Become a hacker: from “Test lab” to “Corporate laboratories”

In 2013, we launched unique penetration testing laboratories - “Test lab”. Being, in essence, copies of real corporate networks (not CTF) containing various vulnerabilities and configuration errors, laboratories make it possible to understand how a real attack occurs on a corporate network by attackers, to master their tools and methodologies, to learn how to build various attack vectors. Without such knowledge, information security professionals cannot develop high-quality protective measures.
After 4 years, “Test lab” did not lose its uniqueness and gathered more than 18,500 participants from around the world. Every day, working with such an audience, accumulating practical skills in penetration testing, forensics and countering cyber attacks, we make Pentestit Corporate Labs - unique in its composition, information security training courses.
Laboratories for penetration testing "Test lab"
The first laboratories “Test lab”, which are copies of a network of small companies (domain, mail, file server and something else), turned into complex and distributed centralized networks (Domains, VPN tunnels, server divisions, etc.), while without losing its essence - it is necessary to make a complete compromise of the IT structure of the laboratory, correctly building attack vectors. This is the unique “Test lab” - unlike CTF, nodes in laboratories are interconnected, the compromise of one of them can help develop the vector of attack on others. In some laboratories, we lay down the socio-technical attack vectors (for example, on an office manager or another laboratory employee) for greater realism.
')
Before you implement an idea, you need to understand your target audience well. Each time, starting another laboratory, we gain invaluable practical experience, which, together with our skills in finding and operating vulnerabilities, we transfer to Pentestit Corporate Laboratories, making them an excellent training ground for obtaining quick and high-quality practical training in the field of information security for information security, pentesters, developers and system administrators.
Warm up - “Zero Security: A”
Training in "Corporate laboratories" requires high-quality preliminary training. Such training can be obtained at the Zero Security: A course, where, under the supervision of the curator, you will learn the standard Kali Linux Rolling Edition 2017 toolkit, learn about all stages of penetration testing - from intelligence and information gathering to finding and exploiting vulnerabilities and social engineering. As well as "Corporate laboratories", practical work in specialized laboratories is 70% of the course.
Zero Security course program: A
- Criminal Code and crimes in the field of information technology
- Threat models, their types, objects of research
- Familiarity with Linux. Introduction to Kali Linux Rolling Edition 2017.1 and Standard Toolkit Overview
- Intelligence and information gathering
- Network scan
- Exploiting web vulnerabilities, an introduction to Burp Suite, familiarity with OWASP Top-10
- Network Infrastructure Security
- Wireless Security Analysis
- Introduction to the Metasploit Framework
- Analysis of circumvention methods for proactive protection systems
- Introduction to Social Engineering
One of the tasks in Zero Security: A - Local File Inclusion
When conducting a pentest web applications, special attention must be paid to the parameters that are present in various requests, thanks to them we can influence the response of the web application. We have only one parameter in the GET request - page, whose values are files with the php extension, from which it can be concluded that various pages are included in the source code of the web application, for example, using the include () function.
Let's start testing. To begin with, we will try to change the parameter value to any random string - website /? Page = abc.php , as a result of which some of the information on the page disappeared, because we added a nonexistent page.
We made sure that the web application is vulnerable to Local File Include.

This vulnerability is interesting because with it, an attacker can execute arbitrary code on a vulnerable machine by including the code in a web application. This can be done, for example, using various log files, if you specify /var/log/apache2/access.log in the page parameter, we get the contents of the log file.
Now you need to implement the code, for which you can replace the User Agent header with a shell:

After implementing the payload in the User Agent field, we can call our web shell from the web server log:

Using command generation in a URI, we can execute commands on a web server and detect the desired token.
Let's start testing. To begin with, we will try to change the parameter value to any random string - website /? Page = abc.php , as a result of which some of the information on the page disappeared, because we added a nonexistent page.
We made sure that the web application is vulnerable to Local File Include.

