How to protect yourself from encryptors on the perimeter of the network

Although the most effective protection from encryptors is implemented on end devices, however, preventive measures should be taken at the network perimeter. Let us explain how this can be done with the help of Panda GateDefender .
The events of recent months have shown that traditional antivirus solutions are not very effective in the fight against unknown threats and attacks, including from encrypters. In our articles, we repeatedly tried to draw your attention to a new security model based on the use of EDR technologies, which, thanks to continuous monitoring, tracking the relationship between all processes and classifying 100% of active processes, can significantly increase the level of security from today's unknown threats: targeted attacks, Fileless attacks, malware-free attacks, unknown exploits and cryptographers, etc. For example, the Panda Adaptive Defense family of solutions, which uses EDR technologies, are designed to combat such “surprises”.
')
But such solutions are solutions for protecting end devices directly. And what would not hurt to take on the perimeter of the network?
Today in our article we will talk about what preventive security measures should be implemented on the network perimeter in order to filter encryptors before penetrating the corporate network, and also to reduce the possible consequences if some of the representatives of this class of threats are activated on end devices.
A little bit about cryptographers
As you know, cryptographers are a form of fraud used to extort money from a victim whose end devices were blocked by a certain type of malware, with the result that she (the victim) loses access to the data on these devices.
Encryption is a type of malware that installs on the end device and encrypts the contents (all or certain types of files) of its hard drives and on all attached network drives. As a result, the user loses access to the stored data until he pays the ransom (and it’s not a fact that after this it will be possible to get full access to all the data!). CryptoLocker is one of the most "popular" examples of cryptographers using a public RSA key. Recently, other well-known examples have also become known.
To put it simply, cryptographers, as a rule, are distributed in disguised form through quite legitimate content, for example, an email attachment, a zip file containing photos, or other types of files that a potential victim is likely to open, t. to. does not imply any danger. However, when opening such files, the encrypter communicates with its management server (the so-called C & C server), which is responsible for generating a new RSA key pair (public / private) and storing the private key, and also sends the public key to the victim's device, after which the malware encrypts everything that it can find on hard drives and connected resources on the local network. After that, the encrypted data cannot be accessed until it is decrypted using the private key, which is only available on the C & C server.
(Although it is worth noting that the latest copies of encrypters “learned” to activate without actions from a potential victim ...).
Indeed, due to the fact that the size of the keys used for encryption is usually not less than 2048 bits, it is almost impossible to decrypt encrypted files without a private key: of course, this is possible in theory, but in practice it may take a lot of time . Thus, the only way to restore access to the data is to either reinstall all affected devices and restore the backup copy to them, or pay a ransom (which we do not recommend doing!) And hope to receive the private key (although there are many cases when the victims did not receive keys after payment).
Therefore, we advise you to keep all your systems and applications in an updated state, as well as to be sure that your employees are well aware of the danger of opening suspicious files or sites. Preventive measures are the best solution to prevent unpleasant events!
Why pay attention to the perimeter of the network?
Ensuring the fight against cryptographers and other modern threats, it is necessary to take preventive measures in various directions. Yes, the most effective measures (if we exclude strict prohibitions for everything at all, so that no one could work properly) can be taken at the level of end devices. The same EDR-technologies show a very high efficiency in the fight against cryptographers and new threats.
But due to the fact that the overwhelming majority of threats penetrate the corporate network from the Internet, the implementation of certain security measures at the perimeter of the network will definitely allow filtering known threats and complicating the encrypters' communication with their external management servers. Moreover, there is not much to do.
An example of protection from encryptors on the network perimeter
As an example, consider the Panda GateDefender solution - a UTM solution for integrated and integrated network perimeter protection, which offers the following modules: antivirus, antispam, content filtering, URL filtering, proxy, firewall, IPS / IDS, VPN, Hotspot, monitoring web applications and more. This solution comes in hardware, software and virtual versions.
With this solution, we will show a number of methods that allow you to intercept these threats at the perimeter of the network, as well as minimize their activity, blocking the channels used by attackers to control malicious processes and the spread of infection.
