the solution, there is the upAdmin.asp script, which allows the SCADA administrator to update his username, password, or description. The Active Server Pages (ASP) script can be exploited by anyone with the permission of the system.

Figure 7: Advantech WebAccess User Settings Panel
, « ».
URL- http:///broadWeb/user/upAdminPg.asp?uname=known&return=bwproj
— IP- , . URL- ,
http:///broadWeb/user/upAdminPg.asp?uname=victim&return=bwproj
, HTML- , .
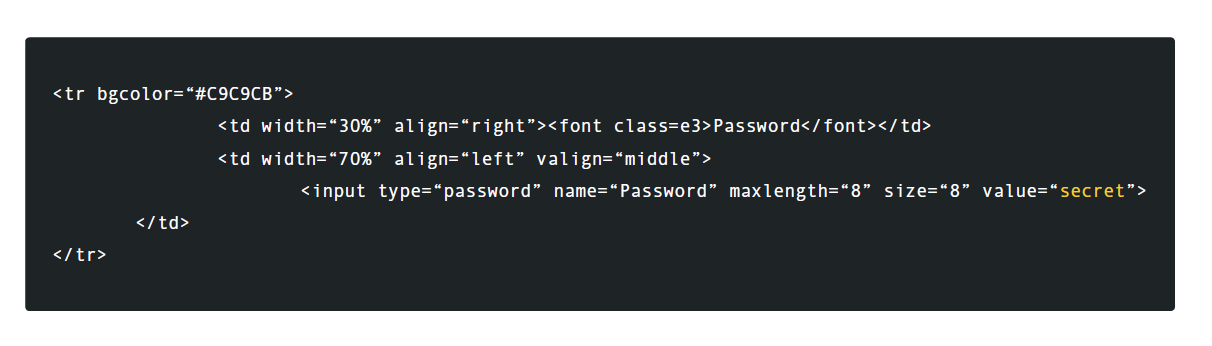
, SCADA .
-, HMI , . 9% . — SQL, , , - , SCADA. - , — Gamma, Cogent DataHub .

- Gamma?
Cogent DataHub Gamma HMI . , Gamma , . , C C ++, , . Gamma API .
: Cogent DataHub
, Cogent DataHub , , OLE (OPC) Windows.
ZDI , , -. .
8: Cogent DataHub WebView
, Cogent DataHub , SCADA . EvalExpression Gamma . Ajax TCP- 80.
Gamma , , SCADA. . , .
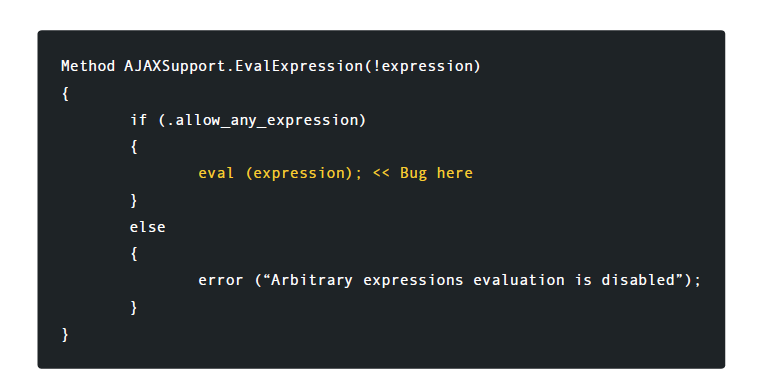
The highlighted error accepts the expression and checks one flag to determine if the system is allowed to execute the expression. If this check returns true, the expression is executed regardless of what it contains. The attacker still has to deceive the system. Fortunately for the intruder, the system allows this as well. To complete this exploit, an attacker must first send an HTTP request to any Gamma script that loads the necessary libraries.
, , , . AJAXSupport.AllowExpressions allow_any_expression True. AJAXSupport.AllowExpressions , . . , Cogent . , — -. .

9:
In the first part of the patch, AllowExpressions is completely removed. This prevents the switch of this flag in the system. Until the developer completely removed EvalExpressions, he made a comment, noting that using the method poses a security risk.
