What is known about the attack on the supply chain CCleaner

An attack on the supply chain or an attack with exploitation of trust in third-party organizations (supply-chain attacks) is a very effective way of spreading malicious software to targeted organizations. This is due to the fact that when attacks on the supply chain attackers use the trust relationship between the manufacturer / supplier and the customer to attack organizations and individuals for various reasons. The Petya / Nyetya / NePetya worm, which was released to the network in early 2017, showed how extensive these types of attacks are. Often, as with Petya, the original attack vector may remain hidden for some time.
Recently, Talos researchers noticed a case where download servers used by a software company to distribute a legitimate software package were used to download malware to suspicious victims on computers. For some period, the version of CCleaner 5.33, distributed by Avast, contained a multistage malicious load. 5 million new users download CCleaner per week. Given the potential damage that could be caused by a network of infected computers of this size, it was decided to act quickly. September 13, 2017 Cisco Talos notified Avast. The following sections will discuss specific details regarding this attack.
')
Technical details
CCleaner is a utility that includes functions such as cleaning temporary files, analyzing the system, determining ways to optimize performance, and a more simplified way to manage installed applications.
Figure 1: Screenshot of CCleaner 5.33
On September 13, 2017, after beta testing clients with new exploit detection technology, Cisco Talos discovered an executable file that was identified as malware. It was the installer of CCleaner v5.33 from legitimate CCleaner download servers. Talos conducted an initial analysis to determine what causes the security system to block CCleaner. They determined that, although the downloaded executable file was signed using Piriform's real digital signature, CCleaner was not the only application that was downloaded. During the installation of CCleaner 5.33, the 32-bit binary file of CCleaner also contained a malicious load with the ability to use a domain generation algorithm (DGA), as well as command issuing and control functions (Command and Control - C2).
When viewing the version history page on the CCleaner download site, it turned out that version (5.33) was released on August 15, 2017. On September 12, 2017 , version 5.34 was released. The version containing the malicious load (5.33) was distributed between these dates. This version was signed using a valid certificate, which was issued for Piriform Ltd, which Avast recently acquired by Symantec and is valid until 10.10.2018.
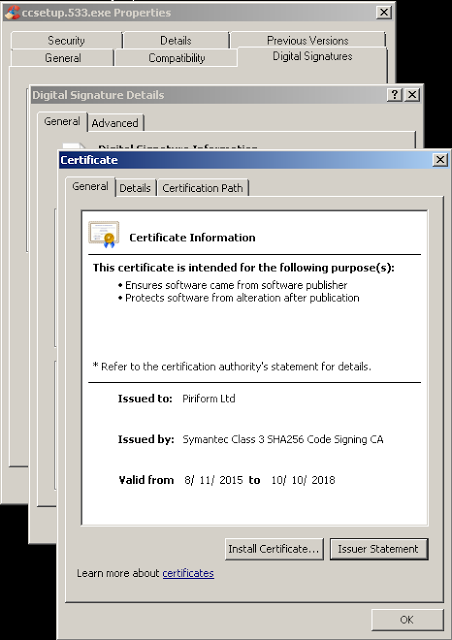
Figure 2: CCleaner 5.33 Digital Signature
Also found was a second installer pattern associated with this threat. This sample was also signed using a valid digital certificate, but the signing time stamp was approximately 15 minutes after the initial assembly was signed.
The presence of a valid digital signature in the CCleaner malicious binary code may indicate a significant problem that caused violations during the development or signing process. Ideally, this certificate should be revoked. When creating a new certificate, it is necessary to ensure that attackers are not in an environment in which to compromise a new certificate. Only in the course of the investigation was it possible to collect detailed information about the extent of this problem and how best to solve it.
The following compilation artifact was found in the CCleaner binary code:
S: \ workspace \ ccleaner \ branches \ v5.33 \ bin \ CCleaner \ Release \ CCleaner.pdb
Given the presence of this compilation artifact, and the fact that the binary code was digitally signed using a valid certificate, it is likely that an attacker from outside compromised part of the development or assembly environment and used this access to insert malicious code into the CCleaner assembly released by the organization. It is also possible that an insider who has access to development or assembly environments within an organization intentionally included malicious code or had a compromised account that allowed an attacker to change the code.
