Solar JSOC analytics: how Russian companies are attacking
The Cyber Threat Monitoring and Response Center Solar JSOC published a cyber threat study for the first half of 2017, prepared on the basis of impersonal statistics on information security incidents among customers. The received analytics answers the questions about who, how, at what time and with what vectors and channels using the attacks of the largest Russian companies. The report is intended to inform IT services and information security about the current threat landscape and major trends.
In the first half of 2017, the average flow of IS events was 6.156 billion per day, of which about 950 per day were events with suspicion of an incident (172,477 in six months). This is about 28% more than in the first half of 2016. The proportion of critical incidents was 17.2%. Thus, if in 2016 every 9th incident was critical, now it is already every 6th . It is assumed that such dynamics is associated with a general increase in the intensity of massive and targeted attacks against organizations.
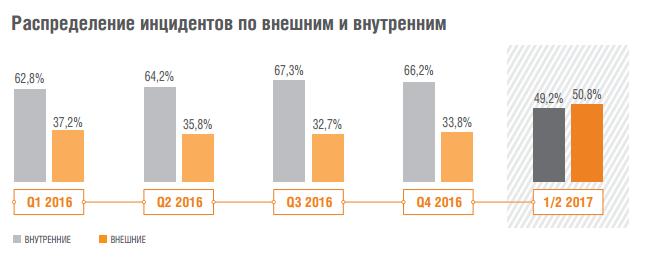
When are they attacking?
If we consider the total number of incidents, then only in 12.5% of cases they occurred at night.
')

However, if critical ones are singled out from the total mass of incidents, this figure rises to 29.4%, that is, almost one third of all cases.

