Configure two-factor authentication in the Astra Linux Directory domain
In this post, we decided to talk about domain authentication in Linux, using smart cards and JaCarta PKI USB tokens as the second authentication factor. If there is quite a lot of information about local authentication via PAM-module, then the issue of domain infrastructure and authentication using Kerberos tickets in Linux is poorly addressed, especially in Russian. Let's take Astra Linux as an operating system and use the example of the Astra Linux Directory (ALD) to show it.
The benefit of this solution is obvious - it allows you to abandon user password authentication, which will help drastically reduce the influence of the “human factor” on system security. Plus it will give a number of advantages from the use of electronic keys within the operating system, after authentication in the domain.
Domain Astra Linux Directory (ALD) is designed to organize a single user space (domain of a local area network) in automated systems.
ALD uses LDAP, Kerberos5, Samba / CIFS technologies and provides:
')
JaCarta PKI is a line of PKI tokens for strict authentication of users in corporate systems, safe storage of key containers of software SKZI and digital certificates of the Russian manufacturer - the company “Aladdin RD” .

In the Astra Linux Directory (ALD) environment, JaCarta PKI dongles can be used for two-factor user authentication in the ALD domain and rejection of passwords. In addition, with the same electronic keys, you can perform various scenarios inside the OS, after authentication, such as: electronic signature, storage of key containers, access to Web resources, key forwarding in an MS Windows session. Access to VDI services, such as VmWare or Citrix.
It is assumed that ALD is already deployed, there is at least one domain user who can authenticate with a password, the time of the client and the server are the same.
To support the JaCarta PKI smart card on the client and server, install the following packages: libccid, pcscd, libpcsclite1 . After installing these mandatory packages, install the IDProtectClient driver package , which can be downloaded from the official website of Aladdin RD.
To support the Kerberos subsystem’s smart card, install the krb5-pkinit package on the client and server additionally to the pre-installed ald / kerberos packages.
To enable the release of keys and certificates on the JaCarta PKI on the server, also install the libengine-pkcs11-openssl and opensc packages .
As a certificate authority (CA) , OpenSSL will be used.
OpenSSL is an open source cryptographic package for working with SSL / TLS. Allows you to create RSA, DH, DSA keys and X.509 certificates, sign them, generate CSR and CRT.
All settings in the manual are made for the test domain EXAMPLE.RU. We assume that the server and the client belong to the domain EXAMPLE.RU, the server name is kdc, and the client is client. When setting up, use the name of your domain, server and client. Perform the following steps.
The contents of the pkinit_extensions file (it should be placed in the directory where you run the commands from):
Make sure the libengine-pkcs11-openssl and opensc packages are installed . Connect the device to be prepared.
Initialize the device, set the user PIN. Remember that device initialization will delete all data on the JaCarta PKI permanently.
For initialization, you must use the pkcs11-tool utility.
pkcs11-tool --slot 0 --init-token --so-pin 00000000 --label 'JaCarta PKI' --module /lib64/libASEP11.so,
Where:
--slot 0 - indicates which virtual slot the device is connected to. As a rule, this is slot 0, but there may be other values - 1.2, etc .;
- init-token - token initialization command;
--so-pin 00000000 - JaCarta PKI admin PIN. The default value is 00000000;
--label 'JaCarta PKI' - device label;
--module /lib64/libASEP11.so - specifies the path to the library libASEP11.so. Installed as part of the idprotectclient package, see the section “Installing drivers on the server and client”.
To set the user PIN code, use the command:
pkcs11-tool --slot 0 --init-pin --so-pin 00000000 --login --pin 11111111 --module /lib64/libASEP11.so,
Where:
--slot 0 - indicates which virtual slot the device is connected to. As a rule, this is slot 0, but there may be other values - 1.2, etc .;
- init-pin - command for setting user PIN;
--so-pin 00000000 - JaCarta PKI admin PIN. The default value is 00000000;
--login - login command;
--pin 11111111 - user PIN;
--module /lib64/libASEP11.so - specifies the path to the library libASEP11.so. Installed as part of the idprotectclient package, see the section “Installing drivers on the server and client”.
