Information security in process control systems: attack vector interface converters
Thinking
Some time ago I attended one conference dedicated to information security, there they discussed all the issues of different security in different systems. In my main specialty I do not have a direct relationship to security and I have many questions and thoughts on this topic, which was the beginning of the study of information security issues in automated control systems.
One guy gave a talk on information security in an automated process control system, told that for a long time the evolution of automation systems was a parallel course with the development of IT systems and that over time, systems built on modern IT technologies began to be used to control automation systems. And that at the present time the interconnection of the technological network with the corporate network is necessary for production management as well as for the administration of the entire system. The vector of attacks from IT systems has shifted to production and industrial networks. He told about a factory somewhere in Germany, which was able to make an attack and disrupt the technological process, as a result of which the foundry production fell and suffered huge losses, and the foundry had to disassemble and still have many terrible stories. Well, in general, the report did not make the necessary (frightening) impression. Those present at the event began to ask questions and discuss, "they say to whom we need small companies with minimal turnover of money, saying that there are real confirmations of incidents with attacks on enterprises in Russia."
The guy could not give examples: either he was not ready, or did not have the right to disclose the information he owned. So why this story?
After this event, I wondered why people responded so well to his speeches, because he was well-versed with terms and international statistics on attacks on objects, but people felt that these attacks are unlikely and do not pose a threat to them. That is what prompted me to do research in the field of information security of ACS TP.
')
Some theory
Consider the atypical direction of attack on interface converters, since There is a lot of information about attacks on PCs, PLCs and the system as a whole, but few people thought that almost every production has all the various systems of devices, sensors, devices and there is a problem of compatibility of various types of devices. There is a huge variety of devices of various types and purposes, a large number of companies engaged in their production, different standards, mostly incompatible with each other. The way out of this situation are interface converters. All of them are used to connect devices with RS-232/422/485 interface, and these are data acquisition systems, recorders, controllers, sensors, terminals, and more. But it is not enough just to connect the ports. It is necessary to establish communication at the program level, which is a more difficult task. Different device standards can transfer data using different technologies. To unify the protocols to bring the transmitted data to a single form with the help of converters is not possible, but it is possible to adapt the type of data transmitted between different parts of the system by different protocols so that they are successfully received and decrypted by an element using a different protocol.
And those who operate real-world systems for automated process control systems know how diverse the equipment and parts of this system are sometimes, which in some cases have been working on the production for about 10-15 years and sometimes have to put another system on top of one system and achieve its coalescence so that everything interacts. between themselves. This is where interface converters fit like never before. Conversion of packets, transmitted data occurs at the software level. In addition to directly changing the structure of the transmitted data, the software component of the converter is responsible for determining the types of protocols used in the system and choosing the algorithm for their coordination.
Interface converter is a modern and effective means of expanding the functionality of an information system, indispensable in the absence of a single standard for building all the various data transmission systems.
And now let's think about it. We use converters on all figurative objects, connect all the various devices (protection terminals, sensors, counters) and all other possible devices to them. But after all, all the information from the object to the client passes through them and it is worth gaining access to them, as we can find out a lot of information that will give us the direction of the attack on the end devices or allow us to receive, replace or send information on behalf of these devices.
To practice
We will conduct an experiment with very popular converters of Taiwanese company MOXA Nport of different versions. We will use free software and allowed resources at the levels of ordinary users.
There is such a very interesting resource on the Internet www.shodan.io allows you to find devices on the global Internet, to which you have access and see where they are. Perform a simple scan with input in the search box Moxa Nport. We look and wonder what is happening in the world. It should be borne in mind that some organizations send a written ban on scanning their subnet to the company www.shodan.io .
In general, we found 7260 devices on request for Moxa Nport worldwide. Then we study how to get access to devices. We notice that for the most part 22, 23, 80, 443 ports are open and through them you can safely connect to devices.

