Blackmailing programs: a threat to the past or the future?
If we look at the attack vectors, the number of unique virus families and the evolution of malware, we note that this is becoming the most serious and widespread security threat. Under the cut, I'll tell you about the analysis of blackmail programs and protection from them.

Analysis of the blackmailers for 2016 showed the following:
The impact of blackmailing programs has affected not only private users, business companies and the public sector as well. After the mainstream media reported these attacks, including that some hospital in California had paid attackers to restore important medical files, as well as a failure in the San Francisco transportation system , the idea of blackmailers went deeper. into the public mind. In September, a Europol report called the blackmailers the biggest digital threat that left behind data theft malware and online banking Trojans.
')
It is noteworthy that according to the Windows Defender antivirus, an interesting tendency is observed: having reached a peak value in August 2016 - 385 thousand registered cases of blackmail program detection - in September their number almost halved and continues to fall.
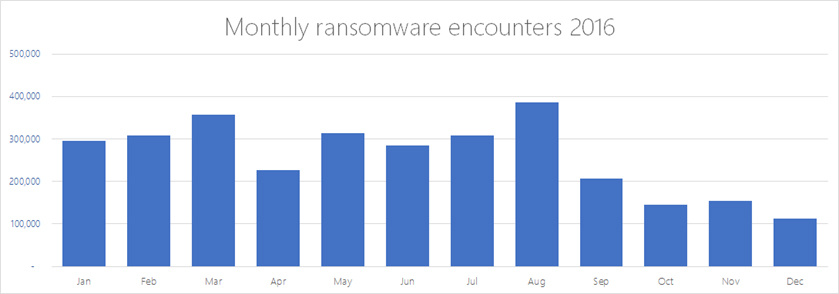
Fig. 1. Monthly frequency of detection of blackmail utility payload files, excluding downloaders and other components. Some industry data combine these two indicators.
Does this trend mean that the end of blackmailing programs is foreseen? If you look at other areas of distribution of blackmailers, it turns out that this is not the case.
To understand whether the prevalence of blackmailers is declining, it is necessary to examine other areas of the infection chain, starting with the attack vectors. Data Windows Defender Antivirus suggests otherwise.
Trojan downloaders such as Nemucod and Donoff install blackmailers on PCs. These downloaders are often in the form of document files or shortcuts and are distributed via email.
The number of e-mail messages containing blackmailer downloaders has not decreased. In the last quarter of 2016, 500 million such messages were recorded. Over the same period of time, bootloaders have infected at least 1 million PCs per month. It is obvious that cybercriminals did not stop using blackmailers to attack users' computers. In fact, right up to the end of 2016, we witnessed campaigns to send email messages with the Nemucod exploit that spread the Locky virus and campaigns to send the Donoff virus, through which the Cerber virus spread .
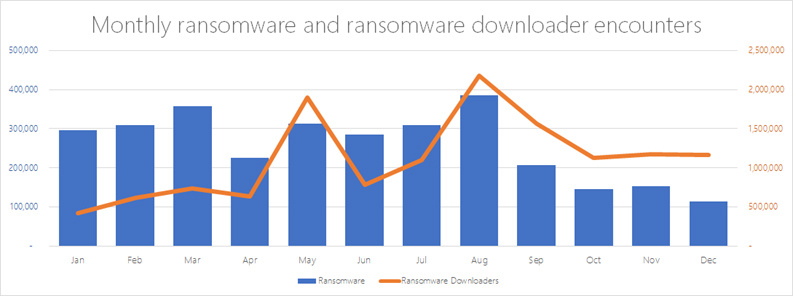
Fig. 2. Although the number of cases of blackmail program detection was significantly reduced by the end of 2016, in the second half of the year compared to the first, the frequency of infection by the blackmailer downloaders was, on average, higher.