It is important to note that, although previous versions of the CCleaner installer are currently available on the download server, the version containing the malicious files has been removed and is no longer available.
Virus installation process
'__scrt_get_dyn_tls_init_callback' was modified to run the CC_InfectionBase code (0x0040102C) to redirect the flow of code execution to malicious code before continuing the usual CCleaner operations. The called code is responsible for decrypting data that contains two levels of malicious load: the PIC (position-independent program code) loader and the DLL file.
Using HeapCreate (HEAP_CREATE_ENABLE_EXECUTE, 0,0) creates an executable heap. The contents of the decrypted data containing malware are copied to the heap, the original data is erased. Then the PE loader is called and its operation begins. As soon as the infection process began, the binary code erases the memory areas that previously contained the PE loader and the DLL file, frees the previously allocated memory, destroys the heap and continues to execute with the usual CCleaner operations.
The PE loader uses position-independent encoding methods to find the DLL file in memory. It then transfers the DLL to the executable memory and calls the DLL EntryPoint to begin its execution.
CCBkrdr_GetShellcodeFromC2AndCall is responsible for many of the malicious operations found by Talos when analyzing this malware. First, it records the current system time. It then delays the execution of the malicious code for 601 seconds, probably with the aim of avoiding automated analysis systems that are configured to scan software for viruses in the debugger for a predetermined period of time. To implement this delay function, the malware calls a function that attempts to ping 224.0.0.0 using the delay_in_seconds timeout set to 601 seconds. It then determines the current system time to see if 600 seconds have passed. If this condition is not met, the virus ends, while CCleaner continues to run. In situations where malware cannot perform IcmpCreateFile, it returns to using the Sleep () function to implement the same delay function. The malware also compares the current system time with the value stored in the following registry key:
HKLM \ SOFTWARE \ Piriform \ Agomo: TCID
If the time stored in the TCID has not yet come, the virus will also stop running.
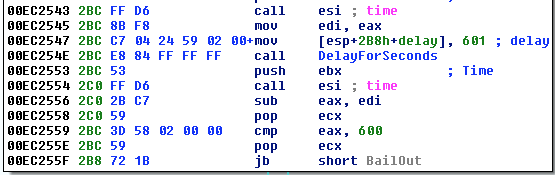
Figure 3: Delay Procedure
Then the privileges assigned to the user are checked. If the current user is not an administrator, the malware will terminate.
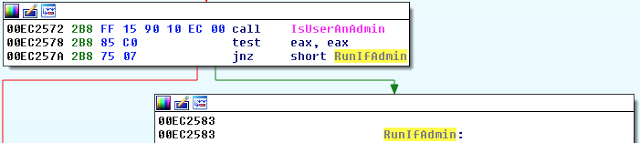
Figure 4: Privilege Check
If the user running the malware has administrator rights, SeDebugPrivilege is activated on the infected system. The malware then reads the InstallID value, which is stored in the following registry key:
HKLM \ SOFTWARE \ Piriform \ Agomo: Muid
If this value does not exist, the malware creates it using '((rand () * rand () ^ GetTickCount ())'.
As soon as the above actions have been completed, the virus begins collecting system information, which is later transmitted to the C2 server. System information is stored in the following data structure:
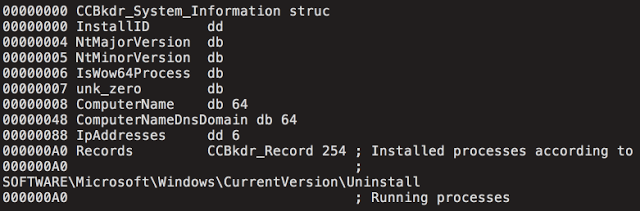
Figure 5: Data structure of CCBkdr_System_Information
After collecting information about the system, it is encrypted and encoded using the modified Base64. The malware then communicates with the command server (C2), as described in the next section.
Command and Control (C2)
Once the previously mentioned system information has been collected and prepared for transmission to the C2 server, an attempt is made to transmit it using the HTTPS POST request to 216 [.] 126 [.] 225 [.] 148.
