Sometimes they come back. Mobile Banker BankBot again in Google Play
The mobile banker, which we first talked about at the beginning of the year, has acquired new opportunities and is again being distributed through Google Play.
During the year BankBot evolved, its versions appeared on Google Play and on unofficial sites. Finally, on September 4, we found the first option on Google Play that combines all the features of evolution: improved code obfuscation, complicated functions for delivering the main components, a complex infection mechanism using the accessibility service Android Accessibility Service.

The ability to use the Android Accessibility Service previously demonstrated several Trojans that were distributed mainly outside of Google Play. Recent studies by SfyLabs and Zscaler have confirmed that BankBot operators have added an application to Google Play that uses special features, but without a banker component.
')
“The developed puzzle” with the function of the banker entered Google Play under the guise of the game Jewels Star Classic. It is important to note that the attackers used the name of the popular legitimate line of games of the developer ITREEGAMER, which is not associated with a malicious campaign.
We notified Google security about a malicious application. However, the application installed approximately 5,000 users before it was removed.
When a user downloads the Jewels Star Classic developer GameDevTony (picture below), he gets a working Android game with hidden add-ons — a banker component hiding among game resources and a malicious service waiting in the hour after the predefined time delay.
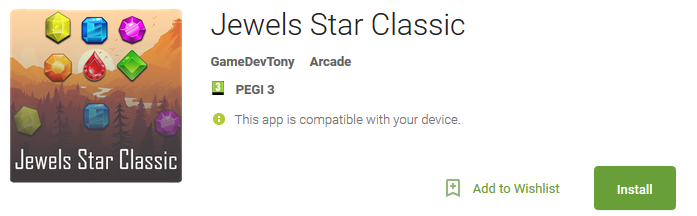
Figure 1. Malicious app on Google Play
The malicious service is activated 20 minutes after the first execution of Jewels Star Classic. The infected device displays a message with a suggestion to include something called Google Service (a malicious notification appears regardless of the user's current activity, with no explicit connection to the game).
