Data masking as a tool to minimize labor costs at the stage of putting new information systems into operation
Many organizations of various fields of activity, such as energy, transport, retail, communications, fuel and energy complex, banks, financial institutions, nuclear, mining, metallurgical industry and companies from other industries, face the necessity of putting into operation simultaneously a large number of new information systems, including development and testing.
The commissioning of each new information system - corporate applications, IT tools, information security solutions, various developed applications, is always accompanied by the process of forming test environments and filling them with test data. To do this, companies have to replicate databases to support the systems testing process.
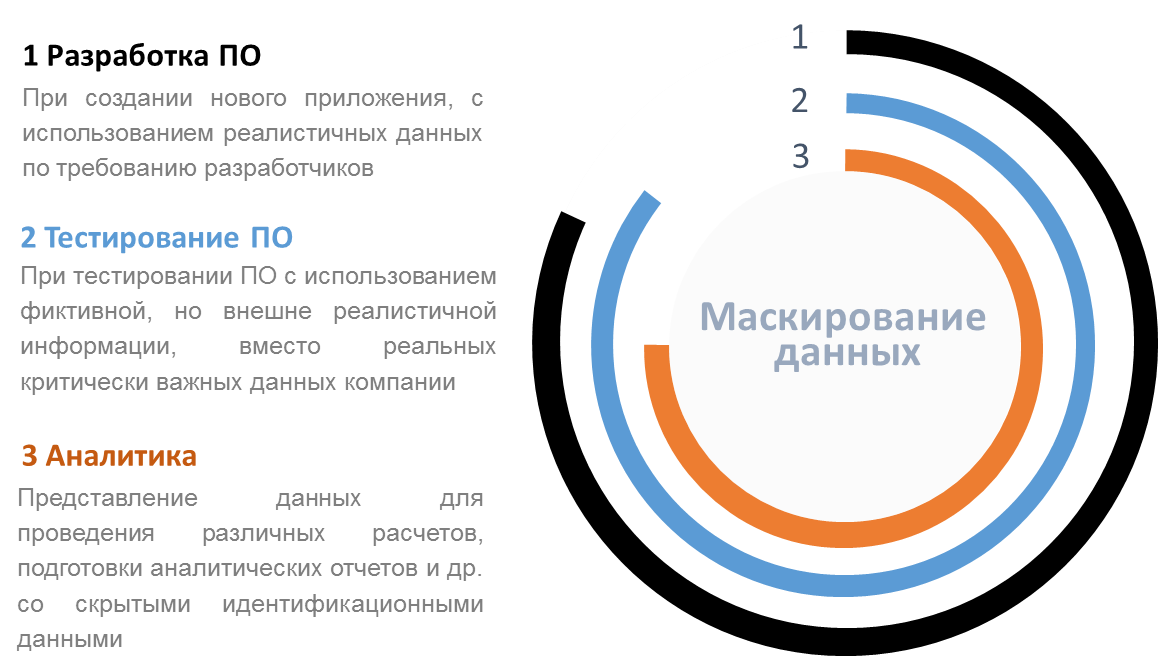
For clarity, we denote the key stages of the project for the implementation of the information system, where the use of test data may be necessary (Fig. 1).
')

Pic1
The testing phase of the implemented information systems includes :
• preparation of test environments;
• data entry;
• verification of the performance of the system being implemented, verification and validation of the software being developed;
• correction of detected errors.
