Blocking operations as malware protection

Not so long ago, a report by Google engineer Darren Bilby, “Gibson Protection in the Age of Enlightenment,” devoted to the antivirus file and other useless methods of information security, appeared on the network.
In a nutshell, it is about the fact that hacked mailboxes became the key topic of the pre-election presidential debate, that the ransomware Trojans encrypt files on corporate computers, and "toasters control large parts of the Internet" (perhaps, under "toasters" Darren had the kind of video camera surveillance, which zaddosili one of the largest DNS-providers).
')
And what does the computer security industry do against these cyber attack methods? Yes, almost nothing new, states Bilby, all the same poor and inefficient old tools. In his opinion, the sellers of such solutions simply “push magic” by hanging noodles on the ears of naive buyers.
What, in fact, offers us a classic antivirus? In the overwhelming majority of file scanners for virus detection by signature and heuristic analyzer for files against which the scanner is powerless (for example, compressed or encrypted). Each of these methods has its own advantages and disadvantages, but in general, Bilby is right, outdated technology has been used for many years, and on the other hand, it is also quite difficult to offer something fundamentally new. But you can. For example, over the past decade, sandboxes have been developed, but they haven’t earned much attention for certain reasons, perhaps due to maintenance difficulties, because the mass solution should be simple as a frying pan and reliable as scrap. Everything ingenious is simple, though not everything simple is ingenious.
The virus does not appear on the computer from where it does not take, it comes to visit with the file downloaded from the Internet or received by mail. That is, “there was a file first” and nothing but a file, and the spirit of the virus resides in it and waits for this file to be launched in order to start the winning march and “fulfill the will of the one who sent me.”
It turns out that any new file is potentially dangerous and protecting yourself from new files will protect you from viruses. But if we talk about a spherical computer in a vacuum, in real life it is impossible to protect oneself from new files, for the reason that creating new files is a natural process of computer functioning. Hence, from the whole mass of files, it is necessary to somehow select the "bad", potentially dangerous.
Certainly, only those that are capable of launching can be classified as virus files; executable or interpretable. It is understandable, what is the use of the virus lying in a text file? Evil should work, not peacefully snuffle in temporary folders.
For example, you downloaded the game and want to play it, but when you start the "game" suddenly begins to create other executable files and place them in the startup section. On the face of the actions of a malicious character, it is necessary as soon as possible to nip them at the root and the invasion will end without even starting. This is what a modern antivirus should offer - preventive protection that will protect against the virus, encryptor, trojan, worm ... and anything.
But at the same time, it is not necessary to forbid everything and everyone to the right and left, since for the normal operation of the operating system it also needs to create files, and sometimes even executables. And since the operating system is not a priori infected, it is possible to trust the work of all its mechanisms, it makes no sense to check what is created by its means. This also includes software products of famous (and not so) brands that you trust, i.e. exclude from the scan "trusted programs" obtained from reliable sources.
So, what happens is that to protect against the threat, there is no need to scan and analyze anything; you need a solution that restricts operations on certain files in certain places, since It is logical to assume that for the “work” the virus will select an available temporary folder, and not the root directory of Windows. Well, it’s nice to be able to exclude trusted applications from scanning.
It would seem that the solution lies on the surface, but for some reason, there are practically no popular blocking programs among mastodons, therefore, applications that are currently little known to the general public, but despite this, do an excellent job with this task.
Today I want to introduce you to the most interesting products in my opinion that meet the requirements described above, these are VoodooShield from the American company VoodooSoft, SecureAPlus from the Singapore-based SecureAge Technology, and also the Russian Defendset from the Krasnoyarsk company VTB. Initially, I managed to find another Russian program - the St. Petersburg Protection System Pantsir, unfortunately the demo version of Pantsir could not be downloaded, the developers require you to send a special form on the company's letterhead, stamped with the company and signed by the responsible person. Since I have no organization, no forms, no printing, we could not include this product in the review, which is a pity. Perhaps in the future it will be possible to get this utility, but for now let's look at today's participants and examine what they are, and most importantly, how to cope with the stated tasks.
VoodooShield
VoodooShield is a utility that blocks the launch of new applications and unknown objects that may contain malware. Before installing, it is important to make sure that there are no malicious objects on the computer; otherwise, they can be added to the number of trusted objects and will function completely officially.
The product is available in two versions - free, with limited settings and full-featured, at a price of $ 19.99 per year. Product site: https://voodooshield.com
The installation process of the antivirus itself is quite familiar; after the welcome window appears and before the installation is completed, the user does not have to take any action.