Obviously, the decrease in cases of detection of blackmailers is not due to the fact that cybercriminals have become less diligent. There are still a huge number of emails containing Trojans-loaders of blackmailers. However, infection by blackmailing programs is blocked at the point of entry. This is an interesting move, since in 2016, blackmailing distributors switched from using exploits to e-mail messages as a more efficient infection vector.
The Neutrino exploit was used to install the Locky blackmailer on a PC. In mid-2016, the Neutrino infection rate increased, filling the niche of the Axpergle virus (also known as the Angler) after it disappeared in June. Obviously, the prevalence of Neutrino began to decline in September, after its operators passed the reins to the cybercriminal groups.
Another popular exploit, Meadgive (also known as RIG), initially distributed the blackmailer Cerber. In 2016, Meadgive was constantly growing, becoming the most frequent malware exploit. In December 2016, the Meadgive campaign began with the latest version of the Cerber virus, which was conducted mainly in Asia and Europe.
Although exploits are being used less and less , blackmailers continue to use exploits to infect computers. This is because exploits allow blackmailers to raise permissions and launch potentially dangerous programs with fewer restrictions.
The decline of blackmailing programs has not yet come, and another evidence of this is the numerous innovations of malicious code recorded in 2016.
Cybercriminals are constantly updating their tools. For example, at the end of 2016, significant updates of the latest version of Cerber were recorded.
These malicious code enhancements are gradually being introduced in attacks such as the blackmailer as a service in which cybercriminals can get the latest versions of blackmailers on illegal forums. This provides cybercriminals with the necessary resources and motivation to launch attacks.
The following are some enhancements to the blackmailer program that we witnessed in 2016.
The discovery of the Samas blackmailer in early 2016 made these programs a major threat to commercial companies. Faced with blackmailers targeting servers, IT administrators had to not only take care of end-user protection, but also increase server protection.
Samas distribution campaigns exploited server vulnerabilities . They searched for vulnerable networks using pen test and used various components to encrypt files on servers.
Zcryptor had the ability to spread, which means that some blackmailers could move from one end point to another without resorting to spam campaigns. The worm virus detects network and logical drives and removable media that it can use for distribution. At the very beginning of 2017, the Spora virus was detected, showing similar behavior.
Usually, blackmailers demanded payment via Bitcoin on illegal websites of the Tor network. In response to the reduction in the number of payments from the victims, cybercriminals began to look for new methods of payment.
The blackmailer Dereilock , for example, forced its victims to contact the cybercriminals via Skype, and Telecrypt offered to use the messaging service Telegram Messenger to communicate with the cybercriminals.
Spora took the path of shareware services - a couple of files could be decrypted for the victim free of charge, and for a small amount it was possible to decrypt a number of files.
In 2016, most blackmailers began using a countdown timer. This forces the victim to pay the ransom immediately, for fear of irretrievable loss of access to the files.
When Cerber blackmailed the program in March, she made a splash: in addition to the usual ransom report, both text and HTML, VBScript transformed the text into an audio message with a ransom demand. Therefore, Cerber was called a "talking blackmailer."
Another blackmailer CornCrypt offered to decrypt files for free, provided that the victim infects two other users. The attackers were counting on the effect of a snowball: the more victims, the greater the likelihood that one of them will pay.
The threat from the blackmailer program most likely does not weaken, as evidenced by the emergence of new families of blackmailer programs. Of the more than 200 active families found, about half were recorded for the first time in 2016.
Most new blackmailing software families use encryption. This type of blackmailing program replaces older screen lock versions that simply lock the screen and do not use file encryption.
In 2016, many families of blackmailers appeared, using new methods and techniques. At the same time, 68% of cases of detection of blackmail programs in 2016 accounted for five leaders.
