"Siege affairs": How companies build a solid fortress to protect the clouds
In the Middle Ages, castles and fortresses were erected by feudal lords to protect themselves and the people from all sorts of interventions and encroachments. Moreover, it was a generally accepted and expedient method of protection that existed from ancient antiquity to the last century. In the digital age, humanity has ceased to build majestic walls of stone - instead, we are building slightly different defenses. Today, companies are trying to strengthen business-critical systems and cloud infrastructures to protect stored data.
At the beginning of 2016, the Cloud Security Alliance conducted a study and identified 12 major threats faced by companies using clouds. Among them, there is ineffective access control to information, data loss, unsafe interfaces, etc. In today's article we decided to tell what the companies should pay attention to “close up the gaps” in the walls of the “cloud fortress”.

/ wikimedia / Siege of the castle of Mortagne-sur-Gironde / PD
')
In 1648, during the Turkish-Venetian war , the siege of Kandia began in Crete. The Kandia garrison, commanded by Francesco Morosini, successfully repelled the attacks of Turkish soldiers and artillery thanks to the support of the fleet, which supplied provisions and reinforcements, and also defended the inhabitants from attack from the water. Because of this kind of “separation of duties”, the city resisted for a long time - the siege lasted 21 years and went down in history as the longest.
In order for the “cloud fortress” to also stand for long years (much longer than Candia), it is important for companies to share protection responsibilities with the cloud provider. The latter removes some of the concerns and responsibility from the organizations. In order to understand what “trouble” the provider protects you from, it is worth exploring the Service Level Agreement (SLA) in detail. So you will understand which gate is securely fastened, and which gates will have to be further strengthened.
The cloud provider can monitor the operation of the infrastructure: data storage systems, computing resources and databases. It can also work with a network: protect from DDoS attacks and spoofing, be responsible for segmentation and perimeter defense. The user, in turn, can control access, updates and monitor security systems. He is also responsible for the components of the hosted application.
Understanding your role and the role of the provider will allow you to better choose a solution for the organization of cloud infrastructure. Moreover, the SLA prescribes the compensation that the provider pays for the breakdown of the services. For example, if the availability indicator does not match: in 1cloud it is equal to 99.9%. Our clients get all the money back if availability falls to 76.98%.
However, when choosing an ally to pay attention only to the "percent" should not be. It is also necessary to consider how the provider is ready to solve the difficulties. For example, we at the company 1cloud offer daily backups to protect user data from damage. Copying is performed to a remote disk array, so the information is restored, even if the server's file system is unavailable.
In addition to studying the SLA, attention should also be paid to access control policies. To do this, it is necessary to determine what is included in the assets of the company and to list the duties necessary to apply to them. It will not be superfluous to develop a plan for the standardization of resources and conduct a study on the presence of vulnerabilities, at the same time classifying risks.
In order to control access to data, experts advise to centralize authentication — this makes it easier to track calls to the system and monitor gaps.
By the way about authentication. Two-factor authentication (2FA) is an additional level of protection against attacks from the outside, which uses another identifier - the token. Today 2FA offers many companies: technical, financial, research, etc. The function of two-factor authentication is used by all major services and social networks - Facebook, Gmail, Twitter, LinkedIn, etc. Last year 2FA introduced Instagram.
Smartphones can act as a token with a code, because today every third inhabitant of the planet has them. One-time password is generated using a special application (Google Authenticator or other specialized) or comes in the form of SMS. The latter option is the most simple and user friendly.
It is this implementation variant 2FA that we use to protect the personal account of clients. To enter the control panel after enabling two-factor authentication, the user must enter the code received via SMS, in addition to the standard email address and password.
“2FA helps protect against a fairly large attack vector,” says Jim Fenton, director of security for OneID, who is developing a unified identity system. “To bypass two-factor authentication, attackers will have to steal your fingerprints or gain access to cookies or codes generated by tokens.”
In fact, 2FA is the second line of defense - a grille on the gate or a moat withcrocodiles with water. It is possible to cross the ditch and safely [without wetting the horses' hoofs] into the castle only when the drawbridge is lowered. Enemies, attacking the castle, soaked in water. Ditches impeded access to the walls of the siege weapons — the rams and siege towers — and prevented the digging.
Both two-factor authentication and the moat are not impenetrable for attackers, but they seriously complicate their lives.
In 1521, Hernan Cortes (Fernando Cortes), a Spanish conquistador, began the siege of the Aztec city of Tenochtitlan. The army of Cortes consisted of 200 thousand people. There were one and a half times more defenders. The Spaniards quickly realized that they couldn’t succeed in taking the city without reason, so they decided to destroy the water supply. This has led to problems with drinking water in the city and outbreaks of the epidemic behind the walls. As a result, the Spaniards looted the city, destroying all the buildings, and in its place a new one was erected - Mexico City.