Generate keys on the device, to do this, enter the following command:
pkcs11-tool --slot 0 --login --pin 11111111 --keypairgen --key-type rsa: 2048 --id 42 --label “test1 key” --module /lib64/libASEP11.so,
Where:
--slot 0 - indicates which virtual slot the device is connected to. As a rule, this is slot 0, but there may be other values - 1.2, etc .;
--login --pin 11111111 - indicates that you should log in as a user with the PIN code "11111111". If your card has a different user PIN, enter it;
--keypairgen --key-type rsa: 2048 - indicates that keys with a length of 2048 bits must be generated;
--id 42 - sets the attribute CKA_ID key. CKA_ID can be any;
Remember this value! It is necessary for the further steps of preparing the device for operation.
--label “test1 key” - sets the attribute CKA_LABEL key. Attribute can be any;
--module /lib64/libASEP11.so - specifies the path to the library libASEP11.so. Installed as part of the idprotectclient package, see the section “Installing drivers on the server and client”.
Generate a certificate request using the openssl utility. To do this, enter the following commands:
Note the -new-key 0:42 , where 0 is the virtual slot number with the device, 42 is the CKA_ID attribute of the keys generated earlier.
The information that must be specified in the request should be set in the field "/ C = RU / ST = Moscow / L = Moscow / O = Aladdin / OU = dev / CN = test1 (! Your_User!) / EmailAddress=test1@mail.com ".
It is necessary to set variable environments
$ export REALM = EXAMPLE.RU # Your Domain
$ export CLIENT = test1 # Your user
and issue a certificate to the user.
$ openssl x509 -CAkey cakey.pem -CA cacert.pem -req -in client.req -extensions client_cert -extfile pkinit_extensions -out client.pem –days 365
Next, recode the received certificate from PEM to DER.
# openssl x509 -in client.pem -out client.cer -inform PEM -outform DER
Record the received certificate on the token.
pkcs11-tool --slot 0 --login --pin 11111111 --write-object client.cer --type 'cert' --label 'Certificate' --id 42 --module /lib/libASEP11.so,
Where:
--slot 0 - indicates which virtual slot the device is connected to. As a rule, this is slot 0, but there may be other values - 1.2, etc .;
--login --pin 11111111 - indicates that you should log in as a user with the PIN code "11111111". If your card has a different user PIN, enter it;
--write-object ./client.cer - indicates that it is necessary to write the object and the path to it;
--type 'cert' - indicates that the type of the recorded object is a certificate;
'cert' --label 'Certificate' - sets the certificate CKA_LABEL attribute. Attribute can be any;
- id 42 - sets the attribute CKA_ID of the certificate. The same CKA_ID must be specified as for keys;
- module /lib64/libASEP11.so - indicates the path to the library libASEP11.so.
Create the / etc / krb5 / directory on the client. Copy the CA certificate (cacert.pem) from the server to / etc / krb5 / .
Configure kerberos in /etc/krb5.conf. Section [libdefaults] supplement the following lines.
Perform a check:
kinit When the PIN request line appears on the card, enter it.
To verify that the kerberos ticket was successfully received for a user, enter the klist command. To remove the ticket - kdestroy.