Immediately after installation, the program offers to choose in which mode the protection should be performed. "Autopilot" provides the program itself to assess the level of danger of applications being launched, and the "White List" ensures the launch of only those applications that are included in this list.
Mode selection window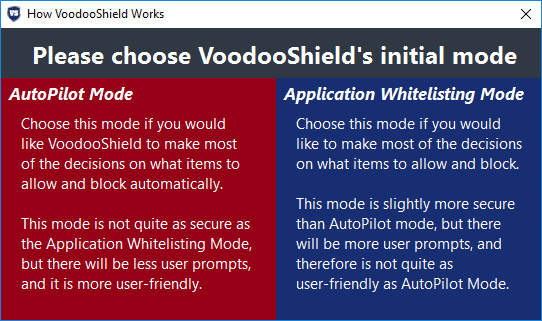

The first launch of the program is accompanied by a small educational program on its use, explaining exactly how the protection will be implemented.
Instructions for work

A control widget is displayed near the system tray, with which you can turn protection on and off, as well as use the context menu to change operational settings.
Control widget

Changing the settings of the program is available in the version of "pro", the free option offers to be content with what is, however, this is quite enough to block unknown files.
Basic and advanced settings provide tuning applications for themselves to make the operation of the application more comfortable.
Basic settings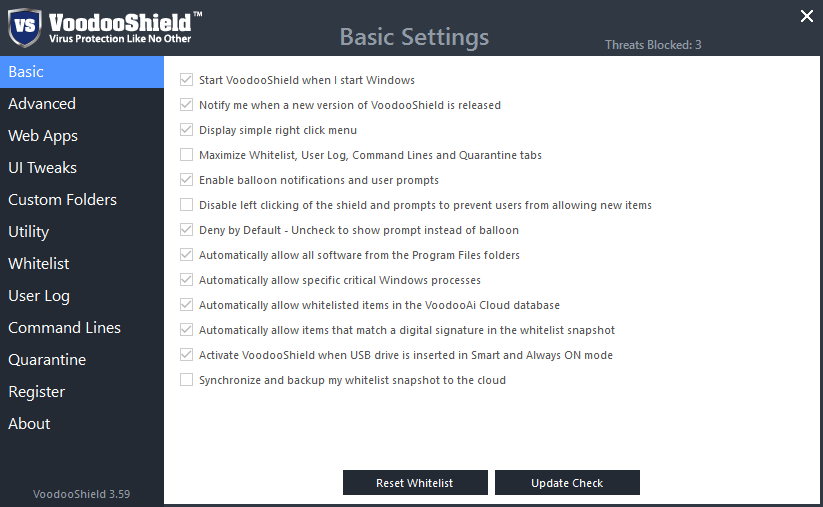

Advanced settings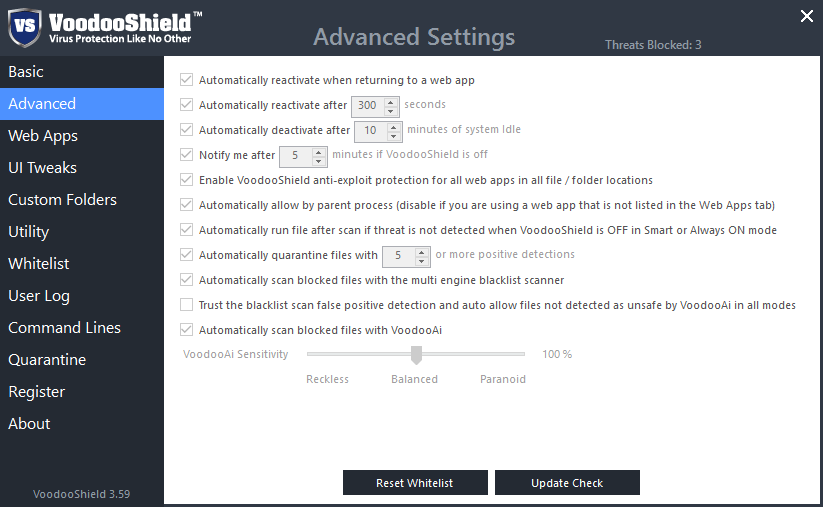

Predefined Internet applications, work with which puts the protection in the desired mode.
Application setup

"White list" of trusted applications, which can be filled automatically or manually.
White list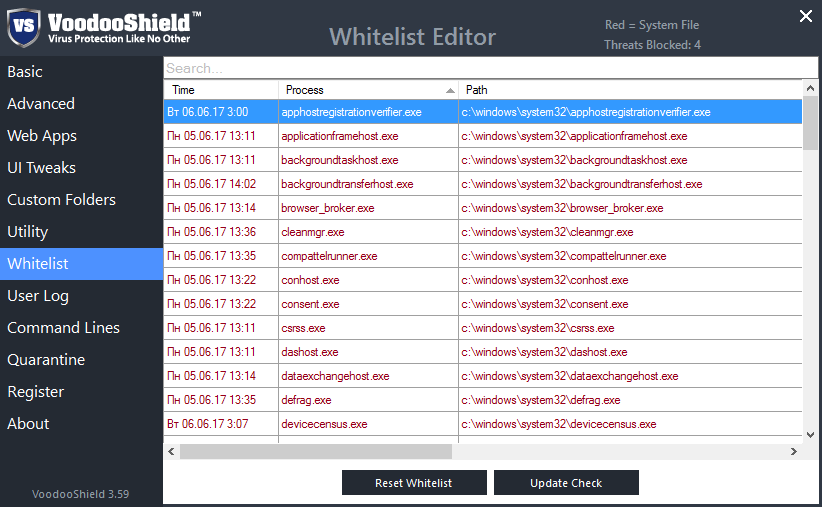

