How I participated in a Xiaomi bug bounty and what was it for me
“We have a security hole.”
- Well, at least something is safe.
- iPhone, won, every year break, and nothing.
I found this error by accident. I am sure that not a single tester would have thought to go this way - this is so not obvious, wild and unpredictable, that only an accident helped me participate in a bug bounty from Xiaomi. In this post I will talk about how I managed it, what it was for and why Chinese services are evil.
')
In MIUI, you can create two “spaces” (for simplicity, I will call them profiles) —a completely independent set of settings, applications and files that are inaccessible from each other (not counting the separate Import application). Both profiles can be password protected and, let's say, use the device with someone else.
Knead is that I found a way to move from the second profile to the first without entering a password. This was possible through the Google Drive application, which is installed by default in the global firmware on MIUI 8 and is immediately available in the second profile.
The second profile has less rights than the first - in it, for example, you cannot enable or disable the mobile Internet or manage backups in Google Drive. If you try to do this, the application offers to go to the “Manage Users” system dialog and select the user on whose behalf the action is performed.
But something went wrong, and the choice of the main profile in this window did not lead to managing backups, but to switching to it without entering a password.
Basically, no big deal. To exploit the vulnerability, you must at least know one of the passwords and have physical access to the phone. But even within a limited team, getting access to the data stored in the second profile can be extremely unpleasant.
On the other hand, I did not really have time to investigate the principle of the appearance of the “Manage Users” screen. Probably, there are system methods for calling it from other applications, but I did not go that far.
At first, I thought of stating it as a bug in a google application (I heard that they sometimes give money for it). But common sense nevertheless suggested that the security hole of the operating system can be estimated more expensive (and you need to fix it more quickly), and I went to look for a program for Xiaomi baunt bug.
A brief search led me to the Xiaomi Security Center . It is now there at the very least 30 percent added an English translation, but then it looked like this:
Xiaomi Security Center, sec.xiaomi.com
With the Google translator, I read some general things about the program and realized that the vulnerability found was high — the SQL injection, business logic vulnerabilities, XSS access to the cookie, information about the device users, escalation privileges, bypassing login screens and a few more things. “Okay,” I thought, I found a form using a spear method and went to describe the problem.

Vulnerability Submit Form
The Google translator built in chrome is good exactly till the moment when it comes to dynamically formed drop-down lists. If the title, description, proof-of-concept and solution fields were somehow clear, I didn’t understand what they wanted from me in the lists. I had to pick out the hieroglyphs from the right places of the page through viewing the HTML-code and translate manually.
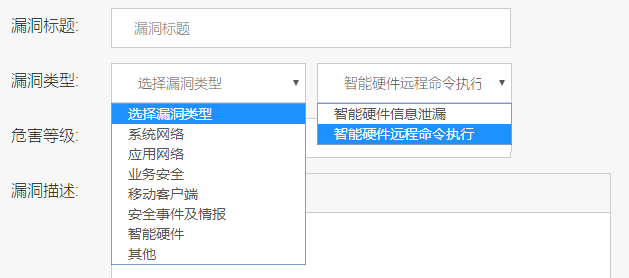
Thank you, now everything is clear
It turned out that the first list defined the type of vulnerability, the second specified it, and in the third it was necessary to choose the scale of the problem - from low to major.
Naturally, I wrote that the problem is extremely important and give me more money, I don’t have the strength to endure, I’m such a good fellow . To confirm my intentions, I recorded a five-minute video where I spoke in broken English how to exploit a vulnerability and easily access personal data. I sent information about the vulnerability and how to fix it (April 6) and waited.
On April 11, right at the Security Center, I received a message from an unnamed employee Xiaomi.
It was like this:
This is not a miui case for this support.
> Thank you for sending, this is not a miui problem, it is marked insignificant and will remain without reward. Thanks for the support.
“How is that? But this! Same! Hole! By the size! WITH! Kimberlite! The tube! In Yakutia! ”- something like this, I resented the next four hours, and then calmed down and wrote a response message. Here it is:
> Miui allows to view "manage users" screen and switch account without pass. anyway
> In MIUI, you can get to the "User Management" screen and switch between accounts without a password. Anyway, are you planning to fix the problem?
I was mentally ready to wait five more days (since I was left without an award anyway), but the answer came an hour later:
> sorry, my mistake, I will test again
> Sorry to blame. Check again.
Due to the operator's “error”, the hole could be closed around infinity. I don’t know how it works in other vulnerability scan programs, but such an approach in Xiaomi clearly tunes in depressing thoughts.
The error, however, was corrected already two weeks after the re-test - in a fresh update of the system such a trick has not been repeated. For the same reason now I am writing this post.