In cloudy architectures, networks like plumbing systems in castles play a big role. Users manage data centers with a varying number of virtual machines, in which distributed services also operate, allowing them to adhere to the DevOps methodology.
In this case, the network assumes all communications, being a kind of “nervous system” of applications. If an attacker manages to access it, he is given the opportunity to change information, download malware, and steal identity data.
If a cloud account is hacked, a third party will be able to use it to access the systems and, for example, damage the company's reputation. Cloud Security Alliance reports that in 2009, many Amazon systems were hacked and used in the work of the Zeus botnet. According to some reports, in the past, these sites were used to send malicious software to NASA and Bank of America.
Therefore, the network needs attention. For a better understanding of the processes taking place, you should monitor its activity. The cloud provider provides certain resources for this. For example, 1cloud clients can monitor the load on the communication channels in the control panel.
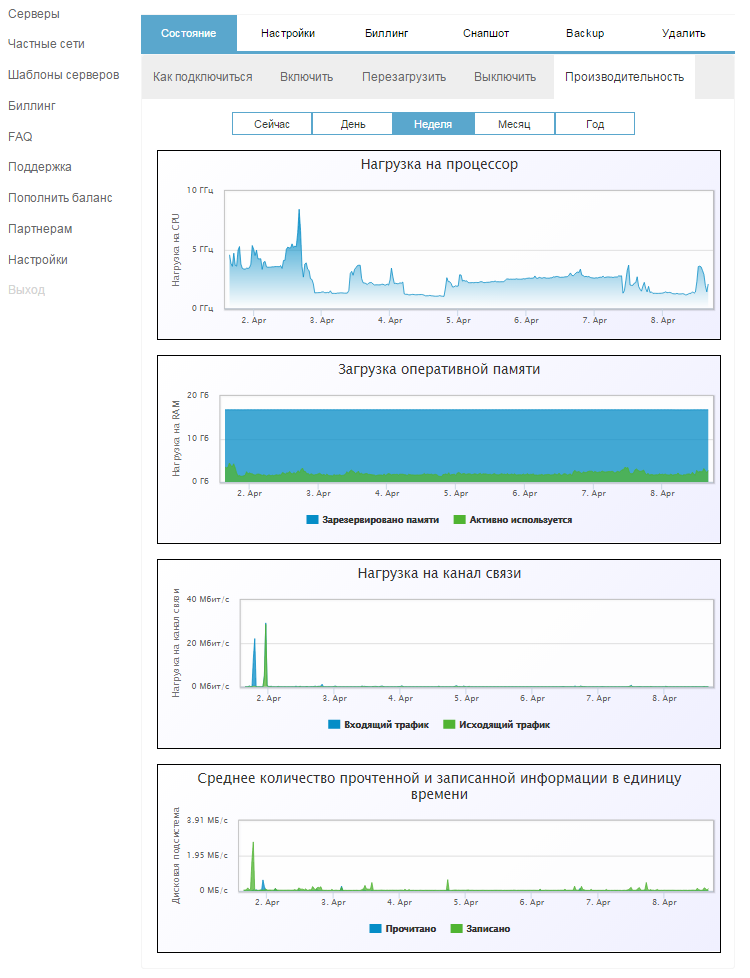
Communication load monitoring window (and not only)
In addition, you should think about the organization of private networks. This is useful for business security. Not all traffic can be “run” over the Internet, plus not all servers should have access there. Additionally, such networks increase application performance and speed. The speed of public connections varies from 10 to 100 Mbps, while the width of a private channel is several times larger - at 1cloud it is 10 Gbps.
Log management is also an effective way to ensure security. Knowing what is happening in the system, it is easier to investigate incidents and find "malware". Known situations where the analysis of logs allowed to track intruders.
Here is an example of an investigation related to the cleaning of iCloud accounts with employees of an unnamed company. IT service was tasked with checking the OWA server logs: there were no suspicious activity on the affected accounts. Administrators found a clue - they were accessed from several unusual IP addresses. Having sorted out events and logs, it was possible to establish the scheme of the attacker's work and close several security holes.
In addition to analyzing the logs, it is worthwhile to constantly stay abreast of developments on existing and emerging vulnerabilities in order to choose an advising strategy. There is also a historical analogy for this - the siege of Kumamoto Castle.

/ wikimedia / Siege of Kumamoto Castle / PD
Saigo Takamori, who led the Satsuma army, attempted a decisive assault on the fortress. The fighting continued until late at night. However, the Satsuma army could not take the castle. After two days of fruitless battles, Satsuma's forces established an environment of fortifications around Kumamoto and laid siege to the stronghold.
