How cash software deals with economic misdemeanors
Any large trading network regularly has to deal with economic crimes - they are committed by both customers and store employees. And if the first can be dealt with using a video recording and monitoring system, then it is much more difficult to protect business processes from personnel directly involved in them. Let's talk about how this can be done at the level of software that controls the work of the cash node.

Modern front-office systems, when closing a check at the POS terminal, transmit information to the cash register server, where data for a shift is accumulated. This allows, including the security service, to analyze events occurring in the cash zone. However, check information is often not enough to fully monitor the actions of the cashier.
')
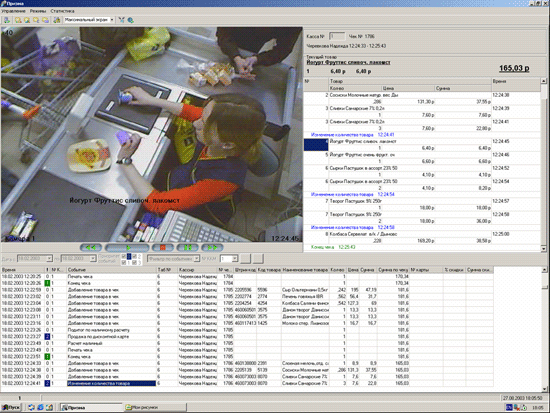
Cash management video monitoring systems combine video recording and monitoring functions with cash events monitoring: that is, the recording of cashier actions and receipt tape data is synchronized over time. This allows you to get information about events that occurred at the POS-terminal, but were not reflected in the check (opening a cash drawer, attempts by the cashier to perform unauthorized actions). To obtain video information, a video camera is installed above the cash node, which allows you to control the entire process of communication between the cashier and the buyer. In parallel with this, the cash register software can send check data in the required format to the video monitoring system. For example, the cash program “Profi-T” is easily integrated with such popular video control systems for cash transactions using protocols such as Prisma, ITV, G2.
The server of the video monitoring system constantly works in the network and receives packets from the Profi-T server with information about cash events. When receiving the “check start” event, a slide is captured and by the time the event occurs, a continuous video is attached to the checkout number.
All modern front-office systems are able to differentiate access rights to operations. Typically, staff are graded for roles:
- “cashier” - his duties include the formation of the commodity part of the check (scanning of goods) and cash or bank transfer with the buyer. At the end of the shift, he needs to hand over the amount that, according to the cash program, is in the cash drawer.
- “senior cashier” or “administrator” - he performs operations that leave loopholes for the unscrupulous cashier.
It:
• reversal (cancellation of a commodity position) in a check that is formed (before it was closed);
• Return - if the buyer for some reason wants to return the goods;
• pending check - this operation is performed at the moment when it is necessary to temporarily postpone the purchase (for example, the cashier has already scanned the goods and switched to the payment mode, and the buyer found that he forgot the wallet in the car). In this case, in order not to delay other customers, the check is canceled with the possibility of subsequent recovery. However, deferred and unclaimed checks are finally eliminated when the shift is closed and information about them is not stored anywhere. This is used by some unscrupulous cashiers - accepting payment, they do not recover the check, and put the money for the purchase into their pocket.
"Profi-T" allows you to differentiate user access rights in two ways:
- by hardware (on the cash register keyboard) by turning the key;
- programmatically, by assigning users with access rights and then entering an individual login and password, scanning an individual barcode or rolling the key card.

You can also differentiate access rights to any cash transactions, for example, to make sure that only administrators perform sales of goods:

As we said above, actions performed by the cashier can be recreated using the data from the video monitoring system. But this is not the only possibility. The actions of the cashier can be tracked in real time through the cash program server. This is relevant in the case when it is necessary to check a new employee or check suspicions regarding one of the cashiers.
"Profi-T" in this case can work in the mirror mode - it allows you to connect to a certain cash desk from the cash server and observe the actions of its operator. If there are any abuses on the part of the cashier, they can be used to prove suspicions or to argue the claims.

The prohibition of the sale of goods allows the store to deal with both economic crimes and re-grading. Typically, such incidents occur in chain stores, where a product directory is formed for all points of sale. At the same time, it sometimes happens that in a certain store there are no certain goods in stock that are uploaded to the cashier. In this case, the cashier can, by chance or by malicious intent, for example, sell expensive apples at a cheaper price.
However, the store administrator can prevent such opportunities in advance by prohibiting the sale of missing goods in the cash program. When the cashier tries to sell goods from this category, the software will issue a ban notice.

When it comes to economic crimes on the part of the store employees, many buyers are immediately interested in the question: can the bank card details with which they pay for the goods be used by fraudsters? To unequivocally answer it is difficult - each cash software has its own capabilities and principles of action.
However, we will try to shed light on this problem using the example of Profi-T. Our cash program does not store personal cards of customers: they are automatically transferred to the bank and do not remain in the system. Payment by credit card is a trilateral transaction in which cash register software, an issuing bank and a company providing acquiring are involved. Cashier software sends a transaction request to acquiring. If the issuing bank replies positively, the buyer’s funds are written off. At the same time, only the transaction number remains in the cash register software in case you need to make a return by check. Full information about the entire transaction made is stored in encrypted form only in the payment terminal, which does not apply to the cash register software.
Of course, the features of cash software that we have listed will not save the store from all economic crimes by employees, but they can help to significantly reduce their number.

