Let them in passwords
Translator's note: The author of the article is a sociotechnical Security Researcher at the National Cyber Security Center of the United Kingdom (NCSC), a division of the Government Communications Center (GCHQ), which is responsible for maintaining electronic intelligence and ensuring the protection of information of government bodies and the army.
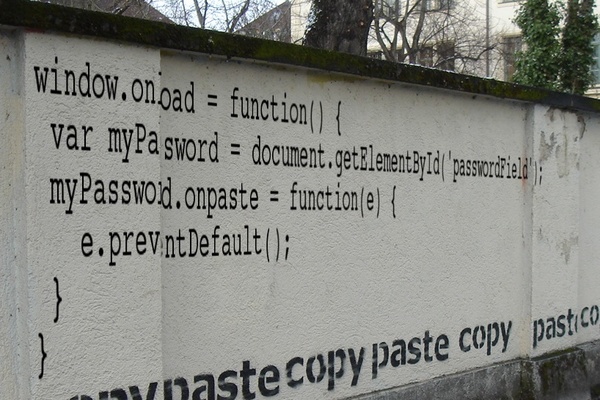
On Twitter, we are often sent examples of sites that block the insertion of a password from the clipboard. Why do sites do this? A discussion broke out - and most debaters point out that this is very annoying.
')
So why do organizations do this? Often they do not give any explanation, but if they do, they talk about "security." NCSC does not think these concerns are justified. We believe that password insertion blocking (BWP) is a bad practice that worsens security. We believe that users should be allowed to insert passwords.
It remains a mystery how the practice of BWP appeared. No one has seen any scientific article, research, rules, RFC (technical standard of the rules of the Internet) or something like that, where it all began. If you are familiar with something, let me know in the comments. We think this is where one of those “best practices” takes place, the ideas of which are born from the appeal to common sense. Previously, such an idea could make sense. Given the larger picture in our time, now she absolutely does not make any sense.
The main reason why password insertion improves security is that it reduces password congestion, which we talked about in our Password Guide . Permission to insert passwords makes web forms well compatible with password managers . Password managers are programs (or services) that pick up, store, and enter passwords in forms for you. They are very useful because:
Disclaimer: Although password managers can provide better security than, for example, storing passwords in a regular (i.e. unprotected) document on a computer, they are not a universal solution to all problems with passwords in an organization. In the next article we will describe in more detail what factors should be considered when choosing a password manager.
Imagine that you do not have a password manager and do not even have that insecure password document. Without password managers, it will be almost impossible to remember all passwords. In this case, you will have to choose one of the following bad choices:
That is why we consider BVP a bad practice, and permission to insert passwords is good. The advantages outweigh the disadvantages, and much more.
There are other reasons for trying to justify BVP. The small and misleading grain of truth in these arguments may sound very convincing. Let's figure it out.
If you allow the insertion of passwords, the malicious software or web page can continuously insert passwords until they find the right one.
This is indeed true, but it is also true that there are other ways to conduct brute-force (for example, through an API), which are just as easy for attackers, but much faster. The risk of attacks with the selection of passwords through copy-paste is very small.
In principle, this is also true: the more often you are forced to remember something, the easier it is to remember it the next time.
However, in the real world, people have to create passwords for services, which they very rarely use. This means that they do not have enough time to practice and small chances to remember something. This justification is true only if you initially assume that users must remember their passwords - and this is not always the case.
People also create passwords for services that they use so often that they cannot forget a password, even if they wanted to (which is rather inconvenient if you need to change the password regularly), and typing it into a crappy form again and again every day just takes them time. Password managers help in this situation, and BVP rejects them.
When a user makes a copy and paste, the copied content is stored in the clipboard, from where it can be pasted as many times as necessary. Any software on the computer (and anyone working with it) has access to the buffer and can view its contents. Copying new content is usually done on top of old content and destroys it.
Many password managers copy your password to the clipboard to paste it into a form on the website. There is a risk that the attacker (or malicious) will get the password before it is removed from the clipboard.
Clipboard passwords can be a bigger problem if they are manually copied from a document on a computer. You may forget to clean the buffer. But this is not such a big risk, because:
Instead of blocking the insertion of passwords, the first step is to protect your computer from malware, following the enterprise security guidelines . And updating software is the IT version of healthy eating and one of the best ways to protect your computer.
No need to think that only we speak out against blocking the insertion of passwords. See the Troy Hunt blog (with a “Historical lesson for all of us”) or this Wired article .
Improve security by supporting your users. Let them insert passwords.

On Twitter, we are often sent examples of sites that block the insertion of a password from the clipboard. Why do sites do this? A discussion broke out - and most debaters point out that this is very annoying.