Taiwan

Poland

Lipetsk

China
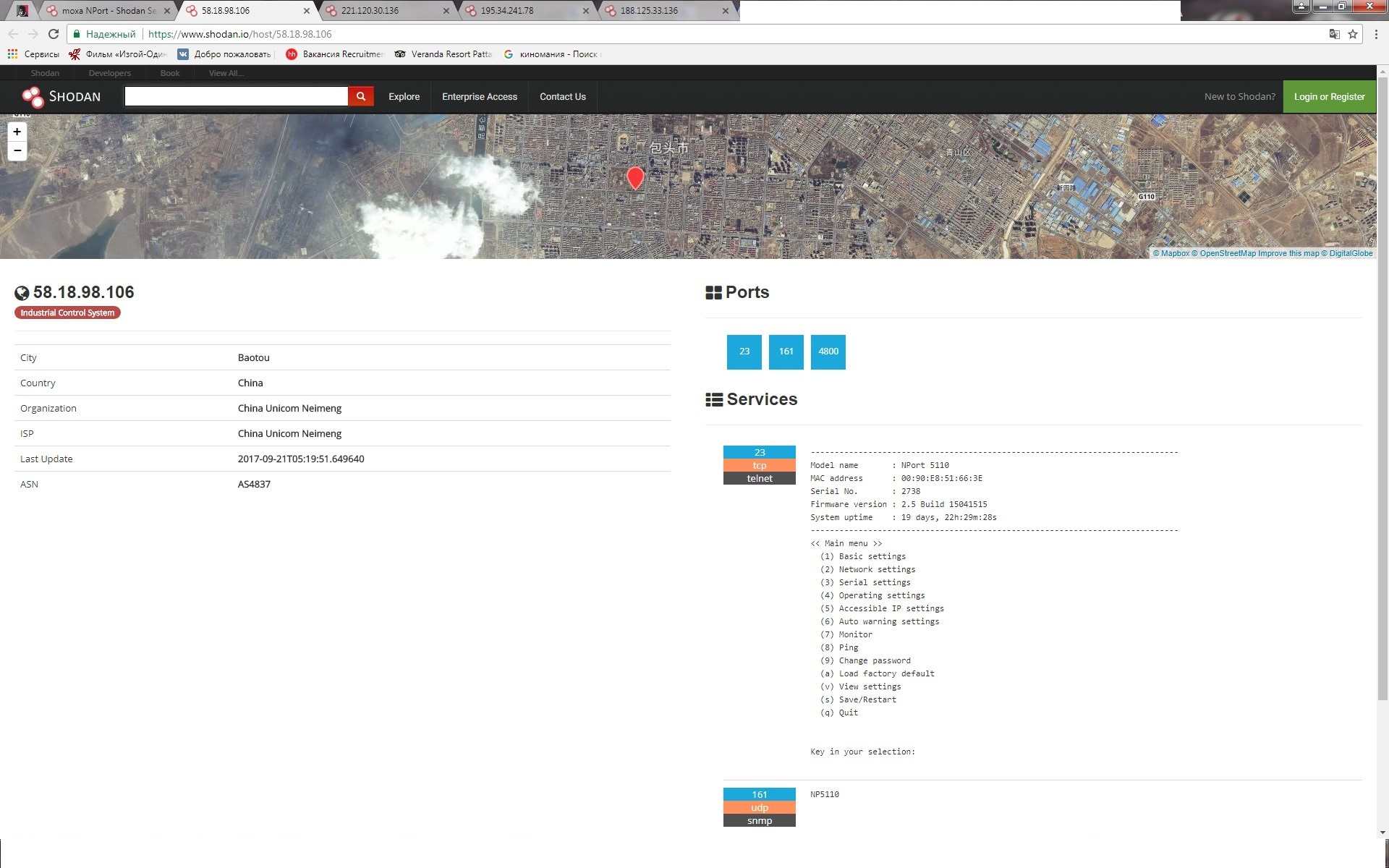
Kazan
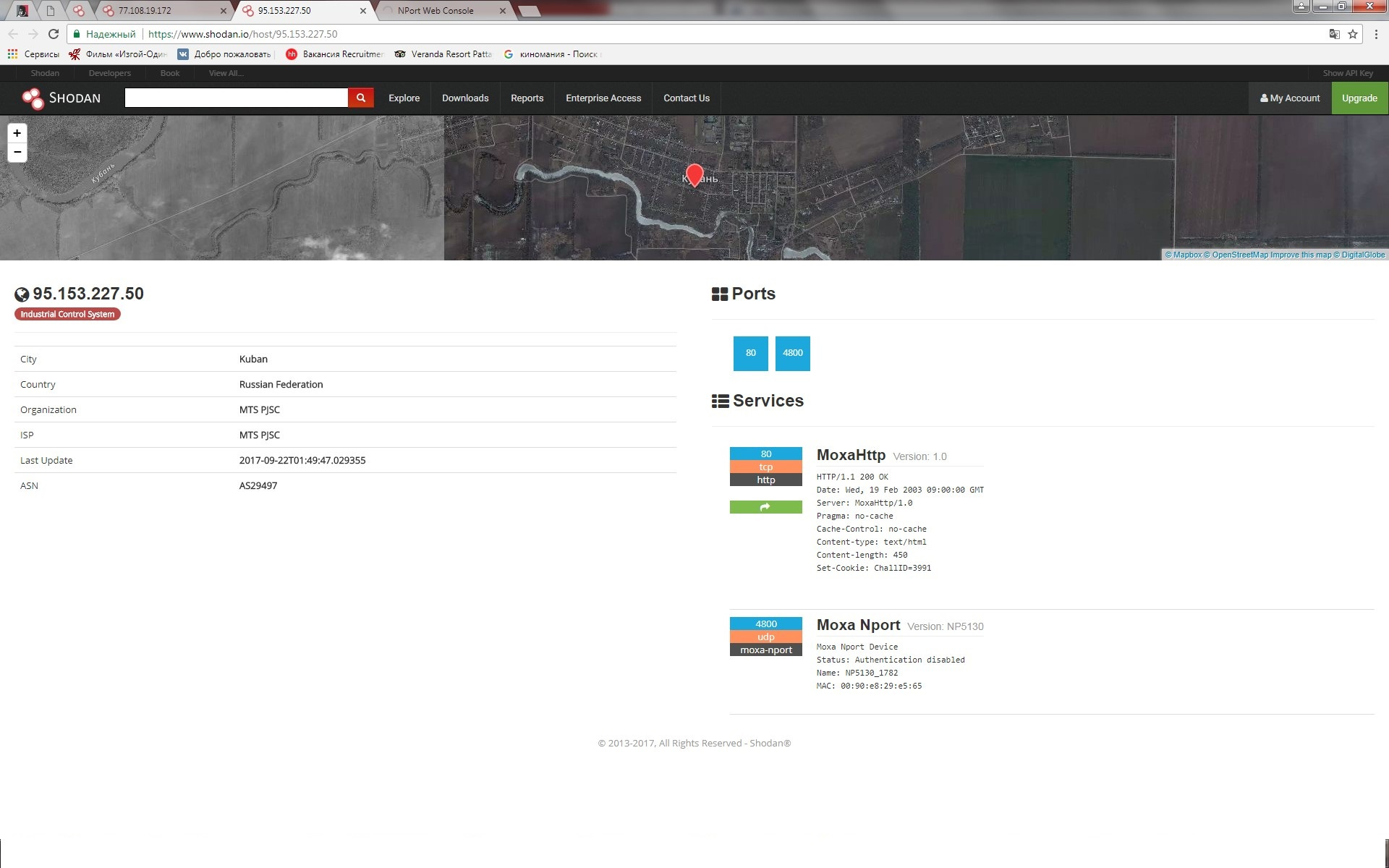
Taiwan

In some cases, the devices are factory default accounts, to know the username and password is not difficult.
