System IEEE Software Taggant: protection against false positives antivirus

In this post I want to talk about the IEEE Software Taggant system, which was developed by the IEEE Malware Working Group in collaboration with leading information security companies.
The plans of the Guardant development team have long been to add support for the IEEE Software Taggant to Guardant Armor protector, and finally we did. A brief overview of the system and practical conclusions in front of you.
Why panic antivirus?
There is no such user who would not face the problem of the false alarm of the antivirus. The reaction of an ordinary person is often reduced to the removal of a “suspicious” file, which is often not only not harmful, but, on the contrary, useful and sometimes valuable. In turn, programmers, knowing about such jokes, can fall into irritation close to stress. Neither contributes to effective work.
Often, such operations occur on files protected by various protectors. The thing is that modern protectors use code obfuscation intensively. By obfuscation, I mean technology mutations and code virtualization, as well as their combination. Obfuscation is used to make it difficult to analyze source code for a certain number of methods and tools. It is the obfuscated areas of the code that cause the heuristic analyzer of the antivirus to panic.
')
A few years ago, a real battle broke out between antivirus companies and protectors. Losing, antiviruses decided to ban all packers that are not used in commercial and widely used software. Then even several well-known packers were banned. Over time, the situation returned to normal, but there is still no complete solution to the problem.
Constant development of obfuscation code, replacing the original code with pseudo-code, which is executed during the work of a protected application, seriously complicated the analysis and affected the performance when scanning protected files with antivirus. A wide variety of protectors used for legitimate as well as malicious purposes creates problems for the antivirus industry. A serious security threat is the use by authors of malicious code (trojans, viruses, etc.) protectors to hide their code from detection. This technique has become used on the server side (server polymorphism), as a result, it has become much more difficult to identify and counteract the threats of malicious code. Antiviruses are not able to determine what is actually inside a protected file and are forced to seek a balance between reliability and the complete absence of false positives on harmless programs.
Control the distribution of protected files
Heuristic analysis was invented by antivirus companies to detect new threats and, in part, is necessary for them to collect suspicious files. In our case, the probability of false positives is much higher, so antiviruses maintain white signature lists for commercial packers. This partly helps to improve the situation, but still leaves the antivirus to feel “with impunity”. Like "gods" playing dice, they are able to give out a harmless file as a virus. To justify their existence, antiviruses are forced to complicate the analysis and come up with additional control schemes. For protectors, they decided to implement a system of complete control over the distribution of protected files. The system allows you to block only files from unreliable publishers of protected software and show loyalty to files from trusted sources.
Antiviruses use digital signatures intensively to verify the authenticity of the file. Confirmed by well-known organizations, digital signatures provide a reliable way to track the source of a file. Such organizations are unlikely to sign the malicious code with their certificate. But not always a digital signature is enough. There are known cases of infection when the file contained a valid digital signature, because the virus was introduced at the compilation of the program. However, the responsibility for applying a digital signature lies with the user of the protector, and a high level of trust is required for the certificate issuer.
In 2010, the IEEE Malware Team began discussing how to develop a system — now called the IEEE Software Taggant — to help identify a particular tread user. The term “taggant” is borrowed from a system used for explosives, to which a chemical marker is added, traceable to, or even after, an explosion. The IEEE Software Taggant System embeds a cryptographic marker in the output executable file created by any protector installation. This allows identification of the unique protector license that was used to protect the file.
The emergence of the IEEE Software Taggant system was preceded by the practice of using “watermarks”. "Watermarks" contain encrypted license information. The most responsible protector developers include two sets of watermarks in the executable file. One to identify the protector, the second to uniquely identify the license. However, there is no single standard for using watermarks, and each developer of the tread is free to act.
According to the system developers themselves, the introduction of the new term “taggant” is ambiguous. On the one hand, this eliminates the use of the terms “watermark” and certificate, on the other hand, the IEEE Software Taggant system includes characteristics of both of these tools, although it is very different in terms of its scope and implementation.
Infrastructure
The IEEE Software Taggant is effective only if it is used simultaneously by both protector and antivirus. The system uses a public key infrastructure (PKI), while the root and trusted centers are controlled by IEEE. If you are a tread vendor, you need to register with IEEE to generate Software Taggant licenses. The license must be transparent to the users of the tread and integrated into the installer before selling.
Before releasing a new tread, vendors are advised to protect a representative sample of 10–20 files with different protection parameters and put it on a general review. Antiviruses, in turn, must ensure that there are no false positives of the heuristic analyzer. The reputation of the file with the Software Taggant should be higher than that of the file without it.
When a protected malware is detected with the Software Taggant token, the license with which the malware was protected becomes a candidate for blacklisting. The community recommends antiviruses to quickly exchange information to compile a complete list of blocked licenses.