In order that the user does not have to suffer the first time, adding all his installed applications to the white list, the developers have provided the Training mode, which adds all the running processes to the white list. After working in this mode for several days, you will receive a setting in which all daily used applications will be included.
Let's now see how the program functions and fulfills its direct responsibilities. For this purpose, download the Yandex browser and try to install it on a test computer.
Downloading the file did not cause any problems, but launching the new application is accompanied by a blocking notification.
Blocking Notification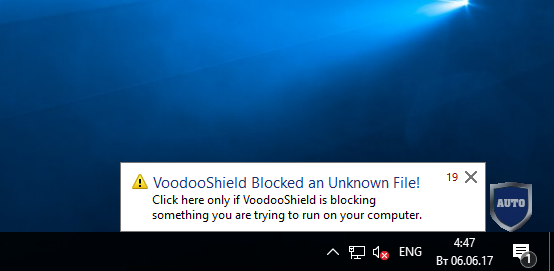

Clicking on the notification opens the action selection panel - block or run in the local or Internet sandbox Cuckoo.
Choice of action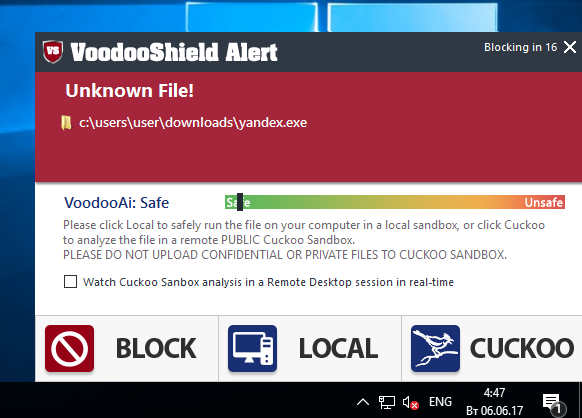

Blocking prevents the execution of the application being launched, and launching it in the local sandbox unfortunately leads to the crash of the application.
Error message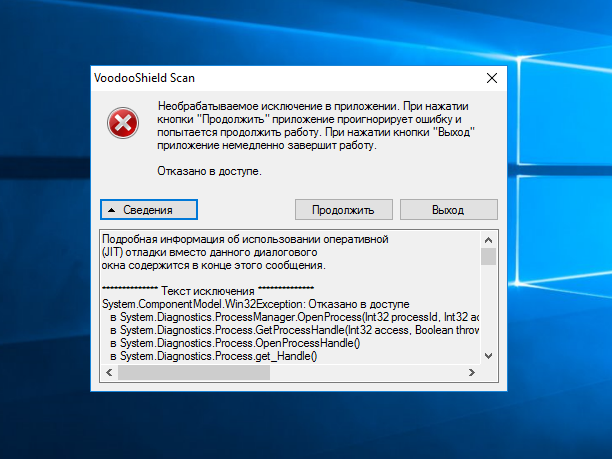

Run the protection again and try to install the browser. When choosing an action, select the launch in the Cuckoo sandbox.
Cuckoo sandbox

Downloading a file and analyzing it takes quite a long time, on the order of several minutes, after which the cuckoo announces its verdict - 7.9 points on a ten-point scale of danger, the application is harmful.
Analysis result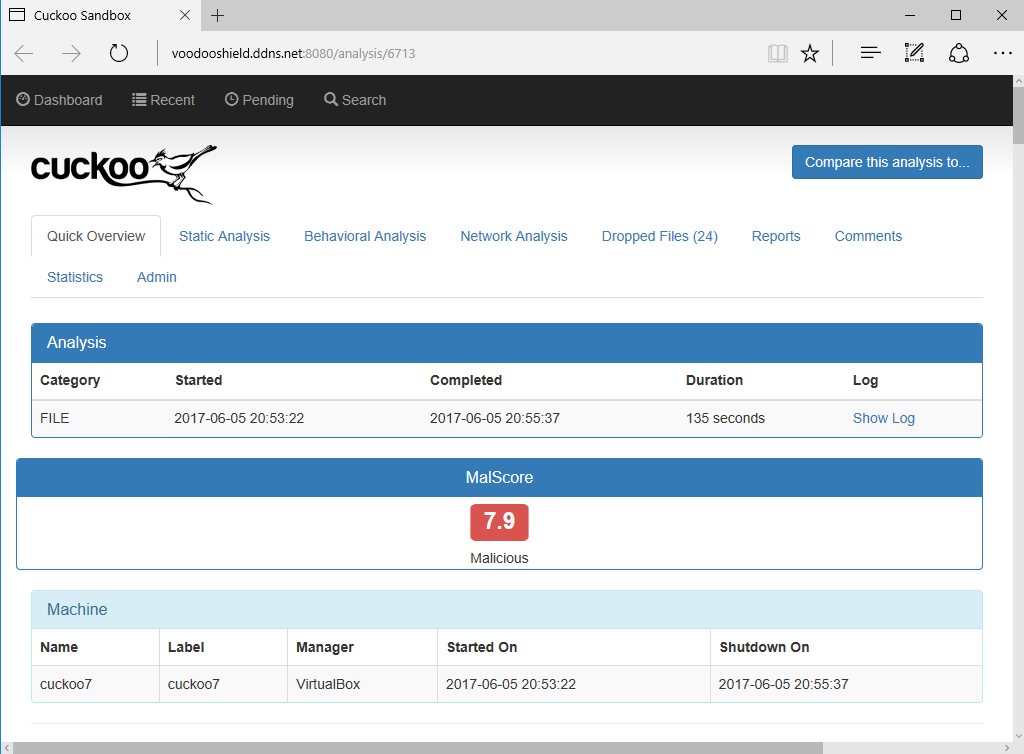