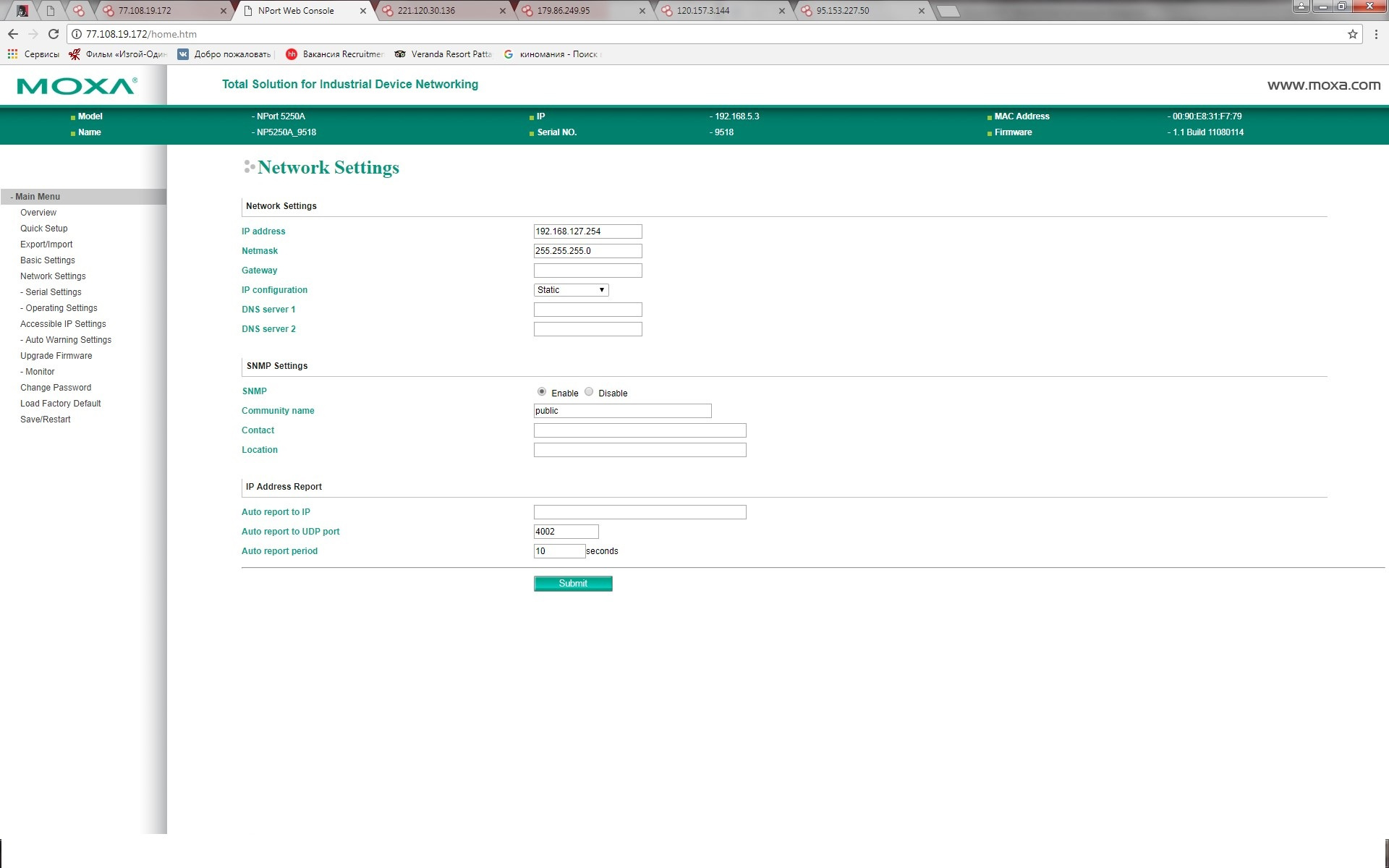
We fall on the device and look at all that is needed, we make sure that there are administrator rights.