Data received from the C2 server is verified to confirm that it is in the correct format for use in CCBkdr_ShellCode_Payload. An example is shown below:
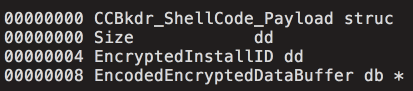
Figure 6: Data structure of CCBkdr_ShellCode_Payload
After the installation of the virus, the usual CCleaner operations continue. Below is a diagram describing how this malware works at a high level:
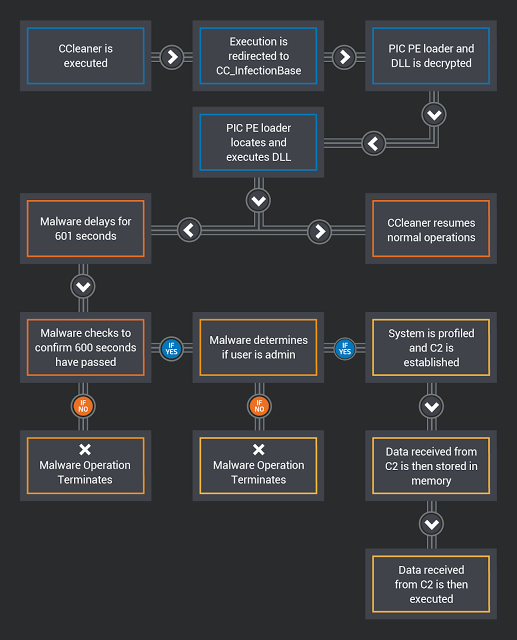
Figure 7: Diagram of the startup process for malware
Domain Generation Algorithm
In situations where the primary C2 server does not return a response to the HTTP POST request described in the previous section, the malware uses the DGA algorithm. In this case, it is based on time and can be calculated using the values of the current year and month. Below is a list of DGA domains:
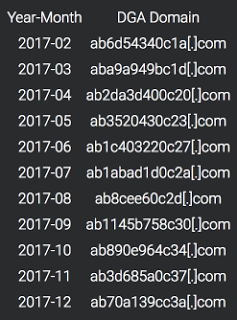
Figure 8: Generation of domains for 12 months
The malware will initiate a DNS lookup for each domain generated by the DGA algorithm. If the DNS lookup does not return the IP address, this process will continue. The malicious program will perform a DNS query of the active DGA domain and expects to receive two IP addresses from the domain name server. The malware will then compute the C2 secondary server by performing a series of bit operations with the obtained IP addresses and combining them to determine the new actual address of the command server. A diagram showing this process is shown below:
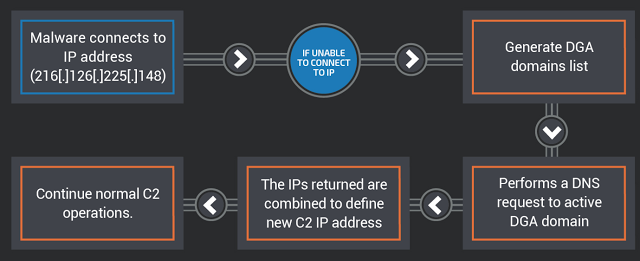
Figure 9: Determining the address of the command server
During the analysis, Cisco Talos determined that the DGA domains were not occupied, so they were registered and blocked so that the attackers could not use them for their own purposes.
Potential damage
The impact of this attack can be serious, given the extremely large number of possible systems. CCleaner claims that, as of November 2016, it has more than 2 billion downloads worldwide and, reportedly, an increase in new users is 5 million per week.
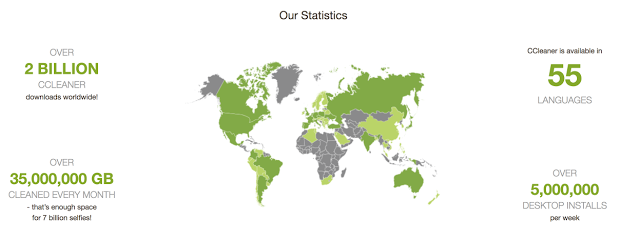
Figure 10: CCleaner Statistics
The systems on which CCleaner was installed during the spread of the virus should be restored to the state of August 15, 2017 or reinstalled. Users must also upgrade to the latest available version of CCleaner to avoid infection. At the time of writing this version was version 5.34. It is important to note that, according to the CCleaner download page, the free version of CCleaner does not provide automatic updates, so this must be done manually.
