New FinFisher cyber espionage operation: MitM attacks at the provider level?
ESET has identified new operations using FinFisher spyware, also known as FinSpy, once sold to government agencies around the world. In addition to the technical improvements of FinFisher, a new, previously unknown vector of infection was fixed, indicating possible participation in the scheme of a large Internet provider (ISP).

FinFisher has a wide range of capabilities for surveillance via a webcam and microphone, as well as keylogging and file theft functions. What distinguishes FinFisher from other surveillance tools is the contradictory information about its implementation. FinFisher positioned as a law enforcement tool, it is believed that it is used by dictatorships . We found the latest versions of FinFisher in seven countries. Unfortunately, we cannot call them, so as not to endanger anyone.
In FinFisher campaigns, various infection mechanisms are used, including targeted phishing, manual installation with physical access to devices, zero-day vulnerability, and watering hole attacks — infecting sites that potential victims allegedly visit (the scheme was used to distribute the mobile version of FinFisher).
')
The new and most disturbing in the latest FinFisher campaigns is the emergence of the man-in-the-middle scheme, where the indicated “man” is most likely at the level of the Internet provider. We have seen the use of this vector in two countries where the latest version of FinFisher is found (the other five countries use traditional infection vectors).
When the user (the object of surveillance) is going to download one of the popular legitimate applications, it is redirected to the version of the program infected with FinFisher. We saw trojanized versions of WhatsApp, Skype, Avast, WinRAR, VLC Player and some other programs. It is important to note that in theory this way you can use any legitimate application.
The attack begins when a user searches on legitimate sites for one of the mentioned applications. When he clicks on the download link, his browser receives a modified link that redirects it to a trojanized installer hosted on the attacker's server. After downloading and execution, not only the legitimate application will appear on the user's device, but also FinFisher spyware.
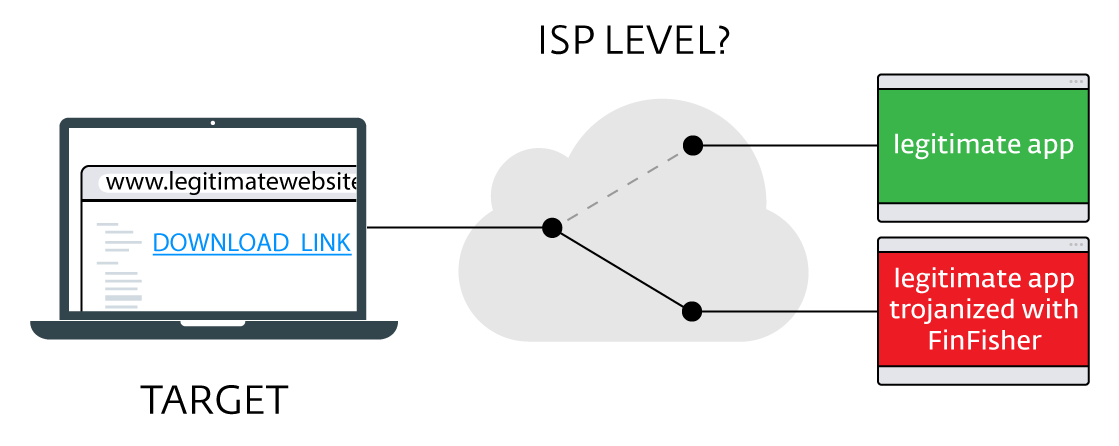
Figure 1. The infection mechanism with the latest versions of FinFisher
Forwarding is done by replacing the legitimate link with a malicious one.
The modified malicious link is delivered to the user's browser using the HTTP 307 Temporary Redirect redirect status response code (the requested content is temporarily moved to the new address). The redirection process is invisible to the user.

Figure 2. Detailed description of the infection mechanism
The latest version of FinFisher has been technically improved, the authors have focused on providing stealth. Spyware uses custom code virtualization to protect most components, including the kernel-mode driver. In addition, the code provides anti-disassembly techniques. We discovered anti-debug, anti-emulation, and anti-virtualization techniques in FinFisher.
After overcoming the first level of protection (anti-disassembly), the next level is code virtualization. In the virtual machine manager 34 handler; Almost all spyware execution is done in the interpreter, which adds another level of protection that will have to be dealt with during the analysis.

