Locky is alive: 23 million infected emails per day
According to a recent study conducted by three experts from Google, it is the Locky ransomware virus that is the most productive in terms of funds collected from victims. At the same time, WannaCry is not even included in the TOP-10.

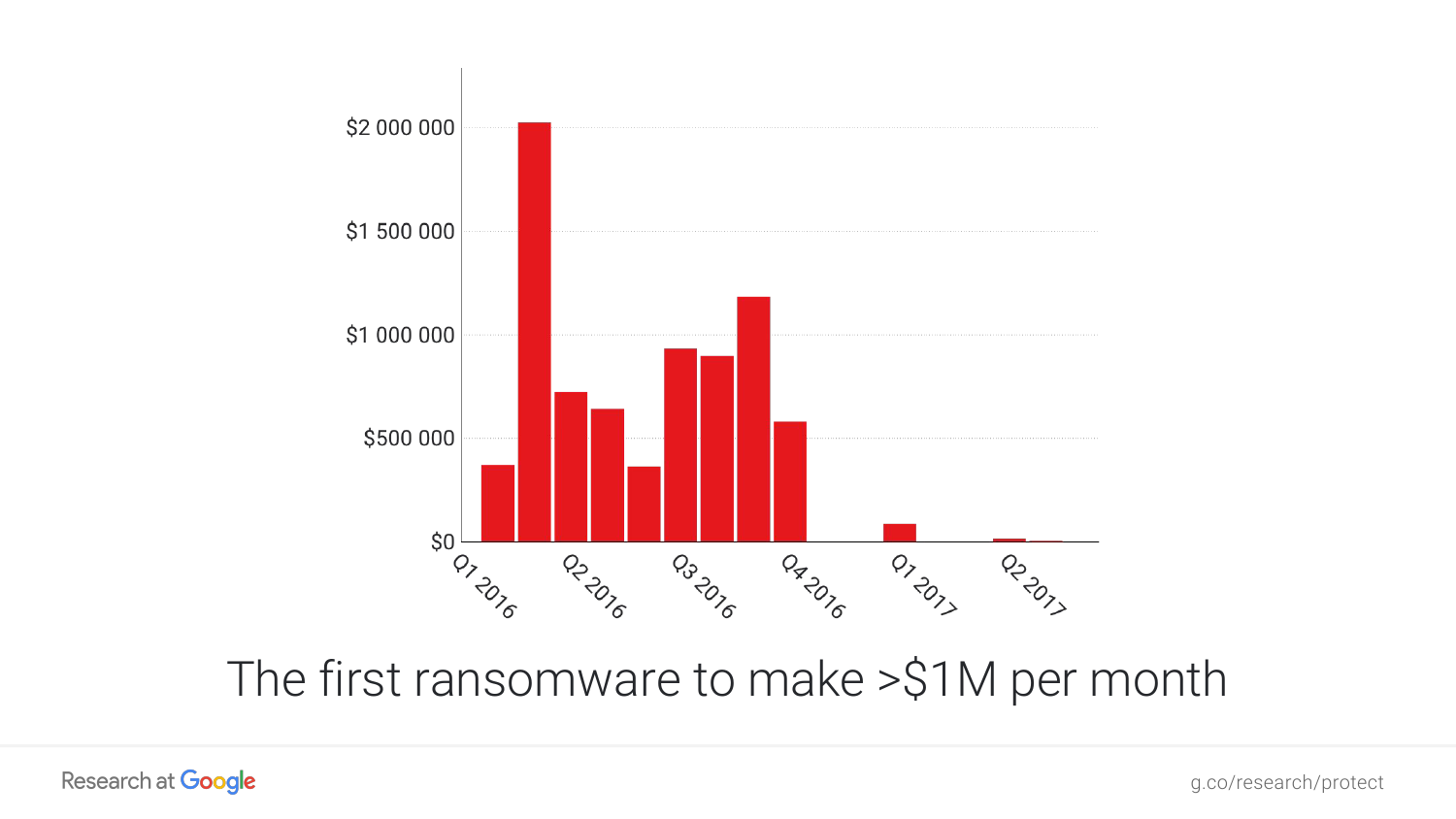
The main wave of infections occurred at the beginning of 2016. Ever since, Locky yielded leadership and the number of known cases of infection has dropped dramatically. But whenever we start thinking that the Locke cipher is dead, the infamous threat returns with a new blow.

')
Recently, researchers from two security companies independently discovered two massive spam campaigns, during which new versions of the Locky cipher were distributed via e-mail.
During the mailing, discovered by AppRiver researchers, just over a day on August 28, more than 23 million messages were sent to the USA containing Ransomware Locky, which seems to be one of the largest “advertising” campaigns of the second half of this year.
As the researchers noted, the emails sent during the attack were “extremely vague”. In order to convince the victims to start the file with Locky, the main themes of the letters were “send to print”, “documents”, “images”, “photos”, “images” and “scans”.
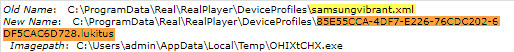
An email is sent with a ZIP archive with a hidden malicious attachment in the form of a Visual Basic Script (VBS) file attached to an additional ZIP file. As soon as the deceived victim clicks on it, the VBS file launches the bootloader, which downloads the latest version of Locky, the so-called Lukitus (“locked” in Finnish), from the greatesthits [.] Mygoldmusic [.com] site. The virus encrypts all files on the target computer and adds the [.] Lukitus extension to the files.
After the encryption process is completed, a ransom message is traditionally displayed on the desktop, requiring the victim to install Tor’s browser and visit the attacker's website for additional instructions.