Cryptographic marker
How does the Software Taggant differ from the usual digital signature Authenticode in Microsoft Windows?
The IEEE Software Taggant system allows the calculation of hash sums for small critical program areas to minimize software integrity checking time (Authenticode always covers the entire file, so the checking time depends on the file size). This is important for antiviruses, as it allows them to work in the quick scan mode. Another interesting thing is that if you have an Internet connection, a trusted timestamp of creating a marker is added (according to RFC 3161), which allows antiviruses to selectively supplement the blacklist (block software only after a certain moment of compromise).
According to the documentation, Taggant can be added not only to PE-format files. In the list of formats there are ELF and JavaScript. It is possible to add Taggant to any unstructured format.
For the PE format, the analogy with the Windows digital signature is traced. The taggant structure is written to the end of the PE file as an overlay. If there is an original overlay in the file, the structure is written after it. To calculate the hash sum, the SHA2-256 algorithm is used. The easiest way to add a Taggant to a PE file is to use a utility with the usual name SignTool.
Example:
> SignTool.exe SimpleTest-x86.exe license.pem
SignTool Application (adds Taggant v2 to files)
SPV Taggant Library version 2
Date is Sat Apr 03 23:59:59 2027
File hashes computed successfully
Put timestamp
Timestamp successfully placed
Prepare the taggant
Taggant successfully created
Taggant is written to file
Microsoft's digital signature does not conflict with Taggant, since is added after the taggant structure and covers the entire file, including the taggant.
Benefits
The IEEE Software Taggant system was developed as a specialized and universal solution for antiviruses and protectors, which certainly is an indisputable advantage over other file authentication methods. Antivirus get:
- the ability to identify a specific license used to generate malware. This allows you to blacklist individual licenses without blocking the entire protector.