1. Use Panda antivirus
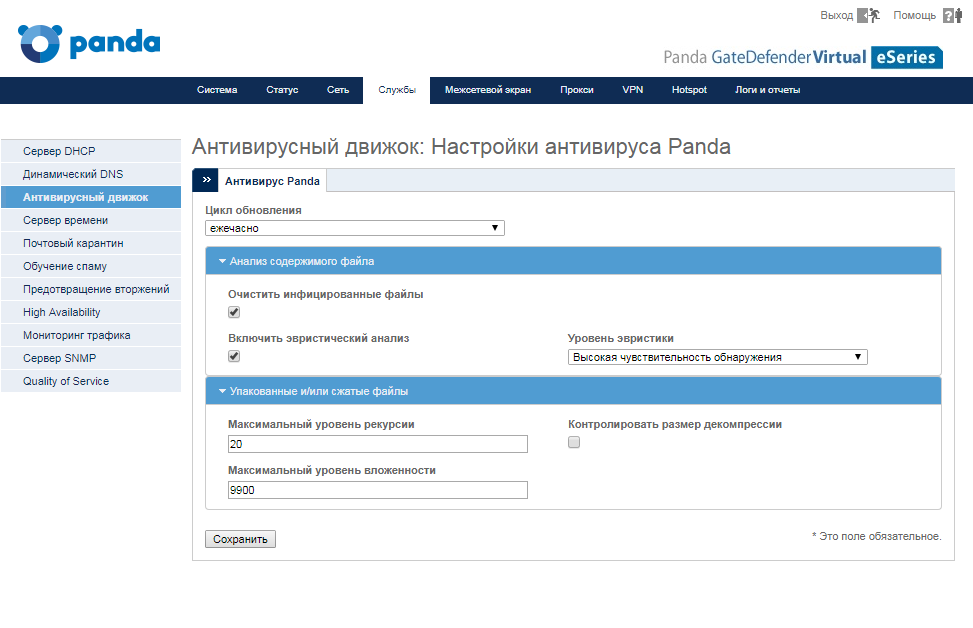
Panda GateDefender uses the Panda anti-virus engine to filter all types of traffic. It stores its signatures in the cloud, so you will always use updated signatures to identify and block any direction of infection. Thanks to the Panda antivirus engine, all checks are carried out in real time using the most "fresh" signatures and cloud knowledge bases.
To enable the anti-virus engine, in the Panda GateDefender management console, go to Services → Anti-virus engine , and on the Panda Anti-virus tab, configure the antivirus options.
2. Use IPS service
Intrusion Prevention System (IPS) can not only detect but also block traffic generated from cryptographers to their management servers.
To enable protection using IPS, in the Panda GateDefender Management Console, go to Services → Intrusion Prevention , where click the Enable IPS switch if it is disabled.
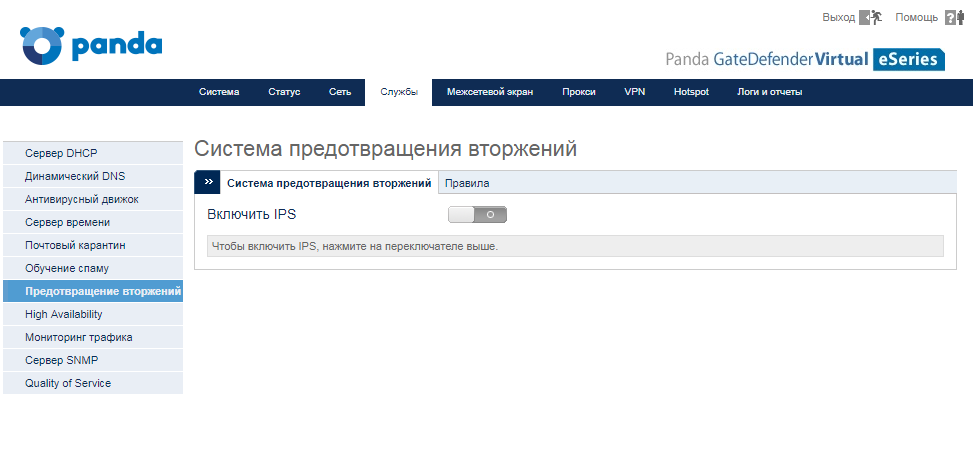
After enabling this service on the Intrusion Prevention System tab, you can configure additional IPS operation options.