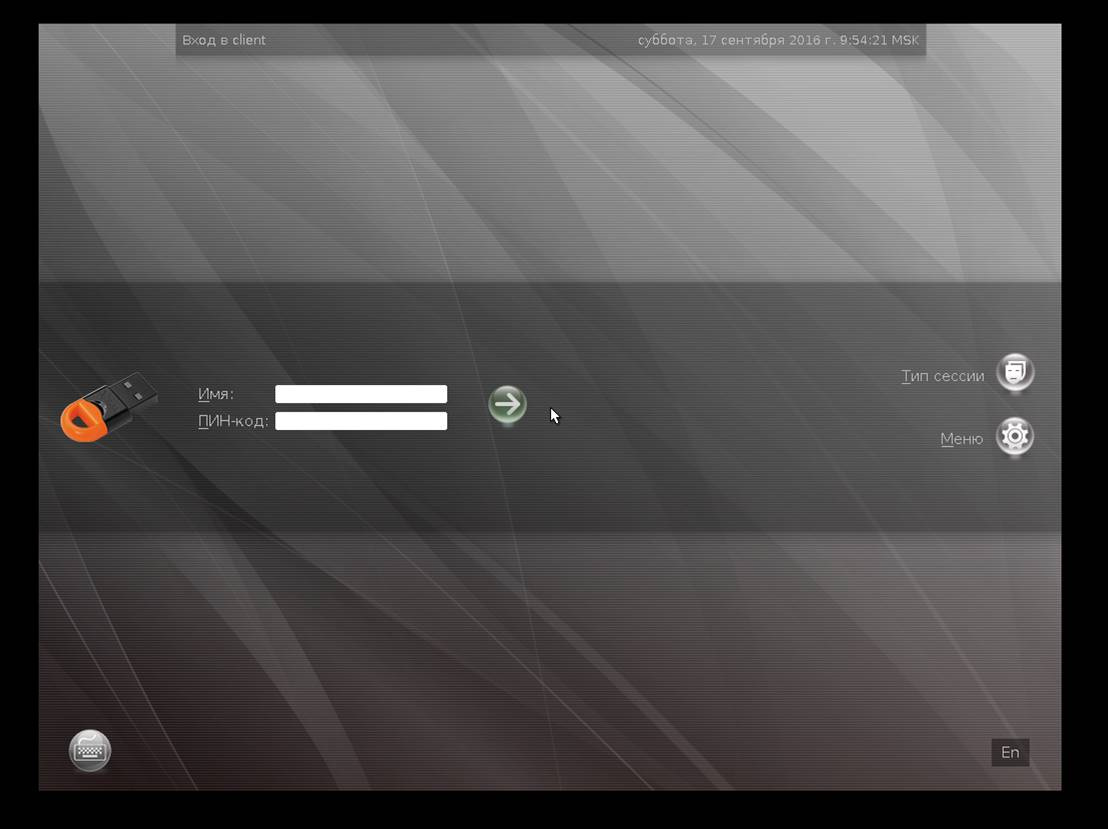
To log in to the domain using a smart card, on the OS login screen, enter the PIN from the smart card instead of the password.
At this setting is over. Yes, unfortunately, the system itself does not change or adjust the login window for the smart card, and it will be standard, but if you make some secret efforts, you can achieve a beautiful result.
The benefit of this solution is obvious - it allows you to abandon user password authentication, which will help drastically reduce the influence of the “human factor” on system security. Plus it will give a number of advantages from the use of electronic keys within the operating system, after authentication in the domain.
Some introductory information about the Astra Linux Directory (ALD) and JaCarta PKI
Domain Astra Linux Directory (ALD) is designed to organize a single user space (domain of a local area network) in automated systems.
ALD uses LDAP, Kerberos5, Samba / CIFS technologies and provides:
')
- centralized storage and management of user and group accounts;
- pass-through authentication of users in the domain using the Kerberos5 protocol;
- the operation of a global repository of home directories accessible via Samba / CIFS;
- automatic configuration of UNIX, LDAP, Kerberos, Samba, PAM configuration files;
- LDAP and Kerberos database compliance support;
- backup copies of LDAP and Kerberos databases;
- integration into the domain of the distribution database, email servers, Web-servers, print servers and other features.
JaCarta PKI is a line of PKI tokens for strict authentication of users in corporate systems, safe storage of key containers of software SKZI and digital certificates of the Russian manufacturer - the company “Aladdin RD” .