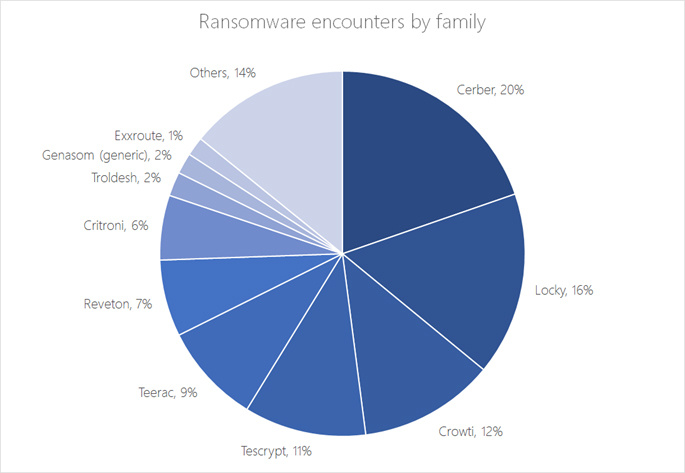
Fig. 3. Cerber and Locky, discovered in 2016, became the leaders of the year among the blackmailers
It is interesting to note that two leading families of blackmailers were discovered only in 2016.
Cerber was discovered in March 2016 and was named for the file extension. From March to December, it hit more than 600 thousand PCs.
Illegal Cerber forums offer a “blackmailer as a service”, so attackers can send it without writing malicious code. Its operation is largely determined by the configuration file. The latest version of Cerber can encrypt almost 500 file types. It is known that when searching for files for encryption, the program can highlight the highest priority folders. Cerber is distributed mainly through spamming mail containing the Donoff loader that installs it.
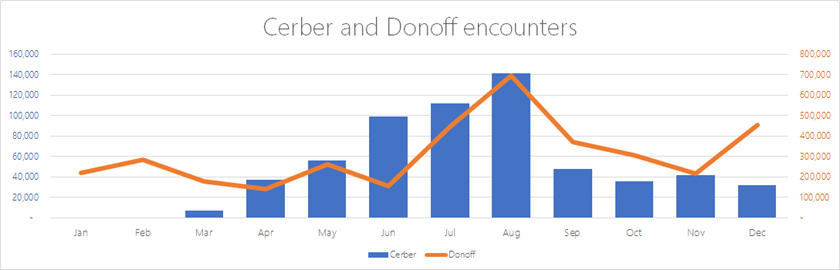
Fig. 4. The frequency of detecting Cerber has fallen sharply since September, while the prevalence of Donoff, the Cerber loader, began to increase in December.
It is also known that infection with the Cerber virus is done via Meadgive or the RIG exploit. Meadgive was the lead exploit at the end of 2016.
In 2016, Locky became the second most common blackmailer program, infecting over 500,000 computers. It was discovered in February and was also named for the file extension. Since then, it has used other extensions, including .zepto, .odin, .thor, .aeris, and .osiris.
As with Cerber, spam e-mail operators subscribe to Locky as a “blackmailer as a service”. It contains code for a cryptographic routine, and can also receive encryption keys and repurchase messages from a remote server before encrypting files.
Initially, Locky spread through the Neutrino exploit, and later they began to use junk e-mail with the Nemucod virus, which downloaded and launched Locky.
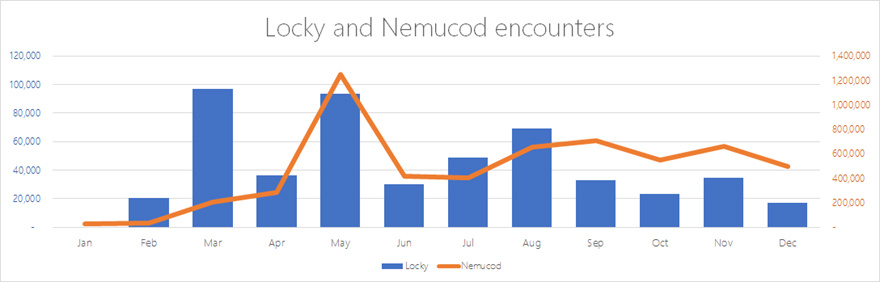
Fig. 5. The frequency of Nemucod detections in the second half of 2016 remained constant, despite the fact that the prevalence of Locky during this period decreased significantly
In 2016, the blackmailers turned into a real global threat and were discovered in more than 200 countries. In the USA alone, blackmail programs hit over 460,000 PCs. Italy and Russia are next (252 thousand and 192 thousand cases of detection, respectively). In Korea, Spain, Germany, Australia and France, over 100,000 infections have been reported.