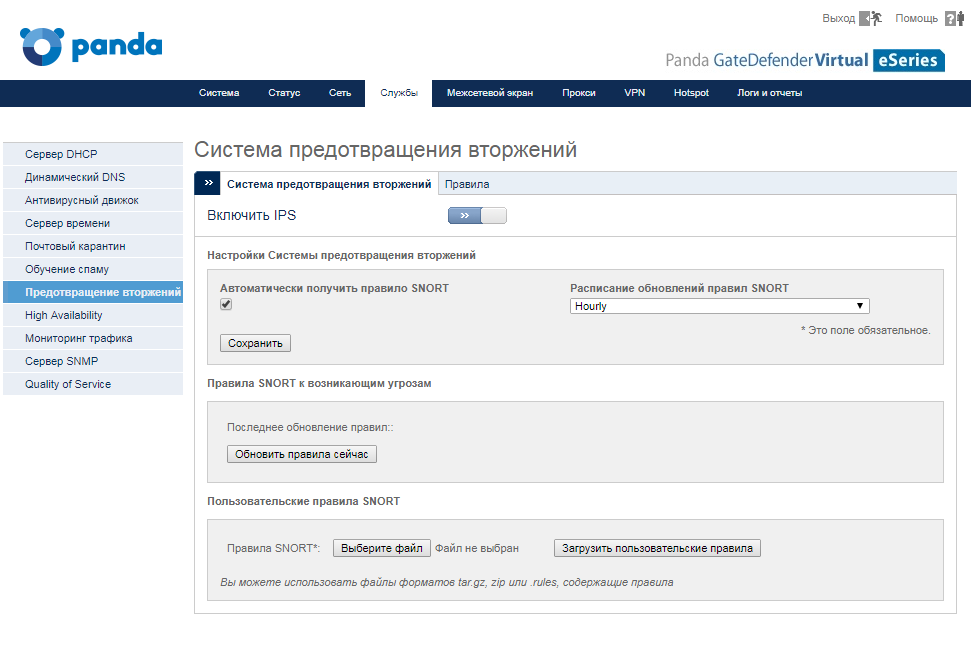
But in this matter we are more interested in the following Rules tab. Here on the third page, find the rule set auto / emerging-trojans.rules .

In this rule set, change the policy from warning to active use by clicking on the icon with the exclamation mark. After applying the change, the icon will change to a red shield.
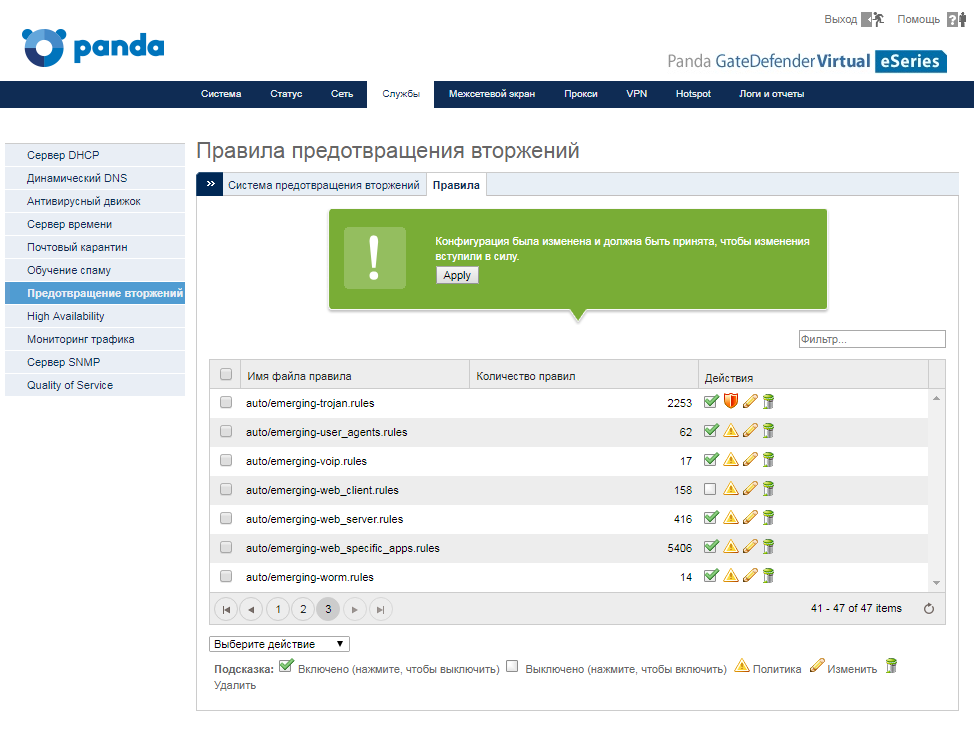
Now all traffic identified with Trojans will be blocked. You can also use the auto / emerging-tor.rules rule set for additional protection.