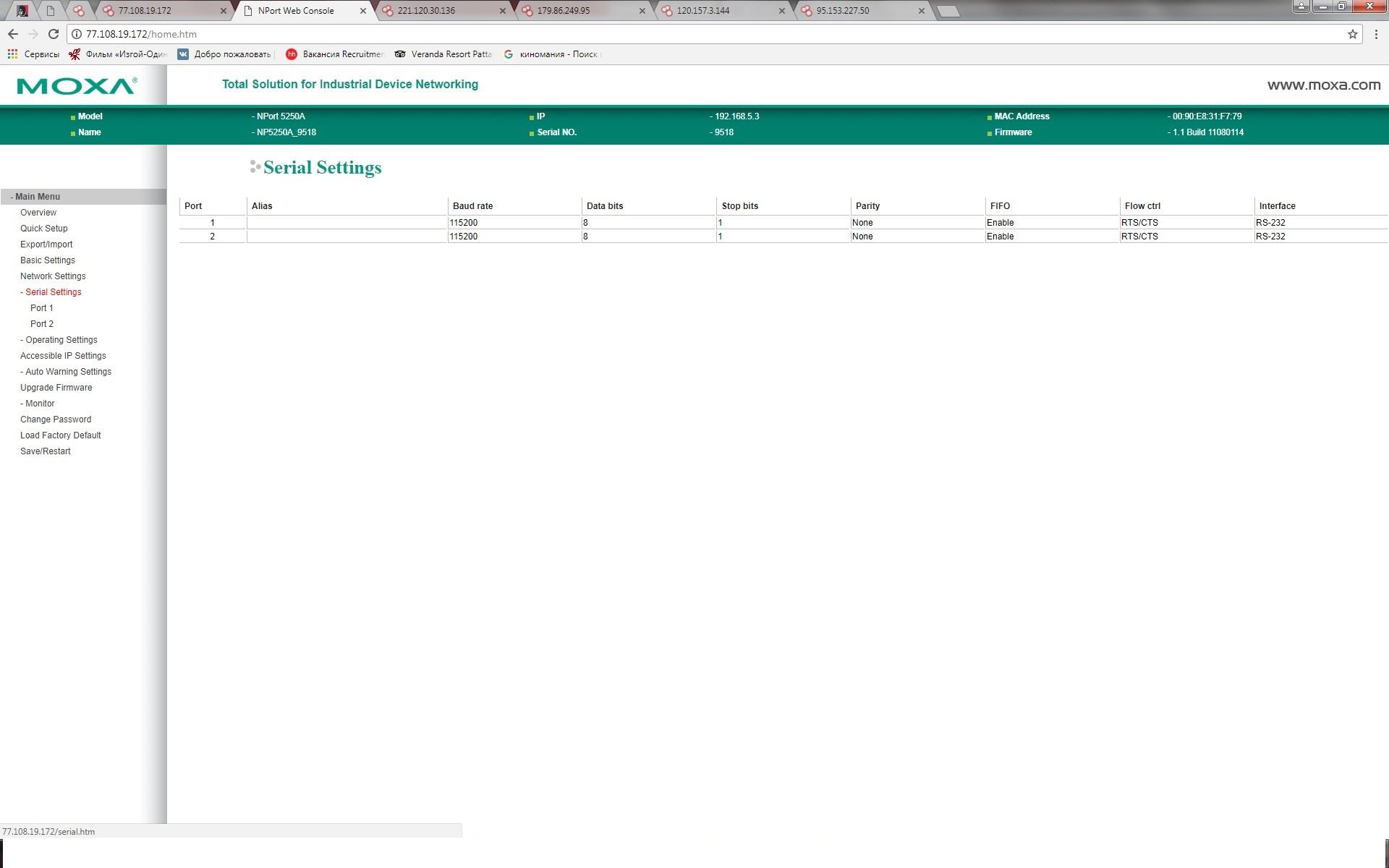
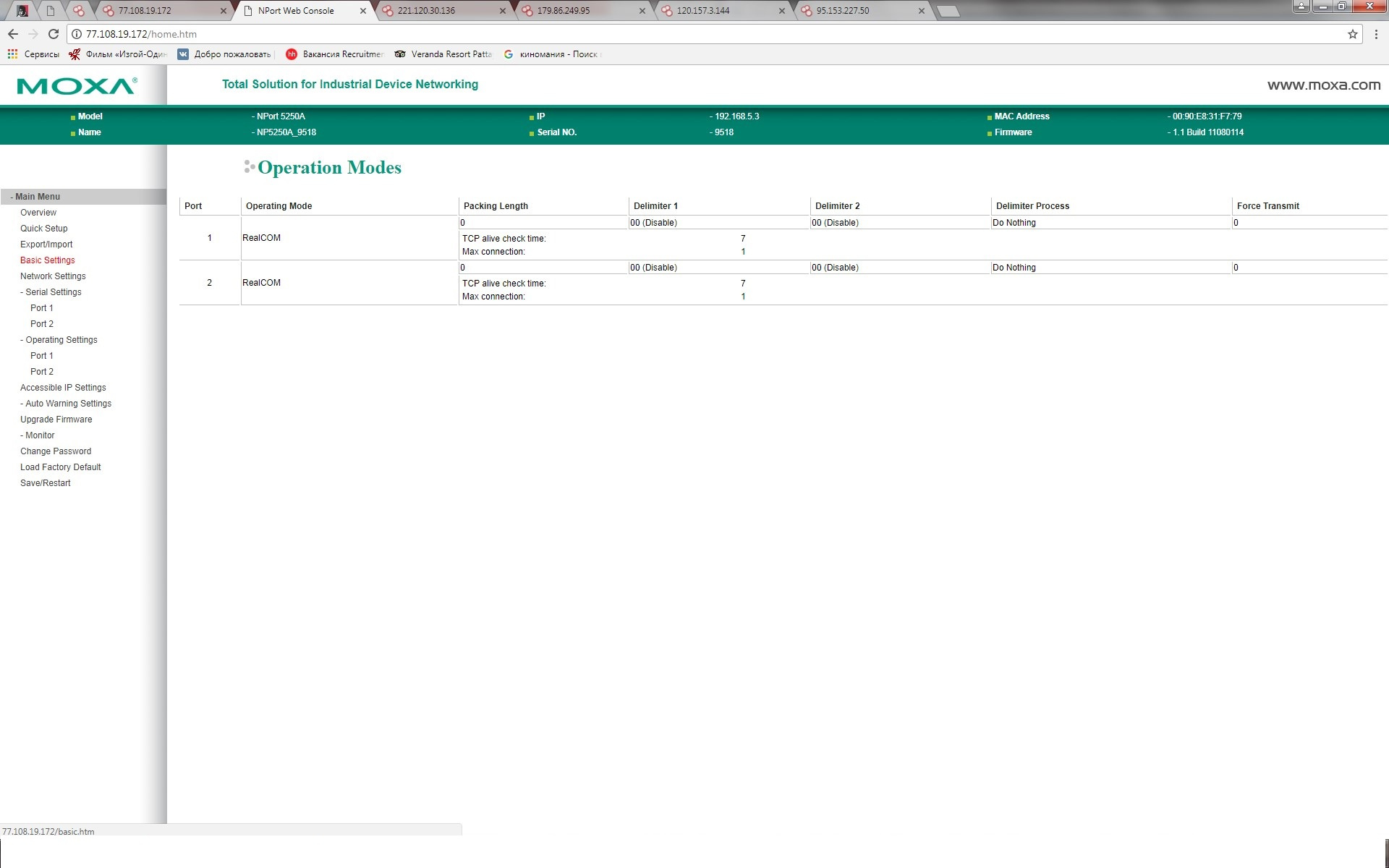
We can both view all the information and change it.
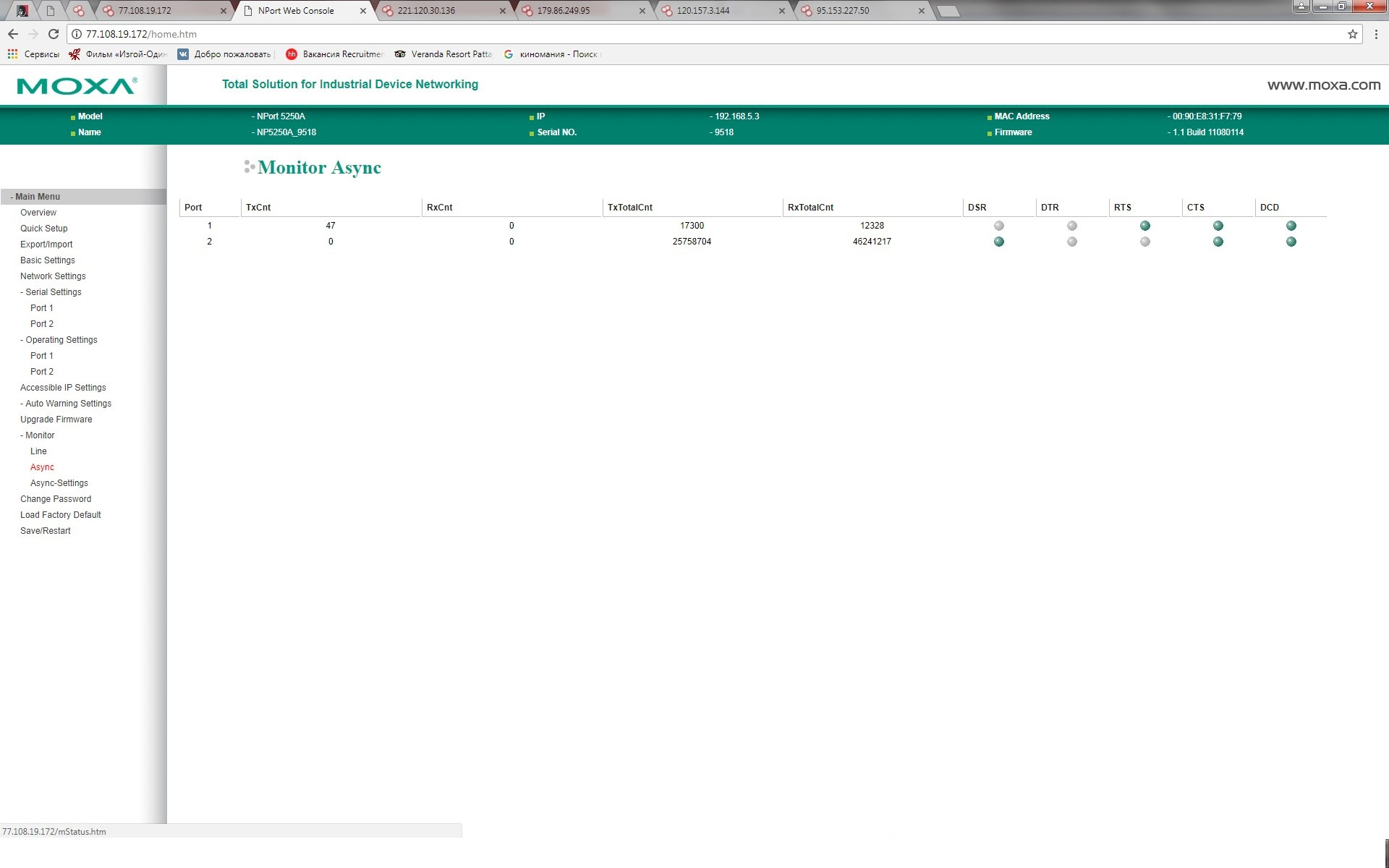
Some users set a non-standard password and close port 80, but www.shodan.io still has the ability to view useful information on other ports that can be used to develop the attack vector. The name of the device, its status, MAC address, SSL certificate, its version and much more.