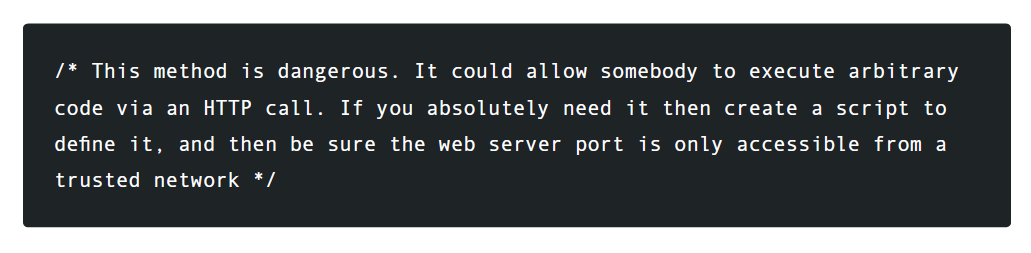
Cogent also commented on the violation code so that it is not installed by default. To enable the code, the developer must log in and manually unlock the method. This method also makes it unlikely for a repeated error to follow.
Information disclosure
When researchers discover vulnerabilities in SCADA products, the amount of time it takes to fix a bug is different. This time is often called the window of vulnerability. ZDI researchers examined all HMI vulnerabilities obtained through the program (more than 250), and analyzed how long they were fixed. As can be seen from the data for the last four years, the average correction time does not decrease.
Since 2013, the average time between when the researchers disclose an error to the supplier and the time when the patch is released is about 140 days.
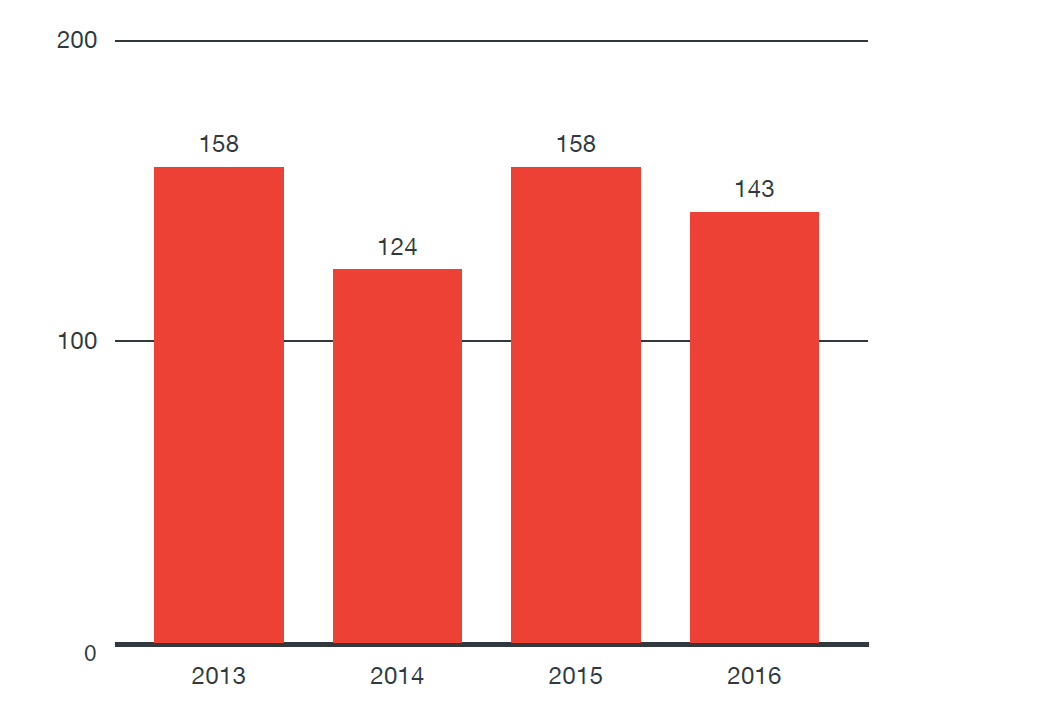
Figure 10: Average time to fix vulnerabilities from the time they are disclosed by year
The quality of the released patch also plays a part in time. A problematic update applied to a system may result in a denial of service (DoS) on a critical portion of the infrastructure. Due to these and other problems, there is a lag between the availability of the patch and the installation of this fix to the production system.
Not all SCADA providers work in the same time frame.
Some providers respond much faster than others. For example, ZDI analyzed that Cogent Real-Time Systems quickly reacted to this vulnerability. For large suppliers, ABB, GE, Indusoft and PTC, it takes an average of more than 200 days to create a patch.