All actions are recorded in the log.
Event log

A separate section stores the executed command line, with the help of which objects were launched, which is convenient for analyzing the parameters passed to the application.
Command line log

VoodooShield is quite easy to use, but at the same time a very effective tool in combating various threats. The application has some rough edges, but considering that the program can be used completely free of charge, this is quite a worthy option that will allow you to control any malicious objects that attempt to penetrate the computer.
Secureaplus
SecureAPlus advanced antivirus from the company SecureAge. The application combines tools for monitoring and detecting threats in real time with the functions of analyzing suspicious objects and using as many as 12 third-party anti-virus engines.
When you install the product, developers generously offer a free annual license, but after a year the license will have to pay $ 2 per month or $ 22.5 per year. Product site: https://www.secureaplus.com
Immediately after installation, the user is prompted to perform a system scan, based on the results of which a list of trusted applications will be created, as well as information about objects with not very good reputation (if any will be detected).
The program icon is displayed in the system tray, through the context menu you can perform standard operations - open the setting, select the current operation mode.
Application context menu

SecureAPlus can operate in the following modes - Interaction, Blocking, and Trust All. The names reflect the essence of the selected mode - "Interaction" every time asks the user to trust or not the unknown application, "Block" automatically blocks unknown suspicious objects that are not on the white list, "Trust all" allows any processes to work.
Mode selection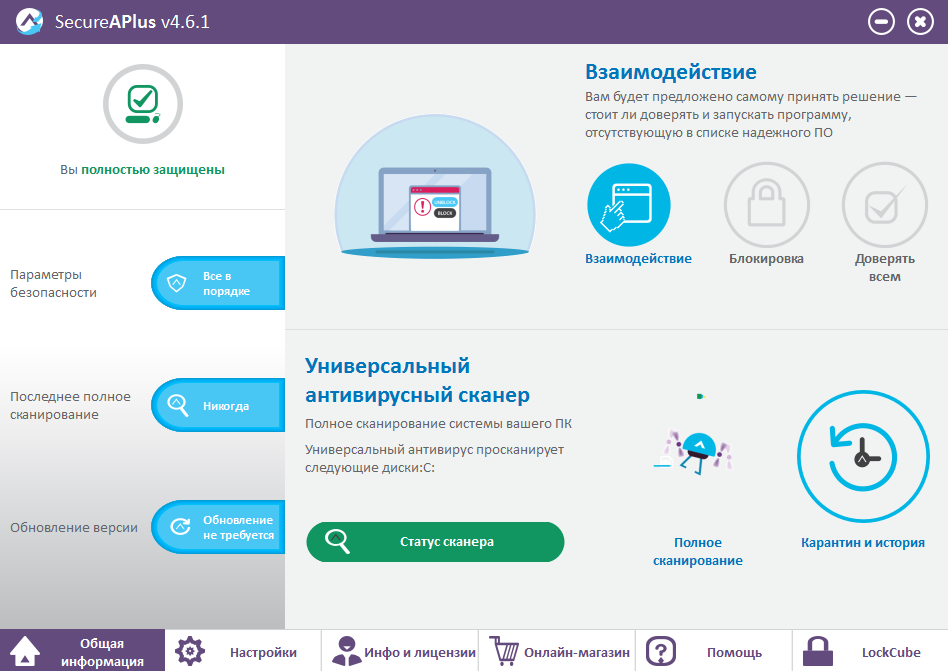

The inclusion of the latter mode can be carried out for a certain time, which is convenient for installing new applications and performing operations that do not require constant monitoring of processes.
Select the shutdown interval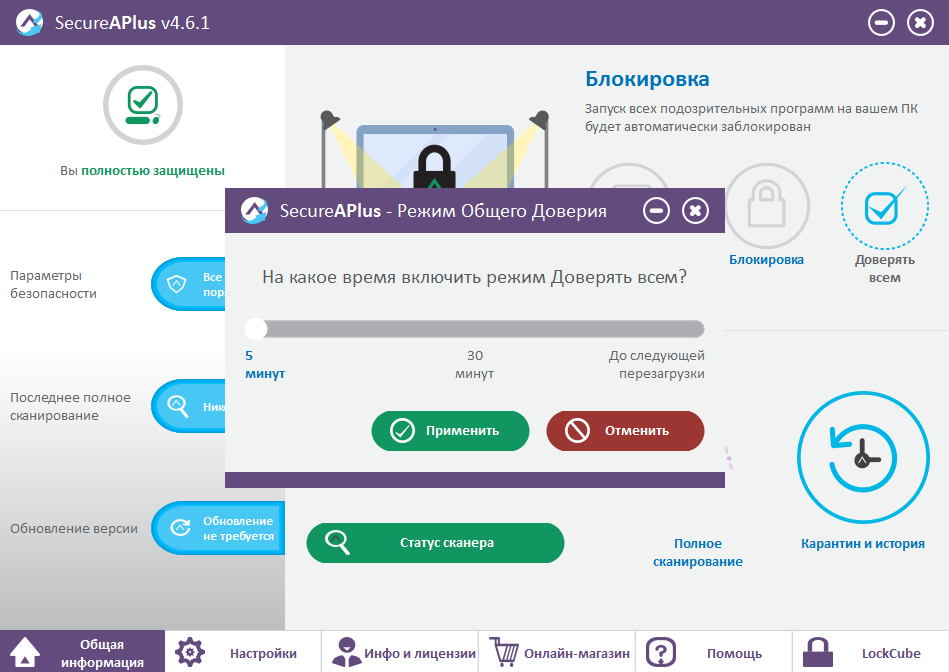