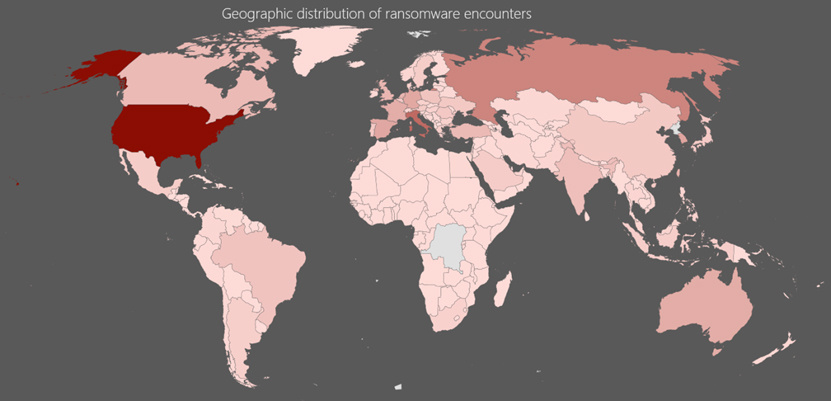
Fig. 6. Infection with blackmailers has been registered in more than 200 countries.
The largest number of Cerber infection cases is registered in the United States: 27% of the total number of infections with this virus in the world. Another powerful blackmailer, Locky, was discovered in 2016. It has become the second most common blackmailer program family in the United States.
In Italy and Russia, on the contrary, older versions of blackmailers are more common. In Italy, the most reported cases of infection with the Critroni virus, which appeared in 2014. When the blackmailer Critroni first appeared, her redemption messages were compiled in English and Russian. In later versions, other European languages appeared, including Italian.
The Troldesh virus, discovered in 2015, has become the leader in the number of infections in Russia. After encrypting the files, Troldesh displayed on the desktop a message in Russian and English that contained instructions on how to contact the attackers and payment instructions.
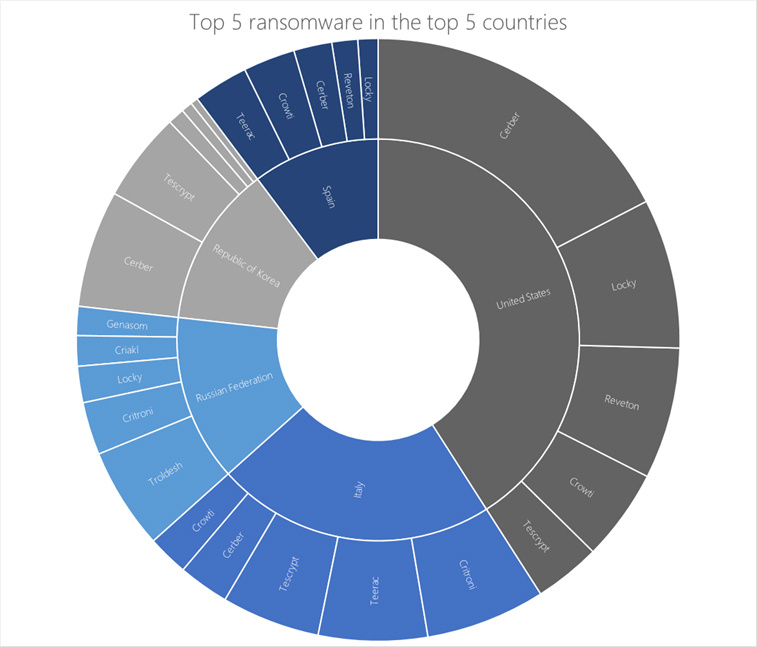
Fig. 7. The countries with the highest prevalence of blackmailing programs - the USA, Italy, Russia, Korea, Spain - are affected by different virus families, possibly due to the local nature of spam campaigns.
