“The State in the Clouds” and one GIS example from our practice

The conservatism of state bodies of executive power in its activities is directly the nature of the law, just so, with a capital letter. But, nevertheless, modern technologies have also reached this traditionally established community. In early 2017, the president signed a decree “On the Strategy for the Development of the Information Society in the Russian Federation for 2017-2030”, which was a logical continuation of the development of the previous strategy from 2008. So, what can the modern IT community offer for the development of the Russian information society?
Answering this question, you can list a lot of modern technologies, methods and automation tools that ensure the implementation of government tasks. We, for our part, as the basis for their implementation, propose to consider the clouds and the issue of placing information systems of state bodies in them. The red line in the issue of placing GIS in the cloud service provider is the issue of information security and compliance with the legislation of the Russian Federation, so we touch on this topic.
')
Placing a GIS in the cloud of an IaaS provider
Placing information systems in the cloud attributed by the legislation of the Russian Federation to state information systems (GIS) requires both the owner of information systems (IS) and the service provider to perform a number of organizational and technical measures to comply with information security requirements defined by the legislation of the Russian Federation.
What does GIS security legislation require?
Perhaps we start with the federal laws, which for us have the greatest practical application. So let's get started.
The starting point for us will be FZ-149 “On Information, Information Technologies and Protection of Information”, it states the following provision:
State bodies defined in accordance with the regulatory legal act regulating the functioning of the state information system must ensure the accuracy and relevance of the information contained in this information system, access to this information in cases and in the manner prescribed by law, as well as protection of this information from unlawful access, destruction, modification, blocking, copying, provision, distribution and other illegal actions.
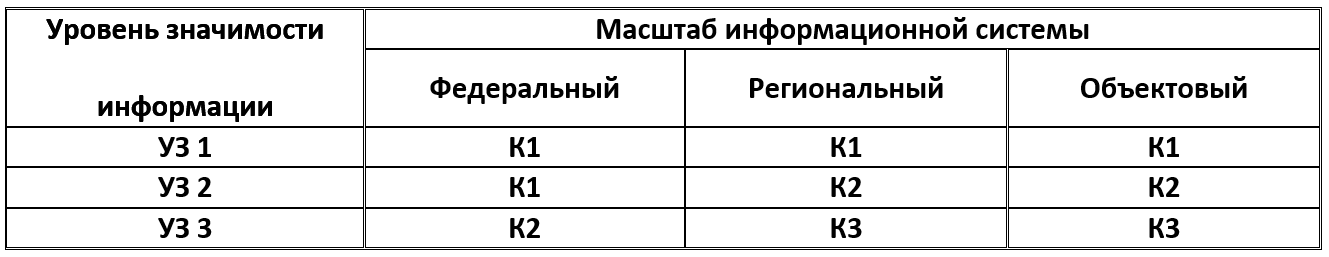
In order to comply with the requirements of this law, the Order of the FSTEC of Russia of February 11, 2013 No. 17 “On Approving Requirements for the Protection of Information Not Containing a State Secret Contained in State Information Systems” was adopted. The last changes to this order were made on February 15, 2017. This change, including the GIS classification, was modified, and at the moment we have 3 GIS security classes left. The lowest class is the third, the highest one is the first.
The security class of an information system (first class (K1), second class (K2), third class (K3)) is determined depending on the level of significance of information (US) processed in this information system, and the scale of the information system (federal, regional, facility ).
When processing in the information system two or more types of information (official secrecy, tax secrecy and other types of restricted access information established by the legislation of the Russian Federation), the significance level of information (US) is determined separately for each type of information. The final level of significance of the information processed in the information system is determined by the highest values of the degree of possible damage determined for the confidentiality, integrity, availability of information of each type of information. (For details, see the Order of the FSTEC of Russia of 11.02.2013 N 17)
Scale of state information systems
The information system has a federal scale, if it operates on the territory of the Russian Federation (within the federal district) and has segments in the constituent entities of the Russian Federation, municipalities and (or) organizations.