Transferring check information to the video monitoring system
Modern front-office systems, when closing a check at the POS terminal, transmit information to the cash register server, where data for a shift is accumulated. This allows, including the security service, to analyze events occurring in the cash zone. However, check information is often not enough to fully monitor the actions of the cashier.
')
Cash management video monitoring systems combine video recording and monitoring functions with cash events monitoring: that is, the recording of cashier actions and receipt tape data is synchronized over time. This allows you to get information about events that occurred at the POS-terminal, but were not reflected in the check (opening a cash drawer, attempts by the cashier to perform unauthorized actions). To obtain video information, a video camera is installed above the cash node, which allows you to control the entire process of communication between the cashier and the buyer. In parallel with this, the cash register software can send check data in the required format to the video monitoring system. For example, the cash program “Profi-T” is easily integrated with such popular video control systems for cash transactions using protocols such as Prisma, ITV, G2.
The server of the video monitoring system constantly works in the network and receives packets from the Profi-T server with information about cash events. When receiving the “check start” event, a slide is captured and by the time the event occurs, a continuous video is attached to the checkout number.

Differentiation of access rights to operations
All modern front-office systems are able to differentiate access rights to operations. Typically, staff are graded for roles:
- “cashier” - his duties include the formation of the commodity part of the check (scanning of goods) and cash or bank transfer with the buyer. At the end of the shift, he needs to hand over the amount that, according to the cash program, is in the cash drawer.
- “senior cashier” or “administrator” - he performs operations that leave loopholes for the unscrupulous cashier.
It:
• reversal (cancellation of a commodity position) in a check that is formed (before it was closed);
• Return - if the buyer for some reason wants to return the goods;
• pending check - this operation is performed at the moment when it is necessary to temporarily postpone the purchase (for example, the cashier has already scanned the goods and switched to the payment mode, and the buyer found that he forgot the wallet in the car). In this case, in order not to delay other customers, the check is canceled with the possibility of subsequent recovery. However, deferred and unclaimed checks are finally eliminated when the shift is closed and information about them is not stored anywhere. This is used by some unscrupulous cashiers - accepting payment, they do not recover the check, and put the money for the purchase into their pocket.
"Profi-T" allows you to differentiate user access rights in two ways:
- by hardware (on the cash register keyboard) by turning the key;
- programmatically, by assigning users with access rights and then entering an individual login and password, scanning an individual barcode or rolling the key card.

You can also differentiate access rights to any cash transactions, for example, to make sure that only administrators perform sales of goods:

Work software in mirror mode
As we said above, actions performed by the cashier can be recreated using the data from the video monitoring system. But this is not the only possibility. The actions of the cashier can be tracked in real time through the cash program server. This is relevant in the case when it is necessary to check a new employee or check suspicions regarding one of the cashiers.
"Profi-T" in this case can work in the mirror mode - it allows you to connect to a certain cash desk from the cash server and observe the actions of its operator. If there are any abuses on the part of the cashier, they can be used to prove suspicions or to argue the claims.

Prohibition of the sale of goods
The prohibition of the sale of goods allows the store to deal with both economic crimes and re-grading. Typically, such incidents occur in chain stores, where a product directory is formed for all points of sale. At the same time, it sometimes happens that in a certain store there are no certain goods in stock that are uploaded to the cashier. In this case, the cashier can, by chance or by malicious intent, for example, sell expensive apples at a cheaper price.
However, the store administrator can prevent such opportunities in advance by prohibiting the sale of missing goods in the cash program. When the cashier tries to sell goods from this category, the software will issue a ban notice.

Myth: Personal data in the store
When it comes to economic crimes on the part of the store employees, many buyers are immediately interested in the question: can the bank card details with which they pay for the goods be used by fraudsters? To unequivocally answer it is difficult - each cash software has its own capabilities and principles of action.
However, we will try to shed light on this problem using the example of Profi-T. Our cash program does not store personal cards of customers: they are automatically transferred to the bank and do not remain in the system. Payment by credit card is a trilateral transaction in which cash register software, an issuing bank and a company providing acquiring are involved. Cashier software sends a transaction request to acquiring. If the issuing bank replies positively, the buyer’s funds are written off. At the same time, only the transaction number remains in the cash register software in case you need to make a return by check. Full information about the entire transaction made is stored in encrypted form only in the payment terminal, which does not apply to the cash register software.
Of course, the features of cash software that we have listed will not save the store from all economic crimes by employees, but they can help to significantly reduce their number.
Source: https://habr.com/ru/post/337366/
All Articles