Despite the decline in the general distribution of blackmailing programs, attack vectors, the number of unique virus families and improvements in malicious code, we say that we still don’t see the end of this multi-factor security threat.
Microsoft has created and is constantly improving the Windows 10 operating system so that your protection tools are directly integrated into the operating system.
Most cases of infection with blackmailing programs begin with receiving e-mail messages containing Trojans loaders. This is the main vector used by cybercriminals to install blackmailers. The Office 365 Advanced Threat Protection service has machine learning capabilities that block dangerous emails containing blackmailer downloaders.
Some blackmailers penetrate computers through exploits. The Microsoft Edge Browser will help protect your computer from blackmailers by preventing exploits from running and executing these viruses. With Microsoft SmartScreen , Microsoft Edge browser blocks access to malicious websites that may contain exploits.
Device Guard can block devices and provide protection at the level of kernel virtualization, allowing only trusted applications to run and prohibiting the launch of blackmailers and other dangerous software.
The creators of blackmailing programs are perhaps one of the most productive intruders who are constantly creating new families of viruses and updating existing ones. They are also very creative in choosing attack vectors for installing blackmailers on your computers.
Windows 10 helps you immediately detect a blackmailer attack at the first sign of its occurrence. Windows Defender Antivirus detects blackmailers, as well as exploits and bootloaders that install them. Using cloud technology, this antivirus helps protect your computer from the latest threats.
Windows Defender Antivirus is built into Windows 10 and, when turned on, protects your PC against real-time threats. Regularly update Windows Defender Antivirus and other software for the most current protection of your PC.
Windows Defender Advanced Threat Protection (Windows Defender ATP) notifies security experts of suspicious activity. These actions are characteristic of some blackmailer families, such as Cerber , and may be characteristic of blackmailers in the future.
The evaluation version of Windows Defender ATP is free .
Among the existing protection tools, the most powerful will be Windows 10 Creators Update, which includes Windows Defender Antivirus and integration with Office 365 to create multi-level protection that reduces the email vulnerability for attacks.
Windows Defender Antivirus will enhance contextual recognition and machine learning capabilities that detect behavioral abnormalities and help detect viruses at different points in the infection chain. Improved integration with threat analytics provides faster blocking of spam.
Windows Defender ATP allows security professionals to isolate compromised PCs from the corporate network , stopping the spread of the virus on the network.
This update also allows you to specify the types of files to be quarantined and prevent their subsequent execution.
The threat of blackmailers may not disappear soon, but Windows 10 will continue to improve protection against this malware.
Tomorrow, September 27, at 10:00 am (MSK), we will host the international online forum “You Trust IT. The path to business security! ”, In which you will learn how to secure your project, avoid external threats, minimize the risks of losing important business information and avoid losses.
Participation is free .

Analysis of the blackmailers for 2016 showed the following:
- Each quarter of the year, over 500 million spam emails are sent, containing spam and blackmailers loaders who are trying to automatically install themselves on users' computers.
- Loaders of blackmail programs hit over 13.4 million computers.
- On the other hand, 4.5 million computers were infected with malware Meadgive and Neutrino , the main attack code of which are blackmailers.
- In 2016, blackmailers were found on 3.9 million PCs.