However, Kumamoto Castle, built in 1598, was one of the strongest fortresses in Japan. In order to inflict tangible damage on the castle, the attackers had to place their artillery at positions close to the castle, which opened them for return fire from the walls. This advantage was used by its advocates who were in the minority. The rebel weapons were powerless against the tactics of the Kumamoto garrison. Thanks to the knowledge of vulnerabilities and the competent use of tactical advantages, the garrison of the fortress withstood the onslaught of the enemy.
Therefore, it is important to know what weaknesses there are in your castle in order to respond to them accordingly. Public resources help users learn about emerging vulnerabilities in software and other systems, in which participants share their exploits. Here are some of them: Seclists , SecurityFocus , Exploit Database , Security Bloggers Network . There are also Russian-speaking resources: SecurityLab , xakep and the corresponding section on Habré.
With the growing number of cybercrimes (the damage from global cybercrime in 2016 approached 600 billion), companies need to take care of the security of the cloud environment. To do this, pay attention to the following things:
These approaches can improve the security of the system, but it is important to remember about care and caution - without constant training [on their own and others' mistakes] protective measures may not work.
PS What else do we write in our blog:
At the beginning of 2016, the Cloud Security Alliance conducted a study and identified 12 major threats faced by companies using clouds. Among them, there is ineffective access control to information, data loss, unsafe interfaces, etc. In today's article we decided to tell what the companies should pay attention to “close up the gaps” in the walls of the “cloud fortress”.

/ wikimedia / Siege of the castle of Mortagne-sur-Gironde / PD
')
The defense of the city is a collective matter
In 1648, during the Turkish-Venetian war , the siege of Kandia began in Crete. The Kandia garrison, commanded by Francesco Morosini, successfully repelled the attacks of Turkish soldiers and artillery thanks to the support of the fleet, which supplied provisions and reinforcements, and also defended the inhabitants from attack from the water. Because of this kind of “separation of duties”, the city resisted for a long time - the siege lasted 21 years and went down in history as the longest.
In order for the “cloud fortress” to also stand for long years (much longer than Candia), it is important for companies to share protection responsibilities with the cloud provider. The latter removes some of the concerns and responsibility from the organizations. In order to understand what “trouble” the provider protects you from, it is worth exploring the Service Level Agreement (SLA) in detail. So you will understand which gate is securely fastened, and which gates will have to be further strengthened.
The cloud provider can monitor the operation of the infrastructure: data storage systems, computing resources and databases. It can also work with a network: protect from DDoS attacks and spoofing, be responsible for segmentation and perimeter defense. The user, in turn, can control access, updates and monitor security systems. He is also responsible for the components of the hosted application.
Understanding your role and the role of the provider will allow you to better choose a solution for the organization of cloud infrastructure. Moreover, the SLA prescribes the compensation that the provider pays for the breakdown of the services. For example, if the availability indicator does not match: in 1cloud it is equal to 99.9%. Our clients get all the money back if availability falls to 76.98%.
However, when choosing an ally to pay attention only to the "percent" should not be. It is also necessary to consider how the provider is ready to solve the difficulties. For example, we at the company 1cloud offer daily backups to protect user data from damage. Copying is performed to a remote disk array, so the information is restored, even if the server's file system is unavailable.
In addition to studying the SLA, attention should also be paid to access control policies. To do this, it is necessary to determine what is included in the assets of the company and to list the duties necessary to apply to them. It will not be superfluous to develop a plan for the standardization of resources and conduct a study on the presence of vulnerabilities, at the same time classifying risks.
In order to control access to data, experts advise to centralize authentication — this makes it easier to track calls to the system and monitor gaps.
Digging the moat is another line of defense
By the way about authentication. Two-factor authentication (2FA) is an additional level of protection against attacks from the outside, which uses another identifier - the token. Today 2FA offers many companies: technical, financial, research, etc. The function of two-factor authentication is used by all major services and social networks - Facebook, Gmail, Twitter, LinkedIn, etc. Last year 2FA introduced Instagram.
Smartphones can act as a token with a code, because today every third inhabitant of the planet has them. One-time password is generated using a special application (Google Authenticator or other specialized) or comes in the form of SMS. The latter option is the most simple and user friendly.
It is this implementation variant 2FA that we use to protect the personal account of clients. To enter the control panel after enabling two-factor authentication, the user must enter the code received via SMS, in addition to the standard email address and password.
“2FA helps protect against a fairly large attack vector,” says Jim Fenton, director of security for OneID, who is developing a unified identity system. “To bypass two-factor authentication, attackers will have to steal your fingerprints or gain access to cookies or codes generated by tokens.”