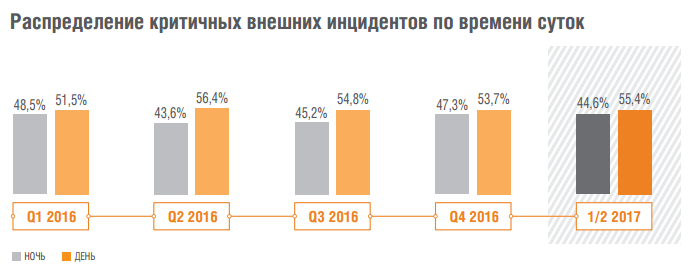
If critical incidents were caused by the actions of an external attacker, then in half of the cases (44.6%) they occurred at night.
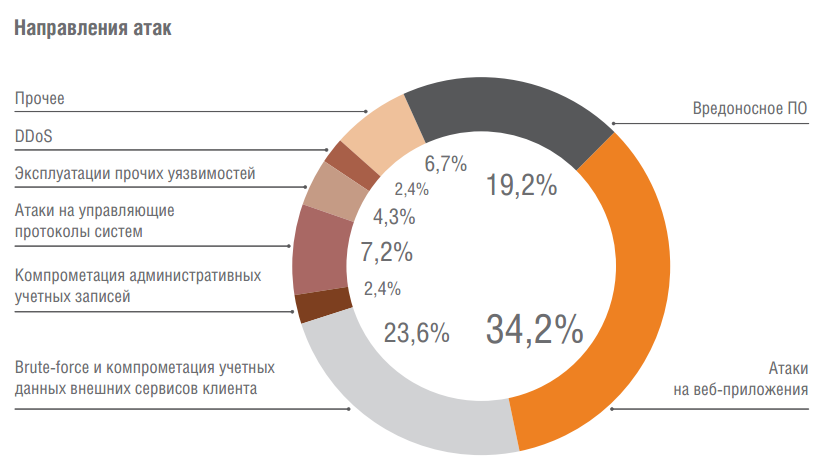
How to attack from the outside?
The main tools of cybercriminals were attacks on web applications (34.2%), compromising the credentials of external client services (23.6%) and malicious software (19.2%).
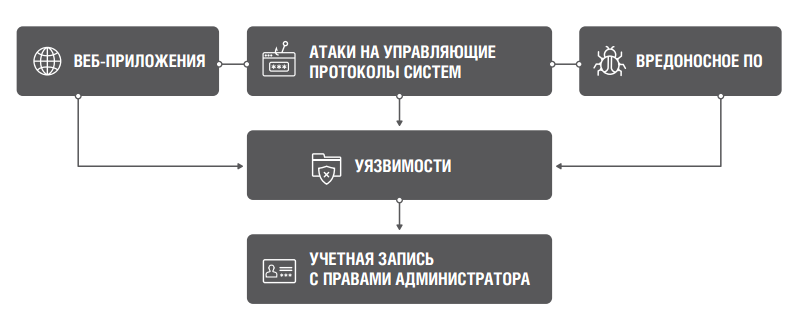
Separately, the report notes an increasing number of incidents that are part of the Kill Chain - a chain of sequential actions of a cybercriminal aimed at hacking the infrastructure and compromising key company resources.
In the first half of 2017, Solar JSOC analysts most often (in 87% of cases) encountered the following attack model: after the first penetration phase of the company’s network (statistics are described below, see page 7), attackers try to identify the most vulnerable infrastructure server (often using network scan as an intermediate tool). As such a vulnerable node can act servers with non-updated versions of the operating system. Attackers are trying to seize control of the server in order to gain access to privileged network accounts (technological accounts, records of IT administrators) from which they can secretly gain access to a large number of infrastructure objects as soon as possible.
In 13% of cases, the first step in penetrating a company was an attack on a web application (for example, an online bank), in 25% - on control protocols of systems (including exploiting Shellshock vulnerability, known since September 2014), in 62% - Implementing an organization with malicious software via email attachments or phishing links.
However, often these or other stages of attack development are even easier to implement: for example, passwords from privileged accounts are found on file servers or in the configuration of system control scripts in open form. It is not uncommon for passwords from technological accounts to be written at the domain controller level in the comments (marks) to the UZ itself and are available for reading by the entire organization, which, of course, makes it easier for attackers to gain access to them.
Interesting observations:
How to attack from the inside?
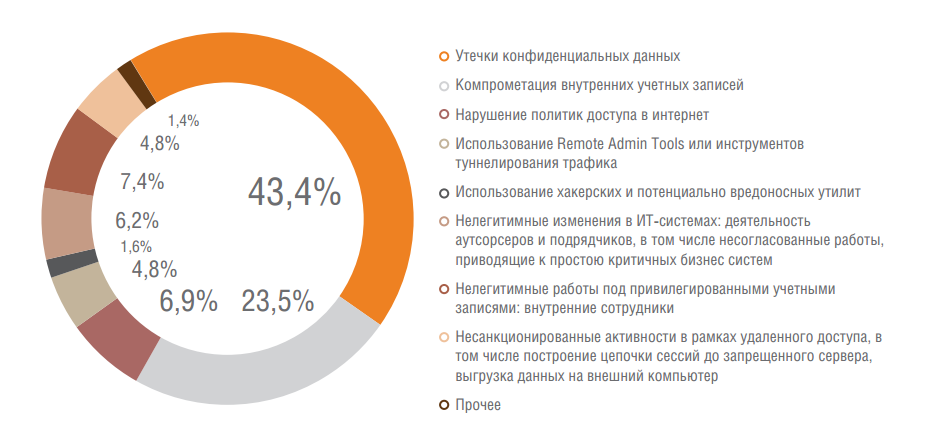
The incidents related to the actions of internal intruders have not changed significantly. In 43.4% of cases, this is information leakage, in 23.5% - compromise of internal accounts, and less than 10% is due to the use of hacking tools, remote administration tools, etc.
Interesting observations:
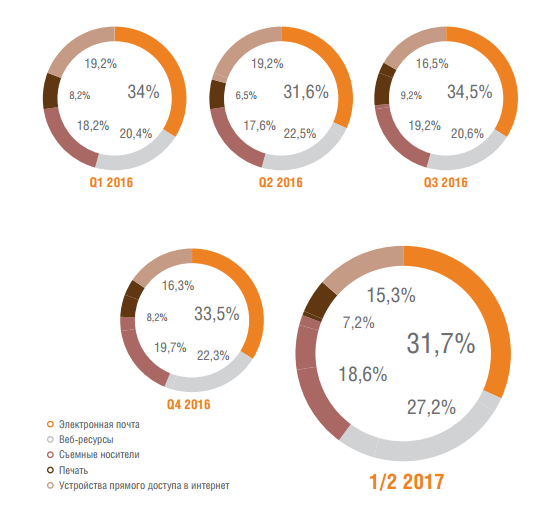
Analysis of the most “popular” channels of leaks shows that most often employees of companies use email for this purpose (31.7%), web resources (27.2%) and removable media (18.6%).
How to defend?
Technical means
About 67% of the investigated events were recorded using basic IT infrastructure services and basic security tools: firewalls and network equipment, VPN gateways, domain controllers, mail servers, basic security tools (antivirus, proxy servers, intrusion detection systems) . This suggests that the full-fledged operation and high-quality configuration of even the basic means of protection can significantly increase the level of information security of the organization.
At the same time, it is worth noting that the remaining incidents (33.1%), detected using sophisticated intellectual means of protection or analyzing business system events, carry a much larger amount of information that is critical for the company's information and economic security. They allow you to deeper and more fully see the picture of the security of the company and timely prevent critical targeted attacks.
Threat intelligence
Sources of Threat Intelligence used in Solar JSOC can be divided into the following categories:

As you can see, the correct use of free sources of information about TI can increase the security of the company and the resistance to mass attacks. But at least half of the incidents are detected only with the help of paid commercial subscriptions.
In the first half of 2017, the average flow of IS events was 6.156 billion per day, of which about 950 per day were events with suspicion of an incident (172,477 in six months). This is about 28% more than in the first half of 2016. The proportion of critical incidents was 17.2%. Thus, if in 2016 every 9th incident was critical, now it is already every 6th . It is assumed that such dynamics is associated with a general increase in the intensity of massive and targeted attacks against organizations.

When are they attacking?
If we consider the total number of incidents, then only in 12.5% of cases they occurred at night.
')

However, if critical ones are singled out from the total mass of incidents, this figure rises to 29.4%, that is, almost one third of all cases.

If critical incidents were caused by the actions of an external attacker, then in half of the cases (44.6%) they occurred at night.

How to attack from the outside?
The main tools of cybercriminals were attacks on web applications (34.2%), compromising the credentials of external client services (23.6%) and malicious software (19.2%).

Separately, the report notes an increasing number of incidents that are part of the Kill Chain - a chain of sequential actions of a cybercriminal aimed at hacking the infrastructure and compromising key company resources.
In the first half of 2017, Solar JSOC analysts most often (in 87% of cases) encountered the following attack model: after the first penetration phase of the company’s network (statistics are described below, see page 7), attackers try to identify the most vulnerable infrastructure server (often using network scan as an intermediate tool). As such a vulnerable node can act servers with non-updated versions of the operating system. Attackers are trying to seize control of the server in order to gain access to privileged network accounts (technological accounts, records of IT administrators) from which they can secretly gain access to a large number of infrastructure objects as soon as possible.
In 13% of cases, the first step in penetrating a company was an attack on a web application (for example, an online bank), in 25% - on control protocols of systems (including exploiting Shellshock vulnerability, known since September 2014), in 62% - Implementing an organization with malicious software via email attachments or phishing links.