The impact of blackmailing programs has affected not only private users, business companies and the public sector as well. After the mainstream media reported these attacks, including that some hospital in California had paid attackers to restore important medical files, as well as a failure in the San Francisco transportation system , the idea of blackmailers went deeper. into the public mind. In September, a Europol report called the blackmailers the biggest digital threat that left behind data theft malware and online banking Trojans.
')
It is noteworthy that according to the Windows Defender antivirus, an interesting tendency is observed: having reached a peak value in August 2016 - 385 thousand registered cases of blackmail program detection - in September their number almost halved and continues to fall.

Fig. 1. Monthly frequency of detection of blackmail utility payload files, excluding downloaders and other components. Some industry data combine these two indicators.
Does this trend mean that the end of blackmailing programs is foreseen? If you look at other areas of distribution of blackmailers, it turns out that this is not the case.
Block blackmailing programs at the point of entry
To understand whether the prevalence of blackmailers is declining, it is necessary to examine other areas of the infection chain, starting with the attack vectors. Data Windows Defender Antivirus suggests otherwise.
Trojan downloaders distributed via email newsletters
Trojan downloaders such as Nemucod and Donoff install blackmailers on PCs. These downloaders are often in the form of document files or shortcuts and are distributed via email.
The number of e-mail messages containing blackmailer downloaders has not decreased. In the last quarter of 2016, 500 million such messages were recorded. Over the same period of time, bootloaders have infected at least 1 million PCs per month. It is obvious that cybercriminals did not stop using blackmailers to attack users' computers. In fact, right up to the end of 2016, we witnessed campaigns to send email messages with the Nemucod exploit that spread the Locky virus and campaigns to send the Donoff virus, through which the Cerber virus spread .

Fig. 2. Although the number of cases of blackmail program detection was significantly reduced by the end of 2016, in the second half of the year compared to the first, the frequency of infection by the blackmailer downloaders was, on average, higher.
Obviously, the decrease in cases of detection of blackmailers is not due to the fact that cybercriminals have become less diligent. There are still a huge number of emails containing Trojans-loaders of blackmailers. However, infection by blackmailing programs is blocked at the point of entry. This is an interesting move, since in 2016, blackmailing distributors switched from using exploits to e-mail messages as a more efficient infection vector.
Exploits
The Neutrino exploit was used to install the Locky blackmailer on a PC. In mid-2016, the Neutrino infection rate increased, filling the niche of the Axpergle virus (also known as the Angler) after it disappeared in June. Obviously, the prevalence of Neutrino began to decline in September, after its operators passed the reins to the cybercriminal groups.
Another popular exploit, Meadgive (also known as RIG), initially distributed the blackmailer Cerber. In 2016, Meadgive was constantly growing, becoming the most frequent malware exploit. In December 2016, the Meadgive campaign began with the latest version of the Cerber virus, which was conducted mainly in Asia and Europe.
Although exploits are being used less and less , blackmailers continue to use exploits to infect computers. This is because exploits allow blackmailers to raise permissions and launch potentially dangerous programs with fewer restrictions.
Hackers are looking for new ways
The decline of blackmailing programs has not yet come, and another evidence of this is the numerous innovations of malicious code recorded in 2016.
Cybercriminals are constantly updating their tools. For example, at the end of 2016, significant updates of the latest version of Cerber were recorded.
These malicious code enhancements are gradually being introduced in attacks such as the blackmailer as a service in which cybercriminals can get the latest versions of blackmailers on illegal forums. This provides cybercriminals with the necessary resources and motivation to launch attacks.
The following are some enhancements to the blackmailer program that we witnessed in 2016.
Attacks on servers
The discovery of the Samas blackmailer in early 2016 made these programs a major threat to commercial companies. Faced with blackmailers targeting servers, IT administrators had to not only take care of end-user protection, but also increase server protection.
Samas distribution campaigns exploited server vulnerabilities . They searched for vulnerable networks using pen test and used various components to encrypt files on servers.
