Announcement: Veeam Backup & Replication 9.5 (and beyond) new features
In this quarter, Veeam plans to release Update 3 for the version of Veeam Backup & Replication 9.5, and then its anniversary, 10th version will follow. This is our well-known flagship product for protecting data in a virtual environment, but recently, solutions for physical machines are also gaining popularity: the Veeam Agent for Microsoft Windows and the Veeam Agent for Linux.
Naturally, the number of users who want to work with backups of virtual and physical machines is growing using a single console. Therefore, our engineers decided to implement this feature in Veeam Backup & Replication, without delaying them, and I will tell you about it today. For details, welcome under cat.

I'll start with the look. Since Veeam Backup & Replication will now work with both virtual and physical machines, it was decided to bring the Inventory section that previously lived in the VMs view into a separate view. It will display all machines protected by Veeam, whether it is Veeam Backup & Replication or any of the Veeam Agents.
')
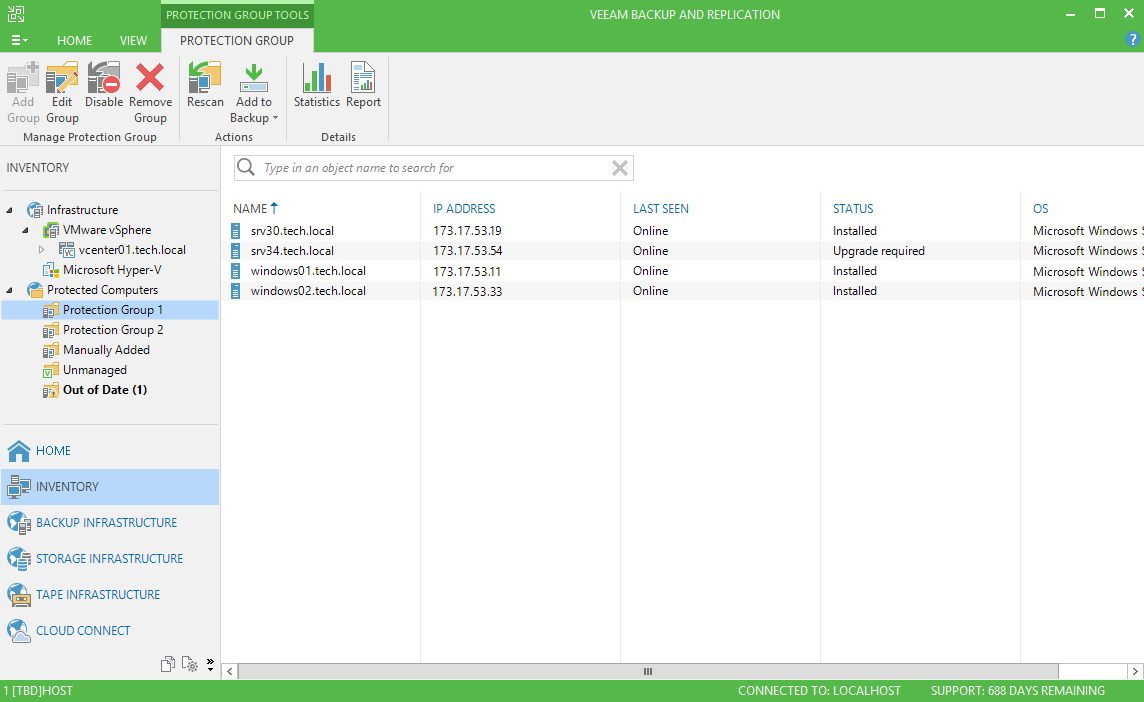
In order to provide the ability to control and configure protection through the console, you need to create the appropriate logical containers - the so-called Protection Groups - and then the necessary objects will be placed there.
First of all, we deal with the type of objects for which we will configure protection. In the Type step of the wizard to create a protective group, there are several options:
Since organizations most likely will use groups for Active Directory objects, we’ll focus on them in more detail first.
If you selected the type of Microsoft Active Directory objects protection group, Veeam Backup & Replication server will automatically request information about the Active Directory structure of your home domain and display it.
Note: You can change the default setting and display as a selection area, for example, a subdomain or another domain in general. You can also exclude individual objects from the selection area — for example, you can exclude computer counts that were turned off during the last month, or you can exclude an entire OU.
So, we have indicated what area of choice our AD objects will be from. Veeam will install the Veeam Agent executable on these objects, which, in fact, will perform backups. Of course, to install agents, the Veeam Backup Service account must have appropriate permissions.
Then you need to specify how often we want to scan our selection area - this entity is dynamic, that is, as soon as new objects are found during the next scan, they will immediately be included in their protective group.
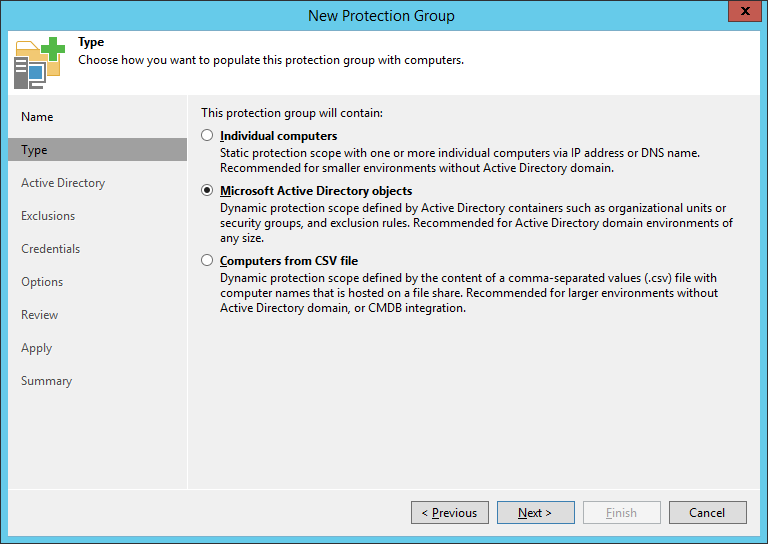
In the scan options (Step Options ) for a group of any type, you can choose whether we want the Veeam Agent to be automatically placed on the newly discovered objects - if we want, then we check the Install backup agent automatically (recommended) checkbox:
After we have properly grouped our computers, we set up a backup for them using an agent. To do this, select the desired protective group and create a new task for it (or include it in an existing one).

