Cybersecurity: Flipping through Cisco's annual report
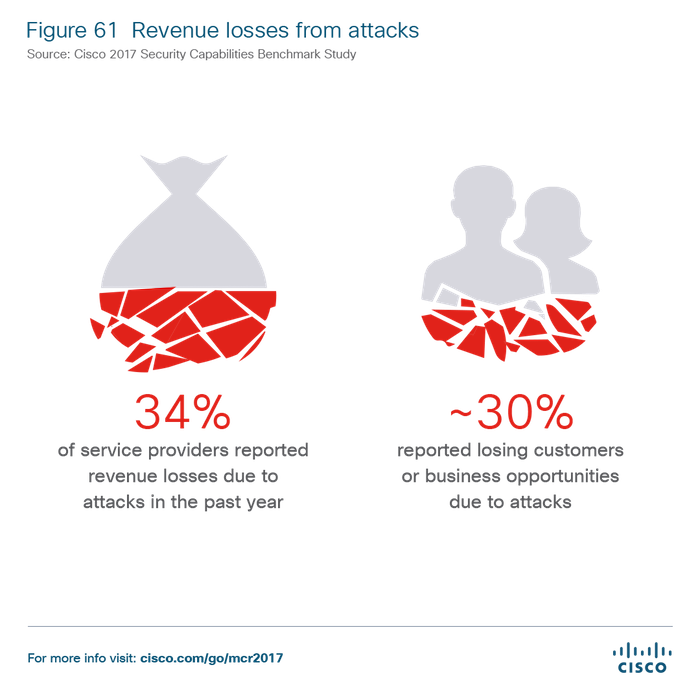
In pursuit of our article on telephone fraud and methods of protection against it, we share the calculations on the topic of cybersecurity in general from Cisco. Under the cut - the main findings of the study Cisco 2017 Midyear Cybersecurity Report .
The Cisco report includes many global findings, but they are all united by one fact: the world of cyber attacks is complex and changeable. As new attack strategies emerge, new defense strategies emerge in response to them, covering “unlocked doors”. And this, in turn, gives life to developing new or refining old attack strategies that pose a real threat to any business and its potential profits.
Weak security tools and the inflexibility of large corporation-level businesses leave huge holes in the protection of the network as a whole. However, this does not mean that IT departments need to change strategy every year. Rather, you should follow the trends and be aware of which threats are the most dangerous at the moment. At the same time, we should not forget about the traditional threats, because history really tends to repeat itself.
How the world of cyber attacks is changing: the main findings of the study
- “Particularly profitable” direction for attacks today is BEC (Business Email Compromise), a fraud carried out as part of corporate correspondence. The report of the Internet Crime Complaint Center shows that from October 2013 to December 2016, 5.3 billion dollars were stolen due to this. For comparison, viral spam schemes demanding ransom in 2016 “earned” $ 1 billion.
- The Internet of Things (IoT) promises a great future for team collaboration technologies. But it also carries great risks. One of the problems is insufficient visibility: “protection” simply does not control which IoT devices are connected to the network. And she needs to quickly deal with this and other issues to the safety of IoT. Hackers are already using thin spots in technology: IoT devices serve as excellent reference points for them to easily and relatively easily navigate networks.
- There has been an increase in email spam since mid-2016, which seems to correlate with a significant decrease in the frequency of using exploit whales (tools aimed at exploiting system vulnerabilities) over the same period of time. Hackers specializing in vulnerabilities have resorted to traditional spam again. The same category includes the method when a malicious attachment is attached to a mail message, which is dangerous for the user's isolated programs and applications. Infection of the system occurs with the involvement of the user in the interaction.
- Spyware, masquerading when installed under potentially unwanted programs (PUA, Potentially Unwanted Applications), is a real virus and a threat to user and corporate data, but it is almost not paid attention to. Thus, the study revealed that three spyware applications from the control group were installed in 20% of the 300 companies in the sample.
- During the period of Cisco's observations of the average attack detection time from November 2015, there have been significant improvements - from 39 hours it fell to 3.5 hours (as of May 2017).
- Supply chain attacks allow fraudsters to spread the virus to many companies via a single infected site. In one of the cases investigated, the software vendor’s web page for software downloads was infected — in this way, the virus got into any company that acquired and downloaded software from this vendor.
- The frequency of cyber attacks, their level of complexity and scale have increased significantly over the past year. Hackers find it easier to find access to resources whose developers do not invest too much in security.
- The need to protect cloud services in terms of their potential danger to business has been underestimated. Open authorization and flaws in managing privileged accounts create security holes that attackers can easily exploit. Hackers are already methodically working on hacking corporate cloud networks.
- The use of exploit whales has fallen significantly - the development of tools has stagnated since Angler and other technology leaders have disappeared or changed their business model. The situation is most likely temporary, given the history of the development of this direction. But factors such as, for example, the complication of exploiting Adobe Flash vulnerabilities, can slow down the return of activity to the previous level.
- DevOps services, deployed incorrectly or intentionally left open for usability, carry significant threats to companies. In fact, many of these service copies are already infected.
All of these findings highlight changes in the world of cybersecurity — the main damage is caused by new methods of attack, which are gaining popularity, including BEC. At the same time, the growth of cloud and other technologies from the category of IoT opens up completely new directions. Although hackers continue to use traditional methods, while companies forget that they still need to defend themselves against them - this is especially true for email-spam.
At the same time, Cisco noted that protection practices have improved significantly lately. For example, automatic updates have become the standard for the functioning of modern systems - even mobile versions. It may annoy us that Microsoft forces us to upgrade to Windows 10, or that Apple tirelessly reminds us of the need to install the latest version of iOS, but this is all for our own safety. With so fast updates, cybercriminals simply shift the focus back to email and virus technology. And they can be considered habitual traditional threats, although the methods of their application are modified.
Old is facing new
Old techniques are combined with new attack formats. The modern way of extorting money for disabling virus programs is based on a long-known technique: packaging malicious files into email messages. He is flavored with the hope that someone will simply download and open them, without thinking twice, whether it is worth it.
Researchers from Cisco note that the growth in spam has been correlated with a decline in activity of hackers using exploit whales to launch attacks. As a rule, such a policy was convenient for penetration through the already known security holes.
For example, the popular Flash player for sites was well-known for its security jambs, and now mainstream web browsers have limited its use for this very reason. Constant updates and reduction in the prevalence of Flash technology has made it a less popular tool for gaining access to user resources among hackers. Instead, they turned to email.
Having done the simplest homework in “social intelligence”, the fraudsters are trying to ensure that the victim opens the Vordovskiy document without suspicion, allegedly from his best friend and gives access to his entire system.