3. Use a firewall for outgoing connections.
The same CryptoLocker uses Torrents as an infection vector, and TOR connections to interact with their C & C management servers. Thus, another tip to improve security is to block all outgoing traffic that uses these two protocols.
In the Panda GateDefender Management Console, go to Firewall → Outbound Traffic.
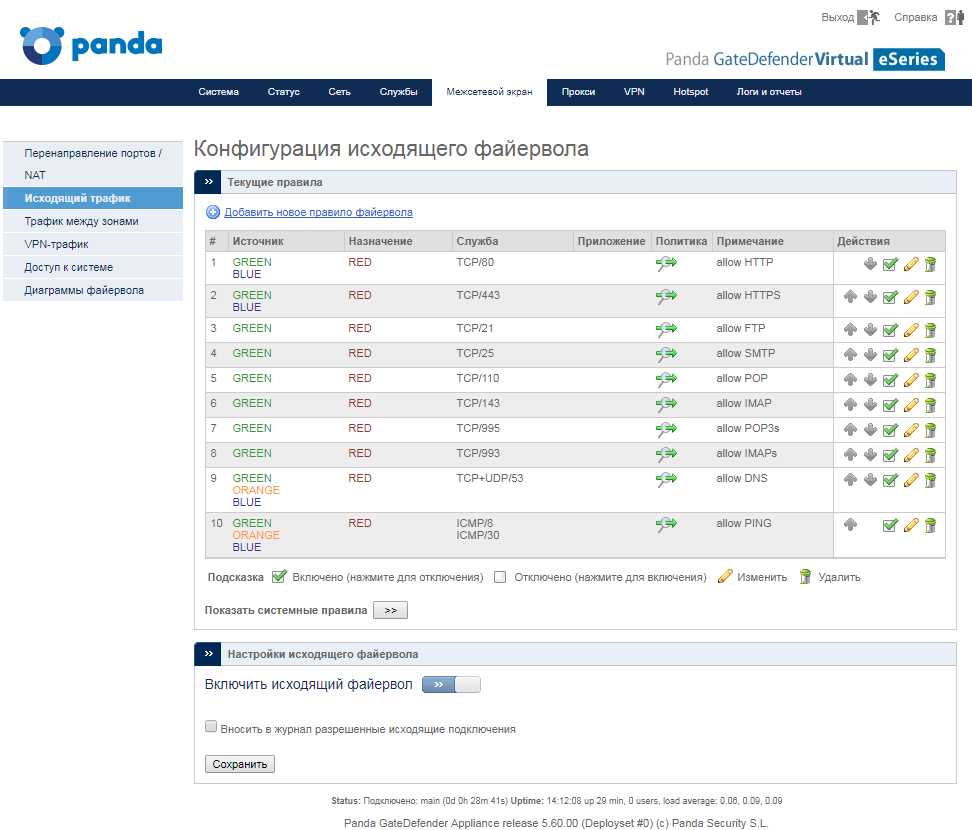
Here create a new rule with a policy to reject or deny to block this outgoing traffic. At the same time, in order to provide a higher level of protection, add all networks or zones that are after Panda GateDefender, specifying the <ANY> for Source / Type option.