In analyzing the Cisco Umbrella telemetry data on the domains associated with this attack, Talos identified a significant number of systems that performed the corresponding DNS queries. Since these domains have never been registered, it is reasonable to conclude that the only cause is this virus. Only domains related to August and September (which correlates with the time when this threat was active) show significant activity.
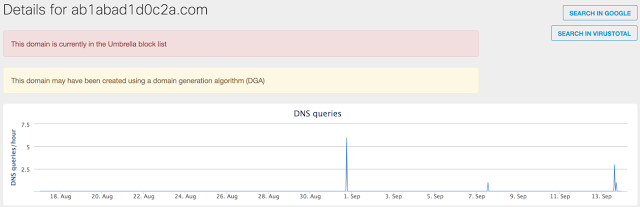
Figure 11: July DGA Domain Activity
As mentioned earlier, the version of CCleaner, which included this malware, was released on August 15, 2017. The following graph shows a significant increase in DNS activity associated with the DGA domain used in August 2017:
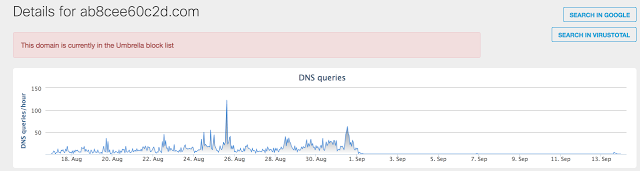
Figure 12: Activity for a domain in August 2017
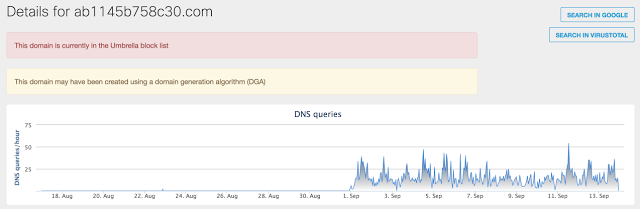
Figure 13: Activity for a domain in September 2017
After contacting Avast, it was noticed that the default C2 server was unavailable to infected systems. As a result, we saw a significant increase in the number of requests directed to DGA-domains.
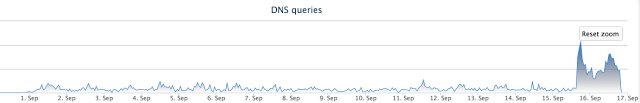
Figure 14: Traffic after shutting down the server
It is also worth noting that on September 18, the antivirus detection of this threat remains very low (1/64).
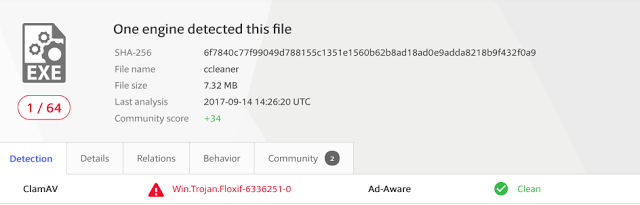
Figure 15: Virus Detection Check
More reasons to worry
Later during our research, we were provided with an archive containing files stored on the C2 server. Our research activity was reflected in the contents of the MySQL database included in the archive files, which confirmed the authenticity of the data.
When analyzing the code from the C2 server , the list of organizations to which the delivery of the second level loader was targeted is immediately highlighted . Based on a review of the C2 tracking database, which covers only four days in September, we can confirm that at least 20 victim machines were infected with specialized malware loads. Below is a list of domains that the attackers tried to target. Not for all companies identified in the .php file, an exchange with a C2 server was noticed.