Setting up the white list is very flexible, and even excessively flexible, so that the anatomical user such anatomical details can easily confuse.
The application allows you to add trusted applications, certificates and scripts.
Advanced installations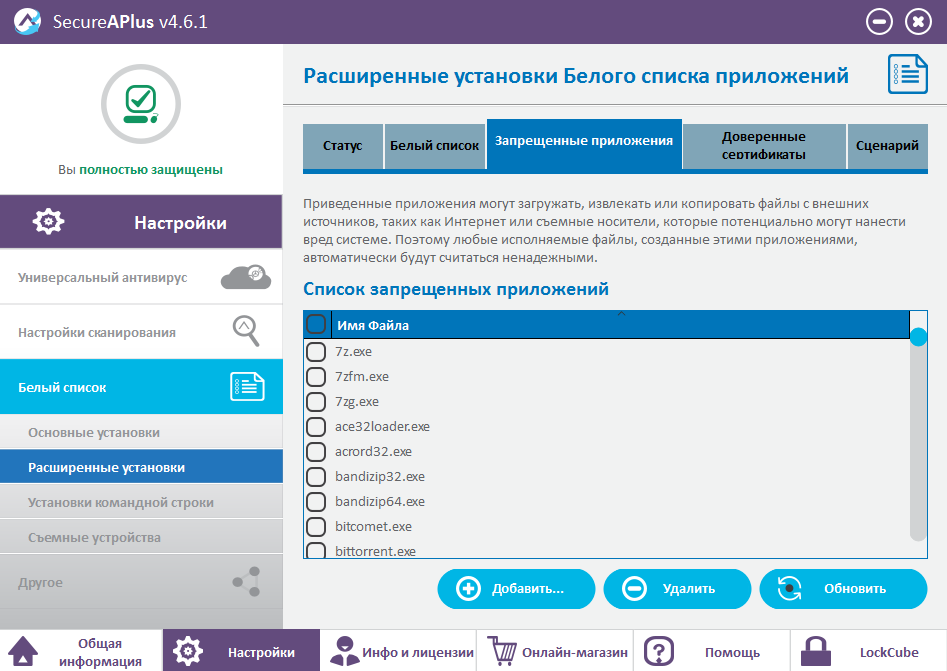

The whitelist can be completely customized. In addition, the program provides a monitoring mode that allows the execution and operation of untrusted processes, but all actions performed by them are saved in a log.
Whitelist settings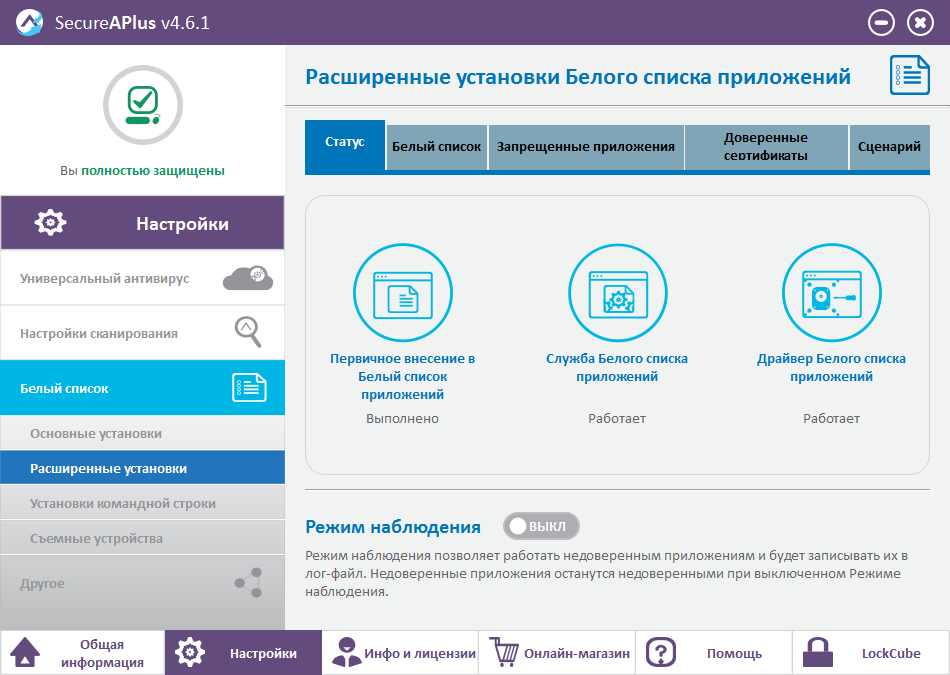

