The return of Locky and Mamba: users are attacking new versions of encryption viruses
In the past few months, the world has faced a whole epidemic of ransomware attacks: private users, companies and organizations in different countries were attacked by the malware WannaCry, Petya and LeakerLocker. Last year, the encryption virus Mamba and the extortioner Locky became their predecessors - and now, as The Hacker News reports , their developers have released new, “improved” versions of their software.
Diablo6: new version of the virus Locky
In 2016, the Locky virus attacked thousands of users who were sent phishing emails - upon clicking on an attachment, a virus was activated that encrypted files on the computer and demanded a request to pay ransom in bitcoins. The virus then returned several times - its new versions were distributed using the Necurs and Dridex botnets.
')
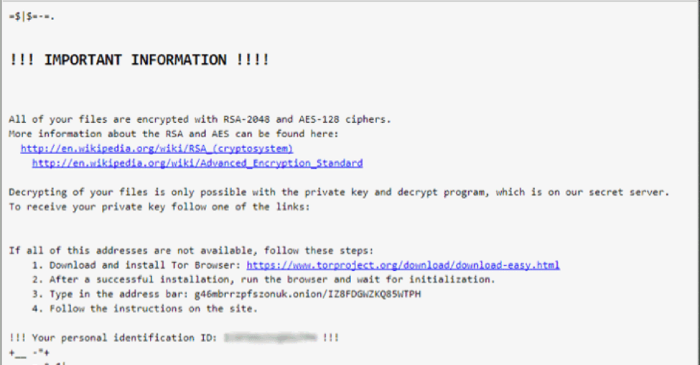
This time, researchers have discovered a mass mailing of spam letters, aimed at distributing a new version of Locky called Diablo6. Letters are sent to users in different countries, but the United States suffered the most from the attack, with Austria in second place in the number of attacked vehicles.
For the first time, a new virus attack wave was noticed by an independent security researcher under the nickname Racco42 - he said that the malware encrypts all files on the hard drive, adding the .diablo6 extension to them. The virus is delivered to the victim's computer under the guise of a Word document attached to a phishing email - after clicking on the attachment, the VBS Downloader script is activated, which downloads the virus code from a remote file server. The virus encrypts files using the RSA-2048 key, then a message is displayed for the user - it explains how to download the Tor browser to access the virus developers' website for instructions on how to pay a ransom of 0.49 bitcoins (more than $ 2100) to unlock.
There is currently no tool for unlocking files on computers attacked by Diablo6, so users need to be careful when opening email attachments.
Mamba Encryption Return
Another well-known extortionist virus, which affected not only ordinary users, but also many organizations, also returned. Last year, the Mamba virus, which encrypts not only individual files, but the entire disk, infected the computers of the San Francisco Municipal Railway (MUNI) - this led to large-scale traffic disruptions, and ticket machines did not work at some stations.

Researchers from Kaspersky Lab discovered a new campaign to spread the Mamba virus - this time corporate networks in different countries were hit. The largest number of infections recorded in Brazil and Saudi Arabia. Mamba uses legitimate open source software to encrypt disks on Windows computers called DiskCryptor. This tool uses strong encryption algorithms, so there is no way to decrypt disks of computers attacked by Mamba.
Researchers suggest that the introduction of the virus into corporate networks occurs through sending phishing emails, including malicious attachments, or using compromised and fake sites that host exploits. After the virus encrypts the drive, a message is displayed containing an email address to which you need to write for receiving unlock instructions.
How to protect against encryption viruses
Since often, as in the cases described above, there is no way to decrypt data encrypted by a virus, users should try to prevent an attack by following simple security principles.
- You do not need to click on attachments in suspicious emails from unknown senders, nor do you need to follow links in such messages.
- It is necessary to conduct regular backups: if a virus has attacked a computer, then the easiest way can be to restore files from a backup on an external drive. The backup disk should not be connected to the computer all the time.
- You need to regularly update your antivirus software and use additional protection methods - for example, corporate networks can be protected using specialized tools such as security scanners. For example, MaxPatrol can detect vulnerabilities leading to a Petya virus attack, and corresponding correlations are present in MaxPatrol SIEM .
Positive Technologies experts published recommendations for protecting against attacks of the WannaCry virus , told how to protect themselves against how to protect against #NotPetya, and also presented a method for recovering data from the disk they encrypted (give a hyperlink).
Source: https://habr.com/ru/post/335794/
All Articles