Fortunately, testing did not take long and the next day I received a reward of 1000 (thousand) coins in a store inside the Security Center.
On sec.xiaomi.com there is a catalog of things that can be bought for an internal-security-currency-victory (sorry, I just did not come up with an easier explanation).
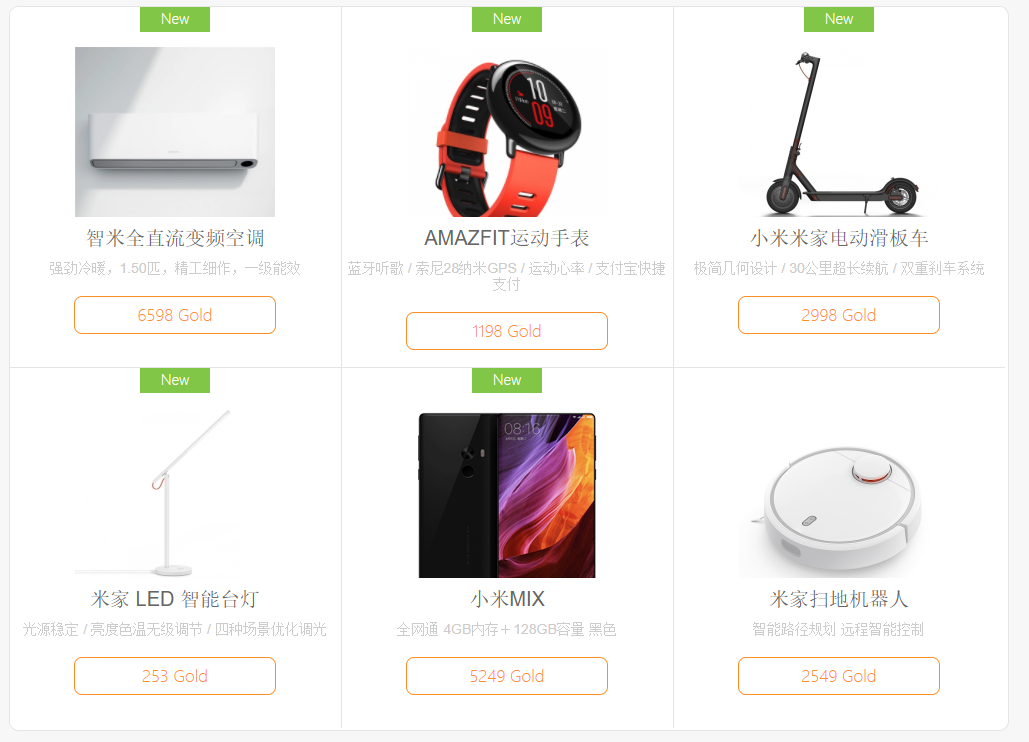
Do not deny yourself anything for a thousand prize coins.
Realizing that nothing good could be chosen from the goods, I began to study another interesting option - you could “buy” yuan for coins, at the rate of 1 yuan for 1.5 coins. A quick calculation showed that my thousand coins famously turned into about 5,200 rubles (at the rate at the time of this writing), and it looked like a very good reward for clicking on a couple of buttons in questionable places in the system.
Of course, I filled a basket of yuan for 900 coins (quantization of 150).
Of course, clicked on the Chinese version of the inscription "Checkout".
And, of course, immediately ran into a bunch of problems.
There would be a screenshot of the form, if I had not lost it
They required my name, bank card number andCVV ID number.

