Investigation of information leaks from the carrier’s corporate database
We were approached by a large Russian carrier that owns an impressive fleet of vehicles. Its customers include dozens of logistics companies and enterprises. The zone of its activity extends far beyond the borders of the CIS countries. Each car is equipped with a monitoring system that sends data about coordinates, fuel consumption and many other indicators to the control center.
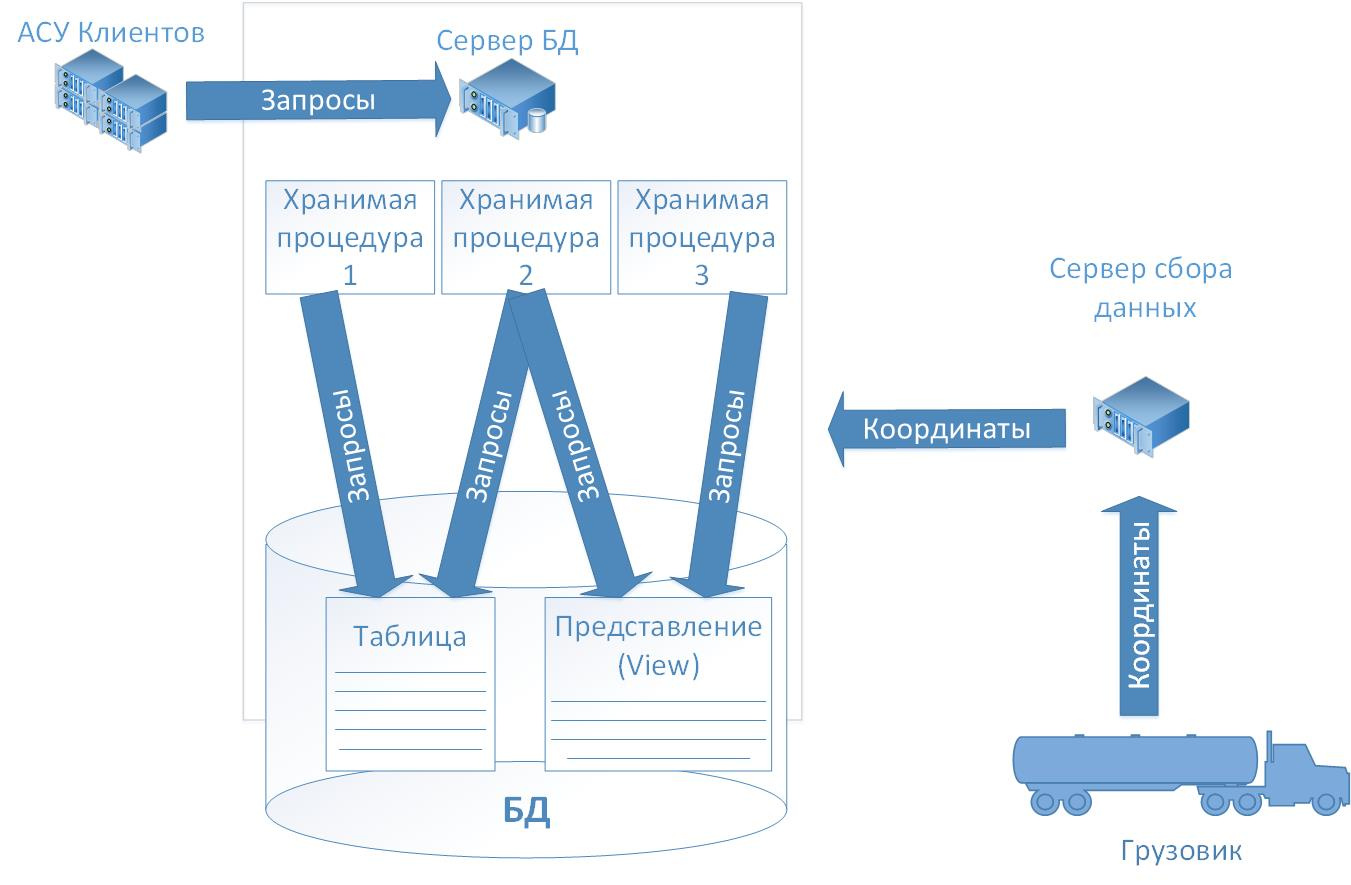
From a single center, information about the coordinates of the goods diverges to customers. Everything works in an automated way. For the convenience of control of delivery, the cost of services included a service to inform customers about the location of their goods.