And all this can serve as a good help in planning and organizing attacks. The more you know the information about the object, the greater the chance that you can use it to attack.

Nowadays, even those devices that were tampered with a brute force hack will not take it, and since most of these devices are not always configured by experts, there is no limit on the number of password entry attempts that could greatly help from brute force.
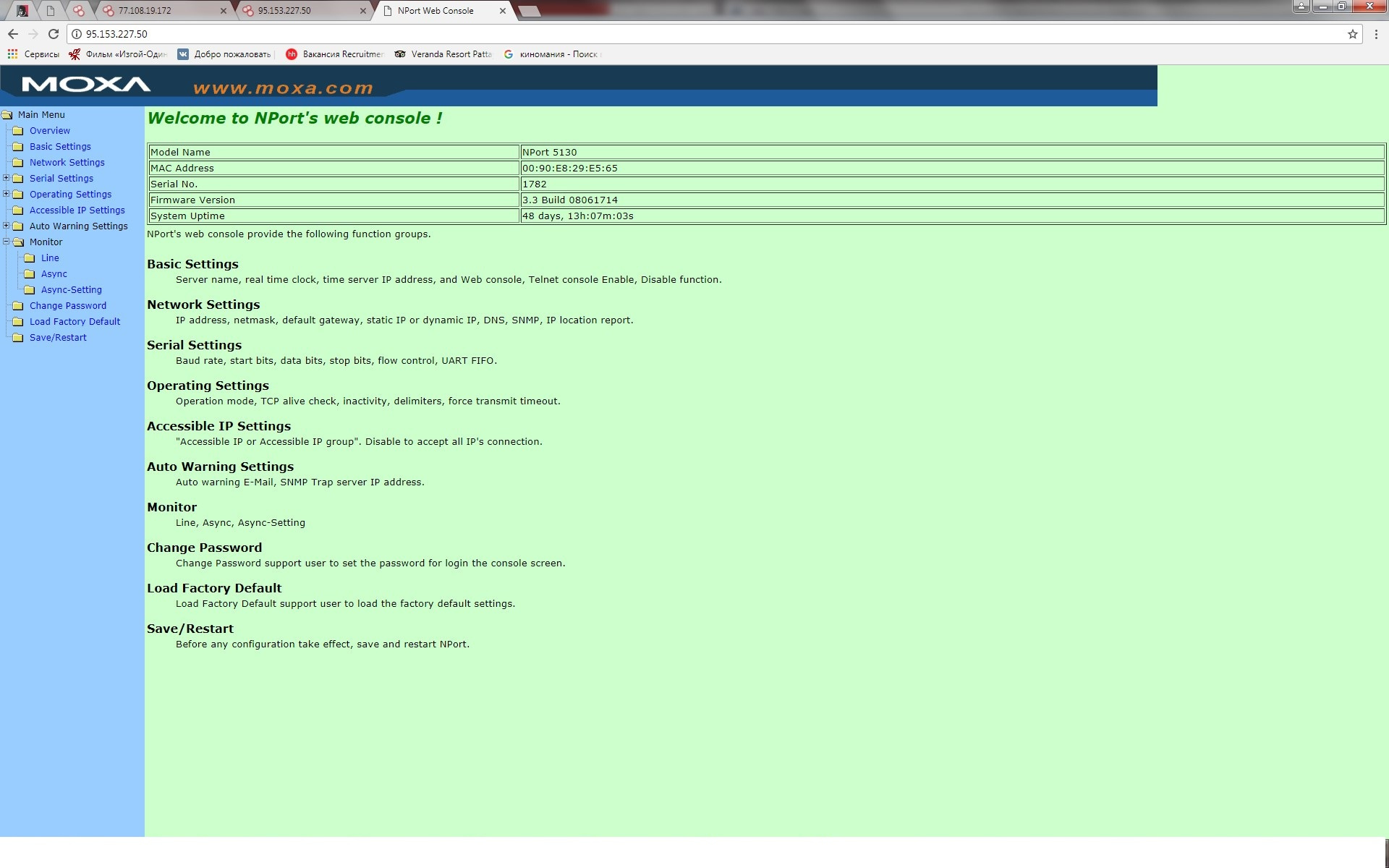
But this is only the beginning, we use standard pairs (and there were quite a few such devices in Russia, the Czech Republic, Poland, Italy, Australia, and in many other countries).