The program integrates into the operating system shell, so that a quick scan of any file is available when you right-click on it. It should be noted that the scan may take some time, since the file must first be uploaded to the server.
Depending on your needs, you can configure the anti-virus mechanism — enable or disable working engines for scanning suspicious objects that will be sent for scanning via the Internet in real time.
In the case of limited communications, it is possible to set a daily limit for downloadable files.
Universal Antivirus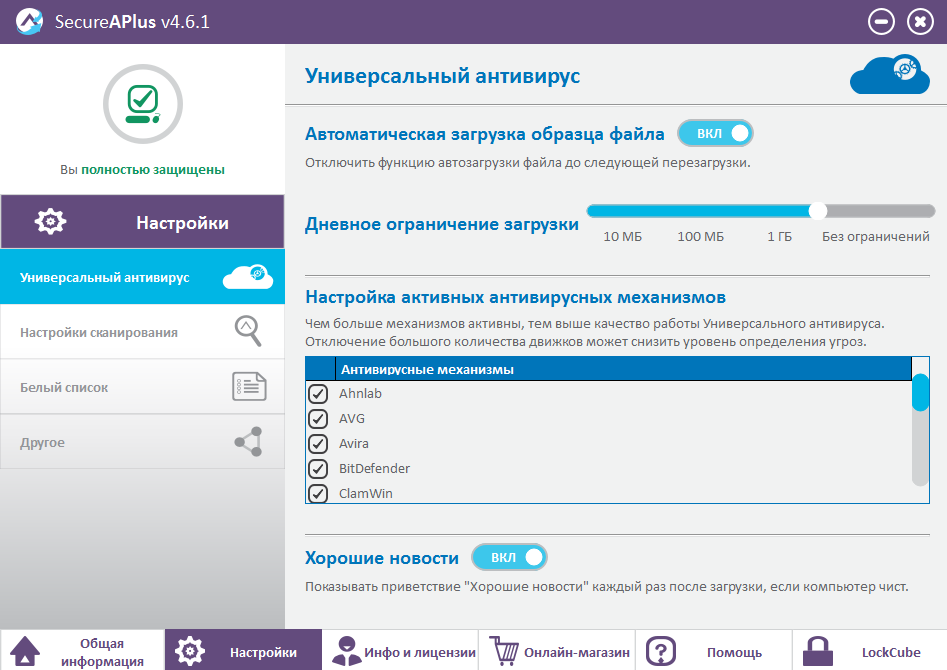

To test the operation of SecureAPlus, I tried to download and start the installation of the Yandex browser. During the launch, a nice window appeared with information about the object and the choice of the desired action. If the user does not know whether he can trust the file being launched, he can check it with the help of the cloud antivirus, or immediately block the malicious application.
Choice of action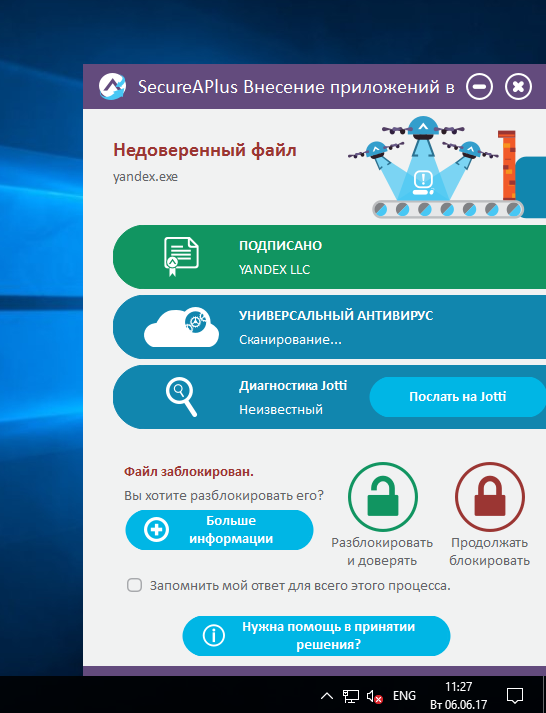

In the course of work, the program also scans files in the background process and, if it finds threats, then immediately informs about them in such a cartoon window.
Threat Information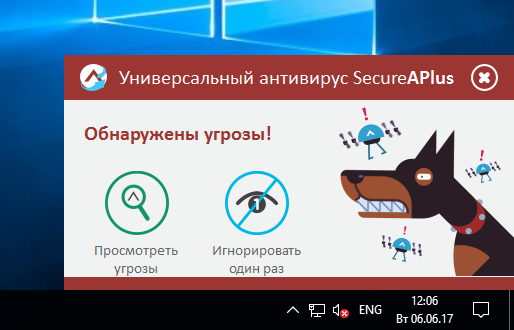

