The results of the summer internship 2017 in Digital Security. Security Analysis Division

Our last year's internship experience was successful, so, as promised, we decided to repeat. This time we recruited interns in two technical departments: research and security analysis. This summer we have tried to improve our internship program, and in general, to reach a new level in this difficult but pleasant business.
This year there were much more people willing to get into our company, the selection criteria were tougher, so we had to try and select the best of the best. As further developments showed, we were not mistaken in our choice. But first things first.
')
brief information
Digital Security has a security analysis department whose employees break everything down (c). And if specifically, our tasks include conducting pentest, security analysis and code analysis of mobile and web applications and corporate software, as well as assessing the awareness of company employees on security measures using social engineering methods and testing D / DoS attack resistance . We waited for enthusiasts close in spirit, ready to understand interesting problems and not retreating before difficulties.
Introduction
Applications for internship came from both students and already well-established specialists in related fields of information security, who decided to raise their professional level. Like last year, there was an opportunity to train remotely: if you could not be present in our office, it was quite possible to work on a number of tasks from home or even from another city. Still, it was much nicer to be present personally: office trainees received not only knowledge and experience, but also branded nishtyaki from Dsec :)

Company mugs and secret envelope
How did the selection process go? Anyone could fill out an electronic form on our website or send their answers to traineeship@dsec.ru. Remote trainees were selected mainly based on the survey results in the questionnaire, as well as on the basis of their answers to some additional questions asked by e-mail. We conducted interviews with office trainees in order to assess their level of preparation, and also offered them a list of topics that we had compiled beforehand. Trainees could choose up to three positions from the list. If any of the guys had their own interesting topic, in which he would like to understand, we, of course, were attentive to every proposal.
From the new: this year we launched a laboratory environment in which everyone could practice exploiting vulnerabilities, searching for flags, and generally testing their strength and skills.
We also conducted various lectures, trying to make it useful for everyone to listen to them, regardless of the level of training in information security. For example, the topics were:
- Over the Garden Wall: What is interesting can be found in the WEB (Denis Rybin)
- Introduction to WEB, SOP (Alexey Tyurin)
- Intelligence in the networks (Alexey Pertsev)
- NFC, payment cards, attacks on them (Yegor Saltykov, Ilya Bulatov)
- Lectures from fellow reversers
But the interns here not only listened, but also spoke - following the results of the internship, the guys held a meeting in a similar format for us, where they shared their research results. Some worked in teams of 2-3 people, and we were very curious whether such group work would be productive. Secretly, say yes ... but stay tuned :)

As mentors, I managed to take part in the project for almost the entire security analysis department. Each had 2-3 interns, and some even had more. Take a bite, for example:
Just like last year, we asked our trainees to share their impressions, and now we are happy to share honest feedback with you.
Questions for the mini-interview were as follows:
- Why did you decide to train in Digital Security? What attracted you to the company?
- Did you like the internship? What is especially remembered? How much reality coincided with your expectations?
- Tell us about your task / tasks.
- Did the tasks you worked on during the internship seem interesting? Was there something you wanted to do, but failed?
- Are you ready to return to the company for an internship or a job?
Below are some answers (not all have reached the end and have worked on their topics) interns.
Alexander Romanov, topic “WAF Bypass”:
- I have been interested in practical security for quite some time. The ability to find vulnerabilities before criminal elements take advantage of them seems to me a very important task. Digital Security has extensive experience in conducting pentest and research in the field of practical information security. I also really like the company's activity in the life of the Russian information security, in particular, the organization ZeroNights.
- The internship really liked its diversity. This is the creation of his project, and interesting lectures from all areas of practical information security, and practical experience in the passage of laboratories. Also an important point, I consider the possibility of live communication. Sometimes an interesting idea can be born from the usual communication about technologies or find an answer to a question.
- My task was to create an algorithm and write an application for finding bypasses in WAF.
- At the moment, my topic is not over yet, because it turned out to be more extensive than it looked at first glance. I plan to significantly expand the capabilities of the application. In the field of practical information security there are still a lot of topics that I would like to do. So my “internship” will never end.
- At some point during my internship, I decided to send my CV to Digital Security. And now I am an employee. Separately, I would like to note the interview. I never thought that at the interview you can get new knowledge or structure existing ones. For this special thanks to those who then attended)
The result of the work can be found here: https://github.com/SndVul/WAF_Bypass_Helper
Igor Fisenko, “GSM Rouge BS” topic:
- A fairly well-known company in Russia with the name, projects and specialists appearing at top conferences on information security. I think the choice of my first internship in life at the moment is obvious.
- In the company of a friendly and responsive team, I was always heard and received answers to any of my questions. All conditions were created for the convenient work of the interns, all this was supported by various lectures. Special thanks for your patience and answers to my stupid questions to curators Ilya and Gleb from the security analysis department.
- It so happened that I worked on the task, not one, but with another person. We tried to create a fake GSM base station on BladeRF (YateBTS) and OsmocomBB to intercept various data from clients of our dummy network.
- The tasks were very interesting, but personally I overestimated my capabilities and could not fully reveal the topic of this work. I completed a certain part, but could not sum up the implementation of the work done due to lack of time due to my own mistake. There was also the topic “Social Engineering” with very interesting tasks that I saved for myself, I would like to do this in the near future.
- If taken again, then of course yes. For yourself, you need to tighten your skills, create a portfolio and again return to work with new knowledge and forces. Company thank you very much.