The only way to remove the notification from the screen is to click "OK". After that, the user is redirected to the accessibility menu of Android Accessibility, where services with these functions are managed. Among the legitimate in the list appears a service called Google Service, created by malware. The service description copies the original Google Terms of Service.
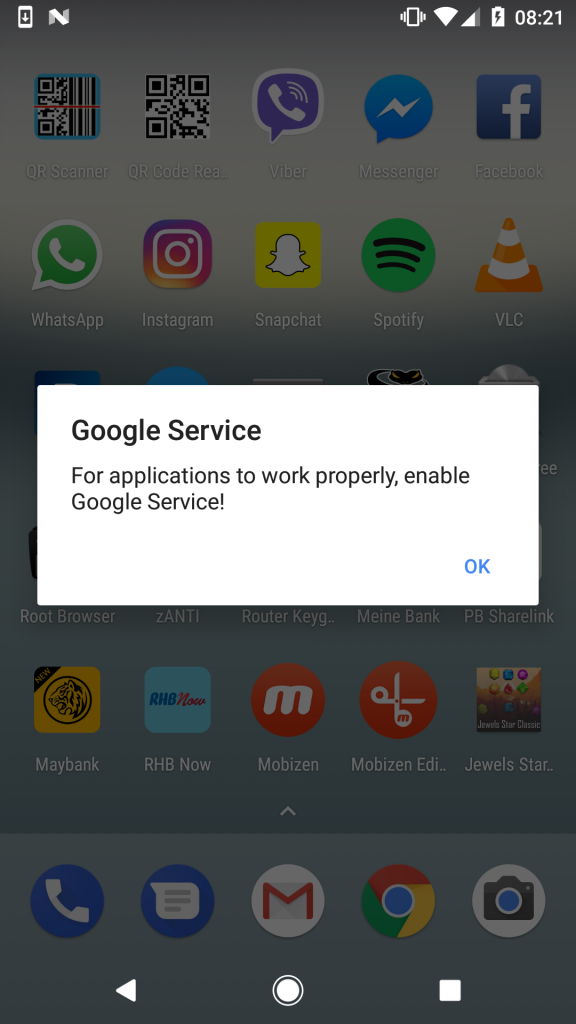
Figure 2. A notification prompting the user to enable Google Service
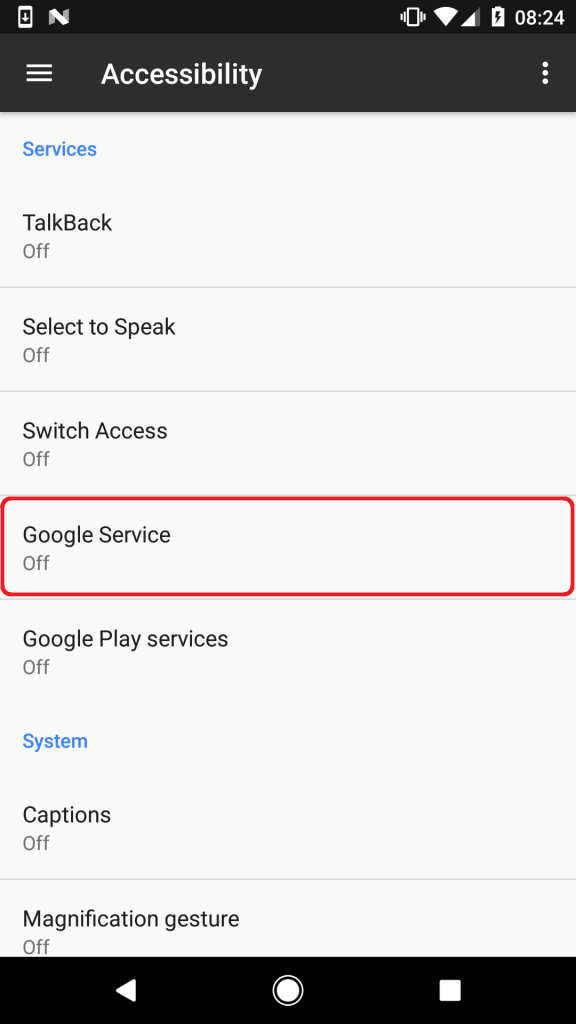
Figure 3. Google Service listed among Android Accessibility services
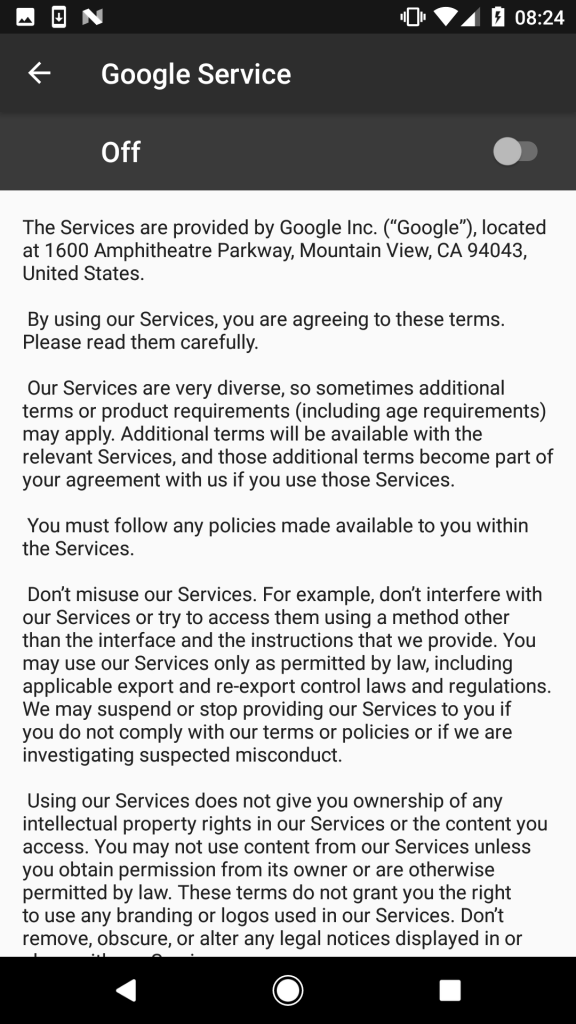
Figure 4. Malware description from Google’s user agreement
Deciding to activate the service, the user will see a list of required permissions: watching your actions, getting the contents of the window, turning on Explore by Touch, turning on improved web accessibility and managing gestures (Figure 5).
Clicking on the “OK” button allows the use of special access services. By giving these permissions, the user gives the banker complete freedom of action that is required to continue his malicious activity.
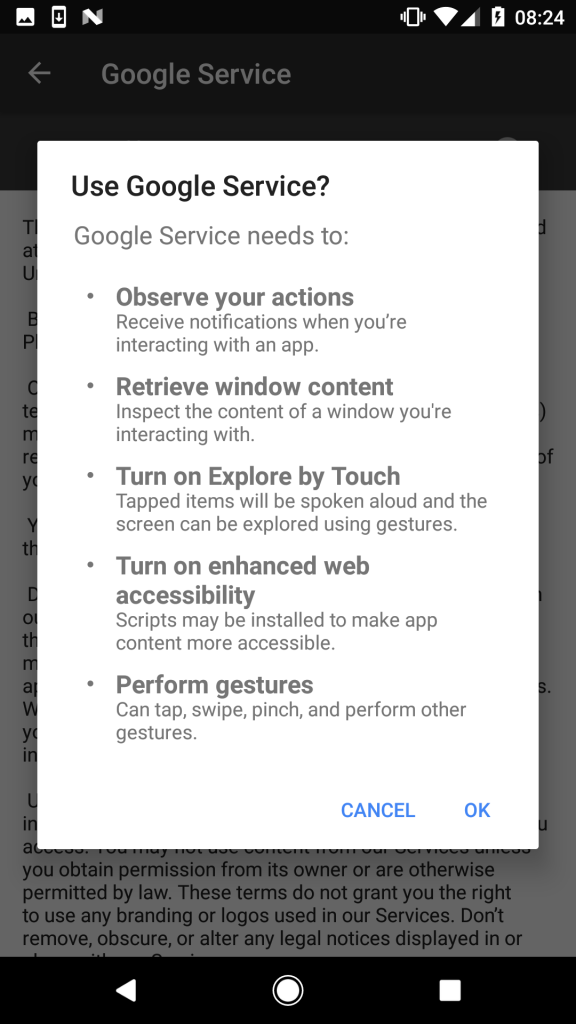
Figure 5. Permissions required to activate Google Service
In practice, after accepting these permissions, the user will be temporarily denied access to the screen due to updating the Google Service; in fact, it is not related to Google and works as a foreground process (Figure 6).
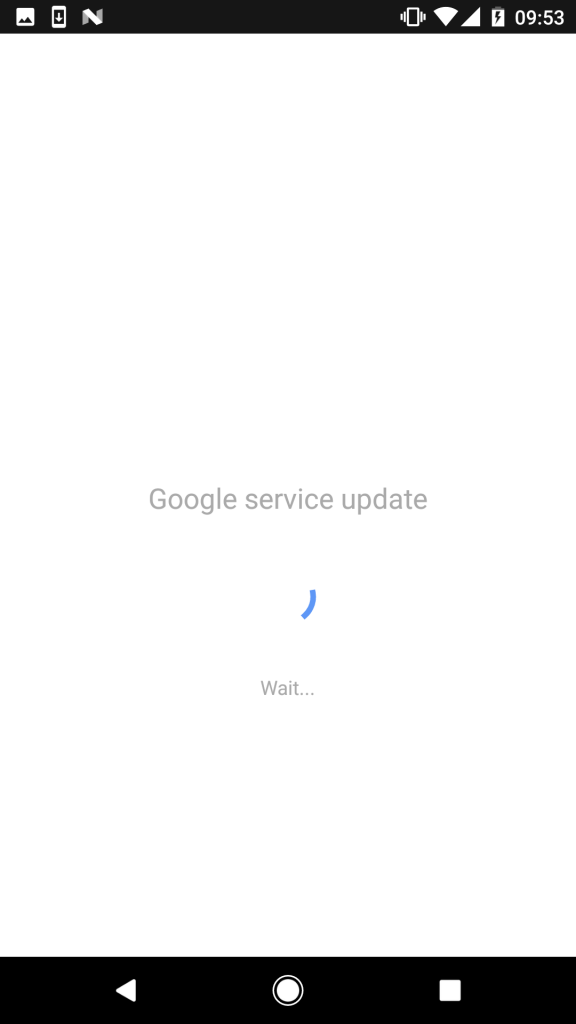
Figure 6. Screen that hides malicious activity
Malware uses this screen to hide the next steps — using the obtained special access permissions. While the user is waiting for a dummy update to download, the malware performs the following tasks:
After successfully completing these tasks, the malware can start working on the next one — stealing the victim’s credit card information. Unlike other BankBot variants that target mobile banking applications and simulate login and password forms, this version “specializes” exclusively on Google Play, an application preinstalled on every Android device.
When a user launches the Google Play application, BankBot enters and overlaps the legitimate application screen with a fake form to fill in the user's credit card information (Figure 7).
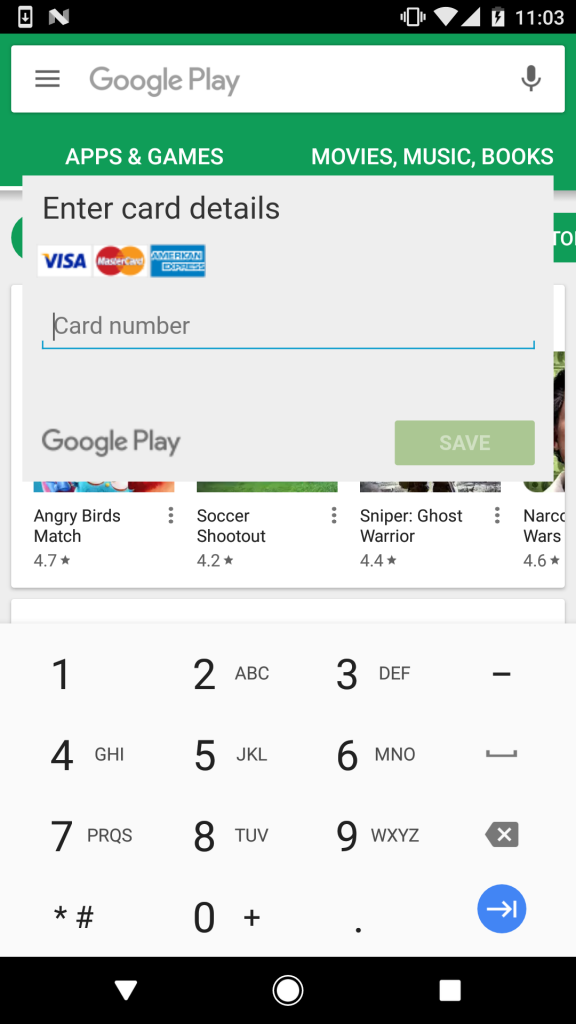
Figure 7. Simulation of the form to fill in the data of the user's bank card
If the user did not recognize the fake and entered the bank card data, the attackers achieved success. By setting BankBot as the default messaging application, malware intercepts all SMS messages that pass through an infected device. This allows attackers to bypass the bank’s two-factor authentication, which is the last possible obstacle between them and the victim’s bank account.
In this campaign, attackers put together several techniques that are becoming increasingly popular among malware authors for Android: using the Android Accessibility Service, masking under Google, and setting a timer that defers the execution of malicious activity to bypass Google’s security measures.
These techniques make it difficult to timely recognize the threat of a victim. Since the malware pretends to be Google and waits 20 minutes before the first notification is shown, the user has little chance of associating her activity with the recently downloaded Jewel Star Classic application. Finally, many of the names used by malware in the infection process make it difficult to locate the threat and remove it manually.
If you often download apps from Google Play and other sites, you should check the presence / absence of BankBot on your device.
Making sure there is no Jewels Star Classic is not enough, since attackers often change the applications used to distribute BankBot. To find out if the device has been infected, we recommend checking the following symptoms:

Figure 8. Malicious applications in the application manager

Figure 9. BankBot disguised as a system update in the list of active device administrators
Any of these signs indicates a possible infection with a new variant of BankBot.
To remove the malware manually, cancel the device administrator rights for the System update, then remove Google Update and the corresponding trojanized application.
The search for a trojanized application that launched an infection (in our case, it is Jewels Star Classic) is difficult due to the 20-minute delay in the start of malicious activity, and also because it works in the expected way. We recommend using a reliable mobile device security solution to detect and remove a threat with all its components.
ESET products detect this BankBot version as Android / Spy.Banker.LA.
In addition to using a reliable solution for the security of mobile devices, there are several preventive measures:
Samples / Indicators of compromise
Package Name / Hash
com.mygamejewelsclassic.app B556FB1282578FFACDBF2126480A7C221E610F2F
com.w8fjgwopjmv.ngfes.app 4D3E3E7A1747CF845D21EC5E9F20F399D491C724
During the year BankBot evolved, its versions appeared on Google Play and on unofficial sites. Finally, on September 4, we found the first option on Google Play that combines all the features of evolution: improved code obfuscation, complicated functions for delivering the main components, a complex infection mechanism using the accessibility service Android Accessibility Service.

The ability to use the Android Accessibility Service previously demonstrated several Trojans that were distributed mainly outside of Google Play. Recent studies by SfyLabs and Zscaler have confirmed that BankBot operators have added an application to Google Play that uses special features, but without a banker component.
')
“The developed puzzle” with the function of the banker entered Google Play under the guise of the game Jewels Star Classic. It is important to note that the attackers used the name of the popular legitimate line of games of the developer ITREEGAMER, which is not associated with a malicious campaign.
We notified Google security about a malicious application. However, the application installed approximately 5,000 users before it was removed.
Principle of operation
When a user downloads the Jewels Star Classic developer GameDevTony (picture below), he gets a working Android game with hidden add-ons — a banker component hiding among game resources and a malicious service waiting in the hour after the predefined time delay.