Worm Features
Zcryptor had the ability to spread, which means that some blackmailers could move from one end point to another without resorting to spam campaigns. The worm virus detects network and logical drives and removable media that it can use for distribution. At the very beginning of 2017, the Spora virus was detected, showing similar behavior.
Alternative Payment and Communication
Usually, blackmailers demanded payment via Bitcoin on illegal websites of the Tor network. In response to the reduction in the number of payments from the victims, cybercriminals began to look for new methods of payment.
The blackmailer Dereilock , for example, forced its victims to contact the cybercriminals via Skype, and Telecrypt offered to use the messaging service Telegram Messenger to communicate with the cybercriminals.
Spora took the path of shareware services - a couple of files could be decrypted for the victim free of charge, and for a small amount it was possible to decrypt a number of files.
New methods of blackmail
In 2016, most blackmailers began using a countdown timer. This forces the victim to pay the ransom immediately, for fear of irretrievable loss of access to the files.
When Cerber blackmailed the program in March, she made a splash: in addition to the usual ransom report, both text and HTML, VBScript transformed the text into an audio message with a ransom demand. Therefore, Cerber was called a "talking blackmailer."
Another blackmailer CornCrypt offered to decrypt files for free, provided that the victim infects two other users. The attackers were counting on the effect of a snowball: the more victims, the greater the likelihood that one of them will pay.
New families of blackmailers - leaders of the rating
The threat from the blackmailer program most likely does not weaken, as evidenced by the emergence of new families of blackmailer programs. Of the more than 200 active families found, about half were recorded for the first time in 2016.
Most new blackmailing software families use encryption. This type of blackmailing program replaces older screen lock versions that simply lock the screen and do not use file encryption.
In 2016, many families of blackmailers appeared, using new methods and techniques. At the same time, 68% of cases of detection of blackmail programs in 2016 accounted for five leaders.

Fig. 3. Cerber and Locky, discovered in 2016, became the leaders of the year among the blackmailers
It is interesting to note that two leading families of blackmailers were discovered only in 2016.
Cerber
Cerber was discovered in March 2016 and was named for the file extension. From March to December, it hit more than 600 thousand PCs.
Illegal Cerber forums offer a “blackmailer as a service”, so attackers can send it without writing malicious code. Its operation is largely determined by the configuration file. The latest version of Cerber can encrypt almost 500 file types. It is known that when searching for files for encryption, the program can highlight the highest priority folders. Cerber is distributed mainly through spamming mail containing the Donoff loader that installs it.

Fig. 4. The frequency of detecting Cerber has fallen sharply since September, while the prevalence of Donoff, the Cerber loader, began to increase in December.
It is also known that infection with the Cerber virus is done via Meadgive or the RIG exploit. Meadgive was the lead exploit at the end of 2016.
Locky
In 2016, Locky became the second most common blackmailer program, infecting over 500,000 computers. It was discovered in February and was also named for the file extension. Since then, it has used other extensions, including .zepto, .odin, .thor, .aeris, and .osiris.
As with Cerber, spam e-mail operators subscribe to Locky as a “blackmailer as a service”. It contains code for a cryptographic routine, and can also receive encryption keys and repurchase messages from a remote server before encrypting files.
Initially, Locky spread through the Neutrino exploit, and later they began to use junk e-mail with the Nemucod virus, which downloaded and launched Locky.

Fig. 5. The frequency of Nemucod detections in the second half of 2016 remained constant, despite the fact that the prevalence of Locky during this period decreased significantly
Blackmail programs as a global threat
In 2016, the blackmailers turned into a real global threat and were discovered in more than 200 countries. In the USA alone, blackmail programs hit over 460,000 PCs. Italy and Russia are next (252 thousand and 192 thousand cases of detection, respectively). In Korea, Spain, Germany, Australia and France, over 100,000 infections have been reported.

Fig. 6. Infection with blackmailers has been registered in more than 200 countries.