Figure 3. Visualization of numerous handlers that complicate code analysis
In the next report, we will present a more detailed technical analysis of the latest version of FinFisher.
A special approach to users interested in privacy
During the analysis of recent campaigns, we found an interesting sample - FinFisher, disguised as an executable file called Threema. It can be used to attack users who are concerned about privacy issues — Threema's legitimate application provides secure instant messaging with end-to-end encryption. There is a certain irony in the fact that a user who is seeking privacy, uploads a file with his own hands and starts the surveillance process.
The focus on users interested in encryption is not limited to instant messengers. During the study, we discovered a FinFisher infected installation file in the once very popular TrueCrypt disk encryption software.
Technically, it can be assumed that man-in-the-middle is involved in an attack at one of the stages of the path from the target computer to the legitimate server (as an option, it could be a compromised Wi-Fi point). However, the geographical distribution of the latest versions of FinFisher, discovered by ESET, suggests that MitM attacks are made at a higher level, and the most likely option is the participation of an Internet service provider (ISP).
This assumption confirms a number of facts. First, according to WikiLeaks’s leaked materials, the FinFisher developer offered a solution called “FinFly ISP” for deployment in ISP networks with functions reminiscent of those needed for MitM attacks. Secondly, the infection method (HTTP 307 redirection) is used in the same way in both countries where the infection occurred. It is unlikely that these schemes are developed and / or provided by different sources. Thirdly, all the targets hit within the country use the services of one Internet provider. Finally, the same method and redirection format is used by providers to filter Internet content in at least one of these countries.
The use of the MitM technique at the provider level, which is referred to in the document leaked to the network, has not yet been detected anywhere - until today. If this information is confirmed, new attacks with FinFisher are the beginning of new ones, unprecedented in their techniques, methods, and coverage of cyber espionage operations.
All ESET products detect and block this threat as Win32 / FinSpy.AA and Win32 / FinSpy.AB. With ESET Online Scanner, you can check your computer for a threat and delete it when it is detected. ESET users are automatically protected.
ESET detection names:
Win32 / FinSpy.AA
Win32 / FinSpy.AB
Call Forwarding:
HTTP / 1.1 307 Temporary Redirect \ r \ nLocation: \ r \ nConnection: close \ r \ n \ r \ n
The list of URLs found during the research process:
Samples (SHA-1)

FinFisher has a wide range of capabilities for surveillance via a webcam and microphone, as well as keylogging and file theft functions. What distinguishes FinFisher from other surveillance tools is the contradictory information about its implementation. FinFisher positioned as a law enforcement tool, it is believed that it is used by dictatorships . We found the latest versions of FinFisher in seven countries. Unfortunately, we cannot call them, so as not to endanger anyone.
Infecting targets
In FinFisher campaigns, various infection mechanisms are used, including targeted phishing, manual installation with physical access to devices, zero-day vulnerability, and watering hole attacks — infecting sites that potential victims allegedly visit (the scheme was used to distribute the mobile version of FinFisher).
')
The new and most disturbing in the latest FinFisher campaigns is the emergence of the man-in-the-middle scheme, where the indicated “man” is most likely at the level of the Internet provider. We have seen the use of this vector in two countries where the latest version of FinFisher is found (the other five countries use traditional infection vectors).
When the user (the object of surveillance) is going to download one of the popular legitimate applications, it is redirected to the version of the program infected with FinFisher. We saw trojanized versions of WhatsApp, Skype, Avast, WinRAR, VLC Player and some other programs. It is important to note that in theory this way you can use any legitimate application.
The attack begins when a user searches on legitimate sites for one of the mentioned applications. When he clicks on the download link, his browser receives a modified link that redirects it to a trojanized installer hosted on the attacker's server. After downloading and execution, not only the legitimate application will appear on the user's device, but also FinFisher spyware.

Figure 1. The infection mechanism with the latest versions of FinFisher
Forwarding is done by replacing the legitimate link with a malicious one.
The modified malicious link is delivered to the user's browser using the HTTP 307 Temporary Redirect redirect status response code (the requested content is temporarily moved to the new address). The redirection process is invisible to the user.

