DoubleLocker: the first encryptor using the accessibility service of the Android Accessibility Service
ESET has discovered Android / DoubleLocker, the first encoder using the accessibility service of the Android Accessibility Service. Malware not only encrypts data, but also blocks the device.
DoubleLocker is based on a banking trojan that uses the special features of the Android OS. However, DoubleLocker does not have functions related to collecting user banking data and erasing accounts; instead, it provides tools for extortion.

')
DoubleLocker can change the PIN of the device, blocking the victim’s access, and also encrypts the data found — this is the first time we’ve seen this combination of functions in the Android ecosystem.
Given the origin of the Malvar bank, the DoubleLocker can be turned into what we call extortion bankers. The malware operates in two stages - trying to delete a bank or PayPal account, and then blocking the device and data in order to request a ransom. We found a test version of such in-the-wild extortionist banker back in May 2017.
DoubleLocker is distributed in a very simple way, like its ancestor banker - mostly under the guise of a fake Adobe Flash Player through compromised sites.
Once launched, the application offers to activate a malicious accessibility service called the Google Play Service. Having obtained the necessary permissions, the malware uses them to activate the device's administrator rights and sets itself as the default launcher — all without the user's consent.
Self-installation as the default launcher increases the persistence of malware. Whenever the user presses the Home button, the extortionist is activated and the device is locked again.
After running on a device, DoubleLocker uses two valid arguments to force the user to pay the ransom.
Firstly, it changes the PIN of the tablet or smartphone, which prevents the use of the device. As a new PIN, a random value is set, the code is not stored on the device and is not sent anywhere outside, so the user or security specialist will not be able to recover it. But after receiving the ransom, the attacker can remotely reset the PIN and unlock the device.
Secondly, DoubleLocker encrypts all files in the main storage device. It uses the AES encryption algorithm and adds the .cryeye extension.

Figure 1. Encrypted files on a DoubleLocker infected device.
The amount of the buyout is 0,0130 Bitcoin (about 4,000 rubles), the message emphasizes that payment must be made within 24 hours. If the ransom is not listed, the data will remain encrypted, but will not be deleted.
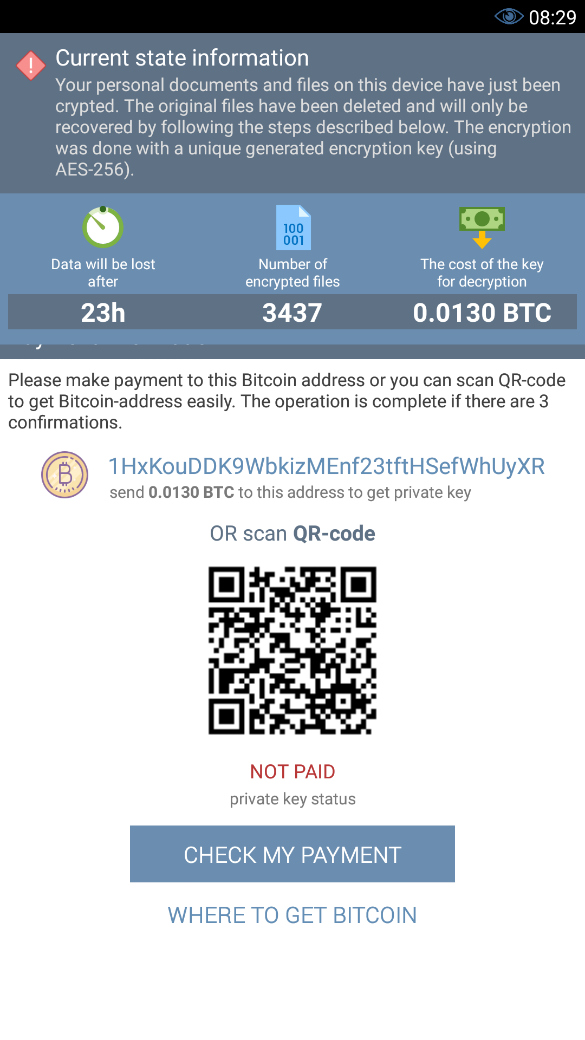
Figure 2. DoubleLocker buyout requirement
In a buyback report, users are warned about the consequences of deleting or blocking DoubleLocker: "Without software, you can never return the source files." To prevent unwanted removal of “software”, scammers even recommend disabling antivirus software — which is rather pointless, because if you have a quality security solution, the device is protected from malware.
To get rid of DoubleLocker, we recommend the following measures:
For prevention, we recommend that you protect your Android device with quality products for security and make regular backups.
ESET products detect new malware like Android / DoubleLocker.
DoubleLocker is based on a banking trojan that uses the special features of the Android OS. However, DoubleLocker does not have functions related to collecting user banking data and erasing accounts; instead, it provides tools for extortion.

')
DoubleLocker can change the PIN of the device, blocking the victim’s access, and also encrypts the data found — this is the first time we’ve seen this combination of functions in the Android ecosystem.
Given the origin of the Malvar bank, the DoubleLocker can be turned into what we call extortion bankers. The malware operates in two stages - trying to delete a bank or PayPal account, and then blocking the device and data in order to request a ransom. We found a test version of such in-the-wild extortionist banker back in May 2017.
Spread
DoubleLocker is distributed in a very simple way, like its ancestor banker - mostly under the guise of a fake Adobe Flash Player through compromised sites.
Once launched, the application offers to activate a malicious accessibility service called the Google Play Service. Having obtained the necessary permissions, the malware uses them to activate the device's administrator rights and sets itself as the default launcher — all without the user's consent.
Self-installation as the default launcher increases the persistence of malware. Whenever the user presses the Home button, the extortionist is activated and the device is locked again.
Device lock and data encryption
After running on a device, DoubleLocker uses two valid arguments to force the user to pay the ransom.
Firstly, it changes the PIN of the tablet or smartphone, which prevents the use of the device. As a new PIN, a random value is set, the code is not stored on the device and is not sent anywhere outside, so the user or security specialist will not be able to recover it. But after receiving the ransom, the attacker can remotely reset the PIN and unlock the device.
Secondly, DoubleLocker encrypts all files in the main storage device. It uses the AES encryption algorithm and adds the .cryeye extension.

Figure 1. Encrypted files on a DoubleLocker infected device.
The amount of the buyout is 0,0130 Bitcoin (about 4,000 rubles), the message emphasizes that payment must be made within 24 hours. If the ransom is not listed, the data will remain encrypted, but will not be deleted.

Figure 2. DoubleLocker buyout requirement
How to get rid of DoubleLocker?
In a buyback report, users are warned about the consequences of deleting or blocking DoubleLocker: "Without software, you can never return the source files." To prevent unwanted removal of “software”, scammers even recommend disabling antivirus software — which is rather pointless, because if you have a quality security solution, the device is protected from malware.
To get rid of DoubleLocker, we recommend the following measures:
- A non-roaming device that does not have a mobile device management solution that can reset a PIN: the only way to get rid of the lock screen is to reset to factory settings.
- Root device: the user can connect to the device via ADB and delete the file in which the PIN code is stored. To do this, you must enable device debugging (Settings - Developer options - USB debugging). The lock screen will be removed and the user will return access to the device. Then, working in safe mode, the user will be able to deactivate the device administrator rights for the malware and delete it. In some cases, a device reboot is required.
For prevention, we recommend that you protect your Android device with quality products for security and make regular backups.
ESET products detect new malware like Android / DoubleLocker.
Source: https://habr.com/ru/post/340022/
All Articles