A bit of the history of cryptography CCPP: M-105, codenamed Agat
The history of cryptography is rooted in the time of Ivan the Terrible. The first cryptographers used simple replacement ciphers, and later, under Peter the Great, professional services involved in the encryption business began to appear. In the middle of 1700, so-called “black cabinets” appeared - secret rooms in post offices, where envelopes with letters were opened safely (sometimes not very well). There was a concept - "perusal".

Cabinet perusal at the post office in the Russian Empire
In the history of the national cryptography of the times of the USSR many gaps were formed, since the information was under seven locks, strictly kept secret. Some moments are covered in the article the treasury of national cryptography , it also mentioned the most famous Soviet cryptomachines.
')
M-105 (code name: Agat) is a Russian, autonomous encryption machine that was developed and created in the USSR in the late 1960s. The predecessor of this cryptomachine was almost identical to M-104 (Amethyst and Amethyst-2). Such machines were used by all the Warsaw Pact countries (GDR, Czechoslovakia, Hungary, Romania, Yugoslavia), they were text-based electromechanical encoders with paper tape recording: SM-1 Cornflower, SM-2, M-104 Amethyst, M-105 Agat , M-125 Violet , M-130 Coral.

SM-1 Cornflower

M-104 Amethyst

M-105 Agate
M-125 Violet

M-130 Coral
M-105 Agate is a cryptomachine in which OTT was used - One-Time-Tape encryption, the essence of such encryption is simple: the key used is one-time and is equal in length to the transmitted data, the text is encrypted and no one can decrypt it.
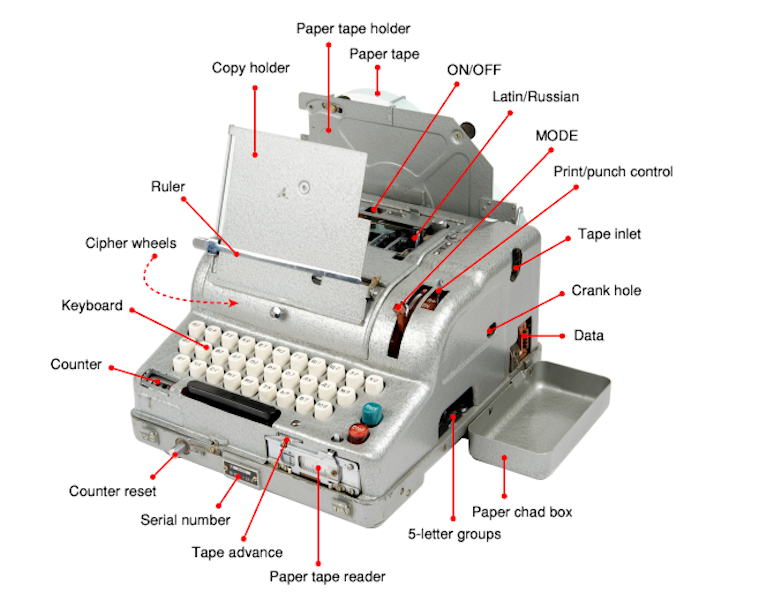
Unlike Violets, in which 10 encryption wheels (rotors) were used to generate the key, the M-105 has a built-in mechanical key generator that outputs random keys to an 11-layer punched tape. It is located at the top of the machine.

At first glance, the car is somewhat reminiscent of M-125 Violet. The electric car, almost the same size, is painted in silver gray with a keyboard in Latin / Cyrillic. But this is where the similarities end.
M-105 printed the results directly onto a piece of paper that was in the carriage at the back. The advanced matrix printhead allows you to print any of the 30 characters (5 x 6). Depending on the language used for printing, some characters or numbers could be missing.
There was a device for inserting punched tape and key entry (standard 5-level punched tape) on the right to the right, although the Bodo code was not used.
Instead, the same coding scheme was used as in Violet. In front of the M-105 was a paper punched tape reader. The punched tape was guided through a ruler, which ran across the entire width of the machine. To start and stop - two keys (Start, Stop), located on the front right.

The image below shows the location of the full keyboard: on each key there is a Cyrillic and Latin letter. 30 keys, a black one-step key at the bottom left and a black control character for the return of the CR / LF cutter at the bottom right, there is a space (at the bottom).

In encryption mode, a space was used when entering text, and the H2 key was locked. In decryption mode, the opposite is true: the space bar is locked, the H2 key is available. When the device was used in plain text mode (MODE is set to “O”), it was possible to use either the space bar or the Y2 key. Two black keys (“step” and CR / LF) are not encrypted. They only worked in text mode to format the output. The missing “Y” can be easily replaced by “I”. Identical to Violet, on the M-105 keyboard there are only 30 most used letters.
Punctuation marks - except for the SPACE symbol using the “” key in the upper left corner — no. Switching between Latin and Cyrillic alphabet meant replacing the print head.
The punched tape could be used for encryption only once, therefore, when switching modes of operation, a Control Hole was punched through. Decryption-only punched tapes had Check Hole so that they were not randomly used as an encryption key.

