Recommendations for neutralizing threats related to the vulnerability CVE-2017-8759
Informzaschita recommends that all organizations take the necessary measures to protect their resources and ensure information security.
September 12, 2017 was published information about the vulnerability CVE-2017-8759 , which is associated with remote code execution using Microsoft Office documents.
Vulnerability was discovered by FireEye due to the fixation of a number of attacks using a previously unknown exploit.
Vulnerability CVE-2017-8759 subject to Microsoft Windows operating systems. Operation of this vulnerability with the implementation of third-party code is performed using the vulnerable component of the Microsoft .NET Framework - SOAP WSDL Parser, allows you to obtain user rights on a vulnerable system.
This vulnerability is highly critical for several reasons:
')
1) The exploitation of the vulnerability does not require the use and inclusion of macros in office applications Microsoft Office;
2) To exploit the vulnerability, a user simply opens a malicious file;
3) The exploit code for this vulnerability is published in open access on the Internet and this means that this vulnerability can be exploited by any user of the network.
Threat Name: CVE-2017-8759 ".NET Framework Remote Code Execution Vulnerability".
Possible attack vectors: targeted phishing with Microsoft Office document attachment (doc, rtf, etc.).
Vulnerable systems: Microsoft Windows operating systems from Windows 7 to the latest versions, Microsoft .NET Framework component from version 2.0 to 4.72. A complete list of vulnerable OS and components is presented here .
The scale of the spread of the threat: at the moment one phishing campaign has been fixed that uses an exploit for the CVE-2017-8759 vulnerability to install the FINSPY Trojan (FinFisher).
To mitigate the risks associated with the CVE-2017-8759 vulnerability, we recommend:
1. Install a security update that matches the version of the operating system and the version of the Microsoft .NET Framework. A complete list of vulnerable OS and components is provided by reference ;
2. Update the signature database of the installed anti-virus software;
3. Update the database of IPS signatures, secure mail and web gateways (ESG, WSG) and other signature-based GIS.
Note: the link contains identifiers of full updates, while for systems up to Windows 8.1 and Windows Server 2012 R2 there is a possibility to install only security updates - the Security Only Release column in the original Microsoft table.
It is also necessary to update the signature databases of the installed anti-virus software in order to prevent FINSPY infection.
A remote code execution vulnerability registered with identifier CVE-2017-8759 has been discovered by FireEye experts in the WSDL Parser (Web Services Description Language) module in the Microsoft .NET Framework. The method of the IsValidUrl module does not correctly check the transmitted values for the presence of the CRLF sequence (line and carriage). Thus, an attacker using this sequence has the ability to inject malicious code into the module execution process.
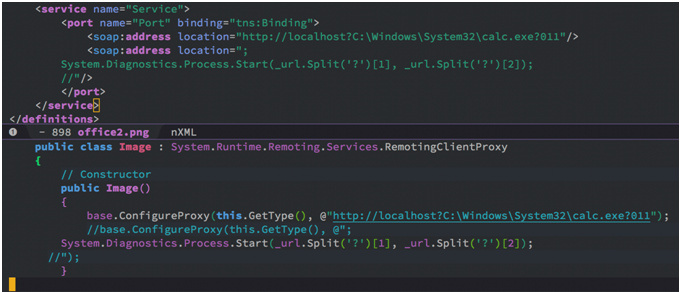
Figure 1. Vulnerability example
Currently known hash amounts (MD5) of malicious files:
- malicious file “Project.doc”: fe5c4d6bb78e170abf5cf3741868ea4c;
- FINSPY: a7b990d5f57b244dd17e9a937a41e7f5.
The team of Informzaschity experts is ready to advise all companies concerned about the current situation on risks and threats, as well as to quickly protect the infrastructure.
Author: Technical Directorate of Informzaschita Company
General description of the threat
September 12, 2017 was published information about the vulnerability CVE-2017-8759 , which is associated with remote code execution using Microsoft Office documents.
Vulnerability was discovered by FireEye due to the fixation of a number of attacks using a previously unknown exploit.
Vulnerability CVE-2017-8759 subject to Microsoft Windows operating systems. Operation of this vulnerability with the implementation of third-party code is performed using the vulnerable component of the Microsoft .NET Framework - SOAP WSDL Parser, allows you to obtain user rights on a vulnerable system.
This vulnerability is highly critical for several reasons:
')
1) The exploitation of the vulnerability does not require the use and inclusion of macros in office applications Microsoft Office;
2) To exploit the vulnerability, a user simply opens a malicious file;
3) The exploit code for this vulnerability is published in open access on the Internet and this means that this vulnerability can be exploited by any user of the network.
Threat Name: CVE-2017-8759 ".NET Framework Remote Code Execution Vulnerability".
Possible attack vectors: targeted phishing with Microsoft Office document attachment (doc, rtf, etc.).
Vulnerable systems: Microsoft Windows operating systems from Windows 7 to the latest versions, Microsoft .NET Framework component from version 2.0 to 4.72. A complete list of vulnerable OS and components is presented here .
The scale of the spread of the threat: at the moment one phishing campaign has been fixed that uses an exploit for the CVE-2017-8759 vulnerability to install the FINSPY Trojan (FinFisher).
Preventive measures
To mitigate the risks associated with the CVE-2017-8759 vulnerability, we recommend:
1. Install a security update that matches the version of the operating system and the version of the Microsoft .NET Framework. A complete list of vulnerable OS and components is provided by reference ;
2. Update the signature database of the installed anti-virus software;
3. Update the database of IPS signatures, secure mail and web gateways (ESG, WSG) and other signature-based GIS.
Note: the link contains identifiers of full updates, while for systems up to Windows 8.1 and Windows Server 2012 R2 there is a possibility to install only security updates - the Security Only Release column in the original Microsoft table.
It is also necessary to update the signature databases of the installed anti-virus software in order to prevent FINSPY infection.
Vulnerability description
A remote code execution vulnerability registered with identifier CVE-2017-8759 has been discovered by FireEye experts in the WSDL Parser (Web Services Description Language) module in the Microsoft .NET Framework. The method of the IsValidUrl module does not correctly check the transmitted values for the presence of the CRLF sequence (line and carriage). Thus, an attacker using this sequence has the ability to inject malicious code into the module execution process.

Figure 1. Vulnerability example
Indicators of compromise
Currently known hash amounts (MD5) of malicious files:
- malicious file “Project.doc”: fe5c4d6bb78e170abf5cf3741868ea4c;
- FINSPY: a7b990d5f57b244dd17e9a937a41e7f5.
The team of Informzaschity experts is ready to advise all companies concerned about the current situation on risks and threats, as well as to quickly protect the infrastructure.
Author: Technical Directorate of Informzaschita Company
Source: https://habr.com/ru/post/338256/
All Articles