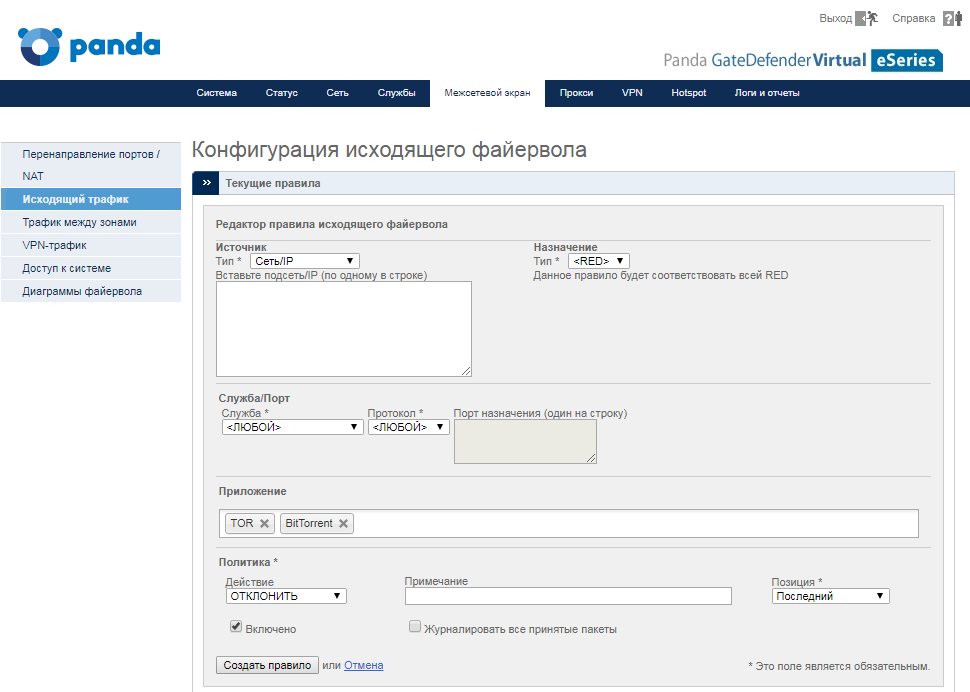
In addition, this rule must necessarily be first in the list of rules, therefore, it is necessary to set the corresponding value for the option Policy / Position .
As a result, in the list of rules you will see something like the following:
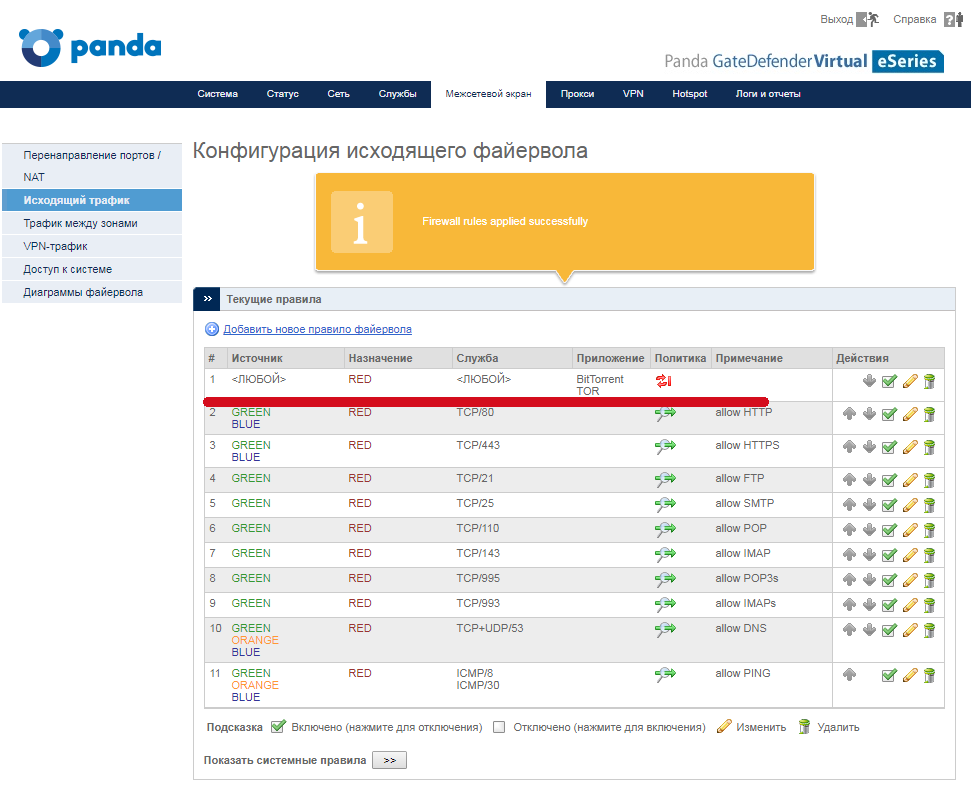
4. Use HTTP Proxy 1/2: Web Filter
Specify a profile in the HTTP proxy that blocks malicious URLs that can be distributed by encryptors.
In the Panda GateDefender management console, go to Proxy → HTTP .