Chinese name entry form
Neither the name nor the number of the Russian passport did not fit - the Chinese ID number contains from 12 to 16 characters, and for the name was given only from 2 to 6.
But after going through the reward, I didn’t want to let go of the award, and I decided to write a letter to technical support and find out how foreigners withdraw money (which, judging by the nicknames of vulnerability catchers, was a lot). Ok, with the translator we are looking for the necessary section, we go ...

… heck.
Okay, I had to choose the goods. A thousand coins contained a smart lamp , a smart 360-degree camera and a bluetooth speaker . Together they cost about 7,200 rubles (or $ 124).
The remaining three dozen coins I lost in the “wheel of luck” on the site.
The benefit of the design is simpler, and I just had to figure out how to fit the international delivery address in the field with a limit of 100 characters , and also shorten the name to six letters - Evgeny, and write the full one in “Notes”.
July ended.
After filling out the form in your account, nothing has changed. On the first of August, I decided nevertheless to clarify what was there with the delivery, and wrote a message in the same dialogue, where I reported on the vulnerability. Nothing has happened.
On August 25, I made another attempt, and after five days I received an answer with the parcel track and apologies.
The delivery took another week, and I finally received a package with a reward for a bounty bug in Xiaomi. It's nice that the courier from EMS delivered her to the door and did not have to go anywhere. Happy end.
In the comments, I am ready to answer your questions about any stages of this time-stretched process.
Thanks for attention!
- Well, at least something is safe.
- iPhone, won, every year break, and nothing.
I found this error by accident. I am sure that not a single tester would have thought to go this way - this is so not obvious, wild and unpredictable, that only an accident helped me participate in a bug bounty from Xiaomi. In this post I will talk about how I managed it, what it was for and why Chinese services are evil.
')
Prehistory
In MIUI, you can create two “spaces” (for simplicity, I will call them profiles) —a completely independent set of settings, applications and files that are inaccessible from each other (not counting the separate Import application). Both profiles can be password protected and, let's say, use the device with someone else.
What, in fact, the batch?
Knead is that I found a way to move from the second profile to the first without entering a password. This was possible through the Google Drive application, which is installed by default in the global firmware on MIUI 8 and is immediately available in the second profile.
The second profile has less rights than the first - in it, for example, you cannot enable or disable the mobile Internet or manage backups in Google Drive. If you try to do this, the application offers to go to the “Manage Users” system dialog and select the user on whose behalf the action is performed.
But something went wrong, and the choice of the main profile in this window did not lead to managing backups, but to switching to it without entering a password.
Dubious Analytics # 1
Basically, no big deal. To exploit the vulnerability, you must at least know one of the passwords and have physical access to the phone. But even within a limited team, getting access to the data stored in the second profile can be extremely unpleasant.
On the other hand, I did not really have time to investigate the principle of the appearance of the “Manage Users” screen. Probably, there are system methods for calling it from other applications, but I did not go that far.
How to live with it?
At first, I thought of stating it as a bug in a google application (I heard that they sometimes give money for it). But common sense nevertheless suggested that the security hole of the operating system can be estimated more expensive (and you need to fix it more quickly), and I went to look for a program for Xiaomi baunt bug.
A brief search led me to the Xiaomi Security Center . It is now there at the very least 30 percent added an English translation, but then it looked like this:

Xiaomi Security Center, sec.xiaomi.com
With the Google translator, I read some general things about the program and realized that the vulnerability found was high — the SQL injection, business logic vulnerabilities, XSS access to the cookie, information about the device users, escalation privileges, bypassing login screens and a few more things. “Okay,” I thought, I found a form using a spear method and went to describe the problem.

Vulnerability Submit Form
The Google translator built in chrome is good exactly till the moment when it comes to dynamically formed drop-down lists. If the title, description, proof-of-concept and solution fields were somehow clear, I didn’t understand what they wanted from me in the lists. I had to pick out the hieroglyphs from the right places of the page through viewing the HTML-code and translate manually.

