Analysis of the on-line conferences of the RKN on the topic: “problematic issues of restricting access to information ...”
In February-May 2017, Roskomnadzor held an on-line conference on the topic: "problematic issues of restricting access to information, the dissemination of which in the territory of the Russian Federation is prohibited" in various regions of the Russian Federation. In this article, an attempt to analyze the results of conferences and bring to the discussion of the community controversial points.
Through the search engines you can find the "traces" of this conference. Here are two links to the Official Website of the Federal Service for Supervision in the Field of Communications, Information Technology and Mass Communications.
conf19.htm (157 questions)
conf17.htm (last year) (89 questions)
Below are two links to conventionally held conferences in 2 regions.
On the Ural Federal District (21 question)
In the Tambov region (5 questions)
There are no posts on the links below. Here either the community did not have a single question, or something happened and the conference did not take place, despite orders from above.
In the Tula region
In the North Caucasus Federal District
Across Tomsk region
In the Republic of Ingushetia
In the Saratov region
In the Kurgan region
A cursory reading of the first 4 references made it possible to formulate 5 main problem areas.
1. How to block resources correctly and will there be sanctions in case the APK "Auditor" reveals an unlocked resource if it changes the IP address?
On the one hand, URLs and IP addresses are indicated in the RKN registry. On the other hand, there are resources that regularly change IP addresses and this can only be revealed by resolving via DNS. Moreover, this rezolving should be performed strictly after the “life” of the recording (TTL) expires. Well, here begins the "race" who quickly cope with rezolvingom. If the system is locked, then everything is fine. And what will happen if the "Inspector" will be faster?
Let's figure it out. This is what the RKN officers say about this:


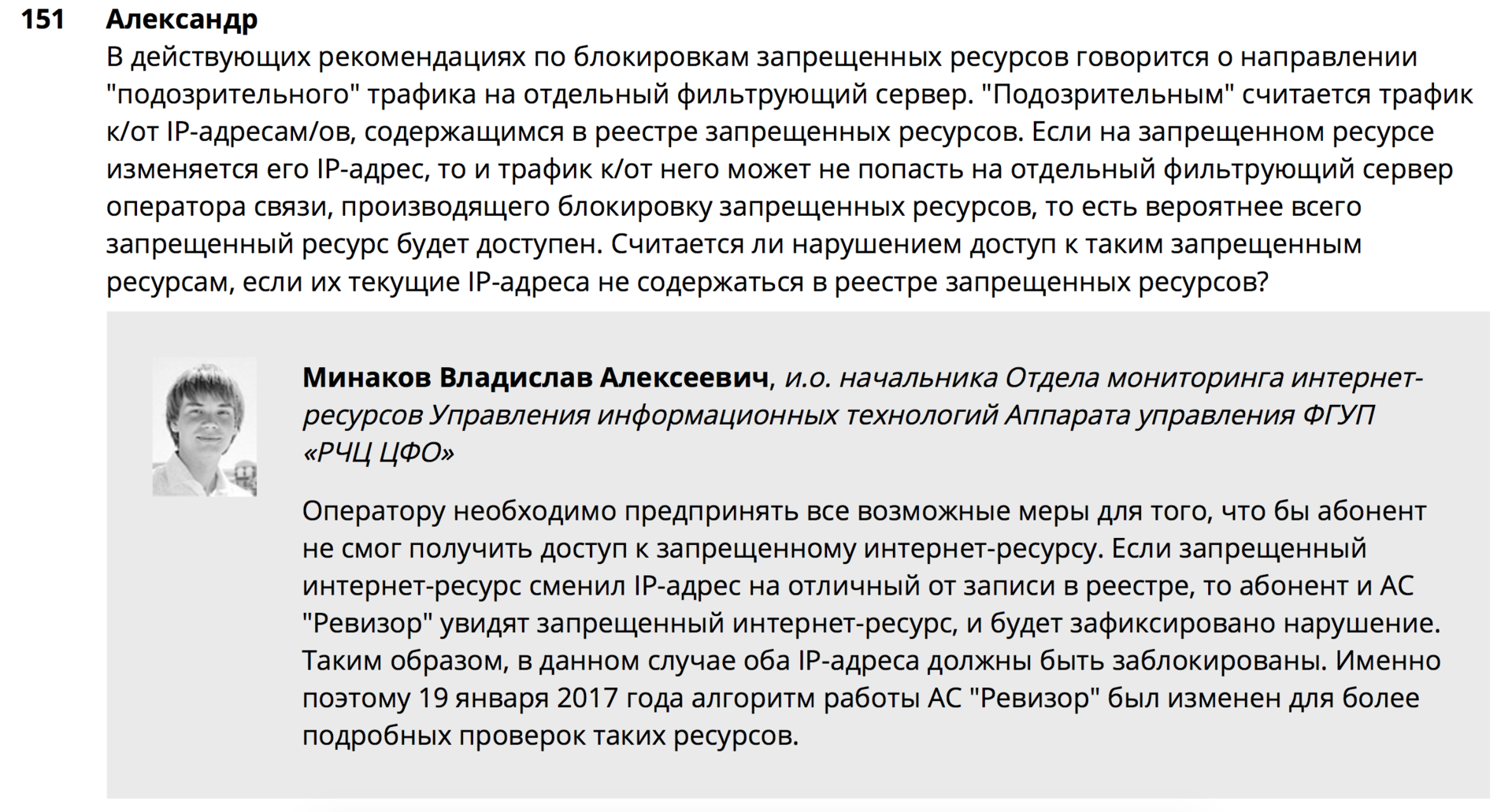


Well, come ...
2. The operator begins to block a resource that is not in the registry, but it is in the DNS. How does that happen? Yes, very simple. The operator does not have a DPI that would look at the SNI of the resource and in this case the blocking is performed by IP address.
ILV employee response:

But what I asked the small operator of Moscow Region, when I turned to him, to the request to add the addresses of habrahabr and geegtimes to the "white list":
We have no right to make any amendments if there is no official letter from the RKN. Otherwise, it will be arbitrariness. The AU Auditor, who is obliged to put on the side of ALL providers, is continuously traversed through the list of locks, and if at some point access to the prohibited site comes up, they will immediately strike us and punish us with a decent fine.
In the current implementation there is no dpi.


A vicious circle (DPI is needed and no matter how much it costs) ...
3. Is it possible for the operator to avoid punishment if the “Auditor” was quicker and some resource left the lock in one of the conditionally “fair” ways? This also includes questions about the possibility of signaling from the "Auditor" that something extra is open before being sent to the punitive bodies and whether there is time to eliminate the comments.
Here the opinion of the ILV staff coincide.





The result is that the operator has no chance of escaping punishment (except in court). This is very strange, in view of the fact that even if problems arise in SORM, the telecom operator is given an order to eliminate the remarks and indicate the deadline for the elimination.
4. Are there technical requirements for the system of blocking resources and monitoring that everything is blocked, the same and mandatory for all telecom operators?


Here is the last answer from the first paragraph. Just in case I will give the link again.



5. If the operator receives traffic from the supervisor, is he obliged to install a filtering system and what will happen if the Auditor finds violations? In my opinion - this is one of the most exciting stories. On the one hand, the parent operator exercises the lock, and no one removes responsibility from the connected operator for the absence of the lock. In the other - if you set your own system with the affiliated operator, then the traffic becomes 2 times "cleaner", but not without overhead costs, both financial and purely technical (additional delay).
Let's see some examples:




The bottom line is that - "Think for yourself how you, as a telecom operator, will get out."
On this, perhaps, everything. It is difficult to say something extra. In our country, everything is as usual ...
UPD 1 (thanks @BlackGorunuch )
In the Updated recommendations of Roskomnadzor to communication operators on restricting access to prohibited information of June 23, 2017, the following phrase actually appeared:
In case the telecom operator receives traffic from all upstream telecom operators filtered in accordance with the recommendations, decisions on bringing the operator to administrative responsibility if the unlawful blocking of unlawful information is taken will be made taking into account the terms of contracts concluded between such telecom operators.
Accordingly, it is necessary to re-read the accession agreement once more to clarify who does what.
Please note that everything described (not counting the pictures from the site of the RKN) is my personal opinion. Your comments are expected to be posted.
Also, please take into account the inadmissibility of offensive statements regardless of whose address they are sent to.
')
Source: https://habr.com/ru/post/336564/
All Articles