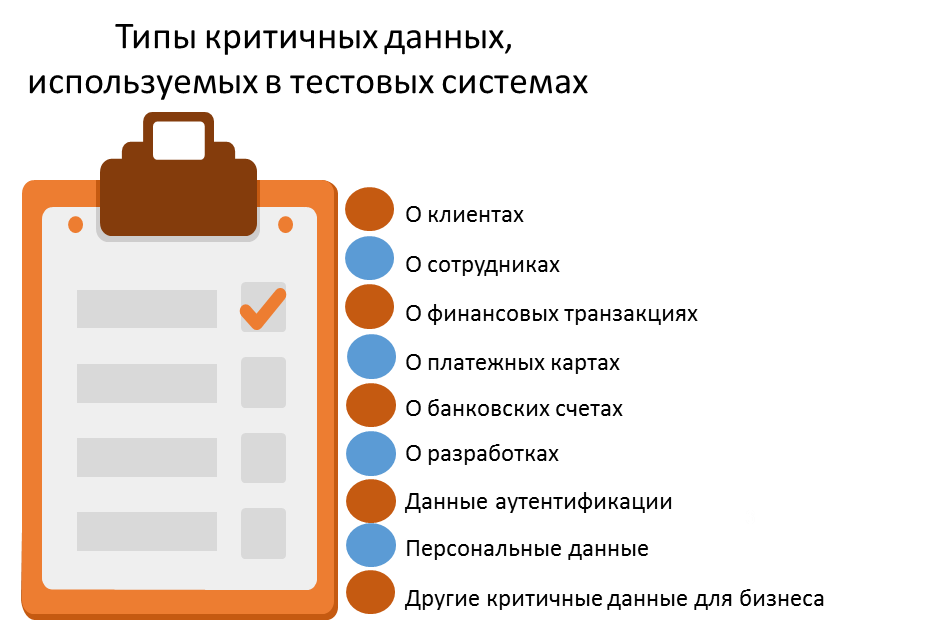
At these stages, companies are faced with organizational issues for obtaining test data for carrying out work on the implementation of information systems by both internal forces and the forces of contracted organizations. The main problem is that copies of working data often contain information that is critical for a company (Fig. 2), which often leads to internal conflicts between the owners of these data and the persons who need them for testing, as well as the need to comply with the requirements of internal and external standards. The process of coordinating the issuance of data by their owners and the appointment of responsible persons for the testing process takes an indefinite time, you have to wait much more than the planned time within the project. All this delays the launching of systems into operation and, accordingly, can lead to monetary and reputational losses.
Pic2
In the process of introducing a new solution into commercial operation, own employees of the organization, temporary workers, trainees and employees of outsourcing companies / partners can take part. For example, developers, programmers, analysts, testers, database administrators, as well as employees of departments controlling the process (Fig. 3).

Pic.3
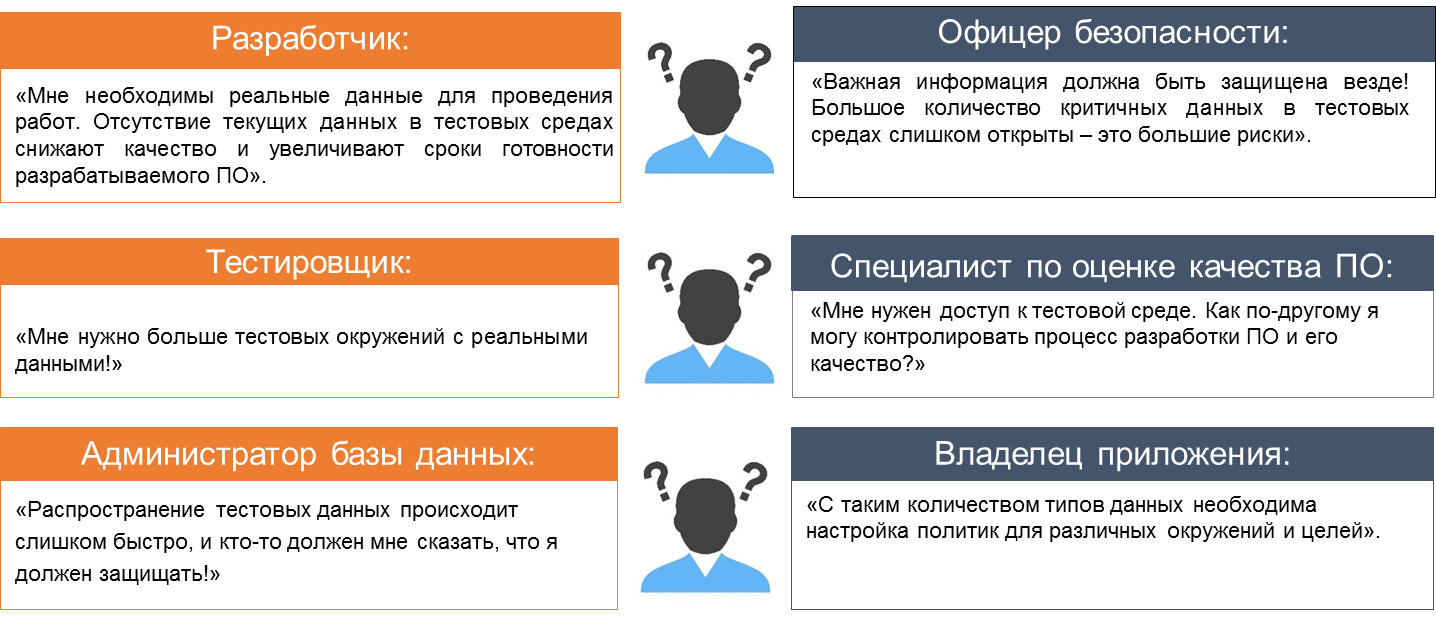
