Security Week 41: Accenture has posted all on Amazon, a year of malvertization on Pornhub, a fresh attack on Office
 We no longer know how to live without cloud technologies, and we still do not know how to live with them. Every now and then the most ridiculous fakapy happen because people do not really understand that their cloud resource and the local one are two big differences, and you need to deal with them accordingly. Here, for example, as now, when researchers found in Amazon S3 a large clearing with delicious data, kindly covered by Accenture.
We no longer know how to live without cloud technologies, and we still do not know how to live with them. Every now and then the most ridiculous fakapy happen because people do not really understand that their cloud resource and the local one are two big differences, and you need to deal with them accordingly. Here, for example, as now, when researchers found in Amazon S3 a large clearing with delicious data, kindly covered by Accenture.The company, to put it mildly, is not one of the last. He is engaged in consulting, helps clients to strategically plan, optimize, modernize and implement. He works with the largest corporations in the world, on which he earns about $ 5 billion a year, a little less than Gazprom. And here in this consulting giant in Amazon S3, four baskets were discovered, open to the outside even without a password. You know the URL - come in, unload what you want.
The baskets were full of Accenture customer data. The guys from UpGuard who found them did everything right - they told the data owner, they waited until all this was removed from access, after which they published a report on the discovery with a clear conscience. The figures themselves were quick to say that nothing terrible had happened: they had a multi-level security model, and this data would not have helped hackers to overcome any one of the levels. Well, you know, security models are like onions - they have many layers.
True, if you read the report, it starts to seem that the data were still a little important there. And there were internal access keys and credentials for the Accenture API, Accenture private signature keys, Accenture account access key for Key Management Service in Amazon Web Services, database dumps where Accenture client credentials were found, password hashes, and backup with 40 thousand unencrypted passwords. With such information, someone could well have carried out the “man in the middle” attack and stand between Accenture and its unsuspecting customers.
')
The strange thing is that the default basket created in S3 is configured as private and requires authentication for access from the outside. That is, it turns out, someone reconfigured these four baskets. The moral of this story is that the company can be arbitrarily respected, it may have the largest customers, but some interesting personality can substitute everyone in four clicks.
Pornhub took up Malvertization
News Research Sounds like a sexual perversion, but there was only another security hole. The largest porn site (according to Alexa ranks 21st among American sites, by the way) picked up malicious banners from the TrafficJunky banner network and showed them to visitors for about a year.
