Mamba: open-source crypto-fiber
At the end of 2016, public transport passengers of San Francisco noticed a laconic message on the information monitors instead of the timetable: “All data is encrypted”. So for the first time the crypto-fiber Mamba declared itself publicly. After that, the cryptographer seems to have gone to the bottom, but the other day he appeared again. This time, organizations in Brazil and Saudi Arabia were attacked.
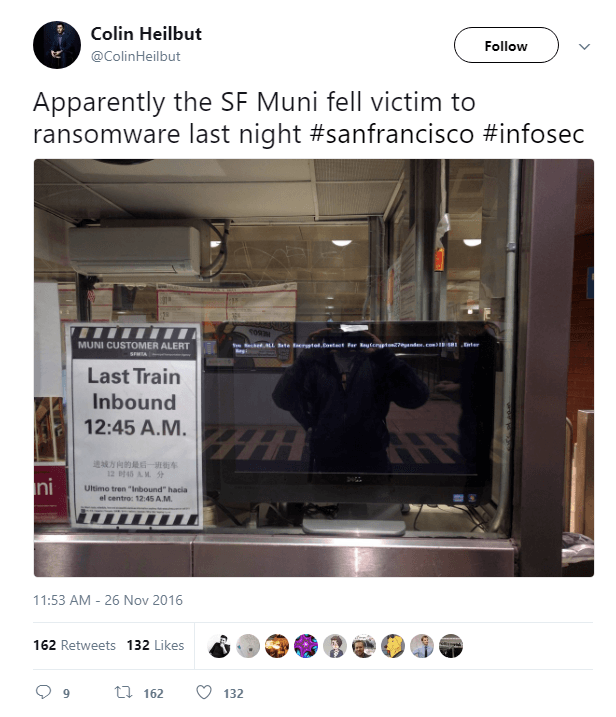
Mamba is notable for the fact that its authors did not bother with the home-grown implementation of encryption, but simply used the open source utility DiskCryptor. Operators of Mamba penetrate into the network of the organization and launch the crypto-fiber utility psexec. For each machine on the network, a separate encryption password is generated, which is transmitted via the command line parameters to the Tropper’s dropper.

The data attack process can be divided into two stages:
Stage 1 - preparation:
')
1. The directory “C: \ xampp \ http“ is created.
2. DiskCryptor is written to the directory.
3. The system installs the DiskCryptor driver.
4. The system registers the service DefragmentService.
5. The system reboots.
Pay attention to the step of writing components DiskCryptor. Dropper Mamba installs a 32- or 64-bit version depending on the system capacity.

The driver is installed is not very surprising - with the installer DiskCryptor.

After that, the Trojan creates a service with the parameters SERVICE_ALL_ACCESS and SERVICE_AUTO_START.

And at the end Mamba performs a forced reboot.

Stage 2 - Encryption:
1. A boot loader is written to the MBR of a disk, and DiskCryptor encrypts the logical disks.
2. Cleaning the system.
3. The system reboots.
The bootloader in the MBR is installed using DiskCryptor.

The bootloader has a requirement to contact extortionists.

Finally, the Trojan calls DiskCryptor to encrypt a disk with a password, transmitted via a command line parameter.

After the reboot, the victim sees the message of the ransomware.

Decryption without a password is not possible - DiskCryptor uses strong encryption algorithms. Our products will detect Mamba as PDM: Trojan.Win32.Generic, infection indicator 79ED93DF3BEC7CD95CE60E6EE35F46A1.

Mamba is notable for the fact that its authors did not bother with the home-grown implementation of encryption, but simply used the open source utility DiskCryptor. Operators of Mamba penetrate into the network of the organization and launch the crypto-fiber utility psexec. For each machine on the network, a separate encryption password is generated, which is transmitted via the command line parameters to the Tropper’s dropper.

The data attack process can be divided into two stages:
Stage 1 - preparation:
')
1. The directory “C: \ xampp \ http“ is created.
2. DiskCryptor is written to the directory.
3. The system installs the DiskCryptor driver.
4. The system registers the service DefragmentService.
5. The system reboots.
Pay attention to the step of writing components DiskCryptor. Dropper Mamba installs a 32- or 64-bit version depending on the system capacity.

The driver is installed is not very surprising - with the installer DiskCryptor.

After that, the Trojan creates a service with the parameters SERVICE_ALL_ACCESS and SERVICE_AUTO_START.

And at the end Mamba performs a forced reboot.

Stage 2 - Encryption:
1. A boot loader is written to the MBR of a disk, and DiskCryptor encrypts the logical disks.
2. Cleaning the system.
3. The system reboots.
The bootloader in the MBR is installed using DiskCryptor.

The bootloader has a requirement to contact extortionists.

Finally, the Trojan calls DiskCryptor to encrypt a disk with a password, transmitted via a command line parameter.

After the reboot, the victim sees the message of the ransomware.

Decryption without a password is not possible - DiskCryptor uses strong encryption algorithms. Our products will detect Mamba as PDM: Trojan.Win32.Generic, infection indicator 79ED93DF3BEC7CD95CE60E6EE35F46A1.
Source: https://habr.com/ru/post/335704/
All Articles