From participating in this process comes a huge number of requests / questions, such as (Fig. 4):
Pic.4
You can also highlight the following problems when working with test data :
• unauthorized access to data of a large number of people without proper authority;
• lack of security policies and data protection tools in test environments and development environments;
• lack of a process to control the transfer of critical data to third-party companies (external developers, testers / partners);
• the ability to use the information received from test systems to organize attacks on the productive system;
• the process of manual or semi-automatic anonymization of data is laborious and error prone;
• The process of manual or semi-automatic truncation of the database for testing is laborious and error prone.
To eliminate such problems and speed up the process of gaining access to test data, as well as protecting information from external and internal threats arising in test environments, the use of data masking tools can help.
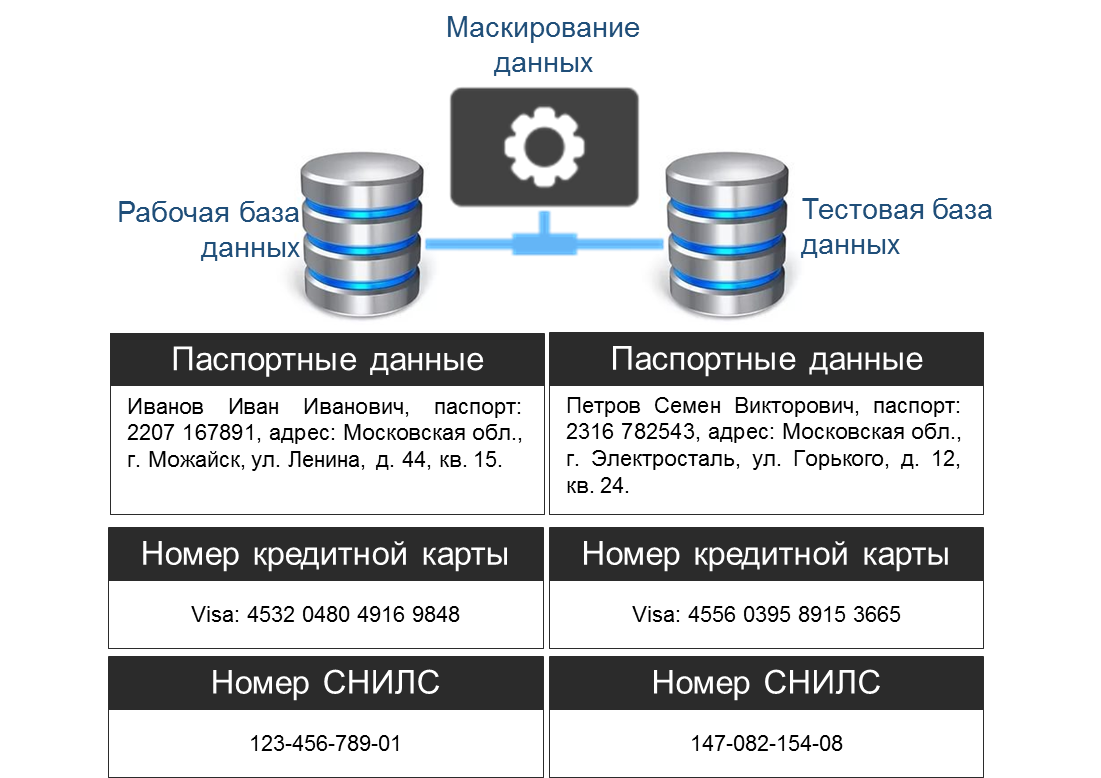
Data masking is a technology that helps prevent the inappropriate use of critical data by providing users with incorrect / dummy data, but looking plausible (hereinafter - realistic), instead of real data. Let us give an illustrative example of what masked data might look like (Fig. 5).