A Cisco report also warns that spam is not the only way to use phishing scams. Disguising corporate correspondence fraud (BEC) is an even bigger headache than using ransom-oriented viral attachments.
Fraud under the guise of corporate correspondence (BEC)
The BEC campaign is carried out using email messages sent to the company's employees responsible for financial calculations. As a rule, fraudsters conduct preliminary training and study the company's hierarchy - for example, they use social networks to build a potential management chain. A scam letter instructing a remittance to a prospective business partner or paying the seller may look like a message from the CEO or from another top manager.
Of course, all this requires careful efforts and preparation, and the fraudster often models the situation of urgency so that the victim does not have time to double-check the information. According to a Cisco report, the targets of such attacks are most often large targets - such as Google or Facebook - and they are really vulnerable in this sense, despite the development of sufficiently mature protection strategies, including against this type of fraud. Although the most successful are attacks on the SMB segment, since such companies, as a rule, do not formalize the communication processes between employees.

Cisco also notes that because fraudulent emails use true social information, they do not contain any suspicious attachments. And so it is easy to bypass the standard protection barriers. And, on average, they create $ 1.7 billion in losses for businesses annually.
New technologies - new threats
E-mail - this is really the grandfather of modern technology. And even if there are still opportunities for successful attacks, then there is every chance that hackers will also be successful in the case of the latest technologies. Unless the attitude to the security problem as a whole changes.
For example, the emerging technologies IoT already contain a traditional flaw: the developers are thinking about protection last. Most of the IoT services just leave the front door unlocked, and although I literally just entered the market, the IoT-based botnets are right there. In 2016, a significant part of cyber attacks was accomplished through integrated devices turned into botnets.
Such DDoS attacks use an army of unified IoT devices (similar to a network of infected computers) to overload and collapse corporate networks. In its report, Cisco analyzes in detail the activities of the three most famous botnets: Mirai, BrickerBot, and Hajime.

Similarly with cloud technology. A Cisco report shows that 60% of users never log out of cloud service interfaces. This does not matter, but for hackers it is downright neon sign "Welcome" and the possibility of unauthorized access to services.
')
Source: https://habr.com/ru/post/337442/
All Articles