New Apache Struts web server vulnerability allows remote code execution

A security bug was detected in the Apache Struts web server that allowed unauthenticated attackers to execute arbitrary code on a vulnerable system.
The Apache Software Foundation assigned the vulnerability to a medium severity level, but Cisco said in its security bulletin that many of its products were affected by the error.
')
What is the problem
The vulnerability is contained in the Freemarker functionality of the Apache Struts 2 package. Freemarker Template Language is a popular template language used in Apache Struts and many Java-based projects. With it, developers can "bandage" the values of parameters passed to the server by the user application, with the internal declared variables of the application.
Incorrect operation of the mechanism allows attackers to send Object Graph Navigation Language (OGNL) expressions to the server, processing of which can lead to the execution of arbitrary code on it.
At the moment, the fact of presence of vulnerability in several Cisco products is precisely confirmed:
- Cisco Digital Media Manager - the patch for it will not be released, since the product support was officially discontinued on August 19, 2016;
- Cisco Hosted Collaboration Solution for Contact Center;
- Cisco Unified Contact Center Enterprise;
- Cisco Unified Intelligent Contact Management Enterprise.
Under suspicion of a vulnerability, there are still more than 20 products of the company - about whether they found security problems can be found in the security bulletin update .
Not only Cisco: hacking Equifax
In addition to the CVE-2017-12611 vulnerability (S2-053), several similar security errors have already been found in Apache Struts, including CVE-2017-9805 (S2-052), CVE-2017-9791 (S2-048) and CVE-2017-5638 (S2-045). The media reported that a loud leak of customer data from one of the US credit bureaus Equifax was the result of a vulnerability in Apache Struts.
According to Positive Technologies expert Lee-Ann Galloway, such attacks can be carried out in order to steal credit card data or use information from people with a good credit history to defraud banks and get loans. At the same time there is no information about what kind of security error led to the problem.
In addition, a vulnerability was later discovered on the Equifax website for credit monitoring - with its help, attackers could steal data from resource users.
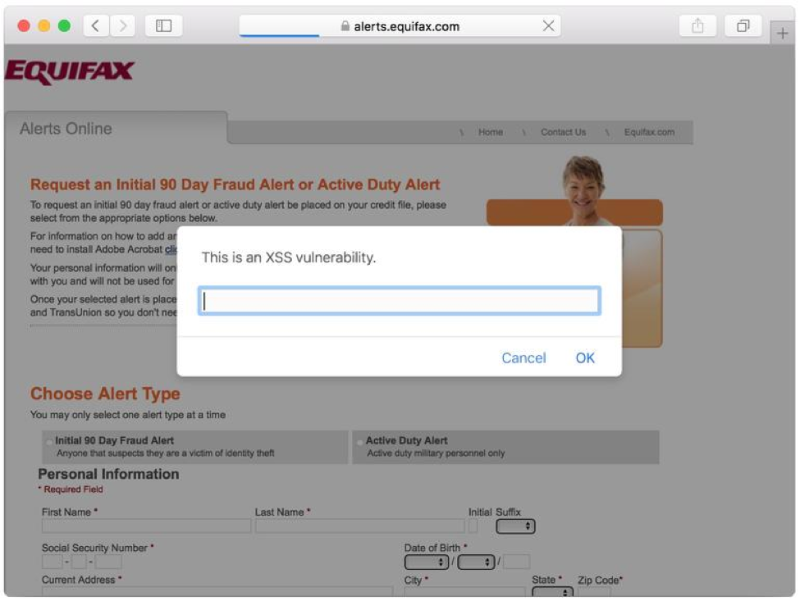
XSS on Equifax site, image: ZDNet
In the wake of the Equifax hacking story, the Apache Struts development team released a statement in which it recommended all users of its web server not to rely on the absence of vulnerabilities in it, but to use specialized tools to ensure the security of the infrastructure. One of the tools to prevent attacks using such vulnerabilities is WAF (we are developing our own application-level firewall, PT Application Firewall ).
How to protect
Although CVE-2017-12611 is vulnerable to a number of Cisco products, its consequences will not be large-scale, since the specific configuration of the attacked application is necessary for operation. If developers do not use Freemarker pattern language constructs or use only read-only entities to initialize attributes, then the error cannot be exploited.
In addition, experts at Positive Technologies recommend that application developers install Apache Struts versions 2.5.12 or 2.3.34, which contain a more customized Freemarker configuration. It will also help reduce the risks of a successful attack.
Source: https://habr.com/ru/post/337760/
All Articles