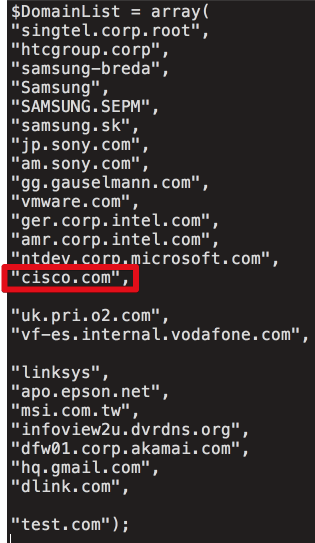
Figure 16
The PHP script compares the system beacons received from the infected machine by three values: $ DomainList, $ IPList and $ HostList. This is necessary to determine whether the infected system should deliver a malicious load on Stage 2. Below is the compressed PHP code that demonstrates this:
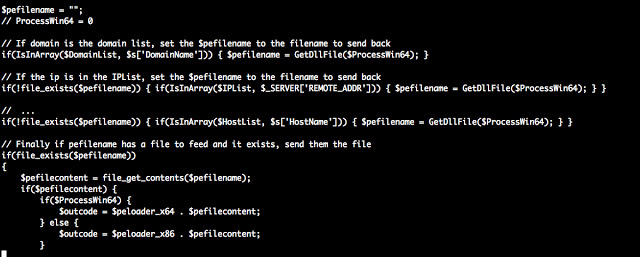
Figure 17
The C2 database contained two tables: one describing all the machines that “communicated” with the server, and a description of all the machines that received the download of Stage 2. And both of them were dated from September 12 to September 16. During this period, more than 700,000 machines were sent to the C2 server, and more than 20 machines received a Stage 2 load. It is important to understand that the target list can be changed and changed during the period when the server was active to infect the target organizations.
During the compromise, the malware periodically contacted the C2 server and transmitted information about the infected systems. This information included IP addresses, time, host name, domain, process lists, and more. This information was probably used by attackers to determine which machines to target in the final stages of the attack.
Basic connection data is stored in the "Server" table. Here is an example for one of the Talos nodes in this database table:
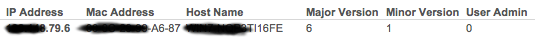
Figure 18
As well as a list of installed programs.
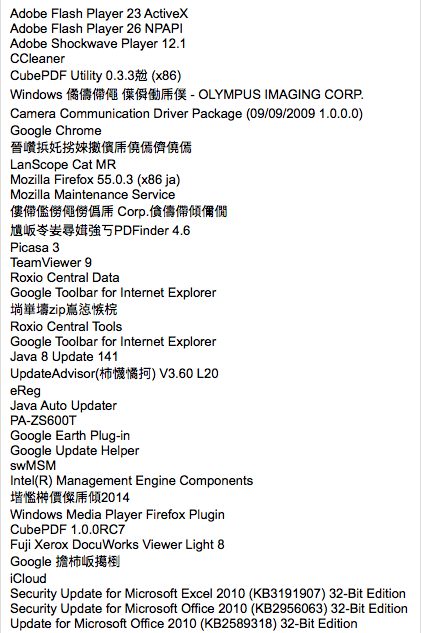
Figure 19
And a list of processes.
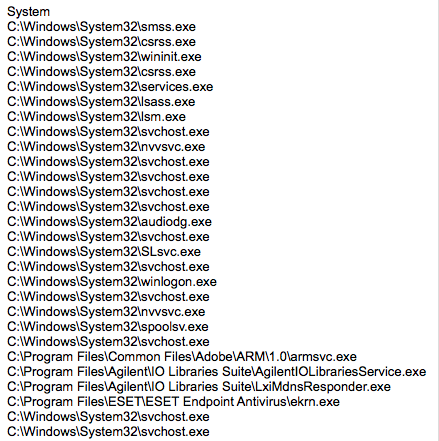
Figure 20
The second database table contained an additional set of data related to the systems to which the load of Stage 2 was actually delivered. This table contained similar information, the structure of which is shown below:
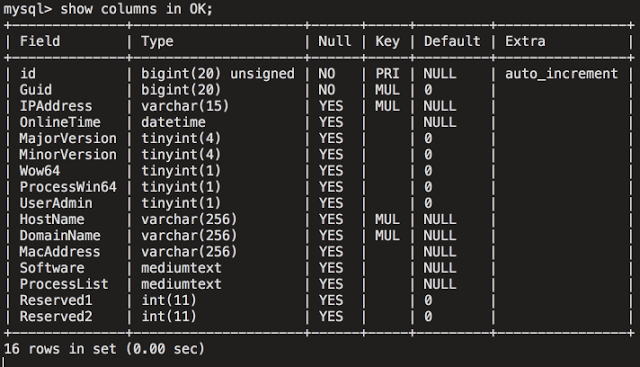
Figure 21
Based on the analysis of the table, it is obvious that this infrastructure provides attackers with access to many different purposes. Given the filtering on the C2 server, attackers can add or delete domains at any time, depending on the environment or the organizations to which they are aimed. The screenshot below shows the number of records that were contained in the database table used to store system profiles:
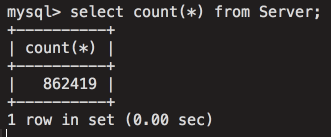
Figure 22
The following screen capture shows the number of affected government systems around the world.