However, often these or other stages of attack development are even easier to implement: for example, passwords from privileged accounts are found on file servers or in the configuration of system control scripts in open form. It is not uncommon for passwords from technological accounts to be written at the domain controller level in the comments (marks) to the UZ itself and are available for reading by the entire organization, which, of course, makes it easier for attackers to gain access to them.
Interesting observations:
- On average, within a month, from 2 to 5 customer services with critical vulnerabilities that have not been fixed for about a year are published on the Internet on public access. Such public services allow attackers to penetrate the company's corporate network without special preparation and complex tools and develop an attack on critical systems. Of these, 2/3 are published by administrators unintentionally, without the knowledge of information security services, thereby creating a significant risk of infrastructure compromise.
- The trend to an increase in the number of encryption viruses is not losing ground. However, if earlier analysts more often dealt with malware, whose only function is to encrypt data on an infected workstation, now encryption is usually only one of the functions. Increasingly, it is accompanied by keylogger and the ability to remotely control an infected workstation. Thus, the toolkit of attackers becomes more multitasking.
- Separately, I would like to emphasize that, despite the massive attacks of Wannacry and Petya, the figures for external incidents show high, but not dramatic growth. The reason is that mass attacks on Russian companies occur regularly, but, as a rule, remain outside the purview of the media.
- The number of cases of compromised remote access credentials has decreased. Previously, the first step of an attack on a company was often hacking into the accounts of its employees in public mail services (Mail.ru, Yandex.ru, Gmail.com), since users often set the same password for different accounts. The gradual introduction of two-factor authentication mechanisms and the complication of access algorithms in Russian companies reduced the effectiveness of this attack method.
How to attack from the inside?
The incidents related to the actions of internal intruders have not changed significantly. In 43.4% of cases, this is information leakage, in 23.5% - compromise of internal accounts, and less than 10% is due to the use of hacking tools, remote administration tools, etc.

Interesting observations:
- Despite the fact that remote access accounts are rarely compromised, the number of incidents related to the remote work of contractors is growing. According to our observations, this is due to the continued development of IT outsourcing services and the low growth of information security in IT outsourcers.
- Informational education of users is growing, but not in the way that security officers would like to see: on average, once every two months, customers of Solar JSOC register attempts to use malicious or hacking utilities by ordinary employees. For example, tools that allow you to get information about user passwords (procdump, mimikatz), network scanning and vulnerability scan systems, etc. In addition to the desire to cause direct harm to the company, employees often move ordinary curiosity.
Analysis of the most “popular” channels of leaks shows that most often employees of companies use email for this purpose (31.7%), web resources (27.2%) and removable media (18.6%).

How to defend?
Technical means
About 67% of the investigated events were recorded using basic IT infrastructure services and basic security tools: firewalls and network equipment, VPN gateways, domain controllers, mail servers, basic security tools (antivirus, proxy servers, intrusion detection systems) . This suggests that the full-fledged operation and high-quality configuration of even the basic means of protection can significantly increase the level of information security of the organization.
At the same time, it is worth noting that the remaining incidents (33.1%), detected using sophisticated intellectual means of protection or analyzing business system events, carry a much larger amount of information that is critical for the company's information and economic security. They allow you to deeper and more fully see the picture of the security of the company and timely prevent critical targeted attacks.
Threat intelligence
Sources of Threat Intelligence used in Solar JSOC can be divided into the following categories:
- Opensource - open database of indicators of malware, management servers and phishing links. As a rule, only network indicators are relevant in the context of detection using SIEM platforms.
- Reputation feeds are paid subscriptions to reputation lists of malware, management servers, and phishing links. As a rule, only network indicators are relevant in the context of detection using SIEM platforms.
- APT / IOC reporting - paid subscriptions to detailed descriptions of 0day malware, including, among other things, a description of the vulnerabilities used and host indicators of malware.
- Information Exchange - information obtained through information exchanges with government, departmental and foreign incident response centers (CERT).
- Internal Solar JSOC database - indicators obtained as a result of Solar JSOC own investigations or incident investigations.
- User experience - information obtained directly from users of clients (successful counteraction to social engineering, detection of phishing mailings, etc.).

As you can see, the correct use of free sources of information about TI can increase the security of the company and the resistance to mass attacks. But at least half of the incidents are detected only with the help of paid commercial subscriptions.
Source: https://habr.com/ru/post/338330/
All Articles