An information system has a regional scale if it functions on the territory of a constituent entity of the Russian Federation and has segments in one or several municipalities and (or) subordinate and other organizations.
An information system has an object scale if it functions at the facilities of one federal state authority, state authority of a constituent entity of the Russian Federation, a municipality and (or) organization and has no segments in territorial bodies, representative offices, branches, subordinate and other organizations.
An information system has a regional scale if it functions on the territory of a constituent entity of the Russian Federation and has segments in one or several municipalities and (or) subordinate and other organizations.
An information system has an object scale if it functions at the facilities of one federal state authority, state authority of a constituent entity of the Russian Federation, a municipality and (or) organization and has no segments in territorial bodies, representative offices, branches, subordinate and other organizations.
The security class of the information system is determined in accordance with the table:
To implement measures to protect the information necessary to ensure the security of the processed information, it is necessary to carry out a number of organizational and technical measures. In general terms, it is possible to distinguish the following stages, the implementation of which is prescribed to us by order No. 17:
- formation of requirements for the protection of information contained in the information system;
- development of information security information system;
- implementation of information system information protection system;
- certification of information systems for information protection requirements (hereinafter - certification of information systems) and putting it into action;
- ensuring the protection of information during the operation of a certified information system;
- ensuring the protection of information during the decommissioning of a certified information system or after the decision to end information processing.
Few features
In many cases, GIS processes personal data, the protection of which must be provided in accordance with Federal Law 152 “On personal data”. How to act in such cases and what to put at the forefront?
This question is answered by the FSTEC in its informational message on the protection of information and ensuring the security of personal data when they are processed in information systems in connection with the publication of the order No. 17 of the FSTEC of Russia dated February 11, 2013 “On Approval of Requirements for the Protection of Information Not state secret contained in state information systems "and the order of the FSTEC of Russia of February 18, 2013 No. 21" On Approval of the Composition and Content of Organizational and Technical Measures to Ensure Security cite personal data at their processing in information systems of personal data "on July 15, 2013 № 240/22/2637. In this informational message, in view of the similarity of the measures, the FSTEC recommends combining and applying the measures contained in both orders. It is obvious that this procedure should be carried out at the stage of developing the information system information protection system.
And what about in practice? Problem and solution
For example, consider the case from our practice of placing GIS in the cloud. So, we have a task, it is necessary to improve the efficiency of information exchange without reducing the level of security and growth of non-core personnel of the regional segment of e-government infrastructure (RIEP) in one of our powerful and immense areas.