View information allows you to get comprehensive information about the threat.
Threat Information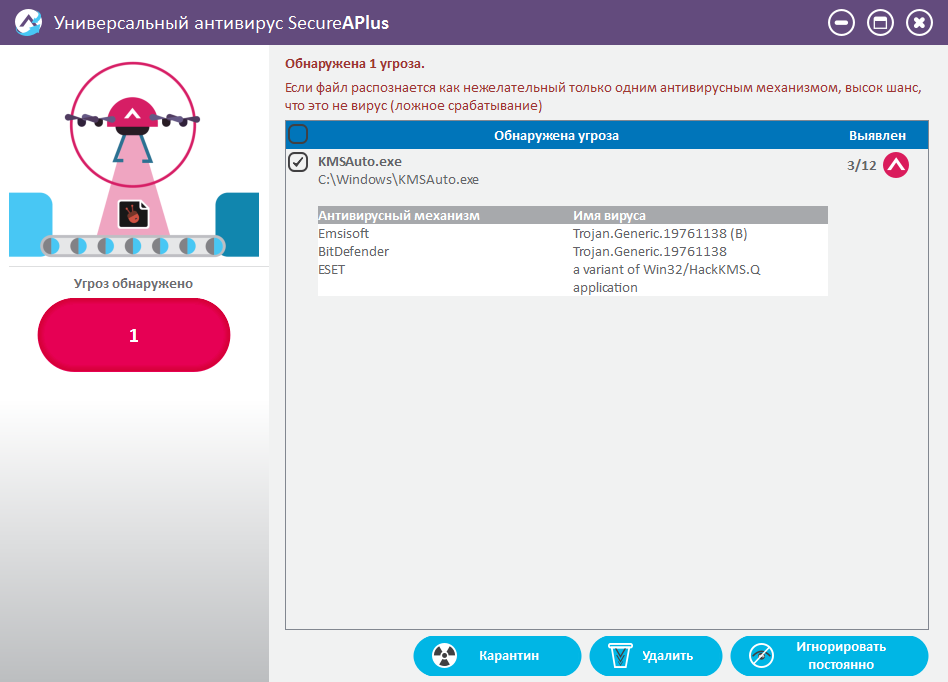

SecureAPlus makes a very good impression, the tool is able to protect the computer before installing and in the process of operating suspicious applications. Antivirus is easy to use and is characterized by a clear, beautiful, albeit slightly frivolous interface. Among the shortcomings, we can distinguish some redundancy in the functionality and a too detailed setting, which may not always be up to the average user.
Defendset
Defendset is a proactive solution for blocking unauthorized file operations that works in Windows 7/8/10 and Windows Server 2008/2012/2016 operating systems.
The cost of the license depends on the scope of its application. Home non-profit or personal license - 320 rubles., Corporate license for organizations - 970 rubles., Server - 4600 rubles. Prices are for one year of use. Product site: https://defendset.ru
When first installed, a trial 30-day license is provided, without any limitations in functionality, which allows you to evaluate the usefulness of the tool and make an informed purchasing decision.
During the installation process, the user is prompted to select the initial security level.
All management is carried out using the settings window, which appears after clicking on the program icon. On the left - on / off protection, at the top of the list of all rules, below - detailed information on the selected item, it changes depending on the active position of the list.
Settings window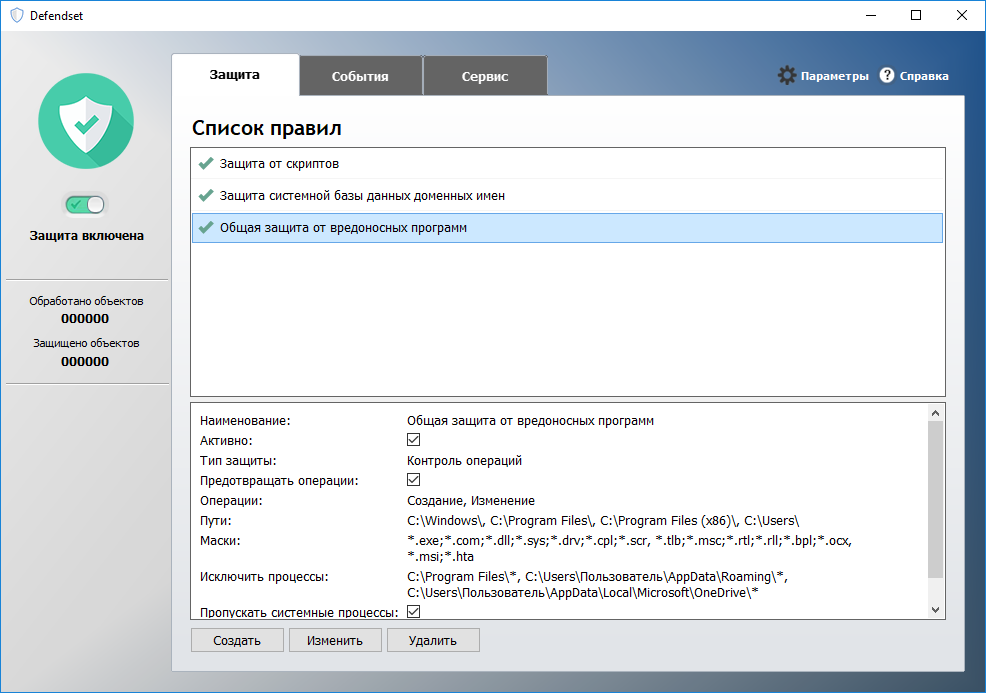