There is a black rotary knob on the front left, just above the keyboard. With it, you can select the desired mode of operation: “O” for typing (Clear text), “3” for encryption (encrypt) and “P” for decryption (decrypt).

In text mode, the M-105 functioned like a regular typewriter or teleprinter and was used to print text, create 5-level punched tapes (5 holes per line). All keys were available, including the space bar, CARE STEP and CR / LF.
When setting encryption modes (3) or decryption (P), a number of mechanical changes took place inside the device. As it was written earlier, in the encryption mode the X2 key is locked, a space is available, in the decryption mode - the opposite is true.
The abbreviations used for different modes are identical for all machines (M-125 or M-130), as shown below.


On the front of the 11-level key reader is a lever with three possible settings: P, PC, and K. It was used to select the recipient (punch, printer, punch and printer) of encoded, decoded, or plain text output.

There were several versions of the M-105, the most common - the device was powered from a 24 V direct current source.

Specially, for connection to the 110 V DC network, a different version of the AGAT was available.



The standard power supply, which was used in the M-105, was suitable for networks of any voltage level (as a rule, in the voltage range 110 - 220 V), could be used almost anywhere in the world. The same power supply was used with the M-125 Violet in most Warsaw Pact countries.

The lever performed several functions. With it, you can work with the machine manually in case of power failure. Since the encryption process was purely mechanical, the machine could read 5-level punched tapes, ribbons with keys, print on paper and without electricity. The lever was also used to “reset” the mechanism if it was jammed.

Lever arm
In M-105, a 5 x 6 matrix (5 rows, 6 columns) was used to address 30 characters. Each 5-bit character was translated into a string (6 bits) and a column (5 bits), as a result, 11 internal “bits” were obtained, therefore the key punched tape is an 11-level one.
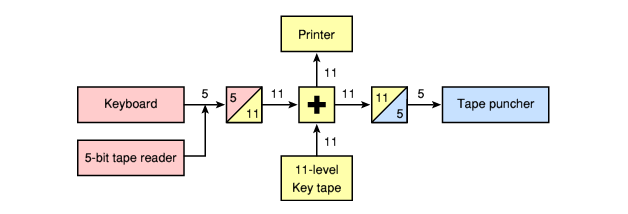
The 11-bit code from the key punched tape was added to the 11-bit data stream, the result was later converted back to a 5-digit digital code (displayed on five-level punched cards).

In East Germany (DDR), the M-105 was commissioned in 1968 and used to communicate with partner countries of the Warsaw Pact, as well as the leadership of the GDR, to exchange messages at the highest level of government.
In 1986, the M-105 became a fully electronic M-205 D machine, but many M-105 remained in operation until the German reunion. M-105 was replaced by T-353 (Dudek) in 1987 for communication of the GDR with Hungary.

T-353 (Dudek)
It is extremely difficult to find materials about this cryptomachine on the Runet’s open spaces, because the information was taken here: Crypto museum and bplaced.net . Most likely, such scant public coverage of advances in the field of cryptography of the USSR times is due to a number of reasons: only partial declassification, underfunding and other problems. Let's hope that soon the domestic scientific achievements and outstanding cryptographers of the country will come out from under the neck “top secret”.
As advertising. Stock! Only now get up to 4 months of free use of VPS (KVM) with dedicated drives in the Netherlands and the USA (configurations from VPS (KVM) - E5-2650v4 (6 Cores) / 10GB DDR4 / 240GB SSD or 4TB HDD / 1Gbps 10TB - $ 29 / month and above, options with RAID1 and RAID10 are available) , a full-fledged analogue of dedicated servers, when ordering for a period of 1-12 months, the conditions of the promotion are here, existing subscribers can receive a 2-month bonus!
How to build the infrastructure of the building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?

Cabinet perusal at the post office in the Russian Empire
In the history of the national cryptography of the times of the USSR many gaps were formed, since the information was under seven locks, strictly kept secret. Some moments are covered in the article the treasury of national cryptography , it also mentioned the most famous Soviet cryptomachines.
')
M-105: Codenamed Agat
M-105 (code name: Agat) is a Russian, autonomous encryption machine that was developed and created in the USSR in the late 1960s. The predecessor of this cryptomachine was almost identical to M-104 (Amethyst and Amethyst-2). Such machines were used by all the Warsaw Pact countries (GDR, Czechoslovakia, Hungary, Romania, Yugoslavia), they were text-based electromechanical encoders with paper tape recording: SM-1 Cornflower, SM-2, M-104 Amethyst, M-105 Agat , M-125 Violet , M-130 Coral.

SM-1 Cornflower

M-104 Amethyst

M-105 Agate

M-125 Violet

M-130 Coral
M-105 Agate is a cryptomachine in which OTT was used - One-Time-Tape encryption, the essence of such encryption is simple: the key used is one-time and is equal in length to the transmitted data, the text is encrypted and no one can decrypt it.
Unlike Violets, in which 10 encryption wheels (rotors) were used to generate the key, the M-105 has a built-in mechanical key generator that outputs random keys to an 11-layer punched tape. It is located at the top of the machine.

