Security Week 33: Flash, bye bye, Chrome extensions steal traffic, Apple SEP firmware key is laid out
 No, you just think about this figure: 1033 ( one thousand and thirty-three ) vulnerabilities in Flash Player have been enforced since 2005! This is more than in Internet Explorer, more than in Windows XP - in general, “it is now good to discard the noodles through it” because the topic is closed .
No, you just think about this figure: 1033 ( one thousand and thirty-three ) vulnerabilities in Flash Player have been enforced since 2005! This is more than in Internet Explorer, more than in Windows XP - in general, “it is now good to discard the noodles through it” because the topic is closed .At one time, Flash Player was a real revolution for the web - thanks to him, animation was thundering on the websites, vidosiki flooded, whistles, games for secretaries at the reception, and, of course, killer banners (I wanted to hang a couple of examples here, but my eyes were twitching from the memories) . There were even sites completely made on a flash.
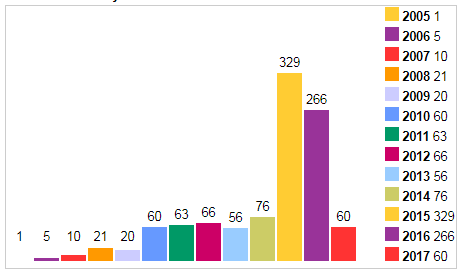 Most of all loved Flash "black hats". Fortunately, its vulnerability is a tradable commodity, and there has never been a shortage of them. The year 2015 was especially fruitful, when 329 new holes were counted in the “sieve”. But in 2010 Jobs warned that Flash should be put in the trash. And the main argument was his closeness. Well, yes, the head of Apple admitted that his company is full of its own proprietary standards, but not for the web! In this case, by the way, Adobe in every way impedes the emergence and development of alternative Flash players. As a result, we have free range for exploits, expanse for large and small horned malware.
Most of all loved Flash "black hats". Fortunately, its vulnerability is a tradable commodity, and there has never been a shortage of them. The year 2015 was especially fruitful, when 329 new holes were counted in the “sieve”. But in 2010 Jobs warned that Flash should be put in the trash. And the main argument was his closeness. Well, yes, the head of Apple admitted that his company is full of its own proprietary standards, but not for the web! In this case, by the way, Adobe in every way impedes the emergence and development of alternative Flash players. As a result, we have free range for exploits, expanse for large and small horned malware.Well, Flash Player also slows down on mobile devices, consumes the battery as if not in itself, and makes the platform vendor dependent on Adobe.
')
And after all Jobs warned us, when full flash web surfing was still impossible without flash support. As events developed further, we know. Flash on the Web is getting smaller, HTML5 is getting bigger. And over the past three years, the outcome process has gained almost free fall acceleration - from 80% of users who visit Flash sites daily in 2014, to 17% in 2017 (data on Chrome desktop users).
 Now Adobe has recognized the inevitable. By the end of 2020, Flash Player support will be discontinued, Flash developers have been
Now Adobe has recognized the inevitable. By the end of 2020, Flash Player support will be discontinued, Flash developers have been However, not everyone agrees with natural selection, as is usual among people. Developer Juha Lindstedt, for example, organized on GitHub a petition to Adobe not to kill Flash, but to transfer the code to the open source community, and they will continue to care and cherish it there. Otherwise, a large layer of the history of the Internet will go into oblivion and all that. Especially a pity, of course, Flash games (actually not).
Hacked Chrome extensions steal ad traffic and replace ads
News Seven. No, already eight extensions in Chrome have been replaced by some bastards. Proofpoint revealed a simple scheme: hackers send phishing emails to extension developers, and if they manage to get the credentials from Google services, they inject their code into the extension and upload it to the store instead of the real one.
List of compromised extensions:
Web Developer 0.4.9
Chrometana 1.1.3
Infinity New Tab 3.12.3
CopyFish 2.8.5
Web Paint 1.2.1
Social Fixer 20.1.1
TouchVPN
Betternet VPN
Chrometana 1.1.3
Infinity New Tab 3.12.3
CopyFish 2.8.5
Web Paint 1.2.1
Social Fixer 20.1.1
TouchVPN
Betternet VPN
It is curious that hackers on behalf of the Google Chrome Web Store Team even frightened developers - they say that your extension violates everything that can and will be thrown out of the store, and if you need more details - here is your link. The link, of course, was a fake Google login page.