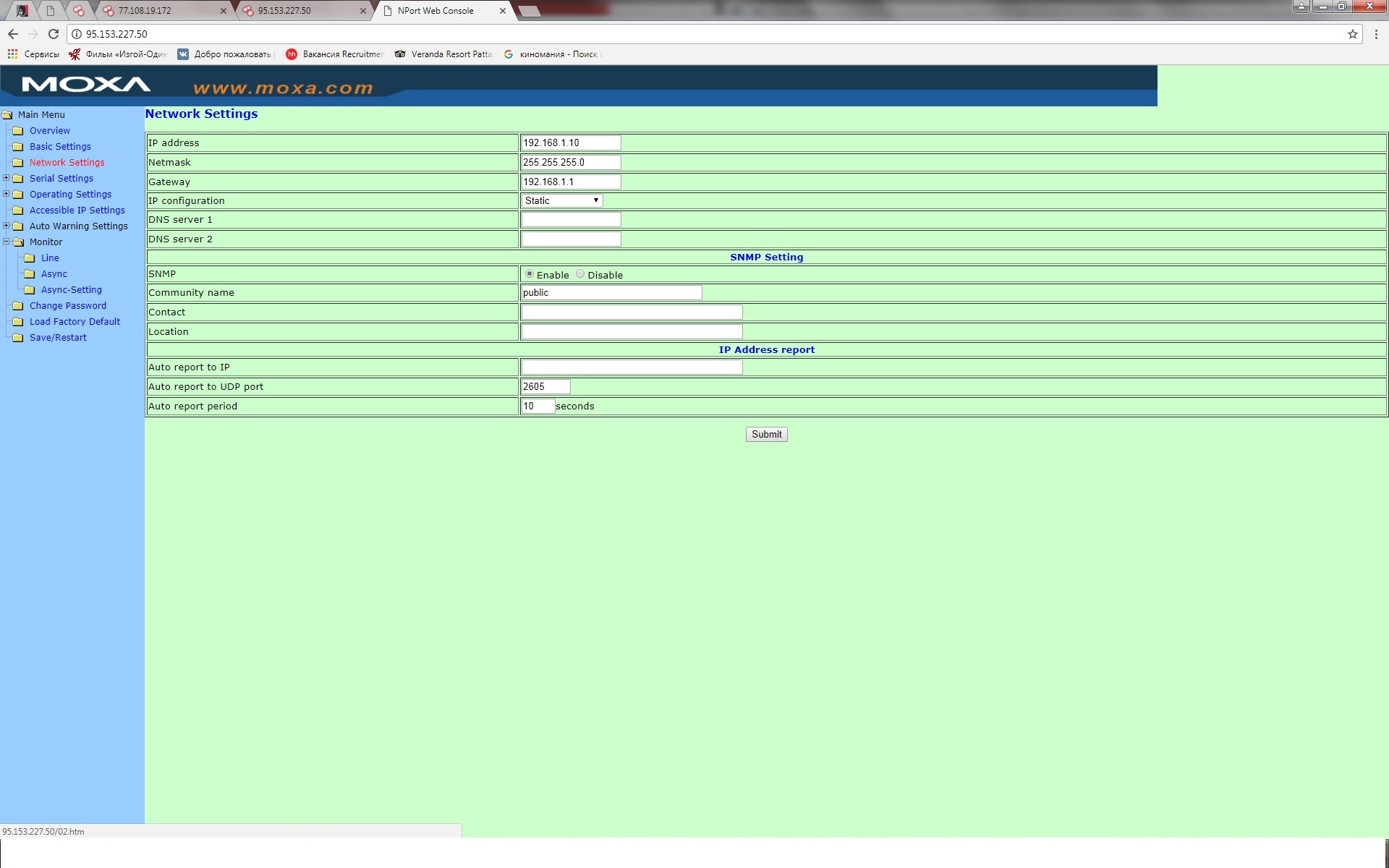
We get not limited access to the device and we can analyze both internal information (the internal network where the device is located, find out the address range and gateway address) and analyze what devices are connected to converters, analyze the amount of information transmitted, and much more.

And change passwords and reboot, in general, unlimited administrator rights.
We all were able to do this simply without having professional knowledge and the necessary specialization. And now let's drip a little deeper, let's say that we have experience with this equipment and devices, we are a little knowledgeable about information security and we know where to look for officially posted vulnerabilities.
Yes, gentlemen, all known vulnerabilities are laid out on the network on professional, specialized sites. You will not believe my surprise when I learned that everything is publicly available, and I am not an information security specialist.
We pass on ics-cert.us-cert.gov and in the search engine simply indicate the equipment we are interested in and have an official list of recognized vulnerabilities from the MOXA company and this list is diverse.

Google further and learn that the exploitation of vulnerabilities allows attackers to perform various actions on the device unnoticed. Taiwan MOXA’s equipment is vulnerable to vulnerabilities allowing a remote, unauthorized user to gain administrative access to devices and important information stored in unencrypted form. Also, an attacker can perform a CSRF attack. Successful exploitation of these vulnerabilities allows an attacker to quietly execute various commands, change the password, settings, and reboot the device.