In the Astra Linux Directory (ALD) environment, JaCarta PKI dongles can be used for two-factor user authentication in the ALD domain and rejection of passwords. In addition, with the same electronic keys, you can perform various scenarios inside the OS, after authentication, such as: electronic signature, storage of key containers, access to Web resources, key forwarding in an MS Windows session. Access to VDI services, such as VmWare or Citrix.
Setup process
Demo zone example
- Server - Astra Linux Smolensk SE 1.5 4.2.0-23-generic, x86_64, with installed packages:
- JaCarta IDProtect 6.37 ;
- libccid;
- pcscd;
- libpcsclite1;
- krb5-pkinit;
- libengine-pkcs11-openssl;
- opensc.
- JaCarta IDProtect 6.37 ;
- Client - Astra Linux Smolensk SE 1.5 4.2.0-23-generic, x86_64, with installed packages:
- JaCarta IDProtect 6.37 ;
- libccid;
- pcscd;
- libpcsclite1;
- krb5-pkinit.
- JaCarta IDProtect 6.37 ;
It is assumed that ALD is already deployed, there is at least one domain user who can authenticate with a password, the time of the client and the server are the same.
Installing drivers on the server and client
To support the JaCarta PKI smart card on the client and server, install the following packages: libccid, pcscd, libpcsclite1 . After installing these mandatory packages, install the IDProtectClient driver package , which can be downloaded from the official website of Aladdin RD.
To support the Kerberos subsystem’s smart card, install the krb5-pkinit package on the client and server additionally to the pre-installed ald / kerberos packages.
To enable the release of keys and certificates on the JaCarta PKI on the server, also install the libengine-pkcs11-openssl and opensc packages .
Installing and configuring a certificate authority on the server
As a certificate authority (CA) , OpenSSL will be used.
OpenSSL is an open source cryptographic package for working with SSL / TLS. Allows you to create RSA, DH, DSA keys and X.509 certificates, sign them, generate CSR and CRT.
All settings in the manual are made for the test domain EXAMPLE.RU. We assume that the server and the client belong to the domain EXAMPLE.RU, the server name is kdc, and the client is client. When setting up, use the name of your domain, server and client. Perform the following steps.
- Create a CA directory with the mkdir / etc / ssl / CA command and navigate to it. Generated keys and certificates will be placed in this directory.
- Create a key and CA certificate:
$ openssl genrsa -out cakey.pem 2048
$ openssl req -key cakey.pem -new -x509 –days 365 -out cacert.pem
In the dialog fill in the necessary information about your certification authority. In Common name specify EXAMPLE.RU. - Create a KDC key and certificate:
$ openssl genrsa -out kdckey.pem 2048
$ openssl req -new -out kdc.req -key kdckey.pem
In the dialogue fill in the necessary information about your server. In Common name specify kdc. - Set the environment variables. Environment variables are set during the session and are not set for other sessions and are not saved after the session is closed.