This vulnerability is interesting because with it, an attacker can execute arbitrary code on a vulnerable machine by including the code in a web application. This can be done, for example, using various log files, if you specify /var/log/apache2/access.log in the page parameter, we get the contents of the log file.
Now you need to implement the code, for which you can replace the User Agent header with a shell:

After implementing the payload in the User Agent field, we can call our web shell from the web server log:

Using command generation in a URI, we can execute commands on a web server and detect the desired token.
Hardcore - Pentestit Corporate Labs
We have our own view on conducting courses, so webinars make up only 30%, the remaining 70% is an intensive practice, leaving the knowledge “at your fingertips”. Such a training scheme requires maximum involvement and commitment - webinars provide insight into how to search, exploit vulnerabilities, know how to resist attacks and deal with incidents, but they are not able to teach how to think correctly. This experience can only give practice. Let's look at some cases.
Case 1 - system administrator error
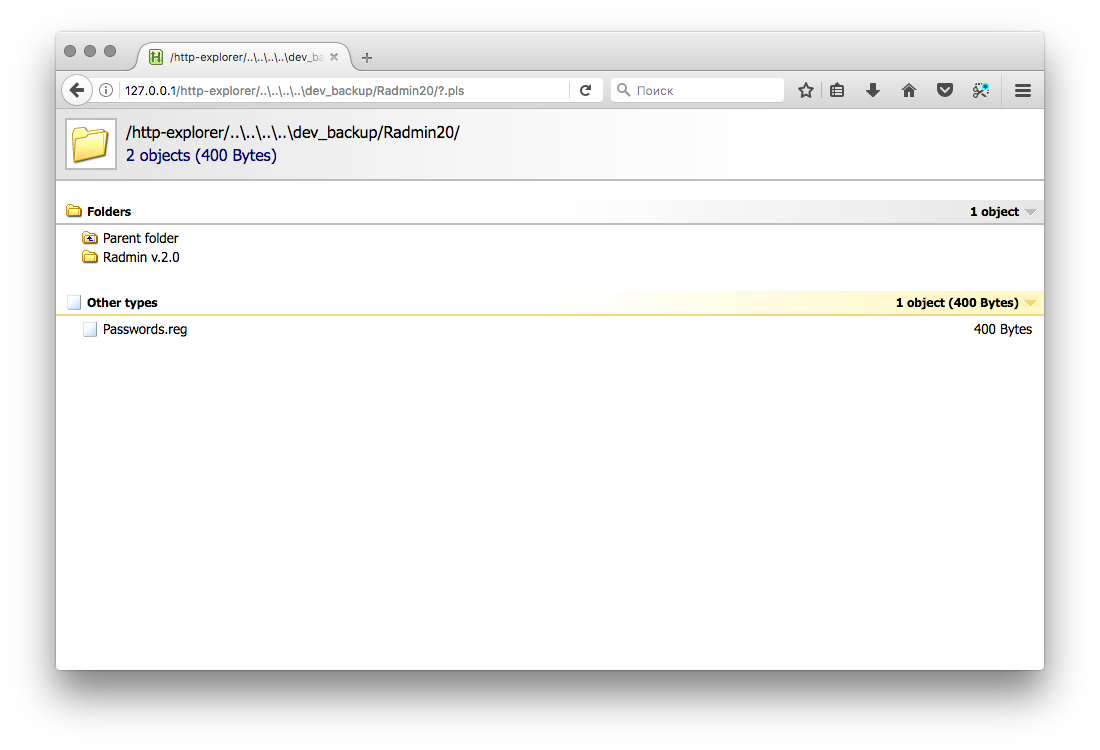
The local network has a mini web server for downloading distributions by system administrators. In the list of files, you can find a backup script with the indication of execution paths on a Windows server. The web server contains the Directory Traversal vulnerability and allows you to get a particular file (if its name is known and it is located on this server). The attacker detects the Backup folder containing the Radmin utility and the unloaded registry branch passwords.reg. The Parameter field contains the hash of the administrator password. We select it and get the opportunity to connect to the Windows-server.

Case 2 - Fornsica: Volatility, Wireshark
Anomalous behavior was detected on one of the machines on the network. It was possible to quickly remove the memory dump and network traffic.
We will analyze the memory dump using the Volatility Framework. We will display information about the dump:

In the memory dump, we notice a process with a non-standard name: Movie_HD720p, PID: 198. We see that the executable file of the process Movie_HD720p.torrent.exe, through which the infection occurred.
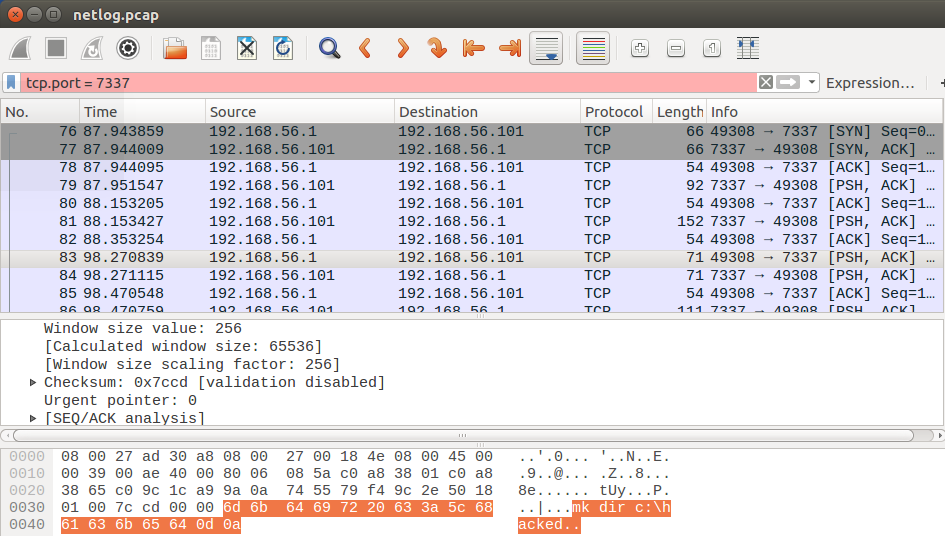
On port 7337, which listened to the process PID 198 (Movie_HD720p), a connection was made from the address XXX.XXX.XXX.XXX.

By configuring the filter in Wireshark, you can see the attacker's network activity: he did not use encryption, so the commands were transmitted in clear text.
We will analyze the memory dump using the Volatility Framework. We will display information about the dump:

In the memory dump, we notice a process with a non-standard name: Movie_HD720p, PID: 198. We see that the executable file of the process Movie_HD720p.torrent.exe, through which the infection occurred.
On port 7337, which listened to the process PID 198 (Movie_HD720p), a connection was made from the address XXX.XXX.XXX.XXX.

By configuring the filter in Wireshark, you can see the attacker's network activity: he did not use encryption, so the commands were transmitted in clear text.

Case 3 - Web Application: Blind SQLi
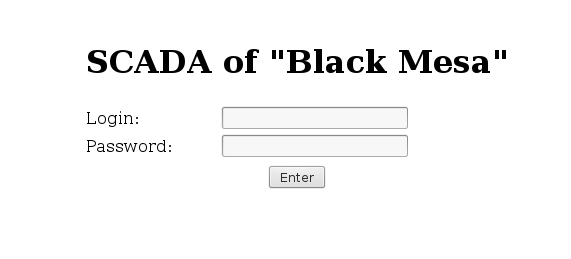
In the local network, we obscure the SCADA web server belonging to the ICS system.
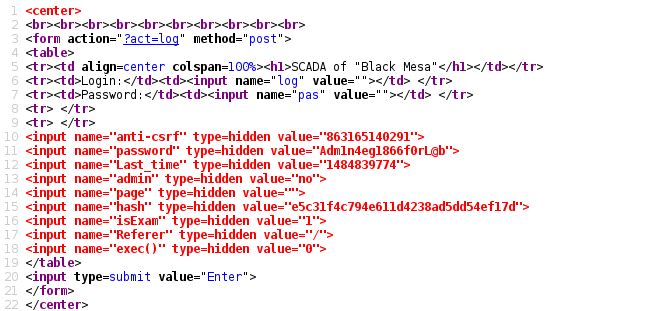
Examine the code of the web application page; we discover hidden values transmitted by the POST method:
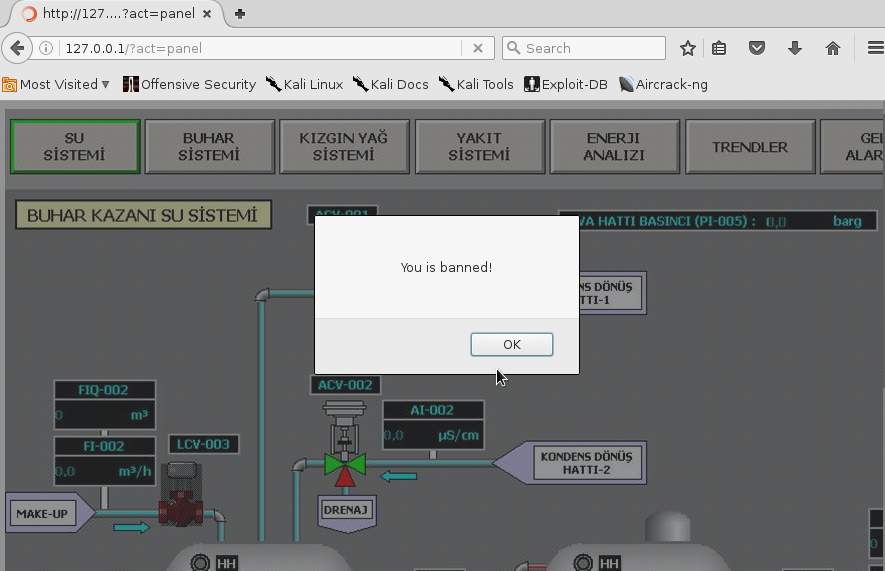
Most likely this information is already outdated, when entering data we receive a message that we are banned:
We try to investigate server responses using the burp suite:
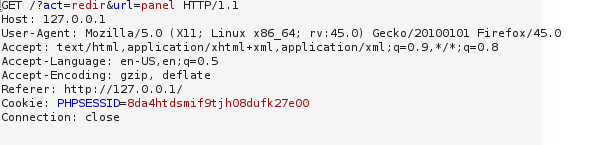
When a user is blocked, a new parameter url = panel is added, we try to investigate the behavior of the server when changing parameters:

By sending several requests for detecting SQL injections, we see that when substituting sleep values, the web application responds with a delay of approximately (error) equal to the value of the sleep parameter. This indicates the presence of a time-based SQL injection.
Using the identified parameter in the sqlmap query, we reveal the contents of the database and get the required token.

Examine the code of the web application page; we discover hidden values transmitted by the POST method:

Most likely this information is already outdated, when entering data we receive a message that we are banned:

We try to investigate server responses using the burp suite:

When a user is blocked, a new parameter url = panel is added, we try to investigate the behavior of the server when changing parameters:

By sending several requests for detecting SQL injections, we see that when substituting sleep values, the web application responds with a delay of approximately (error) equal to the value of the sleep parameter. This indicates the presence of a time-based SQL injection.
Using the identified parameter in the sqlmap query, we reveal the contents of the database and get the required token.
The course program Corporate Laboratories
Module "Profi" - the development of professional skills in the field of penetration testing and gaining practical experience of compromising modern systems.
The module "Expert" - is designed to develop expert practical skills in the field of penetration testing, system protection and investigation of information security incidents.
The “RedTeam” module is intended for training team work in the following areas: penetration testing, investigation of information security incidents
- Legislation in the field of information security in Russia and abroad;
- Penetration testing: methodology, methods, types, tools;
- Network security: scanning, configuration errors, exploitation and post-exploitation;
- Web application security: the nature of SQL injection, XSS basics, and tools for exploiting web vulnerabilities;
- Building effective information security systems: introductory information and a review of existing IDS;
- MITM attacks and protection methods;
- Extended Workshop on SQLi: attacks on popular databases;
- Advanced workshop on XSS;
- Vulnerabilities of modern web applications;
- Extended network security: search for vulnerabilities in network infrastructure;
- The use of Python in penetration testing;
- Building effective information security systems;
- Wireless security;
- Practical work in specialized laboratories.
The module "Expert" - is designed to develop expert practical skills in the field of penetration testing, system protection and investigation of information security incidents.
- Post ‐ operation in Windows systems;
- Post ‑ operation on Linux systems;
- Investigation of cyber crimes;
- Forsenzyk mobile devices;
- Fornsica: using the Volatility Framework for analyzing RAM and file system dumps;
- Practical work in specialized laboratories.
The “RedTeam” module is intended for training team work in the following areas: penetration testing, investigation of information security incidents
- Teamwork during penetration testing;
- Data processing systems during penetration testing;
- Using tools to analyze and manage vulnerabilities;
- Conducting socio-technical campaigns;
- Incident response and investigation;
- Analysis of malicious activity: identifying and neutralizing threats;
- Practical work in specialized laboratories.
Another feature of “Corporate Laboratories” is a single plot of the laboratory environment, to put it simply - laboratories are replicas of real companies with embedded vulnerabilities and configuration errors and require correctly aligned attack vectors. Any of our training programs is accompanied by a curator, whose task is to assist in the implementation of tasks (if required), as well as monitoring the correctness of their implementation. The course ends with the issuance of a proprietary certificate.

Video Reviews of Corporate Laboratories
Full review of "Corporate Laboratories"
Timing attack on SSH
PowerShell Empire framework
Combined attacks on web applications
Encrypted command control via DNS
Demonstration of the operation of OpenVAS9 scanner in Kali Linux
Timing attack on SSH
PowerShell Empire framework
Combined attacks on web applications
Encrypted command control via DNS
Demonstration of the operation of OpenVAS9 scanner in Kali Linux
If you have questions - ask in the comments. See you at Pentestit courses !
Source: https://habr.com/ru/post/338856/
All Articles