In fact, 2FA is the second line of defense - a grille on the gate or a moat with
Both two-factor authentication and the moat are not impenetrable for attackers, but they seriously complicate their lives.
Network resources - a source of life-giving moisture
In 1521, Hernan Cortes (Fernando Cortes), a Spanish conquistador, began the siege of the Aztec city of Tenochtitlan. The army of Cortes consisted of 200 thousand people. There were one and a half times more defenders. The Spaniards quickly realized that they couldn’t succeed in taking the city without reason, so they decided to destroy the water supply. This has led to problems with drinking water in the city and outbreaks of the epidemic behind the walls. As a result, the Spaniards looted the city, destroying all the buildings, and in its place a new one was erected - Mexico City.
In cloudy architectures, networks like plumbing systems in castles play a big role. Users manage data centers with a varying number of virtual machines, in which distributed services also operate, allowing them to adhere to the DevOps methodology.
In this case, the network assumes all communications, being a kind of “nervous system” of applications. If an attacker manages to access it, he is given the opportunity to change information, download malware, and steal identity data.
If a cloud account is hacked, a third party will be able to use it to access the systems and, for example, damage the company's reputation. Cloud Security Alliance reports that in 2009, many Amazon systems were hacked and used in the work of the Zeus botnet. According to some reports, in the past, these sites were used to send malicious software to NASA and Bank of America.
Therefore, the network needs attention. For a better understanding of the processes taking place, you should monitor its activity. The cloud provider provides certain resources for this. For example, 1cloud clients can monitor the load on the communication channels in the control panel.

Communication load monitoring window (and not only)
In addition, you should think about the organization of private networks. This is useful for business security. Not all traffic can be “run” over the Internet, plus not all servers should have access there. Additionally, such networks increase application performance and speed. The speed of public connections varies from 10 to 100 Mbps, while the width of a private channel is several times larger - at 1cloud it is 10 Gbps.
Ask the clerk, or know your vulnerabilities
Log management is also an effective way to ensure security. Knowing what is happening in the system, it is easier to investigate incidents and find "malware". Known situations where the analysis of logs allowed to track intruders.
Here is an example of an investigation related to the cleaning of iCloud accounts with employees of an unnamed company. IT service was tasked with checking the OWA server logs: there were no suspicious activity on the affected accounts. Administrators found a clue - they were accessed from several unusual IP addresses. Having sorted out events and logs, it was possible to establish the scheme of the attacker's work and close several security holes.
In addition to analyzing the logs, it is worthwhile to constantly stay abreast of developments on existing and emerging vulnerabilities in order to choose an advising strategy. There is also a historical analogy for this - the siege of Kumamoto Castle.

/ wikimedia / Siege of Kumamoto Castle / PD
Saigo Takamori, who led the Satsuma army, attempted a decisive assault on the fortress. The fighting continued until late at night. However, the Satsuma army could not take the castle. After two days of fruitless battles, Satsuma's forces established an environment of fortifications around Kumamoto and laid siege to the stronghold.
However, Kumamoto Castle, built in 1598, was one of the strongest fortresses in Japan. In order to inflict tangible damage on the castle, the attackers had to place their artillery at positions close to the castle, which opened them for return fire from the walls. This advantage was used by its advocates who were in the minority. The rebel weapons were powerless against the tactics of the Kumamoto garrison. Thanks to the knowledge of vulnerabilities and the competent use of tactical advantages, the garrison of the fortress withstood the onslaught of the enemy.
Therefore, it is important to know what weaknesses there are in your castle in order to respond to them accordingly. Public resources help users learn about emerging vulnerabilities in software and other systems, in which participants share their exploits. Here are some of them: Seclists , SecurityFocus , Exploit Database , Security Bloggers Network . There are also Russian-speaking resources: SecurityLab , xakep and the corresponding section on Habré.
What to remember
With the growing number of cybercrimes (the damage from global cybercrime in 2016 approached 600 billion), companies need to take care of the security of the cloud environment. To do this, pay attention to the following things:
- Examine the service level agreement. This gives an insight into where the boundaries of responsibility lie, and what weaknesses exist in the fortifications.
- Use 2FA to protect accounts and personal accounts. Although this additional level of protection does not provide 100% security, it creates certain problems for intruders.
- Network monitoring allows timely detection of malicious activity and load spikes in order to take appropriate measures in a timely manner.
- Log management is another effective way to ensure security. The information collected about the system simplifies incident investigation and vulnerability detection.
These approaches can improve the security of the system, but it is important to remember about care and caution - without constant training [on their own and others' mistakes] protective measures may not work.
PS What else do we write in our blog:
Source: https://habr.com/ru/post/337428/
All Articles