The typical regional segment of e-government infrastructure includes a system of regional interdepartmental electronic interaction, an automated system for executing regulations for the provision of services, a regional portal and registry of public services, identification and authentication systems, information and payment gateways and other elements.
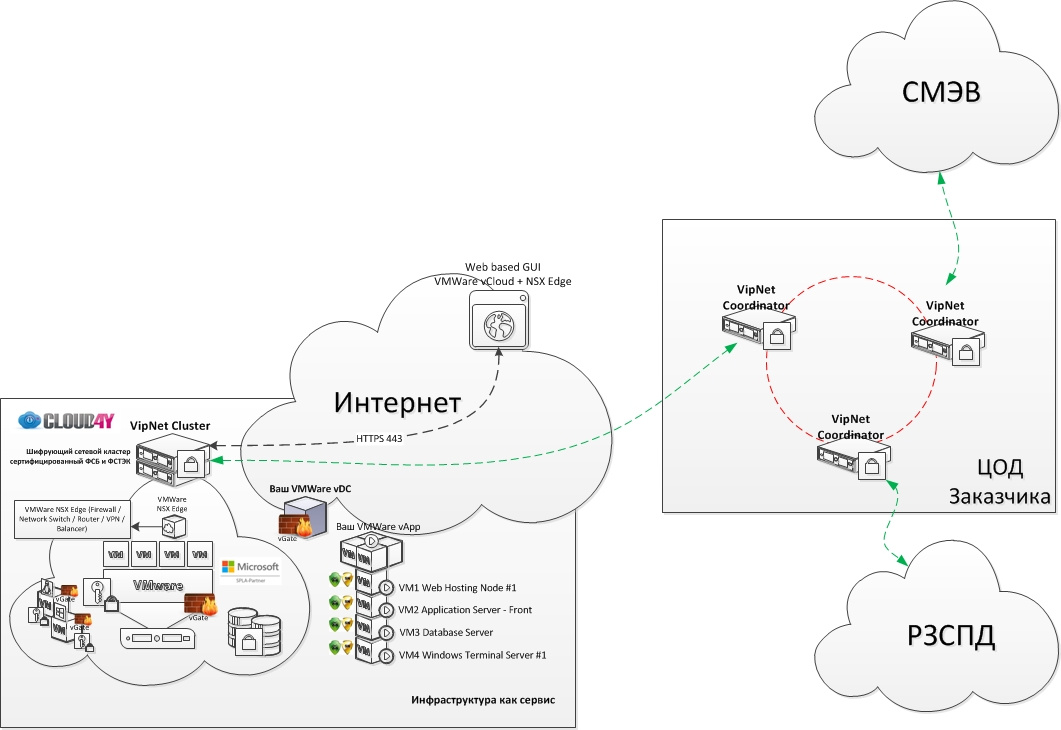
Due to the peculiarities of the functioning of the SMEV (the system of interdepartmental electronic interaction) , directly interconnected with RIEP, it was decided to leave the existing structure of the organization of communication with SMEV unchanged. And to reduce the costs of upgrading the server equipment necessary for the functioning of RIEP services, they were decided to be placed in the cloud infrastructure of the IaaS provider.
One of the problems with this is access of RIEP services from the data center of the provider to the SMEV. The protection of communication channels between the data center in which the cloud infrastructure is deployed and the data center with an expanded access gateway to the IWMS should correspond to the level provided by the documents regulating access to the IWMS. In this particular case, it was not necessary to reinvent the wheel and, relying on “Regulation 3.5 Appendix 4 Requirements for the data transmission network of information exchange participants” published on the SMEV technology portal, a satisfactory decision was made.
As a means of cryptographic protection of communication channels, the Infotecs product line was chosen. At the end points, the ViPNet Coordinator HW1000 software / hardware systems were installed. ViPNet Coordinator HW1000 is a security gateway for protecting enterprise-wide computer networks, which allows you to organize secure access to data centers and corporate cloud infrastructure, and supports the protection of high-speed communication channels up to 1 Gbit / s. These complexes have FSTEC certificates as a means of firewalling and an FSB certificate as a means of cryptographic protection of the KS3 level. The main features and benefits can be explored on the manufacturer's website .

Executed in the 1U form factor, it consumes a low amount of electricity, has a low level of heat generation and does not require any special conditions for placement and operation.
To organize secure communication channels, a fault-tolerant cluster of coordinators HW1000 was placed in the data center of the service provider. To increase the bandwidth of the communication channel and as an additional redundancy mechanism, aggregation of communication channels was set up. On the territory of the customer’s data center there is a single HW1000 coordinator included in the optical ring of the provider.
For the convenience of administration and delimitation of areas of responsibility, the tripartite interaction between the protected data transmission networks (DATS) was implemented without the organization of interworking. Those. within the controlled area, the exchange of traffic between crypto-gateways SMEV, channel DPC-DPC and regional ZSPD occurs in an open mode.
In general, the scheme of the protection system is shown in the figure.
Protection of the virtualization environment is based on GOST R 56938-2016 “Information security. Information security when using virtualization technologies. General provisions. ”In addition to the protection objects inherent in any automated system, the virtual infrastructure also contains specific objects specific to the virtualization environment.
These include:
- tools for creating and managing virtual infrastructure;
- virtual computing system;
- virtual storage system;
- virtual data channel;
- separate virtual devices for processing, storing and transferring data;
- Virtual tool ZI and tool ZI intended for use in a virtualization environment.
When providing services based on virtualization technologies, there is also a purely human problem called “superuser”. Administrator virtual infrastructure, in fact, everything is available.