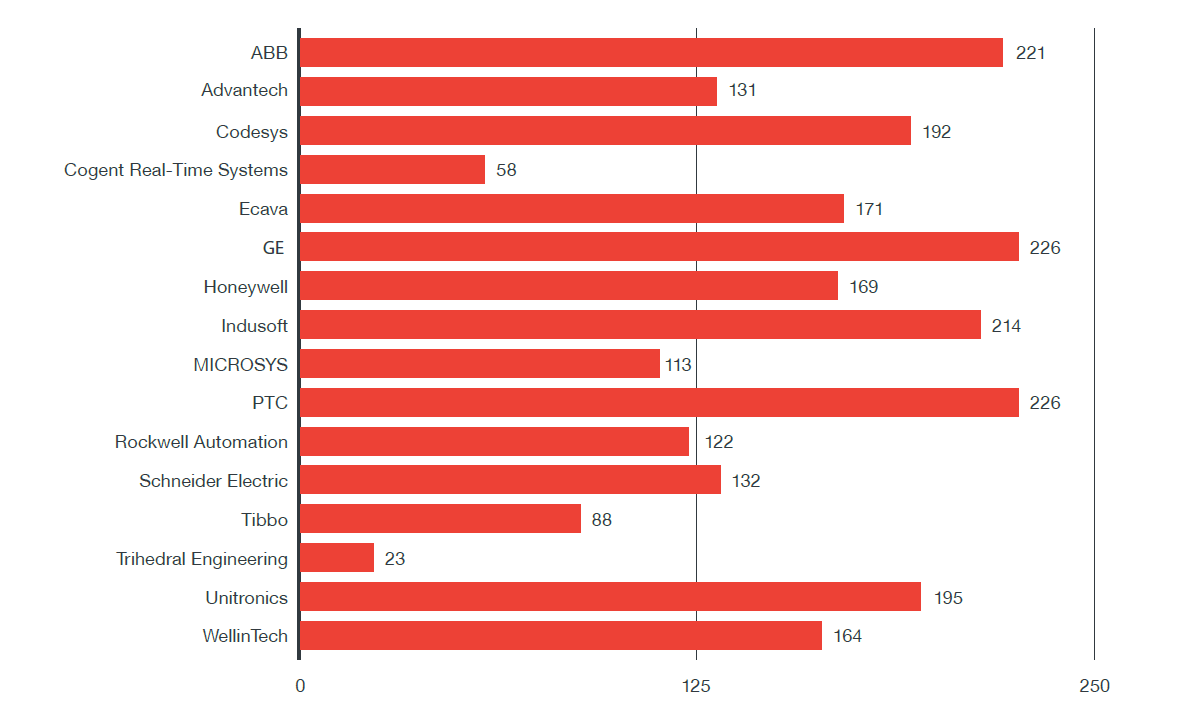
Figure 11: Average time to fix vulnerabilities since they were disclosed by the supplier
. Comparison by industry
A comparison of the response time of the SCADA manufacturers with other industries shows that the response time is not much different from other industries. Although the widespread software of large suppliers such as Microsoft, Apple, Oracle, Adobe and others have an average response time of less than 120 days.
In SCADA-systems and security systems automation on average about 150 days. The security software industry is slightly faster, but not significantly. Business programs include enterprises such as HPE and IBM. These providers require significantly more time to disclose information about errors.

Figure 12: The average time to fix vulnerabilities since they were disclosed by industry
Conclusion
, — 140 . , SCADA- , , .
, . , ( API, ..), .
« HMI SCADA- , . , , , . , »,- .
SCADA HMI . HMI . HMI , .
, HMI , .
, HMI : , , / . .
, , SCADA , 150 , 30 , , Microsoft Adobe, 43 , , HPE IBM.
Taking into account the vector of attacks on HMI, SCADA systems, where the vulnerability is an effective entry point into the system, we hope that the owners of SCADA and administrators are aware of the vulnerabilities promulgated and are therefore trying to block the threat. Developers of HMI and SCADA solutions would benefit from adopting safe methods in the life cycle of developing software code, as it has been done by OS and application developers for a decade.
By taking simple steps, such as auditing to use forbidden APIs, suppliers can make their products more resilient to attacks. SCADA developers should also expect that their products will not be used in ideal systems. For example, although this is considered a bad security practice, developers must take responsibility for their products and solutions and understand that their systems will be connected to a public network.
By adopting such an approach, which implies a worse product usage scenario, developers should implement deeper protection measures. Malicious programs specifically designed for process control systems exist and are actively targeted at HMI.
Errors in SCADA systems are likely to be with us for many more years. Working together, the security of these systems will continue to improve. While a completely secure system is likely to never be created. Enhancing the research and development of software code for the HMI will be our best chance to deter attackers as long as necessary.
Source: https://habr.com/ru/post/340164/
All Articles