Figure 2. Detailed description of the infection mechanism
FinFisher: work out of sight
The latest version of FinFisher has been technically improved, the authors have focused on providing stealth. Spyware uses custom code virtualization to protect most components, including the kernel-mode driver. In addition, the code provides anti-disassembly techniques. We discovered anti-debug, anti-emulation, and anti-virtualization techniques in FinFisher.
After overcoming the first level of protection (anti-disassembly), the next level is code virtualization. In the virtual machine manager 34 handler; Almost all spyware execution is done in the interpreter, which adds another level of protection that will have to be dealt with during the analysis.

Figure 3. Visualization of numerous handlers that complicate code analysis
In the next report, we will present a more detailed technical analysis of the latest version of FinFisher.
A special approach to users interested in privacy
During the analysis of recent campaigns, we found an interesting sample - FinFisher, disguised as an executable file called Threema. It can be used to attack users who are concerned about privacy issues — Threema's legitimate application provides secure instant messaging with end-to-end encryption. There is a certain irony in the fact that a user who is seeking privacy, uploads a file with his own hands and starts the surveillance process.
The focus on users interested in encryption is not limited to instant messengers. During the study, we discovered a FinFisher infected installation file in the once very popular TrueCrypt disk encryption software.
Who is he - man-in-the-middle?
Technically, it can be assumed that man-in-the-middle is involved in an attack at one of the stages of the path from the target computer to the legitimate server (as an option, it could be a compromised Wi-Fi point). However, the geographical distribution of the latest versions of FinFisher, discovered by ESET, suggests that MitM attacks are made at a higher level, and the most likely option is the participation of an Internet service provider (ISP).
This assumption confirms a number of facts. First, according to WikiLeaks’s leaked materials, the FinFisher developer offered a solution called “FinFly ISP” for deployment in ISP networks with functions reminiscent of those needed for MitM attacks. Secondly, the infection method (HTTP 307 redirection) is used in the same way in both countries where the infection occurred. It is unlikely that these schemes are developed and / or provided by different sources. Thirdly, all the targets hit within the country use the services of one Internet provider. Finally, the same method and redirection format is used by providers to filter Internet content in at least one of these countries.
The use of the MitM technique at the provider level, which is referred to in the document leaked to the network, has not yet been detected anywhere - until today. If this information is confirmed, new attacks with FinFisher are the beginning of new ones, unprecedented in their techniques, methods, and coverage of cyber espionage operations.
Is my computer infected?
All ESET products detect and block this threat as Win32 / FinSpy.AA and Win32 / FinSpy.AB. With ESET Online Scanner, you can check your computer for a threat and delete it when it is detected. ESET users are automatically protected.
Indicators of compromise
ESET detection names:
Win32 / FinSpy.AA
Win32 / FinSpy.AB
Call Forwarding:
HTTP / 1.1 307 Temporary Redirect \ r \ nLocation: \ r \ nConnection: close \ r \ n \ r \ n