At first glance, the car is somewhat reminiscent of M-125 Violet. The electric car, almost the same size, is painted in silver gray with a keyboard in Latin / Cyrillic. But this is where the similarities end.
M-105 printed the results directly onto a piece of paper that was in the carriage at the back. The advanced matrix printhead allows you to print any of the 30 characters (5 x 6). Depending on the language used for printing, some characters or numbers could be missing.
There was a device for inserting punched tape and key entry (standard 5-level punched tape) on the right to the right, although the Bodo code was not used.
The Bodo code is a uniform 5-bit telegraph code using two different electrical signals.
Instead, the same coding scheme was used as in Violet. In front of the M-105 was a paper punched tape reader. The punched tape was guided through a ruler, which ran across the entire width of the machine. To start and stop - two keys (Start, Stop), located on the front right.

The image below shows the location of the full keyboard: on each key there is a Cyrillic and Latin letter. 30 keys, a black one-step key at the bottom left and a black control character for the return of the CR / LF cutter at the bottom right, there is a space (at the bottom).

In encryption mode, a space was used when entering text, and the H2 key was locked. In decryption mode, the opposite is true: the space bar is locked, the H2 key is available. When the device was used in plain text mode (MODE is set to “O”), it was possible to use either the space bar or the Y2 key. Two black keys (“step” and CR / LF) are not encrypted. They only worked in text mode to format the output. The missing “Y” can be easily replaced by “I”. Identical to Violet, on the M-105 keyboard there are only 30 most used letters.
Punctuation marks - except for the SPACE symbol using the “” key in the upper left corner — no. Switching between Latin and Cyrillic alphabet meant replacing the print head.
The punched tape could be used for encryption only once, therefore, when switching modes of operation, a Control Hole was punched through. Decryption-only punched tapes had Check Hole so that they were not randomly used as an encryption key.

Switching modes
There is a black rotary knob on the front left, just above the keyboard. With it, you can select the desired mode of operation: “O” for typing (Clear text), “3” for encryption (encrypt) and “P” for decryption (decrypt).

In text mode, the M-105 functioned like a regular typewriter or teleprinter and was used to print text, create 5-level punched tapes (5 holes per line). All keys were available, including the space bar, CARE STEP and CR / LF.
When setting encryption modes (3) or decryption (P), a number of mechanical changes took place inside the device. As it was written earlier, in the encryption mode the X2 key is locked, a space is available, in the decryption mode - the opposite is true.
The abbreviations used for different modes are identical for all machines (M-125 or M-130), as shown below.


On the front of the 11-level key reader is a lever with three possible settings: P, PC, and K. It was used to select the recipient (punch, printer, punch and printer) of encoded, decoded, or plain text output.
Power Supply

There were several versions of the M-105, the most common - the device was powered from a 24 V direct current source.

Specially, for connection to the 110 V DC network, a different version of the AGAT was available.



The standard power supply, which was used in the M-105, was suitable for networks of any voltage level (as a rule, in the voltage range 110 - 220 V), could be used almost anywhere in the world. The same power supply was used with the M-125 Violet in most Warsaw Pact countries.

The lever performed several functions. With it, you can work with the machine manually in case of power failure. Since the encryption process was purely mechanical, the machine could read 5-level punched tapes, ribbons with keys, print on paper and without electricity. The lever was also used to “reset” the mechanism if it was jammed.

Lever arm
In M-105, a 5 x 6 matrix (5 rows, 6 columns) was used to address 30 characters. Each 5-bit character was translated into a string (6 bits) and a column (5 bits), as a result, 11 internal “bits” were obtained, therefore the key punched tape is an 11-level one.

The 11-bit code from the key punched tape was added to the 11-bit data stream, the result was later converted back to a 5-digit digital code (displayed on five-level punched cards).

In East Germany (DDR), the M-105 was commissioned in 1968 and used to communicate with partner countries of the Warsaw Pact, as well as the leadership of the GDR, to exchange messages at the highest level of government.
In 1986, the M-105 became a fully electronic M-205 D machine, but many M-105 remained in operation until the German reunion. M-105 was replaced by T-353 (Dudek) in 1987 for communication of the GDR with Hungary.

T-353 (Dudek)
It is extremely difficult to find materials about this cryptomachine on the Runet’s open spaces, because the information was taken here: Crypto museum and bplaced.net . Most likely, such scant public coverage of advances in the field of cryptography of the USSR times is due to a number of reasons: only partial declassification, underfunding and other problems. Let's hope that soon the domestic scientific achievements and outstanding cryptographers of the country will come out from under the neck “top secret”.
As advertising. Stock! Only now get up to 4 months of free use of VPS (KVM) with dedicated drives in the Netherlands and the USA (configurations from VPS (KVM) - E5-2650v4 (6 Cores) / 10GB DDR4 / 240GB SSD or 4TB HDD / 1Gbps 10TB - $ 29 / month and above, options with RAID1 and RAID10 are available) , a full-fledged analogue of dedicated servers, when ordering for a period of 1-12 months, the conditions of the promotion are here, existing subscribers can receive a 2-month bonus!
How to build the infrastructure of the building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Source: https://habr.com/ru/post/335904/
All Articles