Thank you, now everything is clear
It turned out that the first list defined the type of vulnerability, the second specified it, and in the third it was necessary to choose the scale of the problem - from low to major.
Naturally, I wrote that the problem is extremely important and give me more money, I don’t have the strength to endure, I’m such a good fellow . To confirm my intentions, I recorded a five-minute video where I spoke in broken English how to exploit a vulnerability and easily access personal data. I sent information about the vulnerability and how to fix it (April 6) and waited.
How long did you have to wait?
On April 11, right at the Security Center, I received a message from an unnamed employee Xiaomi.
It was like this:
This is not a miui case for this support.
> Thank you for sending, this is not a miui problem, it is marked insignificant and will remain without reward. Thanks for the support.
“How is that? But this! Same! Hole! By the size! WITH! Kimberlite! The tube! In Yakutia! ”- something like this, I resented the next four hours, and then calmed down and wrote a response message. Here it is:
> Miui allows to view "manage users" screen and switch account without pass. anyway
> In MIUI, you can get to the "User Management" screen and switch between accounts without a password. Anyway, are you planning to fix the problem?
I was mentally ready to wait five more days (since I was left without an award anyway), but the answer came an hour later:
> sorry, my mistake, I will test again
> Sorry to blame. Check again.
Dubious Analytics # 2
Due to the operator's “error”, the hole could be closed around infinity. I don’t know how it works in other vulnerability scan programs, but such an approach in Xiaomi clearly tunes in depressing thoughts.
The error, however, was corrected already two weeks after the re-test - in a fresh update of the system such a trick has not been repeated. For the same reason now I am writing this post.

Fortunately, testing did not take long and the next day I received a reward of 1000 (thousand) coins in a store inside the Security Center.
What kind of store ?
On sec.xiaomi.com there is a catalog of things that can be bought for an internal-security-currency-victory (sorry, I just did not come up with an easier explanation).

Do not deny yourself anything for a thousand prize coins.
Realizing that nothing good could be chosen from the goods, I began to study another interesting option - you could “buy” yuan for coins, at the rate of 1 yuan for 1.5 coins. A quick calculation showed that my thousand coins famously turned into about 5,200 rubles (at the rate at the time of this writing), and it looked like a very good reward for clicking on a couple of buttons in questionable places in the system.
Of course, I filled a basket of yuan for 900 coins (quantization of 150).
Of course, clicked on the Chinese version of the inscription "Checkout".
And, of course, immediately ran into a bunch of problems.
There would be a screenshot of the form, if I had not lost it
They required my name, bank card number and

Chinese name entry form
Neither the name nor the number of the Russian passport did not fit - the Chinese ID number contains from 12 to 16 characters, and for the name was given only from 2 to 6.
But after going through the reward, I didn’t want to let go of the award, and I decided to write a letter to technical support and find out how foreigners withdraw money (which, judging by the nicknames of vulnerability catchers, was a lot). Ok, with the translator we are looking for the necessary section, we go ...

… heck.
Okay, I had to choose the goods. A thousand coins contained a smart lamp , a smart 360-degree camera and a bluetooth speaker . Together they cost about 7,200 rubles (or $ 124).
The remaining three dozen coins I lost in the “wheel of luck” on the site.
The benefit of the design is simpler, and I just had to figure out how to fit the international delivery address in the field with a limit of 100 characters , and also shorten the name to six letters - Evgeny, and write the full one in “Notes”.
July ended.
How long do I have to wait?
After filling out the form in your account, nothing has changed. On the first of August, I decided nevertheless to clarify what was there with the delivery, and wrote a message in the same dialogue, where I reported on the vulnerability. Nothing has happened.
On August 25, I made another attempt, and after five days I received an answer with the parcel track and apologies.
The delivery took another week, and I finally received a package with a reward for a bounty bug in Xiaomi. It's nice that the courier from EMS delivered her to the door and did not have to go anywhere. Happy end.
In the comments, I am ready to answer your questions about any stages of this time-stretched process.
Thanks for attention!
Source: https://habr.com/ru/post/338776/
All Articles