export REALM = EXAMPLE.RU - Your domain
export CLIENT = kdc - your server - Download the pkinit_extensions file - http://dms.aladdin-rd.ru/970c5538-afbf-4a26-a7ef-d76550cbc435
The contents of the pkinit_extensions file (it should be placed in the directory where you run the commands from):
[ kdc_cert ] basicConstraints=CA:FALSE # Here are some examples of the usage of nsCertType. If it is omitted keyUsage = nonRepudiation, digitalSignature, keyEncipherment, keyAgreement #Pkinit EKU extendedKeyUsage = 1.3.6.1.5.2.3.5 subjectKeyIdentifier=hash authorityKeyIdentifier=keyid,issuer # Copy subject details issuerAltName=issuer:copy # Add id-pkinit-san (pkinit subjectAlternativeName) subjectAltName=otherName:1.3.6.1.5.2.2;SEQUENCE:kdc_princ_name [kdc_princ_name] realm = EXP:0, GeneralString:${ENV::REALM} principal_name = EXP:1, SEQUENCE:kdc_principal_seq [kdc_principal_seq] name_type = EXP:0, INTEGER:1 name_string = EXP:1, SEQUENCE:kdc_principals [kdc_principals] princ1 = GeneralString:krbtgt princ2 = GeneralString:${ENV::REALM} [ client_cert ] # These extensions are added when 'ca' signs a request. basicConstraints=CA:FALSE keyUsage = digitalSignature, keyEncipherment, keyAgreement extendedKeyUsage = 1.3.6.1.5.2.3.4 subjectKeyIdentifier=hash authorityKeyIdentifier=keyid,issuer subjectAltName=otherName:1.3.6.1.5.2.2;SEQUENCE:princ_name # Copy subject details issuerAltName=issuer:copy [princ_name] realm = EXP:0, GeneralString:${ENV::REALM} principal_name = EXP:1, SEQUENCE:principal_seq [principal_seq] name_type = EXP:0, INTEGER:1 name_string = EXP:1, SEQUENCE:principals [principals] princ1 = GeneralString:${ENV::CLIENT} - Issue a KDC certificate:
$ openssl x509 -req -in kdc.req -CAkey cakey.pem -CA cacert.pem-out kdc.pem -extfile pkinit_extensions -extensions kdc_cert –CAcreateserial –days 365 - Transfer the kdc.pem, kdckey.pem, cacert.pem files to / var / lib / krb5kdc /
- Create a backup copy of the /etc/krb5kdc/kdc.conf file. Edit /etc/krb5kdc/kdc.conf, adding the following entries to the [kdcdefaults] section:
pkinit_identity = FILE: /var/lib/krb5kdc/kdc.pem,/var/lib/krb5kdc/kdckey.pem
pkinit_anchors = FILE: /var/lib/krb5kdc/cacert.pem
The first entry specifies the keys and certificate of the server, and the second indicates the root certificate of the certification authority. - To accept the changes, run:
/etc/init.d/krb5-admin-server restart
/etc/init.d/krb5-kdc restart
Preparing a smart card. Release keys and user certificate
Make sure the libengine-pkcs11-openssl and opensc packages are installed . Connect the device to be prepared.
Initialize the device, set the user PIN. Remember that device initialization will delete all data on the JaCarta PKI permanently.
For initialization, you must use the pkcs11-tool utility.
pkcs11-tool --slot 0 --init-token --so-pin 00000000 --label 'JaCarta PKI' --module /lib64/libASEP11.so,
Where:
--slot 0 - indicates which virtual slot the device is connected to. As a rule, this is slot 0, but there may be other values - 1.2, etc .;
- init-token - token initialization command;
--so-pin 00000000 - JaCarta PKI admin PIN. The default value is 00000000;
--label 'JaCarta PKI' - device label;
--module /lib64/libASEP11.so - specifies the path to the library libASEP11.so. Installed as part of the idprotectclient package, see the section “Installing drivers on the server and client”.
To set the user PIN code, use the command:
pkcs11-tool --slot 0 --init-pin --so-pin 00000000 --login --pin 11111111 --module /lib64/libASEP11.so,
Where:
--slot 0 - indicates which virtual slot the device is connected to. As a rule, this is slot 0, but there may be other values - 1.2, etc .;
- init-pin - command for setting user PIN;
--so-pin 00000000 - JaCarta PKI admin PIN. The default value is 00000000;
--login - login command;
--pin 11111111 - user PIN;
--module /lib64/libASEP11.so - specifies the path to the library libASEP11.so. Installed as part of the idprotectclient package, see the section “Installing drivers on the server and client”.