The list of URLs found during the research process:
hxxp://108.61.165.27/setup/TrueCrypt-7.2.rar
hxxp://download.downloading.shop/pcdownload.php?a=dad2f8ed616d2bfe2e9320a821f0ee39
hxxp://download.downloading.shop/pcdownload.php?a=84619b1b3dc8266bc8878d2478168baa
hxxp://download.downloading.shop/pcdownload.php?a=ddba855c17da36d61bcab45b042884be
hxxp://download.downloading.shop/pcdownload.php?a=d16ef6194a95d4c8324c2e6673be7352
hxxp://download.downloading.shop/pcdownload.php?a=95207e8f706510116847d39c32415d98
hxxp://download.downloading.shop/pcdownload.php?a=43f02726664a3b30e20e39eb866fb1f8
hxxp://download.downloading.shop/pcdownload.php?a=cb858365d08ebfb029083d9e4dcf57c2
hxxp://download.downloading.shop/pcdownload.php?a=8f8383592ba080b81e45a8913a360b27
hxxp://download.downloading.shop/pcdownload.php?a=e916ba5c43e3dd6adb0d835947576123
hxxp://download.downloading.shop/pcdownload.php?a=96362220acc8190dcd5323437d513215
hxxp://download.downloading.shop/pcdownload.php?a=84162502fa8a838943bd82dc936f1459
hxxp://download.downloading.shop/pcdownload.php?a=974b73ee3c206283b6ee4e170551d1f7
hxxp://download.downloading.shop/pcdownload.php?a=cd32a3477c67defde88ce8929014573d
hxxp://download.downloading.shop/pcdownload.php?a=36a5c94ffd487ccd60c9b0db4ae822cf
hxxp://download.downloading.shop/pcdownload.php?a=0ebb764617253fab56d2dd49b0830914
hxxp://download.downloading.shop/pcdownload.php?a=f35e058c83bc0ae6e6c4dffa82f5f7e7
hxxp://download.downloading.shop/pcdownload.php?a=64f09230fd56149307b35e9665c6fe4c
hxxp://download.downloading.shop/pcdownload.php?a=b3cc01341cb00d91bcc7d2b38cedc064
hxxp://download.downloading.shop/pcdownload.php?a=5fc0440e395125bd9d4c318935a6b2b0
hxxp://download.downloading.shop/pcdownload.php?a=5ca93ad295c9bce5e083faab2e2ac97a
hxxp://download.downloading.shop/pcdownload.php?a=f761984bb5803640aff60b9bc2e53db7
hxxp://download.downloading.shop/pcdownload.php?a=5ca93ad295c9bce5e083faab2e2ac97a
hxxp://download.downloading.shop/pcdownload.php?a=514893fa5f3f4e899d2e89e1c59096f3
hxxp://download.downloading.shop/pcdownload.php?a=a700af6b8a49f0e1a91c48508894a47c
hxxp://download.downloading.shop/pcdownload.php?a=36a5c94ffd487ccd60c9b0db4ae822cf
hxxp://download.downloading.shop/pcdownload.php?a=a700af6b8a49f0e1a91c48508894a47c
hxxp://download.downloading.shop/pcdownload.php?a=395ce676d1ebc1048004daad855fb3c4
hxxp://download.downloading.shop/pcdownload.php?a=cd32a3477c67defde88ce8929014573d
hxxp://download.downloading.shop/pcdownload.php?a=49d6d828308e99fede1f79f82df797e9
hxxp://download.downloading.shop/pcdownload.php?a=d16ef6194a95d4c8324c2e6673be7352Samples (SHA-1)
ca08793c08b1344ca67dc339a0fb45e06bdf3e2f
417072b246af74647897978902f7d903562e0f6f
c4d1fb784fcd252d13058dbb947645a902fc8935
e3f183e67c818f4e693b69748962eecda53f7f88
d9294b86b3976ddf89b66b8051ccf98cfae2e312
a6d14b104744188f80c6c6b368b589e0bd361607
417072b246af74647897978902f7d903562e0f6f
f82d18656341793c0a6b9204a68605232f0c39e7
df76eda3c1f9005fb392a637381db39cceb2e6a8
5f51084a4b81b40a8fcf485b0808f97ba3b0f6af
4b41f36da7e5bc1353d4077c3b7ef945ddd09130
1098ba4f3da4795f25715ce74c556e3f9dac61fc
d3c65377d39e97ab019f7f00458036ee0c7509a7
c0ad9c242c533effd50b51e94874514a5b9f2219
a16ef7d96a72a24e2a645d5e3758c7d8e6469a55
c33fe4c286845a175ee0d83db6d234fe24dd2864
cfa8fb7c9c3737a8a525562853659b1e0b4d1ba8
9fc71853d3e6ac843bd36ce9297e398507e5b2bd
66eccea3e8901f6d5151b49bca53c126f086e437
400e4f843ff93df95145554b2d574a9abf24653f
fb4a4143d4f32b0af4c2f6f59c8d91504d670b41
f326479a4aacc2aaf86b364b78ed5b1b0def1fbe
275e76fc462b865fe1af32f5f15b41a37496dd97
df4b8c4b485d916c3cadd963f91f7fa9f509723f
Source: https://habr.com/ru/post/338422/
All Articles