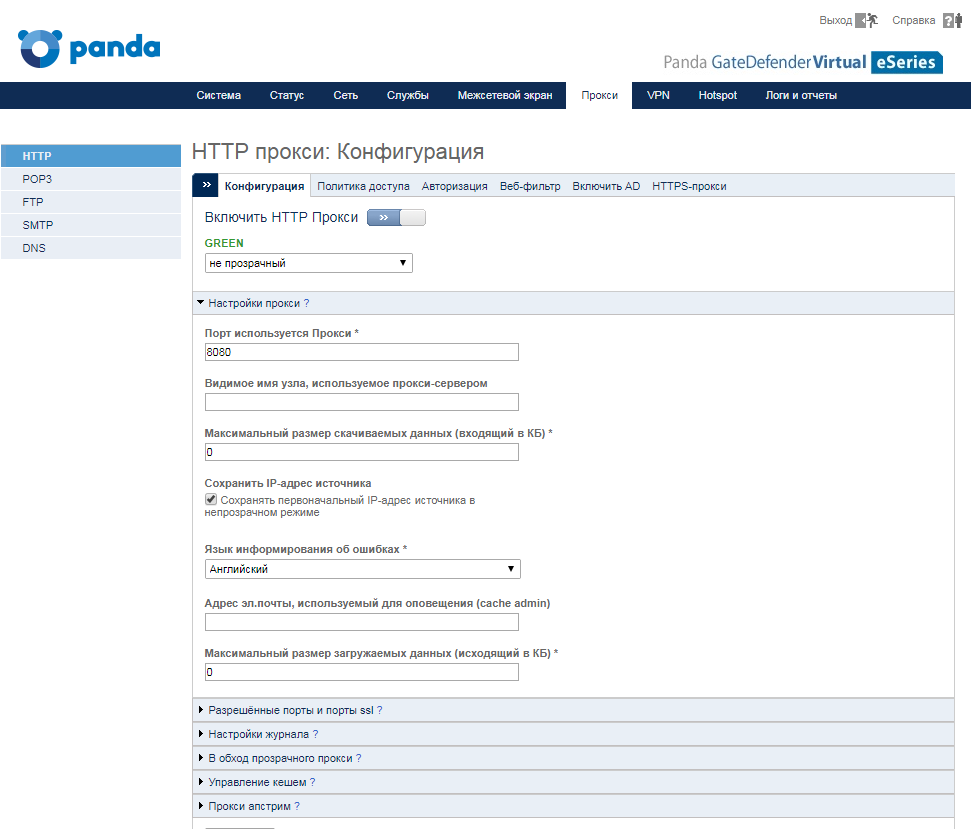
Here go to the Web Filter tab, where you can make changes to an existing profile or create a new one.
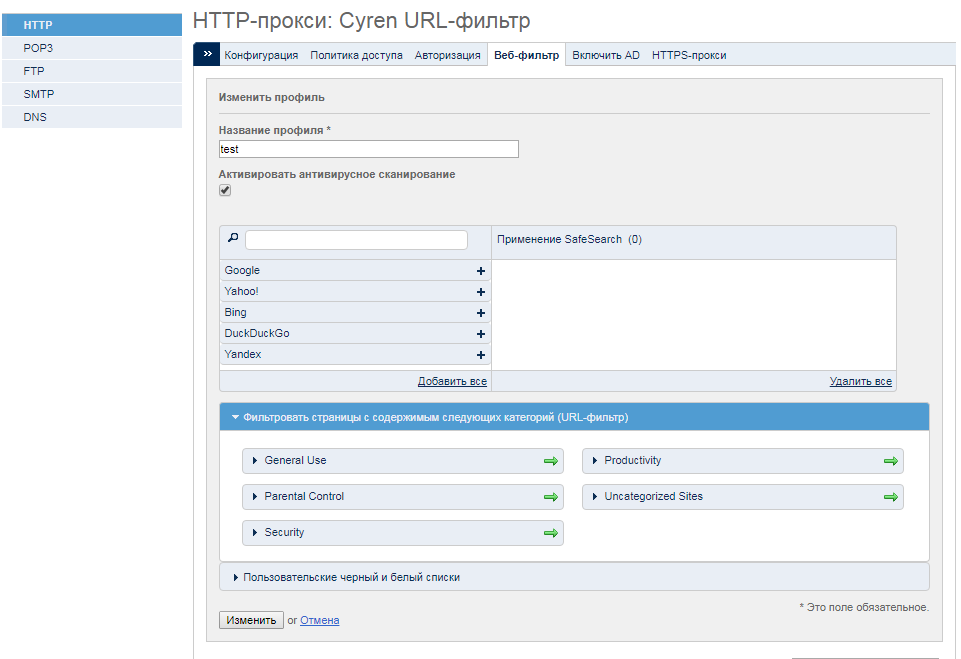
In the block for selecting filtered categories of web sites in the category Security, block access to the categories Anonymizers, Botnets, Compromised, Malware, Network Errors, Parked Domains, Phishing & Fraud, Spam Sites .