Generate keys on the device, to do this, enter the following command:
pkcs11-tool --slot 0 --login --pin 11111111 --keypairgen --key-type rsa: 2048 --id 42 --label “test1 key” --module /lib64/libASEP11.so,
Where:
--slot 0 - indicates which virtual slot the device is connected to. As a rule, this is slot 0, but there may be other values - 1.2, etc .;
--login --pin 11111111 - indicates that you should log in as a user with the PIN code "11111111". If your card has a different user PIN, enter it;
--keypairgen --key-type rsa: 2048 - indicates that keys with a length of 2048 bits must be generated;
--id 42 - sets the attribute CKA_ID key. CKA_ID can be any;
Remember this value! It is necessary for the further steps of preparing the device for operation.
--label “test1 key” - sets the attribute CKA_LABEL key. Attribute can be any;
--module /lib64/libASEP11.so - specifies the path to the library libASEP11.so. Installed as part of the idprotectclient package, see the section “Installing drivers on the server and client”.
Generate a certificate request using the openssl utility. To do this, enter the following commands:
#openssl OpenSSL> engine dynamic -pre SO_PATH:/usr/lib/ssl/engines/engine_pkcs11.so -pre ID:pkcs11 -pre LIST_ADD:1 -pre LOAD -pre MODULE_PATH:/lib64/libASEP11.so OpenSSL> req -engine pkcs11 -new -key 0:42 -keyform engine -out client.req -subj "/C=RU/ST=Moscow/L=Moscow/O=Aladdin/OU=dev/CN=test1 (!_!)/emailAddress=test1@mail.com" OpenSSL>quit. Note the -new-key 0:42 , where 0 is the virtual slot number with the device, 42 is the CKA_ID attribute of the keys generated earlier.
The information that must be specified in the request should be set in the field "/ C = RU / ST = Moscow / L = Moscow / O = Aladdin / OU = dev / CN = test1 (! Your_User!) / EmailAddress=test1@mail.com ".
It is necessary to set variable environments
$ export REALM = EXAMPLE.RU # Your Domain
$ export CLIENT = test1 # Your user
and issue a certificate to the user.
$ openssl x509 -CAkey cakey.pem -CA cacert.pem -req -in client.req -extensions client_cert -extfile pkinit_extensions -out client.pem –days 365
Next, recode the received certificate from PEM to DER.
# openssl x509 -in client.pem -out client.cer -inform PEM -outform DER
Record the received certificate on the token.
pkcs11-tool --slot 0 --login --pin 11111111 --write-object client.cer --type 'cert' --label 'Certificate' --id 42 --module /lib/libASEP11.so,
Where:
--slot 0 - indicates which virtual slot the device is connected to. As a rule, this is slot 0, but there may be other values - 1.2, etc .;
--login --pin 11111111 - indicates that you should log in as a user with the PIN code "11111111". If your card has a different user PIN, enter it;
--write-object ./client.cer - indicates that it is necessary to write the object and the path to it;
--type 'cert' - indicates that the type of the recorded object is a certificate;
'cert' --label 'Certificate' - sets the certificate CKA_LABEL attribute. Attribute can be any;
- id 42 - sets the attribute CKA_ID of the certificate. The same CKA_ID must be specified as for keys;
- module /lib64/libASEP11.so - indicates the path to the library libASEP11.so.
Customize the client. Health check
Create the / etc / krb5 / directory on the client. Copy the CA certificate (cacert.pem) from the server to / etc / krb5 / .
Configure kerberos in /etc/krb5.conf. Section [libdefaults] supplement the following lines.
[libdefaults] default_realm = EXAMPLE.RU pkinit_anchors = FILE:/etc/krb5/cacert.pem # pkinit_identities = PKCS11:/lib64/libASEP11.so Perform a check:
kinit When the PIN request line appears on the card, enter it.
To verify that the kerberos ticket was successfully received for a user, enter the klist command. To remove the ticket - kdestroy.
To log in to the domain using a smart card, on the OS login screen, enter the PIN from the smart card instead of the password.
At this setting is over. Yes, unfortunately, the system itself does not change or adjust the login window for the smart card, and it will be standard, but if you make some secret efforts, you can achieve a beautiful result.
Source: https://habr.com/ru/post/337820/
All Articles