')
So why do organizations do this? Often they do not give any explanation, but if they do, they talk about "security." NCSC does not think these concerns are justified. We believe that password insertion blocking (BWP) is a bad practice that worsens security. We believe that users should be allowed to insert passwords.
No one knows where it went.
It remains a mystery how the practice of BWP appeared. No one has seen any scientific article, research, rules, RFC (technical standard of the rules of the Internet) or something like that, where it all began. If you are familiar with something, let me know in the comments. We think this is where one of those “best practices” takes place, the ideas of which are born from the appeal to common sense. Previously, such an idea could make sense. Given the larger picture in our time, now she absolutely does not make any sense.
So why is inserting passwords good?
The main reason why password insertion improves security is that it reduces password congestion, which we talked about in our Password Guide . Permission to insert passwords makes web forms well compatible with password managers . Password managers are programs (or services) that pick up, store, and enter passwords in forms for you. They are very useful because:
- facilitate the storage of different passwords for different sites;
- improve productivity and prevent typing errors when entering passwords;
- simplify the use of long, complex passwords.
Disclaimer: Although password managers can provide better security than, for example, storing passwords in a regular (i.e. unprotected) document on a computer, they are not a universal solution to all problems with passwords in an organization. In the next article we will describe in more detail what factors should be considered when choosing a password manager.
Imagine that you do not have a password manager and do not even have that insecure password document. Without password managers, it will be almost impossible to remember all passwords. In this case, you will have to choose one of the following bad choices:
- reuse the same passwords on different sites;
- choose very simple (and therefore easily matched) passwords;
- record passwords and store them in places that are easy to find (such as Post-It leaves on the monitor).
That is why we consider BVP a bad practice, and permission to insert passwords is good. The advantages outweigh the disadvantages, and much more.
Why block the insertion of passwords (BVP) wrong
There are other reasons for trying to justify BVP. The small and misleading grain of truth in these arguments may sound very convincing. Let's figure it out.
Justification 1: "Inserting passwords makes brute force easier"
If you allow the insertion of passwords, the malicious software or web page can continuously insert passwords until they find the right one.
This is indeed true, but it is also true that there are other ways to conduct brute-force (for example, through an API), which are just as easy for attackers, but much faster. The risk of attacks with the selection of passwords through copy-paste is very small.
Justification 2: "Because of the insertion of passwords, it is more difficult to remember them, because you rarely type them manually"
In principle, this is also true: the more often you are forced to remember something, the easier it is to remember it the next time.
However, in the real world, people have to create passwords for services, which they very rarely use. This means that they do not have enough time to practice and small chances to remember something. This justification is true only if you initially assume that users must remember their passwords - and this is not always the case.
People also create passwords for services that they use so often that they cannot forget a password, even if they wanted to (which is rather inconvenient if you need to change the password regularly), and typing it into a crappy form again and again every day just takes them time. Password managers help in this situation, and BVP rejects them.
Justification 3: “The password will remain on the clipboard”
When a user makes a copy and paste, the copied content is stored in the clipboard, from where it can be pasted as many times as necessary. Any software on the computer (and anyone working with it) has access to the buffer and can view its contents. Copying new content is usually done on top of old content and destroys it.
Many password managers copy your password to the clipboard to paste it into a form on the website. There is a risk that the attacker (or malicious) will get the password before it is removed from the clipboard.
Clipboard passwords can be a bigger problem if they are manually copied from a document on a computer. You may forget to clean the buffer. But this is not such a big risk, because:
- Most password managers clear the clipboard as soon as they insert a password on the website, and some do not use the buffer at all by typing the password on the virtual keyboard.
- Internet Explorer 6 web browser provides malicious pages with access to the clipboard; but very few people use this browser.
- Viruses on the computer can copy the contents of the buffer and get passwords. But this is still not a good excuse for BVP; if your computer is infected with a virus, then you cannot trust it at all. Viruses and other malware that copies the clipboard almost always register all keystrokes, all numbers and characters, including passwords. They will know your password regardless of whether you copy it from the clipboard or enter it manually, so BVP gives you a little.
Instead of blocking the insertion of passwords, the first step is to protect your computer from malware, following the enterprise security guidelines . And updating software is the IT version of healthy eating and one of the best ways to protect your computer.
Not only our words
No need to think that only we speak out against blocking the insertion of passwords. See the Troy Hunt blog (with a “Historical lesson for all of us”) or this Wired article .
Improve security by supporting your users. Let them insert passwords.
Source: https://habr.com/ru/post/339476/
All Articles