- The ability to quickly identify the version and license of the packer, which are used in a well-defined safe mode, without the need to unpack files. This should improve file scanning performance.
- ability to identify modified file versions. Such files can be blacklisted.
- ability to track license history to enhance the reputation of a particular user of the protector.
All of these features should reduce the risk of false positives and improve performance when scanning protected files.
Testing
We hoped to reduce the false positives of antiviruses, because the system appeared quite a long time ago. But alas, the miracle did not happen. First, look at the results of VirusTotal:
Clean file:
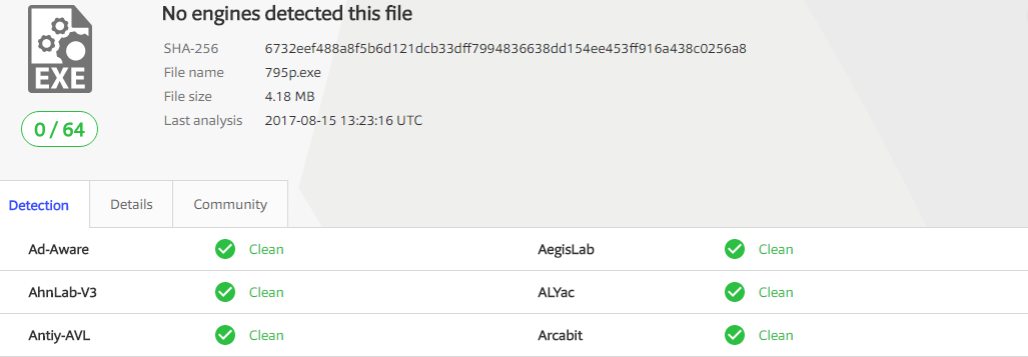
Protected file without taggant:
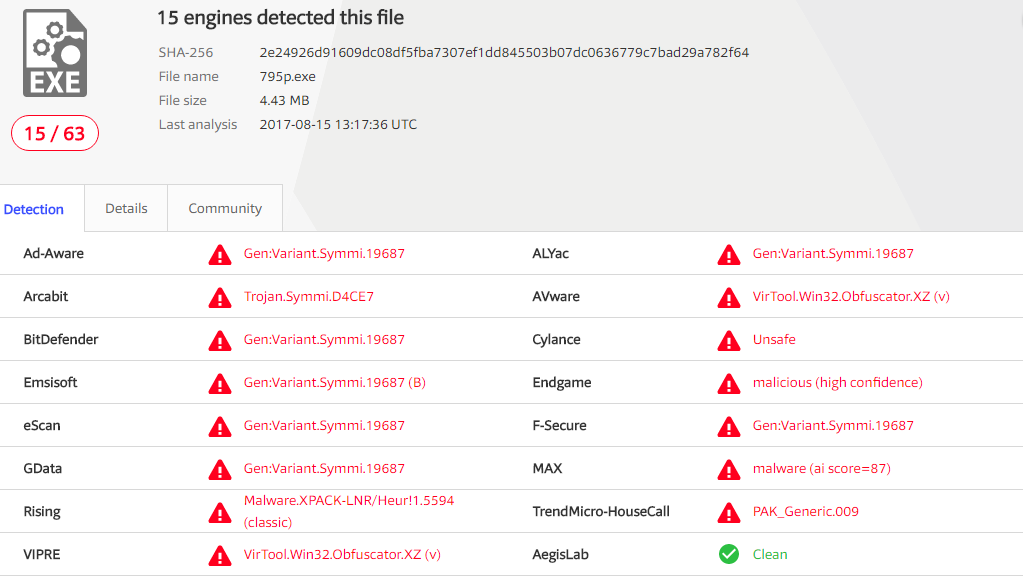
Protected file with Taggant:
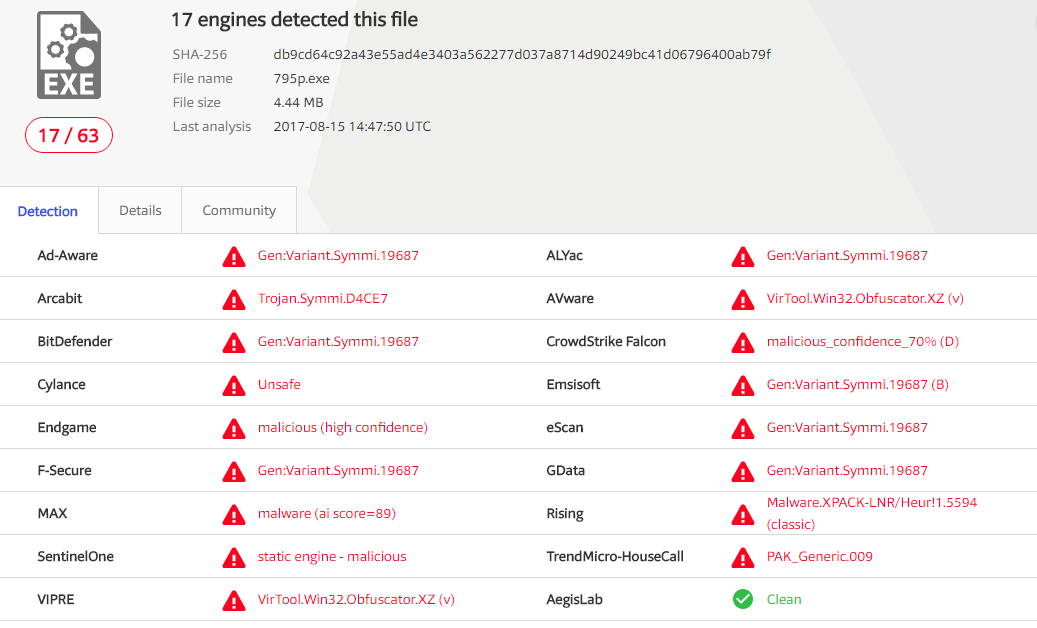
Secure Taggant file with Microsoft signature:

Little-known antiviruses do not react to the presence of the Taggant signature, they react more precisely, but vice versa. For them, the Microsoft signature is still an important argument.
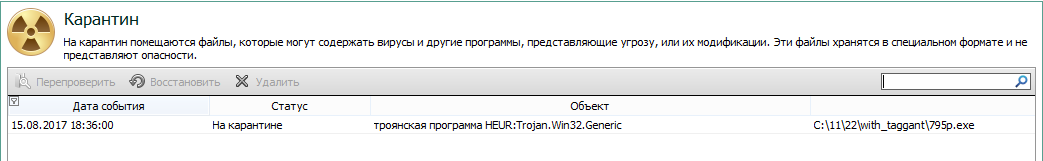
Upset us and Kaspersky Endpoint Security. It places this file in quarantine regardless of the presence of the Taggant signature and the Microsoft signature. As before, only turning off the heuristic analyzer helps. At the same time, the scan on VirusTotal by Kaspersky antivirus says that the file is clean.
Conclusion
Apparently, not all antiviruses are in a hurry to build Taggant support into their engines. IEEE bureaucracy is also a matter of concern. Correspondence with this organization took us a huge amount of time. A simple developer can get into the "white" lists of legal software distributors can be more difficult than using the Microsoft digital signature mechanism. Nevertheless, Taggant is a worthy alternative to watermarking, and we hope that the system will be gradually introduced. In the meantime, Microsoft's signature is a stronger argument for antiviruses.
References:
Source: https://habr.com/ru/post/336138/
All Articles