')
The reason for contacting us was the activity of several online resources that sold information about the carrier’s cargo. It is unlikely that a logistics company or another client of our carrier will be glad to know that anyone, including competitors, can acquire data on his goods.
From a technical point of view, information about your cargo can be obtained in two ways.
The first is on the carrier’s website, the second, more complex, by connecting its logistic information system (customer’s ACS) directly to the carrier’s base. All requests from the client's ACS to the carrier’s database (DB) are implemented through a set of Stored Procedures. To control access to each client, his own account is allocated with a set of necessary powers and rights.
The carrier’s specialists understood that, in addition to data on the location of the cargo, other information may also flow from their database. Who and for what purpose they will use is unknown, but alarming. Presumably the customers of such sites may be not only competitors, but also the clients of the carrier who wish to have an alternative channel of control. Also information on trucks may be interesting to those who managed to unofficially "attach" their cargo in the back, for example, by agreeing with the driver. There is an obvious information leakage, and our task was to find out the method of its organization.
To begin with, we conducted an analysis of the information provided by these sellers of stolen goods. It turned out that the range of their services is quite wide. For quite reasonable money that even a private person can afford, you can get information on the location of a particular truck or cargo at the moment. You can subscribe to the tracking of cargo or vehicle, then you will receive data by e-mail or by SMS with the frequency for which you have enough money.
To continue the investigation, we chose the “test purchase” method. We registered on one of these criminal resources and paid for several dozen requests for the coordinates of the truck. When planning each request, we planned to track the sources of calls to the carrier’s central database.
After reviewing the base structure, we realized that information about the coordinates of a vehicle can be obtained either from the base table or from the view. We chose one of the trucks of the company that was on the flight, asked the database administrators of the control center to enable tracing of calls to the table and views containing data on the coordinates of the truck. Over the next three hours we made 10 requests on the fraudulent website and received GPS coordinates for each request. Data for each request came to us with a delay of no more than a second. During these three hours, about 70 megabytes of text magazines were added. To analyze them, we went to our office, where we had the right tools, leaving the base administrators alone.
During the analysis, we realized that the data in response to our requests came in online mode, and versions about leaks from backup copies, or about processing requests in manual mode, were noted. We were hoping that within a second of our request, the data about the external client that "merges" the information will appear in the trace. The results of the analysis were disappointing - in the trace made by standard DBMS tools there was information on appeals to the table and views, but there was no information about specific requests for data on our truck. It turned out that in a second there are more than two hundred calls to the table and views, and it is not possible to single out the calls made in response to our requests among them.
There is a need for additional tools, which will give us the contents of each specific reference to the table or view. Many tools can analyze SQL queries and the like in traffic, but in our case it was necessary to have software that not only could intercept requests from stored procedures to the database on the same server, but also “parse” their contents.
It’s good that we managed to quickly find such a tool and agree on its temporary use. This solution (InfoSphere Guardium) can analyze requests from stored procedures using the software agent directly on the database server. By analyzing queries on the fly, the system allows us to obtain all the data we need. After the nightly installation and configuration work, we again conducted a series of 10 data requests for our truck on the “left” resource. This time, thanks to the built-in filtering methods of our analytical system, we received a list of 12 accounts to which the data on the coordinates of our truck “flew” within a second after each of our requests. For any of these accounts is the ACS of one of the carrier's customers. The task was to determine which specific ACS transfers data to the side, for which we used the method of setting individual "tags".
Together with the database administrators, we slightly modified those stored procedures, using which the 12 accounts we detected take data from the database. The modification pursued one goal - depending on the account, to make individual adjustments to the coordinates of the truck. For each of the 12 automated control systems, individual coordinates were formed, differing in the last two digits, all values sent by us were carefully stored in a special journal. Having received the "marked" coordinates from the criminal website, we, referring to the log of issuing tags, were able to identify the ACS that merges the data.
Now a rather delicate moment has come - for further investigation, data from the client’s ACS were needed. This meant that the client must be at least partially privy to the heart of the matter. Moreover, if the data is drained by the administrator of this automated control system, he can catch all traces. It was necessary to act very carefully. The circumstances were successful, because An agreement was reached on cooperation at the level of the carrier’s security services and this client, a major logistics operator. The client security service agreed to provide us with the ACS server logs. Log analysis gave us a single account that received data tagged. The account belonged to one of the employees of the logistics company. What happened to him next story is silent. The main thing is that the goal was achieved - the sale of stolen data has stopped.
From a single center, information about the coordinates of the goods diverges to customers. Everything works in an automated way. For the convenience of control of delivery, the cost of services included a service to inform customers about the location of their goods.