Depending on what machines we want to process, choose the type of task. It may be:

At the same step, it is necessary to decide in which mode the agent responsible for backup will work. Depending on which type of protected machine was selected, either both or one of two options will be available:
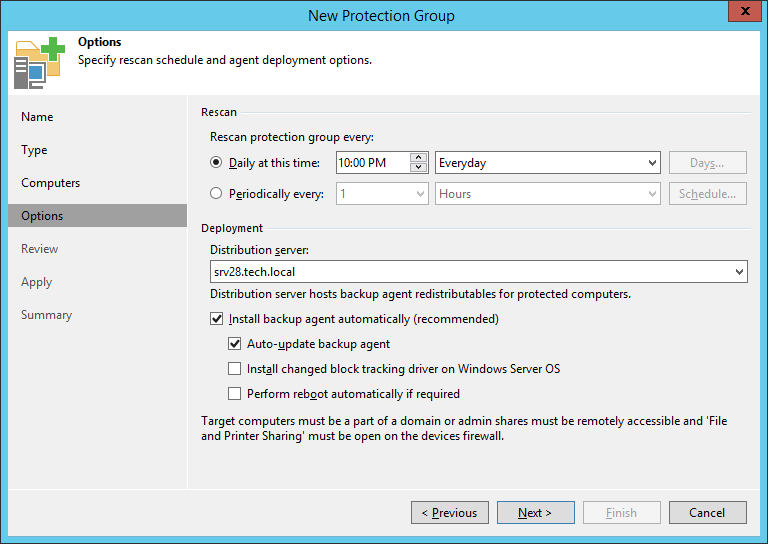
At the Guest Processing step, you can specify that the backup should be created taking into account applications running on the machine (application consistency). The following applications are supported:
To restore the objects of these applications from the backup, you can use the tools from the line of Veeam Explorers.
For SQL and Oracle databases, transaction log backups will be supported - to be able to recover to the selected point in time.
Yes, yes, this year we invite our readers and all those interested in participating in the VeeamON Forum 2017 Russia forum dedicated to the issues of data accessibility. The event will be held on October 26, the venue - Lotte Hotel Moscow.
In the forum program:
In addition, for anyone who knows and knows how to work with Veeam Availability Suite 9.5, there will be exciting LabWarz competitions. The prize for the victory - a certificate worth 30,000 rubles. for any training course at any Veeam certified training center.
Participation in the VeeamON Forum Russia 2017 is free, you only need to register in advance. I recommend not to postpone the registration at the last moment, and even more so on the day of the event, especially those who want to take part in laboratory work and competitions.
On the conference website you can also find a detailed description of the program and materials from VeeamON Forum Russia 2016 . Report on the forum-2015 was published in our blog on Habré.
Naturally, the number of users who want to work with backups of virtual and physical machines is growing using a single console. Therefore, our engineers decided to implement this feature in Veeam Backup & Replication, without delaying them, and I will tell you about it today. For details, welcome under cat.