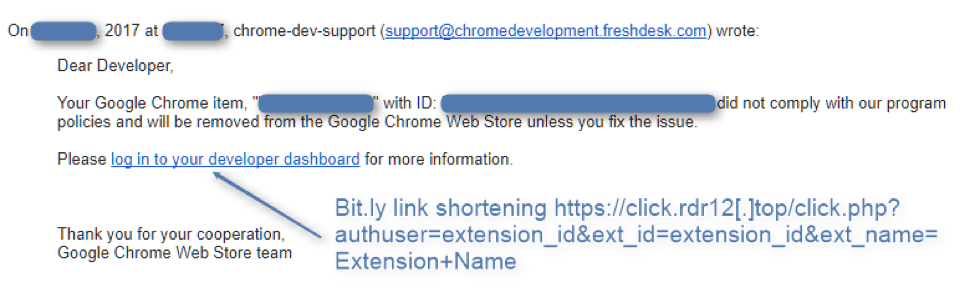
If the developer didn’t pay attention to the address from which the letter came (from which Google uses Freshdesk?), Or to the address of the login page, then the credentials flowed to the dashing guys. An extension with embedded malicious code has spread across users through the update mechanism.
After launching the extension, the HTTPS code pulled the js file from the management and control server, and the domain was generated on the fly. And then the user roamed the Internet as usual, only clicks on banners brought him to completely different sites. But this, however, is not the most disgusting. Sometimes the victim fell js-alert, saying that her computer is infected (and in fact did not lie, devils)! The click on the alert led to where it is known - on the page with Malvar.
The effectiveness of this campaign is not very clear, however, Alexa shows that the attendance of such sites has grown from zero for hundreds of thousands over the last month. It may, of course, not only because of the hacked extensions.
In addition to these malverting outrages, extensions are trapping the credentials of Cloudflare. According to Proofpoint, hackers thus prepare subsequent attacks with the circumvention of the protection of Cloudflare sites.
Hacker has published the key to the firmware Apple SEP
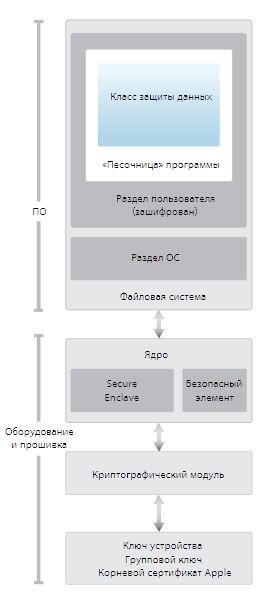 News Someone xerub took and laid out something that, according to him, is the key to decipher the firmware of the cryptographic co-processor Secure Enclave Processor in Apple chips. I must say that this is a secret thing, where iOS stores encryption keys and processes data from the Touch ID sensor.
News Someone xerub took and laid out something that, according to him, is the key to decipher the firmware of the cryptographic co-processor Secure Enclave Processor in Apple chips. I must say that this is a secret thing, where iOS stores encryption keys and processes data from the Touch ID sensor.Apple has not yet admitted that the key is real. However, she hastened to declare that even if it is not a fake, there is no threat to user data. Most likely, this is true, but not all. Not just because the company hid all the details about the firmware SEP. Decrypted firmware can be explored and found vulnerabilities there. And without them, software is harder than “hello world”.
SEP has its own operating system, which, because of its total closeness and encryption, has been doing all this time without basic protection technologies, such as memory randomization. This will greatly facilitate the creation of an exploit if vulnerabilities are found. So if Cherub did not lie, Apple should hurry up with the completion of the SEP firmware - it seems that the race has started.

Antiquities
"Tetris-552"
Resident very dangerous virus. Standardly written to COM and OVL files when loaded into memory. When opening .PRG files, it writes a “?” PLAY TETRIS, HI-HI-HI ”command to their beginning. Intercepts int 21h.
Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 84.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/335928/
All Articles