The largest number of Cerber infection cases is registered in the United States: 27% of the total number of infections with this virus in the world. Another powerful blackmailer, Locky, was discovered in 2016. It has become the second most common blackmailer program family in the United States.
In Italy and Russia, on the contrary, older versions of blackmailers are more common. In Italy, the most reported cases of infection with the Critroni virus, which appeared in 2014. When the blackmailer Critroni first appeared, her redemption messages were compiled in English and Russian. In later versions, other European languages appeared, including Italian.
The Troldesh virus, discovered in 2015, has become the leader in the number of infections in Russia. After encrypting the files, Troldesh displayed on the desktop a message in Russian and English that contained instructions on how to contact the attackers and payment instructions.

Fig. 7. The countries with the highest prevalence of blackmailing programs - the USA, Italy, Russia, Korea, Spain - are affected by different virus families, possibly due to the local nature of spam campaigns.
Conclusion: the growing threat requires new countermeasures
Despite the decline in the general distribution of blackmailing programs, attack vectors, the number of unique virus families and improvements in malicious code, we say that we still don’t see the end of this multi-factor security threat.
Microsoft has created and is constantly improving the Windows 10 operating system so that your protection tools are directly integrated into the operating system.
Protection against infections by blackmailers
Most cases of infection with blackmailing programs begin with receiving e-mail messages containing Trojans loaders. This is the main vector used by cybercriminals to install blackmailers. The Office 365 Advanced Threat Protection service has machine learning capabilities that block dangerous emails containing blackmailer downloaders.
Some blackmailers penetrate computers through exploits. The Microsoft Edge Browser will help protect your computer from blackmailers by preventing exploits from running and executing these viruses. With Microsoft SmartScreen , Microsoft Edge browser blocks access to malicious websites that may contain exploits.
Device Guard can block devices and provide protection at the level of kernel virtualization, allowing only trusted applications to run and prohibiting the launch of blackmailers and other dangerous software.
Detection of blackmailers
The creators of blackmailing programs are perhaps one of the most productive intruders who are constantly creating new families of viruses and updating existing ones. They are also very creative in choosing attack vectors for installing blackmailers on your computers.
Windows 10 helps you immediately detect a blackmailer attack at the first sign of its occurrence. Windows Defender Antivirus detects blackmailers, as well as exploits and bootloaders that install them. Using cloud technology, this antivirus helps protect your computer from the latest threats.
Windows Defender Antivirus is built into Windows 10 and, when turned on, protects your PC against real-time threats. Regularly update Windows Defender Antivirus and other software for the most current protection of your PC.
Responding to blackmail attacks
Windows Defender Advanced Threat Protection (Windows Defender ATP) notifies security experts of suspicious activity. These actions are characteristic of some blackmailer families, such as Cerber , and may be characteristic of blackmailers in the future.
The evaluation version of Windows Defender ATP is free .
Enhanced protection in Windows 10 Creators Update
Among the existing protection tools, the most powerful will be Windows 10 Creators Update, which includes Windows Defender Antivirus and integration with Office 365 to create multi-level protection that reduces the email vulnerability for attacks.
Windows Defender Antivirus will enhance contextual recognition and machine learning capabilities that detect behavioral abnormalities and help detect viruses at different points in the infection chain. Improved integration with threat analytics provides faster blocking of spam.
Windows Defender ATP allows security professionals to isolate compromised PCs from the corporate network , stopping the spread of the virus on the network.
This update also allows you to specify the types of files to be quarantined and prevent their subsequent execution.
The threat of blackmailers may not disappear soon, but Windows 10 will continue to improve protection against this malware.
Tomorrow, September 27, at 10:00 am (MSK), we will host the international online forum “You Trust IT. The path to business security! ”, In which you will learn how to secure your project, avoid external threats, minimize the risks of losing important business information and avoid losses.
Participation is free .
Source: https://habr.com/ru/post/338690/
All Articles