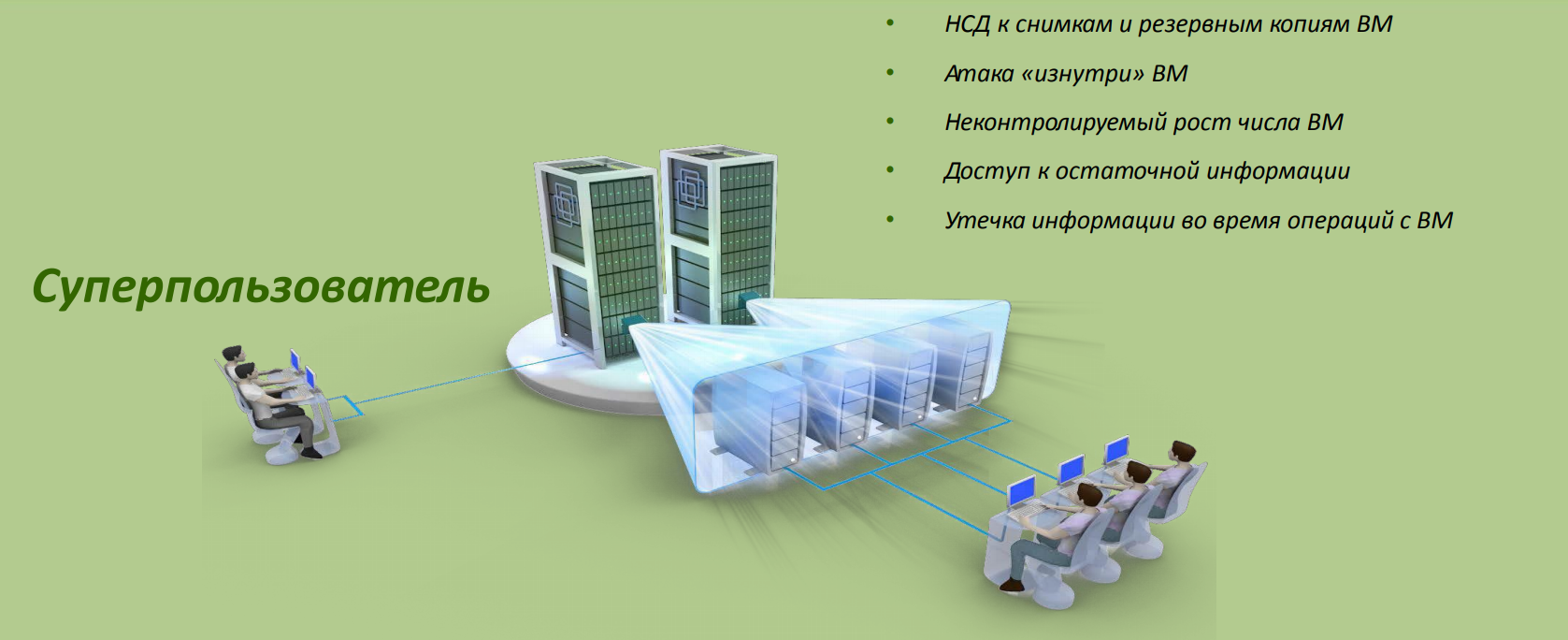
Vulnerability of virtual infrastructure. Slide from the presentation of vGate R2
Based on these prerequisites, to protect the virtualization environment, a company product was chosen Security Code - vGate R2. VGate implements a fully functional product on the VMware vSphere virtualization platform used in our cloud.