')
The reason for contacting us was the activity of several online resources that sold information about the carrier’s cargo. It is unlikely that a logistics company or another client of our carrier will be glad to know that anyone, including competitors, can acquire data on his goods.
From a technical point of view, information about your cargo can be obtained in two ways.
The first is on the carrier’s website, the second, more complex, by connecting its logistic information system (customer’s ACS) directly to the carrier’s base. All requests from the client's ACS to the carrier’s database (DB) are implemented through a set of Stored Procedures. To control access to each client, his own account is allocated with a set of necessary powers and rights.

The carrier’s specialists understood that, in addition to data on the location of the cargo, other information may also flow from their database. Who and for what purpose they will use is unknown, but alarming. Presumably the customers of such sites may be not only competitors, but also the clients of the carrier who wish to have an alternative channel of control. Also information on trucks may be interesting to those who managed to unofficially "attach" their cargo in the back, for example, by agreeing with the driver. There is an obvious information leakage, and our task was to find out the method of its organization.
To begin with, we conducted an analysis of the information provided by these sellers of stolen goods. It turned out that the range of their services is quite wide. For quite reasonable money that even a private person can afford, you can get information on the location of a particular truck or cargo at the moment. You can subscribe to the tracking of cargo or vehicle, then you will receive data by e-mail or by SMS with the frequency for which you have enough money.
To continue the investigation, we chose the “test purchase” method. We registered on one of these criminal resources and paid for several dozen requests for the coordinates of the truck. When planning each request, we planned to track the sources of calls to the carrier’s central database.
After reviewing the base structure, we realized that information about the coordinates of a vehicle can be obtained either from the base table or from the view. We chose one of the trucks of the company that was on the flight, asked the database administrators of the control center to enable tracing of calls to the table and views containing data on the coordinates of the truck. Over the next three hours we made 10 requests on the fraudulent website and received GPS coordinates for each request. Data for each request came to us with a delay of no more than a second. During these three hours, about 70 megabytes of text magazines were added. To analyze them, we went to our office, where we had the right tools, leaving the base administrators alone.
During the analysis, we realized that the data in response to our requests came in online mode, and versions about leaks from backup copies, or about processing requests in manual mode, were noted. We were hoping that within a second of our request, the data about the external client that "merges" the information will appear in the trace. The results of the analysis were disappointing - in the trace made by standard DBMS tools there was information on appeals to the table and views, but there was no information about specific requests for data on our truck. It turned out that in a second there are more than two hundred calls to the table and views, and it is not possible to single out the calls made in response to our requests among them.
There is a need for additional tools, which will give us the contents of each specific reference to the table or view. Many tools can analyze SQL queries and the like in traffic, but in our case it was necessary to have software that not only could intercept requests from stored procedures to the database on the same server, but also “parse” their contents.
It’s good that we managed to quickly find such a tool and agree on its temporary use. This solution (InfoSphere Guardium) can analyze requests from stored procedures using the software agent directly on the database server. By analyzing queries on the fly, the system allows us to obtain all the data we need. After the nightly installation and configuration work, we again conducted a series of 10 data requests for our truck on the “left” resource. This time, thanks to the built-in filtering methods of our analytical system, we received a list of 12 accounts to which the data on the coordinates of our truck “flew” within a second after each of our requests. For any of these accounts is the ACS of one of the carrier's customers. The task was to determine which specific ACS transfers data to the side, for which we used the method of setting individual "tags".
Together with the database administrators, we slightly modified those stored procedures, using which the 12 accounts we detected take data from the database. The modification pursued one goal - depending on the account, to make individual adjustments to the coordinates of the truck. For each of the 12 automated control systems, individual coordinates were formed, differing in the last two digits, all values sent by us were carefully stored in a special journal. Having received the "marked" coordinates from the criminal website, we, referring to the log of issuing tags, were able to identify the ACS that merges the data.
Now a rather delicate moment has come - for further investigation, data from the client’s ACS were needed. This meant that the client must be at least partially privy to the heart of the matter. Moreover, if the data is drained by the administrator of this automated control system, he can catch all traces. It was necessary to act very carefully. The circumstances were successful, because An agreement was reached on cooperation at the level of the carrier’s security services and this client, a major logistics operator. The client security service agreed to provide us with the ACS server logs. Log analysis gave us a single account that received data tagged. The account belonged to one of the employees of the logistics company. What happened to him next story is silent. The main thing is that the goal was achieved - the sale of stolen data has stopped.
Source: https://habr.com/ru/post/337804/
All Articles