I'll start with the look. Since Veeam Backup & Replication will now work with both virtual and physical machines, it was decided to bring the Inventory section that previously lived in the VMs view into a separate view. It will display all machines protected by Veeam, whether it is Veeam Backup & Replication or any of the Veeam Agents.
')

Logical Containers Protection Groups
In order to provide the ability to control and configure protection through the console, you need to create the appropriate logical containers - the so-called Protection Groups - and then the necessary objects will be placed there.
First of all, we deal with the type of objects for which we will configure protection. In the Type step of the wizard to create a protective group, there are several options:
- If we want to place individual computers into a container (group), we assign the type of Individual computers to a group. We get a static association (the changes are not picked up on the fly), in which computers can be added by specifying their IP address or domain name. Such groups are recommended to be used for small infrastructures where the Active Directory domain is not configured.
- If we want to have a dynamic group where we will place Microsoft Active Directory objects - we assign the group the type Microsoft Active Directory objects . This is a container of a dynamic type, where objects will automatically fall after being enabled, for example, in the Active Directory OU or security group. It is recommended to use such groups for infrastructures of any size working with Active Directory.
- If you have a rather large infrastructure, but you do not use Active Directory, or you have set up integration with CMDB, it is recommended to use protective groups that are replenished through the list of computers imported from a CSV file - Computers from CSV file .

Since organizations most likely will use groups for Active Directory objects, we’ll focus on them in more detail first.
If you selected the type of Microsoft Active Directory objects protection group, Veeam Backup & Replication server will automatically request information about the Active Directory structure of your home domain and display it.
Note: You can change the default setting and display as a selection area, for example, a subdomain or another domain in general. You can also exclude individual objects from the selection area — for example, you can exclude computer counts that were turned off during the last month, or you can exclude an entire OU.
So, we have indicated what area of choice our AD objects will be from. Veeam will install the Veeam Agent executable on these objects, which, in fact, will perform backups. Of course, to install agents, the Veeam Backup Service account must have appropriate permissions.
Then you need to specify how often we want to scan our selection area - this entity is dynamic, that is, as soon as new objects are found during the next scan, they will immediately be included in their protective group.
In the scan options (Step Options ) for a group of any type, you can choose whether we want the Veeam Agent to be automatically placed on the newly discovered objects - if we want, then we check the Install backup agent automatically (recommended) checkbox:

Backup
After we have properly grouped our computers, we set up a backup for them using an agent. To do this, select the desired protective group and create a new task for it (or include it in an existing one).

Job type
Depending on what machines we want to process, choose the type of task. It may be:
- Working page - then choose the option Workstation
- Server - choose, of course, Server
- And - by popular demand of the user audience! - Failover Cluster

Job control mode
At the same step, it is necessary to decide in which mode the agent responsible for backup will work. Depending on which type of protected machine was selected, either both or one of two options will be available:
- Centralized control from the server side Veeam backup ( Managed by backup server ).
If this mode was chosen, then a lightweight version of the Veeam Agent will be installed on the machines - without a GUI, without a local configuration database. All settings will need to be done on the server Veeam backup server.
In this embodiment, the server monitors all work, including remote start and stop the job, view statistics, etc.
This mode is convenient for backup machines that are always connected to the infrastructure. It will always be assigned for the backup of clusters, and will also be an option for the backup of servers. - Control over the task is performed by the agent ( Managed by agent ).
If you select this mode, then the full version of the Veeam Agent will be installed on the machines.
All schedule settings and task management are performed on the side of the agent itself.
This mode is convenient for backup machines, for which it is not always possible to provide a permanent connection to the infrastructure via a good channel, but for which, nevertheless, it is necessary to fulfill the RPO requirements. He will always be assigned to the backup of workstations, and will also be an option for the backup of servers.
Create a backup with running applications
At the Guest Processing step, you can specify that the backup should be created taking into account applications running on the machine (application consistency). The following applications are supported:
- SQL Server, including support for Always-On Groups,
- Oracle
- Exchange, including DAG support
- Active Directory
- SharePoint
To restore the objects of these applications from the backup, you can use the tools from the line of Veeam Explorers.
For SQL and Oracle databases, transaction log backups will be supported - to be able to recover to the selected point in time.

Invitation to VeeamON Forum Russia 2017
Yes, yes, this year we invite our readers and all those interested in participating in the VeeamON Forum 2017 Russia forum dedicated to the issues of data accessibility. The event will be held on October 26, the venue - Lotte Hotel Moscow.
In the forum program:
- Veeam expert stories about best practices, announcements of new versions of our products
- speeches by representatives of storage companies (NEC, Quantum, Infinidat) with a story about integrated solutions
- question and answer sessions
- prize draws
- 4 flows of laboratory work that will run in parallel with the main session
In addition, for anyone who knows and knows how to work with Veeam Availability Suite 9.5, there will be exciting LabWarz competitions. The prize for the victory - a certificate worth 30,000 rubles. for any training course at any Veeam certified training center.
Participation in the VeeamON Forum Russia 2017 is free, you only need to register in advance. I recommend not to postpone the registration at the last moment, and even more so on the day of the event, especially those who want to take part in laboratory work and competitions.
On the conference website you can also find a detailed description of the program and materials from VeeamON Forum Russia 2016 . Report on the forum-2015 was published in our blog on Habré.
Additional links:
Source: https://habr.com/ru/post/339710/
All Articles