Add-on base station YateBTS

Information about the tower to which you managed to connect
Lyrchikov Igor, topic “Vulnerabilities in NagiosXI”:
- My friends worked and trained in DSec, I heard only positive feedback from them, so when I saw the selection for an internship I went without thinking.
- Everything was on the level! I liked the lectures and high-quality feedback from the curators.
- Before the internship, I had mostly only theoretical and superficial knowledge in the search for web-based vulnerabilities, I wanted to go beyond the banal XSS search, for which bb is paid an average of $ 500, and ultimately did not lose)
- A colleague and I were looking for vulnerabilities in the Nagios monitoring system. Initially, there was intelligence and awareness of the business logic of the application, analysis of already closed vulnerabilities, and after that a rapid breakthrough: found several XSS, refined the vector with RCE and combined the vulnerabilities into one attack vector. After this, the main task was completed, reported to developers about vulnerabilities and a little work on tasks that were not originally in our scope. It was cool)
- The tasks were interesting, I liked the work format, in which there was no pressure or control - so the tasks were solved in the hours of maximum productivity. Even after the completion of the internship, we continue to engage in other monitoring systems (zabbix, prtg) and prepare materials for ZeroNights articles and conferences on all of this (I hope they will approve our application). So there are still tasks, and a lot of work)
- Strange question) Of course we are ready and with great pleasure! Thanks to the leadership, organizers and curators for this movement!

Output via php shell contents / etc / passwd
The following 2 people worked as a team and dealt with a common theme - Cisco wireless technology.
Julia Sharafitdinova:
- I learned about DSec over a year ago. Then I also wanted to try an internship, but over time it did not work out. And this year, when I learned that I could go, I hoped that they would take me)
- It was attracted by the fact that the company is engaged in information security in all areas (as it seemed to me)), and not just in one, for example, reverse engineering.
- Internship very much. The guys presented a variety of topics to choose from for every taste, as they say. It was nice to work with specialists and guys like me. Of course, I got a lot of new practice. An important point - I liked it very much that the lectures were held: it was possible to study my own topic and at the same time try something else.
- I had an internship theme - “Cisco Wireless Technology”. It was originally planned to build a network and learn technologies such as 802.11w, Clear Air. But a lot of time was spent on administration (which is also an interesting experience for me). Wifi was configured and it turned out to “play around” with Cisco equipment (real and virtual).
- It was a very rewarding experience for me. I would love to return to DSec :)