Visitors at Pornhub - in the region of 8.7 million per day, that is, an abundant harvest for the authors of the campaign was provided. The victim, who clicked on the banner, received an offer to update the browser, and launched the js-file, which, in turn, downloaded an interesting piece - the almost incorporeal Kovter Trojan.
Kovter is famous for storing itself in the Windows registry keys, saving only a script in the file to extract itself from the registry. In this case, the researchers found only a clicker version of Kovter, which is used for fraudulent earnings on non-existent transitions by advertising banners, but earlier in nature they also caught the early version .
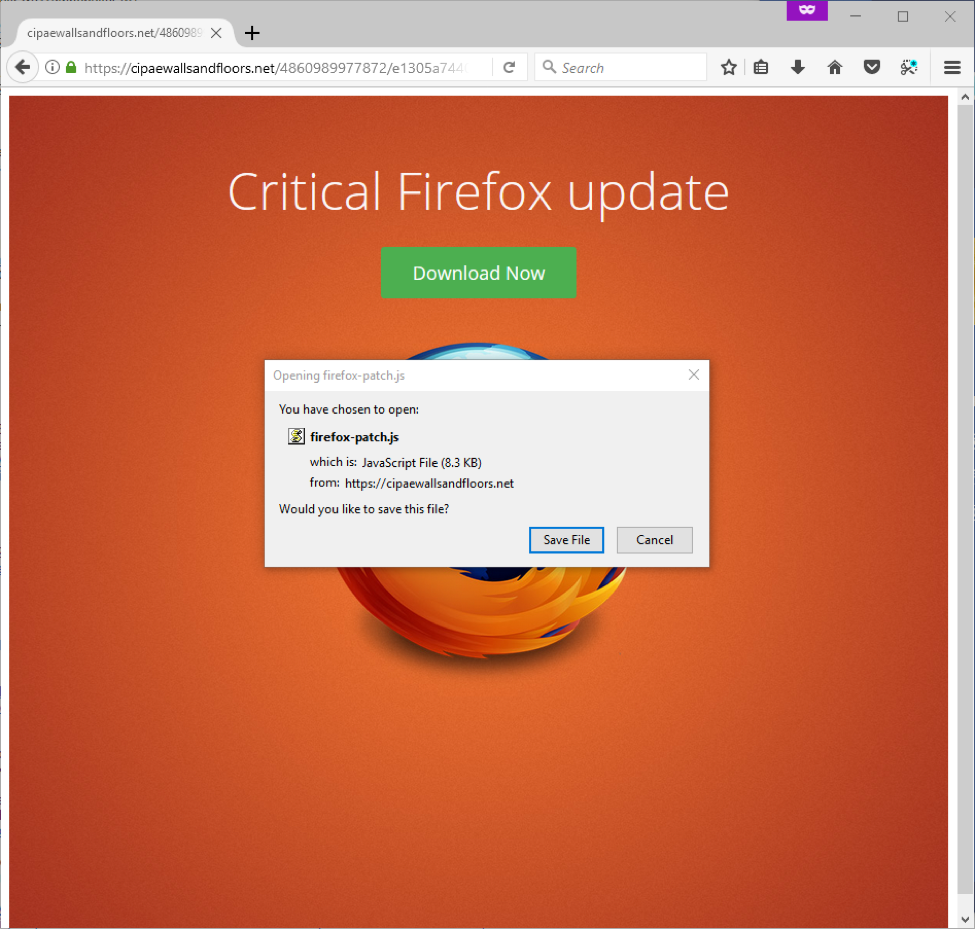
Pornhub, so active in social networks and media, did not comment on such an outstanding failure, but it is safe to predict that this incident will not affect the number of visitors. Visitors to porn sites either take risks or ignore them — you can't hide a libido in your pocket!
Microsoft patches an actively exploited flaw in Office
News , causing an acute sense of déjà vu. The most popular office suite in the world is doomed to the attention of hackers, and often they manage to get ahead of researchers, finding vulnerabilities earlier. Sometimes - much earlier.
Researchers from Qihoo 360 Core Security at the end of September found a new, spick-and-span attack on their customers, during which valuable data was leaked from computers. After the analysis, it turned out that the attack tools were developed somewhere in August, that is, a month or two, hackers visited the Office users unhindered, as if they were visiting their dacha.
Vulnerability CVE-2017-11826 is relevant for all supported versions of Office. The malicious .docx was embedded in RTF files, you need to try to open it for infection - to force the victim to do this, the attackers used the good old social engineering. Properly using tags in a Microsoft Word document, the attackers achieved the execution of malicious code with the rights of the current user.

Especially an attack is fraught for those who like to work with administrator rights - in this case, an attacker can install programs, view, change or delete data, create new accounts with full rights. Microsoft closed the problem on its Tuesday patch, along with 62 other holes.

Antiquities
Family "Loz"
Resident dangerous viruses, encrypted, some of them use the "ghost" -technology. COM-as well as later versions and EXE-files, as they execute, open, rename and change file attributes, are usually affected. Change the first 4 bytes of COM files (JMP Loc_Virus; DB '+'). When creating a resident copy, reduce the value of the word at address 0000: 0413.
"Loz-1018, -1023" corrects the system information in the boot sectors of floppy disks (zero the word corresponding to the number of drive heads). When you run AIDSTEST.EXE, the message “Welcom to demo version © Zherkov. Lozinsky-OAK, AIDSTEST-hunchback ".
"Loz-1018" destroys the AIDSTEST program.
"Loz-1940" contains the text "© Pravdichenko A.".
"Loz-1882, -1915" when you run the file AIDSTEST.EXE destroy it and give a message like:

Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 38.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/340008/
All Articles