Lukitus requires 0.5 Bitcoin (~ $ 2,300) for Locky-Descrambler, which allegedly will allow you to return your files.
The Lukitus spam campaign continues, and AppRiver researchers have posted a message stating that more than 5.6 million people have been quarantined by their security systems. Unfortunately, for this option, Locky is currently unknown about the possibility of decryption.
As a result of the second spam campaign of Locky, Comodo Labs researchers discovered more than 62,000 emails sent to the mailboxes they protected.
In just a few days of a coordinated attack, tens of thousands of users were sent letters with an attached file and small text. Attachment is an archive named “E 2017-08-09 (580) .vbs” (for each letter, the part “580” and the extension “vbs” are changed).

Attached files may have the extension .doc, zip, pdf, jpg, tiff. In fact, a click on the file downloaded “IKARUSdilapidated”, the latest type of virus from the “Locky” family.
After social engineering works, the sequence of events is similar to the one for the first spam campaign. The size of the required buyout ranges from 0.5 to 1 Bitcoin.

13325 different IP addresses were used in 133 countries to complete this distribution. Most attack servers were located in Vietnam, India, Mexico, Turkey and Indonesia. The researchers checked the owners of the IP-range and noted that most of them - telecommunications companies and Internet service providers. This indicates that the IP addresses belong to the infected devices, the so-called “zombie computers”, so the “botnet” can be distinguished among the elements of this attack in addition to the trojan and phishing.
What happened demonstrates the growing complexity of the organization and the scale of the new attacks with the aim of extortion. Ransomware viruses have become a multimillion-dollar and profitable business for attackers, there is no hope for an early cessation of attacks. Many experts believe that soon artificial intelligence systems will be able to fully protect the user from such threats. We recommend simple and obvious preventive measures that can be used today:
PS Other interesting articles from our blog:
→ How to stop a DDoS attack + code analysis WireX Botnet
→ How to share Cloud or vCloud Director
→ “State in the Clouds” and one GIS example from our practice
→ How much is your company? Brief on business valuation

The main wave of infections occurred at the beginning of 2016. Ever since, Locky yielded leadership and the number of known cases of infection has dropped dramatically. But whenever we start thinking that the Locke cipher is dead, the infamous threat returns with a new blow.


')
Recently, researchers from two security companies independently discovered two massive spam campaigns, during which new versions of the Locky cipher were distributed via e-mail.
During the mailing, discovered by AppRiver researchers, just over a day on August 28, more than 23 million messages were sent to the USA containing Ransomware Locky, which seems to be one of the largest “advertising” campaigns of the second half of this year.
As the researchers noted, the emails sent during the attack were “extremely vague”. In order to convince the victims to start the file with Locky, the main themes of the letters were “send to print”, “documents”, “images”, “photos”, “images” and “scans”.
An email is sent with a ZIP archive with a hidden malicious attachment in the form of a Visual Basic Script (VBS) file attached to an additional ZIP file. As soon as the deceived victim clicks on it, the VBS file launches the bootloader, which downloads the latest version of Locky, the so-called Lukitus (“locked” in Finnish), from the greatesthits [.] Mygoldmusic [.com] site. The virus encrypts all files on the target computer and adds the [.] Lukitus extension to the files.

After the encryption process is completed, a ransom message is traditionally displayed on the desktop, requiring the victim to install Tor’s browser and visit the attacker's website for additional instructions.

Lukitus requires 0.5 Bitcoin (~ $ 2,300) for Locky-Descrambler, which allegedly will allow you to return your files.
The Lukitus spam campaign continues, and AppRiver researchers have posted a message stating that more than 5.6 million people have been quarantined by their security systems. Unfortunately, for this option, Locky is currently unknown about the possibility of decryption.
As a result of the second spam campaign of Locky, Comodo Labs researchers discovered more than 62,000 emails sent to the mailboxes they protected.
In just a few days of a coordinated attack, tens of thousands of users were sent letters with an attached file and small text. Attachment is an archive named “E 2017-08-09 (580) .vbs” (for each letter, the part “580” and the extension “vbs” are changed).

Attached files may have the extension .doc, zip, pdf, jpg, tiff. In fact, a click on the file downloaded “IKARUSdilapidated”, the latest type of virus from the “Locky” family.
After social engineering works, the sequence of events is similar to the one for the first spam campaign. The size of the required buyout ranges from 0.5 to 1 Bitcoin.

13325 different IP addresses were used in 133 countries to complete this distribution. Most attack servers were located in Vietnam, India, Mexico, Turkey and Indonesia. The researchers checked the owners of the IP-range and noted that most of them - telecommunications companies and Internet service providers. This indicates that the IP addresses belong to the infected devices, the so-called “zombie computers”, so the “botnet” can be distinguished among the elements of this attack in addition to the trojan and phishing.
What happened demonstrates the growing complexity of the organization and the scale of the new attacks with the aim of extortion. Ransomware viruses have become a multimillion-dollar and profitable business for attackers, there is no hope for an early cessation of attacks. Many experts believe that soon artificial intelligence systems will be able to fully protect the user from such threats. We recommend simple and obvious preventive measures that can be used today:
- Beware of phishing emails. It is difficult for ordinary users to explain all the dangers of documents obtained from unverified sources. A possible solution is anti-spam protection with virus scan.
- Regular backup on external remote storage or in the cloud .
- Online update of antivirus software and protection systems.
PS Other interesting articles from our blog:
→ How to stop a DDoS attack + code analysis WireX Botnet
→ How to share Cloud or vCloud Director
→ “State in the Clouds” and one GIS example from our practice
→ How much is your company? Brief on business valuation
Source: https://habr.com/ru/post/336958/
All Articles