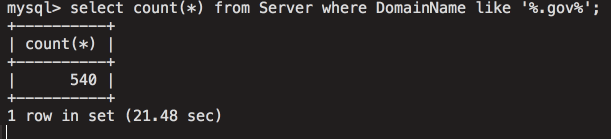
Figure 23
Vulnerable systems with a domain containing the word "bank":
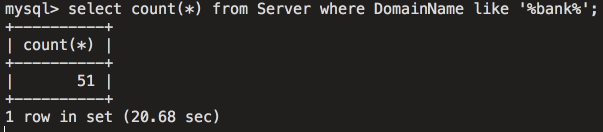
Figure 24
This demonstrates the level of access for intruders, obtained through the use of this infrastructure, and also underlines the seriousness and potential impact of this attack.
CODE REUSE
Talos reviewed allegations from Kaspersky Lab researchers about the coincidence of the code with malware samples known to be used by Group 72 . Although this is by no means proof, we can confirm the coincidence and agree that this is important information.
Left: 2bc2dee73f9f854fe1e0e409e1257369d9c0a1081cf5fb503264aa1bfe8aa06f (CCBkdr.dll)
Right: 0375b4216334c85a4b29441a3d37e61d7797c2e1cb94b14cf6292449fb25c7b2 (Missl backdoor - APT17 / Group 72)
Figure 25
CONCLUSION
Attacks on the supply chain are growing in speed and complexity. In this particular example, the attacker developed a system that appears to be specifically targeted at technology companies to compromise a huge number of machines. This reinforces the concern about these events and also confirms the recommendation that users who downloaded CClenaer during the infection period should not only remove the infected version of CCleaner or upgrade to the latest version, but also restore data from backups to ensure complete removal of malware.
Below are the compromise indicators associated with this attack.
File hashes
6f7840c77f99049d788155c1351e1560b62b8ad18ad0e9adda8218b9f432f0a9
1a4a5123d7b2c534cb3e3168f7032cf9ebf38b9a2a97226d0fdb7933cf6030ff
36b36ee9515e0a60629d2c722b006b33e543dce1c8c2611053e0651a0bfdb2e9
DGA Domains
ab6d54340c1a [.] com
aba9a949bc1d [.] com
ab2da3d400c20 [.] com
ab3520430c23 [.] com
ab1c403220c27 [.] com
ab1abad1d0c2a [.] com
ab8cee60c2d [.] com
ab1145b758c30 [.] com
ab890e964c34 [.] com
ab3d685a0c37 [.] com
ab70a139cc3a [.] com
IP Addresses
216 [.] 126 [.] 225 [.] 148
Installer on the CC: dc9b5e8aa6ec86db8af0a7aa897ca61db3e5f3d2e0942e319074db1aaccfdc83 (GeeSetup_x86.dll)
64-bit trojanized binary
128aca58be325174f0220bd7ca6030e4e206b4378796e82da460055733bb6f4f (EFACli64.dll)
32-bit trojanized binary: 07fb252d2e853a9b1b32f30ede411f2efbb9f01e4a7782db5eacf3f55cf34902 (TSMSISrv.dll)
DLL in registry: f0d1f88c59a005312faad902528d60acbf9cd5a7b36093db8ca811f763e1292a
Registry Keys:
HKLM \ Software \ Microsoft \ Windows NT \ CurrentVersion \ WbemPerf \ 001
HKLM \ Software \ Microsoft \ Windows NT \ CurrentVersion \ WbemPerf \ 002
HKLM \ Software \ Microsoft \ Windows NT \ CurrentVersion \ WbemPerf \ 003
HKLM \ Software \ Microsoft \ Windows NT \ CurrentVersion \ WbemPerf \ 004
HKLM \ Software \ Microsoft \ Windows NT \ CurrentVersion \ WbemPerf \ HBP
Source: https://habr.com/ru/post/338980/
All Articles