Figure 1. Malicious app on Google Play
The malicious service is activated 20 minutes after the first execution of Jewels Star Classic. The infected device displays a message with a suggestion to include something called Google Service (a malicious notification appears regardless of the user's current activity, with no explicit connection to the game).
The only way to remove the notification from the screen is to click "OK". After that, the user is redirected to the accessibility menu of Android Accessibility, where services with these functions are managed. Among the legitimate in the list appears a service called Google Service, created by malware. The service description copies the original Google Terms of Service.

Figure 2. A notification prompting the user to enable Google Service

Figure 3. Google Service listed among Android Accessibility services

Figure 4. Malware description from Google’s user agreement
Deciding to activate the service, the user will see a list of required permissions: watching your actions, getting the contents of the window, turning on Explore by Touch, turning on improved web accessibility and managing gestures (Figure 5).
Clicking on the “OK” button allows the use of special access services. By giving these permissions, the user gives the banker complete freedom of action that is required to continue his malicious activity.

Figure 5. Permissions required to activate Google Service
In practice, after accepting these permissions, the user will be temporarily denied access to the screen due to updating the Google Service; in fact, it is not related to Google and works as a foreground process (Figure 6).

Figure 6. Screen that hides malicious activity
Malware uses this screen to hide the next steps — using the obtained special access permissions. While the user is waiting for a dummy update to download, the malware performs the following tasks:
- allows installation of applications from unknown sources
- installs the BankBot from the set and runs it
- activates administrator rights for BankBot
- sets BankBot as default SMS exchange application
- gets permission to show on top of other applications
After successfully completing these tasks, the malware can start working on the next one — stealing the victim’s credit card information. Unlike other BankBot variants that target mobile banking applications and simulate login and password forms, this version “specializes” exclusively on Google Play, an application preinstalled on every Android device.
When a user launches the Google Play application, BankBot enters and overlaps the legitimate application screen with a fake form to fill in the user's credit card information (Figure 7).

Figure 7. Simulation of the form to fill in the data of the user's bank card
If the user did not recognize the fake and entered the bank card data, the attackers achieved success. By setting BankBot as the default messaging application, malware intercepts all SMS messages that pass through an infected device. This allows attackers to bypass the bank’s two-factor authentication, which is the last possible obstacle between them and the victim’s bank account.
What is dangerous BankBot
In this campaign, attackers put together several techniques that are becoming increasingly popular among malware authors for Android: using the Android Accessibility Service, masking under Google, and setting a timer that defers the execution of malicious activity to bypass Google’s security measures.
These techniques make it difficult to timely recognize the threat of a victim. Since the malware pretends to be Google and waits 20 minutes before the first notification is shown, the user has little chance of associating her activity with the recently downloaded Jewel Star Classic application. Finally, many of the names used by malware in the infection process make it difficult to locate the threat and remove it manually.
How to clean the infected device?
If you often download apps from Google Play and other sites, you should check the presence / absence of BankBot on your device.
Making sure there is no Jewels Star Classic is not enough, since attackers often change the applications used to distribute BankBot. To find out if the device has been infected, we recommend checking the following symptoms:
- Availability of an application called Google Update (Figure 8: located in the Settings> Application manager / Apps> Google Update menu)
- An active device administrator called System update (Figure 9: located in Settings> Security> Device administrators).
- Repeat Google Service Notification (Figure 2)

Figure 8. Malicious applications in the application manager

Figure 9. BankBot disguised as a system update in the list of active device administrators
Any of these signs indicates a possible infection with a new variant of BankBot.
To remove the malware manually, cancel the device administrator rights for the System update, then remove Google Update and the corresponding trojanized application.
The search for a trojanized application that launched an infection (in our case, it is Jewels Star Classic) is difficult due to the 20-minute delay in the start of malicious activity, and also because it works in the expected way. We recommend using a reliable mobile device security solution to detect and remove a threat with all its components.
ESET products detect this BankBot version as Android / Spy.Banker.LA.
How to protect yourself?
In addition to using a reliable solution for the security of mobile devices, there are several preventive measures:
- If possible, use official app stores, not alternative sources. And although they are not perfect, Google Play does apply advanced security mechanisms, which third-party stores do not.
- Check applications before downloading - view the number of downloads, rating and reviews.
- After starting any installed application, pay attention to permission requests.
Samples / Indicators of compromise
Package Name / Hash
com.mygamejewelsclassic.app B556FB1282578FFACDBF2126480A7C221E610F2F
com.w8fjgwopjmv.ngfes.app 4D3E3E7A1747CF845D21EC5E9F20F399D491C724
Source: https://habr.com/ru/post/339158/
All Articles