The emergence of problems is a consequence of insufficient protection systems for industrial control systems in general. For example, converters are supplied without a password or with a standard factory password and account (CVE-2016-2286). Like many devices for ACS systems, which allows any user to gain access to the device with administrator rights via TCP / 80 (HTTP) and TCP / 23 (Telnet). Currently, according to the manufacturer, there is no information on cases of active exploitation of errors. And the manufacturer recommended at one time to simply disable TCP / 80 (HTTP) and TCP / 23 (Telnet) ports.

CVE-2016-0875 Allows a remote user to elevate their privileges and access configuration and log files using a specially formulated URL.
CVE-2016-087 A remote attacker can cause a denial of service by sending a specially formulated request.
CVE-2016-0877 is related to the PING function, and its operation can lead to data leaks.
CVE-20164500 affects embedded computers uc7408 lx plus allows a remote authorized user to interrogate devices and cause a failure in the work.
CVE-016-8717 experts found in the MOXA devices hard-coded credentials that allow you to log into an undocumented account.

Researchers and various specialists regularly find, in addition to vulnerabilities, bugs, and outdated software, backdoors. On the security of the Internet of things in general, they are talking more and more, but from such large manufacturers of communication equipment, such as the MOXA company, no one expected anything like that. After all, problems have been discovered in a number of cases, ranging from problems with authentication, which allows for dictionary attacks, a lot of XSS bugs in the web interface, DoS vulnerabilities, the ability to inject commands.
For most problems, the manufacturer has released corrective firmware updates that eliminate a number of vulnerabilities, in other cases, MOXA has decided to stop the release of some devices due to the inability, and sometimes not the desire to eliminate the vulnerabilities.
Having learned about such vulnerabilities from such a large manufacturer, everyone who uses the equipment of this company should think about updating the firmware, changing passwords, and device settings. But in the practice of process control systems, everything is much more complicated. On the production equipment that does not ever have been updated, or can not be updated in connection with the technology of continuous production. And here there are even more questions, but this is another story and another attack vector.
Let's talk about the results of the study: they are not comforting, without possessing specialized knowledge and software, we managed to penetrate an impressive number of converters without much difficulty and this is a reality, not a theory. Further, if we assume that a person has experience in communicating with these devices and knows where to look for critical information about vulnerabilities, then in most cases it may simply be about exploiting vulnerabilities, because most of the equipment we went through had standard firmware from the factory without the necessary updates. and at almost 80% chance of penetration will be successful.
And now the most interesting thing is to consider that we are dealing with a group of intruders who are professionals in their field and it’s not difficult for them to automate the process of searching for devices and selecting passwords and exploit vulnerabilities. Having gained access to devices, they can use both the device itself and information from it for future attack vectors (upgrade the devices and use them in the bot network, intercept information, replace them, and send on behalf of this device).
findings
Development of automated systems for data collection, processing and process control requires the use of special solutions for building networks. Data transmissions of the automated process control system are based on a hierarchical principle and have a multi-level structure:
- Lower level - the level of sensors and actuators
- Medium-level industrial controllers
- Top level - level of industrial servers and network equipment
- Operator level - the level of the operator and control stations
Let's not forget that such non-standard vectors of attacks on converters can serve as a halt in production and technological process. From the statistics of attacks on industrial computers, we see that every year attacks grow and their vector is the most diverse.
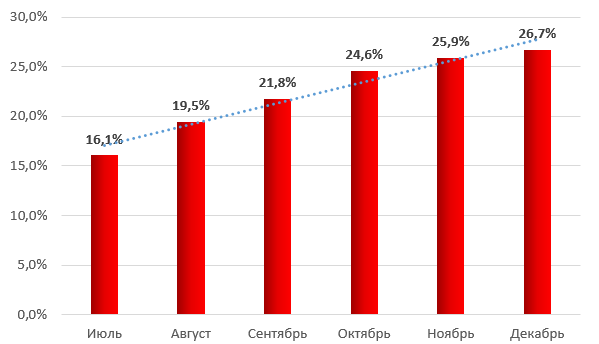
Percentage of industrial computers attacked by months in Russia in 2016
In this study, we and you have seen that such attacks are real and may concern both ordinary users who use converters to remotely connect, control, and configure devices on different interfaces. So all the various organizations whose network is very diverse and has different equipment operating through interface converters. In my experience, I dealt with both moxa converters for remote configuration of PBXs and for remote control of terminals of various protections that transmit and receive information from the industrial network through converters.
The approach of manufacturers of industrial software and equipment to fix vulnerabilities and the situation with the elimination of known vulnerabilities in enterprises cannot be called encouraging. The overwhelming majority of industrial enterprises, both small and large, remain vulnerable to attacks for years. So what conclusions can be made: attacks of non-standard direction are and will be. You need to defend against them and know vulnerabilities too, because information is power. As for the converters used on my an enterprise? I checked all the MOXA equipment, updated everything to the latest version, changed and increased the complexity of passwords, studied the materials about the vulnerabilities of this company and followed the recommendations of experts to minimize the chances of the attackers, if all the same attack will take place.
PS As a result of this study, no device was affected. And this experiment pursued research objectives (to show the reality of attacks and their simplicity).
Source: https://habr.com/ru/post/339066/
All Articles