Cisco Catalyst Switch 3850
Nikolay Durnikin:
- DSec is one of the few Russian companies involved in information security. Unlike Kaspersky Lab, it is not a giant empire, but a cozy little republic. Among the topics for internship, I found one that I have been interested in for more than a year. Actually, I dedicated two months of internship to her.
- Internship very much. I gained experience with industrial equipment, developed network administration skills, frolicked in the lab, played table football. Once even managed to try an unripe walnut. The internship exceeded all expectations. Before her, I assumed that the curator would give routine tasks, and I would blindly carry them out. But everything turned out differently - you can retreat from the proposed plan, there was a lot of room for independent solution of non-trivial tasks.
- I needed to examine for vulnerabilities the products offered by Cisco for administering large corporate networks. To do this, it was necessary to first deploy such a network, then deal with the settings, play with them, find errors.
- In the course of solving problems, a lot of pitfalls came to light, which I had never thought about before. Each time it was very interesting to put crutches and reinvent the next bike when solving such problems. I stopped at installing Cisco ISE. Very interesting system, I would like to study it better. But we didn’t manage to install it (again, due to unforeseen problems with images / iron / virtualization).
- If I have free time, I’ll be happy to return to DSec.
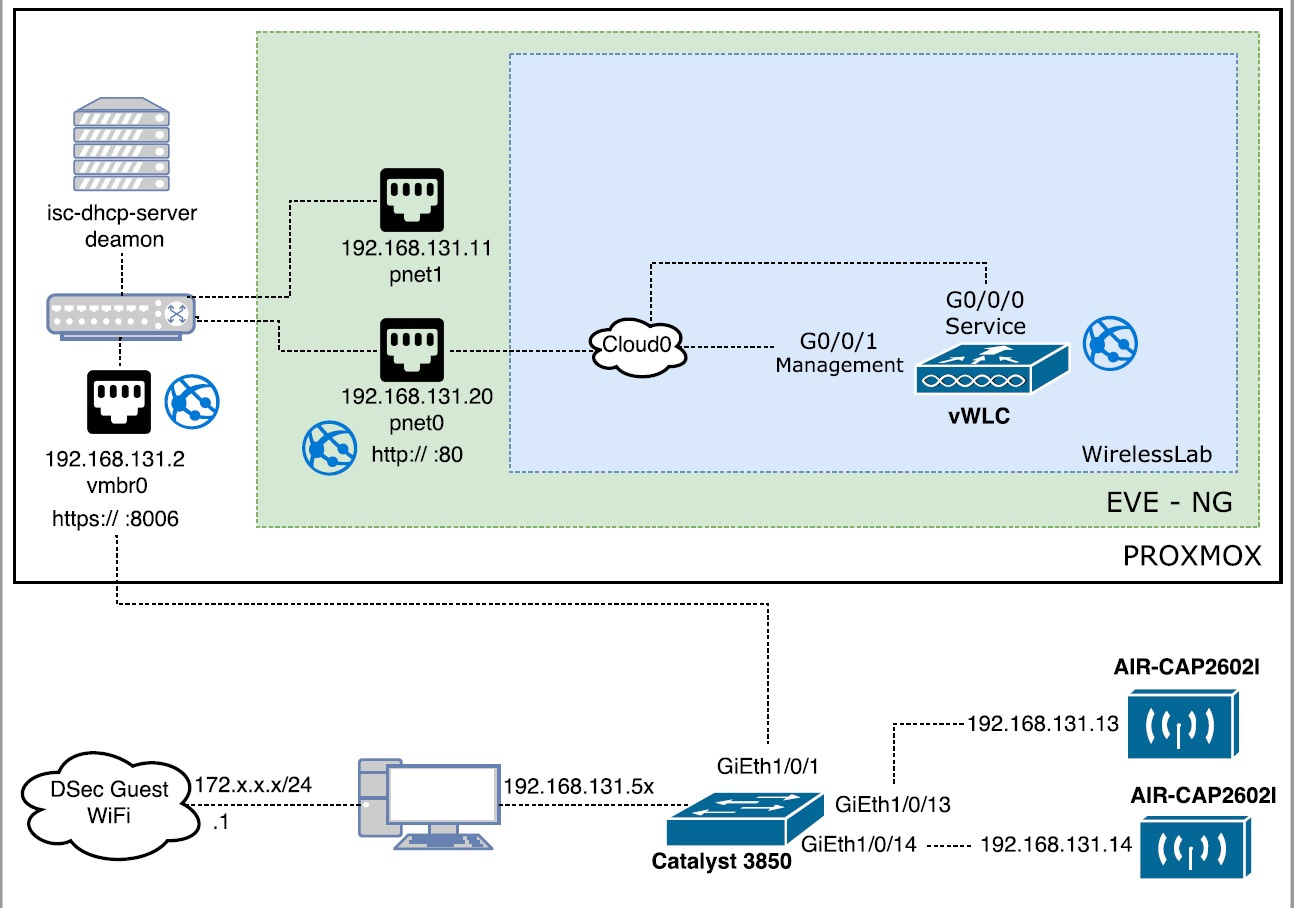
General scheme of the stand
Arseny Sinev, Shellshock checker tool:
- DSec attracted me by the description of a friend who said that I would regret if I did not register for participation in the internship. He knew that I would be interested, and therefore suggested.
- I really liked the internship, very interesting tasks, a cool team, both in the DSec and among the interns. Especially memorable presentations and reports, of course. Reality coincided with expectations, my previous practice was much worse, because I had to come to the “office” at 8:30 and sit until 5 pm without the right to leave the territory: D
- It's simple. Programming and Research on Shellshock vulnerability, that's all. I had to convert a large amount of material and Coca-Cola into several small python scripts.
- Tasks are one of the most interesting, which I only had to solve. I also wanted to do the reverse, but in the meantime, I solved Crackme from FantOm, so there was no problem with that. Developing exploits and vulnerability testing tools is probably one of the areas in which I could succeed, just need to just do more and more of this, and not jump between different areas in search of the right one.
- I would be happy to return for internship and work, the kind of information security in DSec seemed to me much more interesting than information security in the state and defense sector.
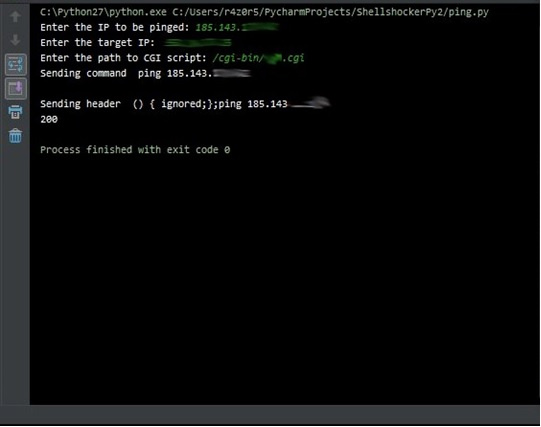
Ping the IP address from where the malicious request was sent

Listening to a response from a vulnerable host using tcpdump
Conclusion
We took into account last year's results, changed and improved some points in our program, corrected something already in the process ... In the end, we can say that everything went well - the interns were satisfied, and we ourselves were pleased to work with them.
Soon there will be another interesting article, already from colleagues from the research department. They will sum up their internship and tell a lot of interesting things.
We are waiting for all the new internship!
Source: https://habr.com/ru/post/338026/
All Articles