Pic.5
There are several types of data masking :
• static masking - used to protect data stored in test environments;
• dynamic masking - provides for the substitution of critical data in real time when accessing the production database. Real data does not leave the database; they are replaced at the request stage, for example, with completely realistic, without intermediate recording.
In this article we will consider the use of the method of static masking, its advantages and describe the problems that arise when testing software without using it.
Static masking is an irreversible process of replacing critical data with realistic, based on predefined rules, in which data is transformed in one direction and original data cannot be obtained, extracted or restored, unlike encryption and tokenization, which allow you to reverse the data conversion process , thereby increasing the risk of leakage of critical information.
The process of static data masking by specialized tools is as follows :
• creating a copy of the production database by employees with appropriate access rights;
• a reduction in the amount of information contained in the database according to the set rules (if necessary);
• search for critical data in a copy of the database based on the specified search patterns;
• masking of the found critical data according to customized patterns and rules;
• providing a masked copy of the database to developers / testers.
Static masking is used for analytics, training courses, with the need to use realistic data, software development and application testing (Figure 6.).
Pic.6
The use of static data masking tools can help enterprises in reducing the risks of losing critical data, protecting them, and meeting the requirements of external and internal regulators and information security standards (for example, PCI DSS, FZ-152). The use of static data masking technology ensures that critical data does not fall into non-production environments (development, testing environments), while the possibility of using this protected data to the necessary extent by company employees or involved contracting organizations.
Static data masking solutions allow you to quickly provide protected copies in the right quantity with realistic data for transmission to test environments in accordance with established safety rules. Thereby increasing the efficiency of database administrators in the preparation of test environments, as well as in addition, depending on the specific solution for static masking, reducing the amount of stored data by correctly cutting back on databases, if necessary.
Putting new solutions into operation and testing them, as well as developing applications and creating reports using the static data masking solution, takes much less time: programmers, engineers, testers, developers can quickly deploy new test environments and conduct test runs.
Due to this, projects are executed on time, without attracting a large number of participants, including resolving issues related to issuing data access rights, which allows companies to minimize labor costs when a new information system is put into operation, improves administrator productivity, eliminates manual processes and helps apply information security policies, thereby reducing the likelihood of loss of critical data in non-production environments.
Author: Yana Shevchenko, Manager, Promotion Department, Informzaschita, y.shevchenko@infosec.ru
The commissioning of each new information system - corporate applications, IT tools, information security solutions, various developed applications, is always accompanied by the process of forming test environments and filling them with test data. To do this, companies have to replicate databases to support the systems testing process.
For clarity, we denote the key stages of the project for the implementation of the information system, where the use of test data may be necessary (Fig. 1).
')

Pic1
The testing phase of the implemented information systems includes :
• preparation of test environments;
• data entry;
• verification of the performance of the system being implemented, verification and validation of the software being developed;
• correction of detected errors.