By the way, this method is best used in conjunction with the following method.
5. Use HTTP Proxy 2/2: Antivirus HTTP Verification
On the same page with options, check that the Enable antivirus scan option is enabled. By default, it is turned on, and therefore we recommend leaving it on.

6. Enable HTTPS Proxy
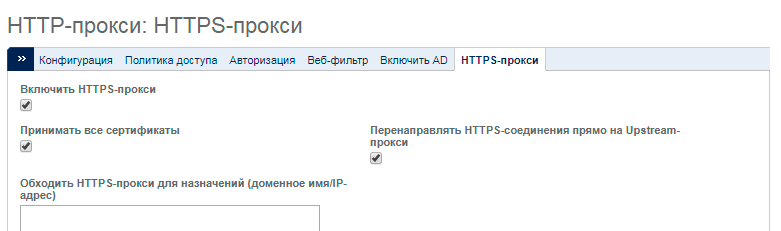
HTTPS connections are often used to spread the infection. Thus, HTTPS proxies can be used to intercept connections, allowing only legitimate connections to well-known websites.
Since HTTPS proxy works only in a pair with the HTTP proxy enabled, then first check that the latter is enabled in the Proxy → HTTP section. After that, go to the HTTPS proxy tab and enable the Enable HTTPS proxy option.
7. Enable SMTP proxy 1/2: Anti-virus scan
Often, cryptographers are distributed through attachments to emails, which at first glance may seem letters from well-known and legitimate senders, but in fact they contain a false link or a fake dangerous attachment. In this regard, it is recommended to activate anti-virus scanning in the SMTP proxy.
In the Panda GateDefender management console, go to Proxy → SMTP and enable SMTP proxy. Then, in the Virus settings section, enable the Scan mail for viruses option to activate the anti-virus engine for mail traffic.
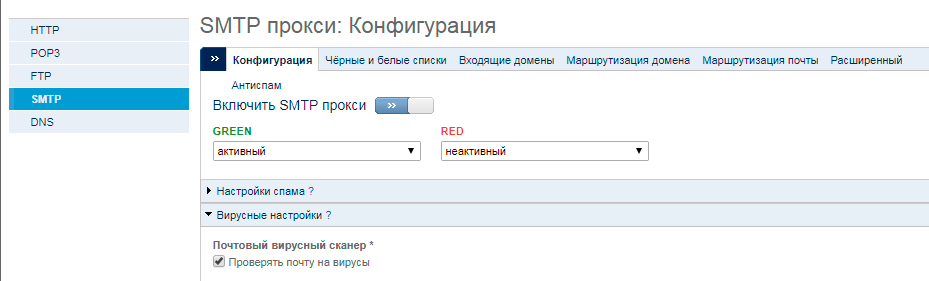
You can also configure what to do with the letters that will be marked as spam, as well as a number of other options.
After that, click the Save button to save the new configuration, and then in the confirmation message, you must apply the modified configuration in order to restart the SMTP proxy.
8. Enable SMTP Proxy 2/2: File Extensions and Dual Extensions
Another way to deliver encryptors as a mail attachment is to name the attached file using a double extension. (for example, meeting.png.bat), as a result of which the email client shows only the first extension (meeting.png), by virtue of which the user thinks that he has received a file with a picture. Double-clicking on this file, the user will not see any image, but a bat file will run without the user's permission. So another good recommendation is to block potentially dangerous file extensions and to ban the transfer of email attachments with a double extension.
To configure in the Panda GateDefender management console, go to the Proxy -> SMTP section and enable the SMTP proxy (if it was turned off).