The product is actively developing and has many easy-to-use templates. In addition to the availability of certificates, this product is notable for a number of convenient features and capabilities that I would like to draw attention to, since they greatly facilitate the work on bringing the system into conformity:
- Built-in templates for setting policies for the protection of PDN and GIS;
- the possibility of segmentation of the infrastructure according to the types of protected data, the boundaries of information systems, groups of users without the need to make changes to the infrastructure itself;
- access control to infrastructure elements (discretionary and mandatory access control);
- additional log files of information security events;
- automatic alignment of the virtual infrastructure configuration to PCI DSS, VMware Security Hardening Best Practice, and CIS VMware ESX Server 3.5 Benchmark;
- coordination of the finished virtual machine at the information security administrator;
- prohibition of access by virtual infrastructure administrators to virtual machine data;
- reporting on information security events and configuration changes made;
- registration of attempts to access the infrastructure;
- integrity monitoring and trusted loading of virtual machines;
To solve the “superuser” problem, vGate implements the separation of user roles. Virtual infrastructure management is assigned to VM administrators, and security management is assigned to a security administrator.
And yet, which is important for us, the developers in the new version promise to add a new security template in accordance with GOST R 56938-2016, mentioned earlier.
The vGate architecture is shown below.

In addition to the means of protection from unauthorized access, all allowed traffic sent to the virtual machines is inspected for the presence of attack signatures by an intrusion detection system. As an IDS, the Infotecs product is also used. Hardware-software complex (PAK) ViPNet IDS is an effective and reliable system for detecting computer attacks (intrusions) into corporate information systems. The operation of the system is based on the dynamic analysis of network traffic, starting with the data link layer and ending with the application layer of the open systems interaction model. In this case, the choice was due to the uniformity of the solutions applied and the compatibility of the controls.
Of the various options for backup facilities certified by FSTEC, the choice fell on the proven Veeam. Veeam Backup & Replication provides efficient backup, replication, and recovery of virtualized applications and data. The solution performs fast and reliable backup of VMware virtual machines without the use of agents inside virtual machines. Veeam Backup & Replication speeds up the backup process and reduces the cost of data storage.
Naturally, cloud protection is not limited to the means listed. But in the light of the stated topic of the article, the applied non-certified solutions do not play a big role in assessing compliance with the requirements of legislation on the protection of GIS. But, of course, it will certainly be important for the final customer. As an example, there is no way yet a regulated service - DDoS protection .
Naturally, in this case questions of organizational measures and measures for protection implemented directly inside the virtual machines are also omitted. Nevertheless, this solution is based on certified information security tools, as required by law, and allows you to fully solve the problem of protecting GIS in the service provider's cloud infrastructure. In this example: the solution makes it possible to transmit confidential data via a communication channel protected by an IMSP that meets the requirements of the Federal Security Service of Russia for class KS3, and protect virtual machines from unauthorized access with the help of a certified vGate virtual environment protection tool, solving virtual infrastructure in compliance with the requirements of orders of FSTEC of Russia.
Why is the cloud?
In addition to the classic advantages of cloud technologies, placing GIS on the cloud service provider site allows customers to get rid of the headache of implementing security requirements in a virtualization environment. The service provider fully undertakes the implementation of protective measures for the entire cloud infrastructure. In addition, serious and responsible service providers, such as Cloud4Y;) are ready to provide the necessary means of protection, provide advice and make recommendations to comply with the information security requirements inside the customer's virtual machines. The most suitable finished product in our portfolio is Cloud FZ 152 , of course, it is possible to develop a solution specifically for the client’s requirements.
What should be considered when choosing a service provider to host a GIS?
To place a GIS on the provider's site, the cloud infrastructure of the provider must comply with the requirements for IP not lower than the customer’s IP class. The data on compliance is confirmed by the Certificate of compliance of the IS of the provider with the information security requirements issued by the licensee of FSTEC according to the results of certification tests.
The service provider imposes additional obligations regarding the organization of information security, in contrast to the traditional cloud. Such obligations include the use of information security tools certified by the FSTEC and / or the Federal Security Service of Russia, the presence of a FSTEC license for technical information protection activities. And in the case of the use of cryptographic protection of information, the service provider also needs an FSB license to distribute the means of cryptographic protection of information.
As you can see, the placement of GIS in the cloud of a third-party service provider is quite possible and also fits into the framework of the Russian legislation. Although this service is quite new in the market, but successfully implemented projects suggest that GIS in the cloud is a definite plus for the Customer in terms of convenience and cost.
Source: https://habr.com/ru/post/336384/
All Articles