At these stages, companies are faced with organizational issues for obtaining test data for carrying out work on the implementation of information systems by both internal forces and the forces of contracted organizations. The main problem is that copies of working data often contain information that is critical for a company (Fig. 2), which often leads to internal conflicts between the owners of these data and the persons who need them for testing, as well as the need to comply with the requirements of internal and external standards. The process of coordinating the issuance of data by their owners and the appointment of responsible persons for the testing process takes an indefinite time, you have to wait much more than the planned time within the project. All this delays the launching of systems into operation and, accordingly, can lead to monetary and reputational losses.

Pic2
In the process of introducing a new solution into commercial operation, own employees of the organization, temporary workers, trainees and employees of outsourcing companies / partners can take part. For example, developers, programmers, analysts, testers, database administrators, as well as employees of departments controlling the process (Fig. 3).

Pic.3
From participating in this process comes a huge number of requests / questions, such as (Fig. 4):

Pic.4
You can also highlight the following problems when working with test data :
• unauthorized access to data of a large number of people without proper authority;
• lack of security policies and data protection tools in test environments and development environments;
• lack of a process to control the transfer of critical data to third-party companies (external developers, testers / partners);
• the ability to use the information received from test systems to organize attacks on the productive system;
• the process of manual or semi-automatic anonymization of data is laborious and error prone;
• The process of manual or semi-automatic truncation of the database for testing is laborious and error prone.
To eliminate such problems and speed up the process of gaining access to test data, as well as protecting information from external and internal threats arising in test environments, the use of data masking tools can help.
Data masking is a technology that helps prevent the inappropriate use of critical data by providing users with incorrect / dummy data, but looking plausible (hereinafter - realistic), instead of real data. Let us give an illustrative example of what masked data might look like (Fig. 5).

Pic.5
There are several types of data masking :
• static masking - used to protect data stored in test environments;
• dynamic masking - provides for the substitution of critical data in real time when accessing the production database. Real data does not leave the database; they are replaced at the request stage, for example, with completely realistic, without intermediate recording.
In this article we will consider the use of the method of static masking, its advantages and describe the problems that arise when testing software without using it.
Static masking is an irreversible process of replacing critical data with realistic, based on predefined rules, in which data is transformed in one direction and original data cannot be obtained, extracted or restored, unlike encryption and tokenization, which allow you to reverse the data conversion process , thereby increasing the risk of leakage of critical information.
The process of static data masking by specialized tools is as follows :
• creating a copy of the production database by employees with appropriate access rights;
• a reduction in the amount of information contained in the database according to the set rules (if necessary);
• search for critical data in a copy of the database based on the specified search patterns;
• masking of the found critical data according to customized patterns and rules;
• providing a masked copy of the database to developers / testers.
Static masking is used for analytics, training courses, with the need to use realistic data, software development and application testing (Figure 6.).

Pic.6
The use of static data masking tools can help enterprises in reducing the risks of losing critical data, protecting them, and meeting the requirements of external and internal regulators and information security standards (for example, PCI DSS, FZ-152). The use of static data masking technology ensures that critical data does not fall into non-production environments (development, testing environments), while the possibility of using this protected data to the necessary extent by company employees or involved contracting organizations.
Static data masking solutions allow you to quickly provide protected copies in the right quantity with realistic data for transmission to test environments in accordance with established safety rules. Thereby increasing the efficiency of database administrators in the preparation of test environments, as well as in addition, depending on the specific solution for static masking, reducing the amount of stored data by correctly cutting back on databases, if necessary.
Putting new solutions into operation and testing them, as well as developing applications and creating reports using the static data masking solution, takes much less time: programmers, engineers, testers, developers can quickly deploy new test environments and conduct test runs.
Due to this, projects are executed on time, without attracting a large number of participants, including resolving issues related to issuing data access rights, which allows companies to minimize labor costs when a new information system is put into operation, improves administrator productivity, eliminates manual processes and helps apply information security policies, thereby reducing the likelihood of loss of critical data in non-production environments.
Author: Yana Shevchenko, Manager, Promotion Department, Informzaschita, y.shevchenko@infosec.ru
Source: https://habr.com/ru/post/337446/
All Articles