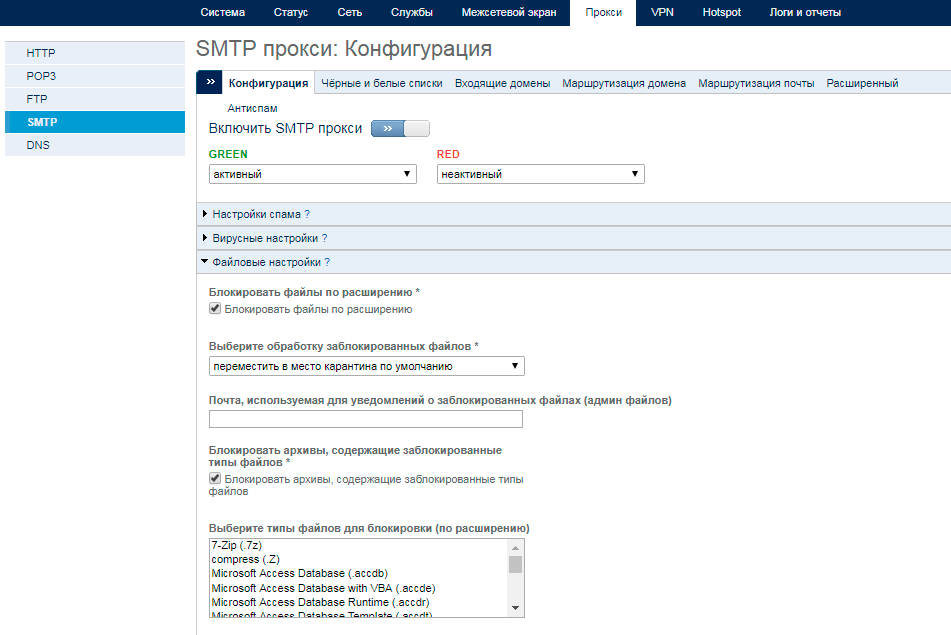
Then, in the File settings section, enable the Block files by extension option to activate the email attachment checking system.
After that, in the list for selecting file types for blocking by extension, select all extensions that should be blocked by SMTP proxy, and enable the option to block double extension files and select the corresponding values in the drop-down menu that appears.
9. Enable DNS Proxy
When CryptoLocker or other cryptographers are launched, they will try to change the DNS settings on the infected machine so that they can communicate with their management servers to work correctly. This development can be avoided by enabling the DNS proxy in the Panda GateDefender solution. In this case, all DNS requests from the device, which is located behind the Panda GateDefender solution, will always be intercepted by them, blocking any opportunity for cryptographers to contact their management server.
To do this, go to the section Proxy → DNS .
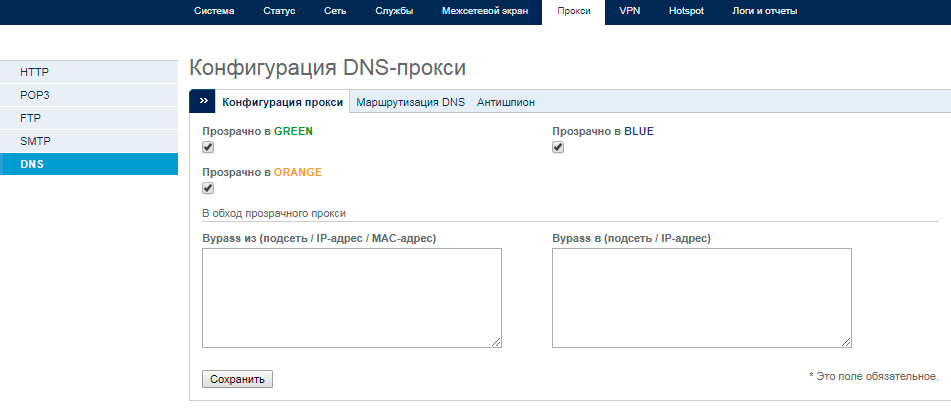
By the way, on the Antispyware tab, it makes sense to put daily updates to block known malicious domains.
Conclusion
As a result of the above simple actions, you can configure the perimeter protection of the network from encrypters by trying to block their penetration into the corporate network from the Internet, as well as complicating their ability to interact with their management servers. Such preventive measures will significantly reduce the risk of infection, as well as be able to minimize the possible consequences after the launch of encrypters in the corporate network.
More information about Panda GateDefender
You can also order a free version of Panda GateDefender for a period of 1 month by sending a request to sales@rus.pandasecurity.com.
Source: https://habr.com/ru/post/337174/
All Articles