After installation, the program already has a set of predefined rules with the help of which protection is carried out, besides, they are useful in that you can enter and understand how everything is arranged, especially from the name of the rule it is clear what it is responsible for and how it should function.
On the main tab - the name of the rule, its activity and the choice of the desired type of protection, type of control, and of the operations themselves, which can be blocked. There are not many of them, but these are the most basic ones - creation, modification, deletion and discovery.
Rule settings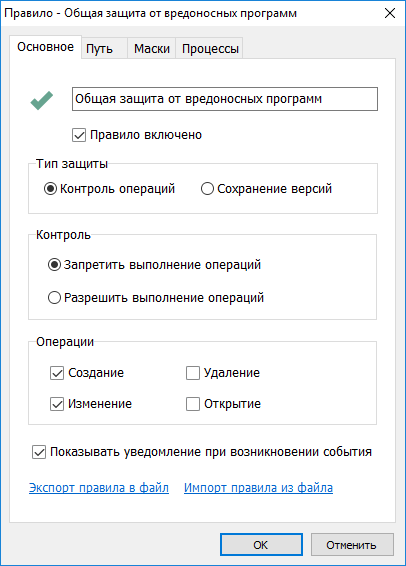

The next tab is the paths for placing blocked files, and exceptions to them. Here is a list of controlled directories. You can specify something specific, but you can immediately all.
Setting paths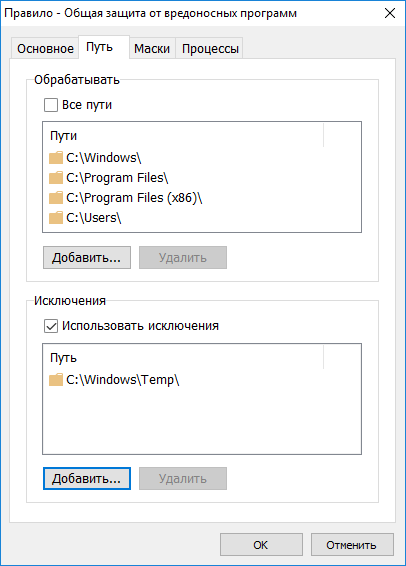

The choice of types of monitored files, all by analogy with directories.
Setting masks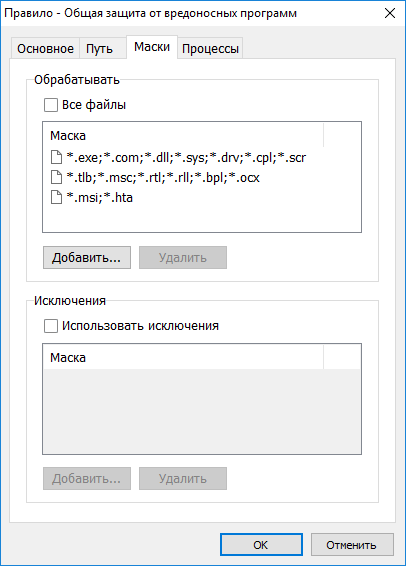

Well, the last tab with the processes - they are processed all, and here you can set exceptions: system processes for normal operation of Windows and any trusted applications, and they can be specified explicitly, or by mask. For example, in this rule it is not forbidden to do anything to programs from standard program folders, there will be a need - you can add something else.
Process setup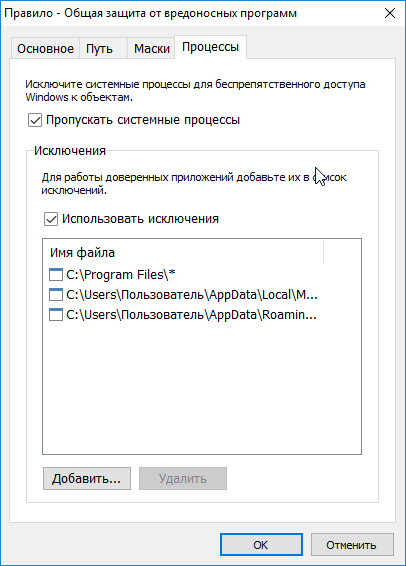

For testing, we will try to download and install the Yandex browser. Downloading takes place without any obstacles, and the installation is blocked. The lock is accompanied by an information window in the lower right corner in which information about the event is displayed.
Blocking Notification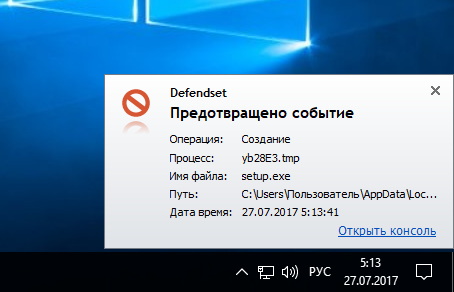

For further tests, I made a new rule - in the root folder, Test prohibited all operations on any files.
Test rule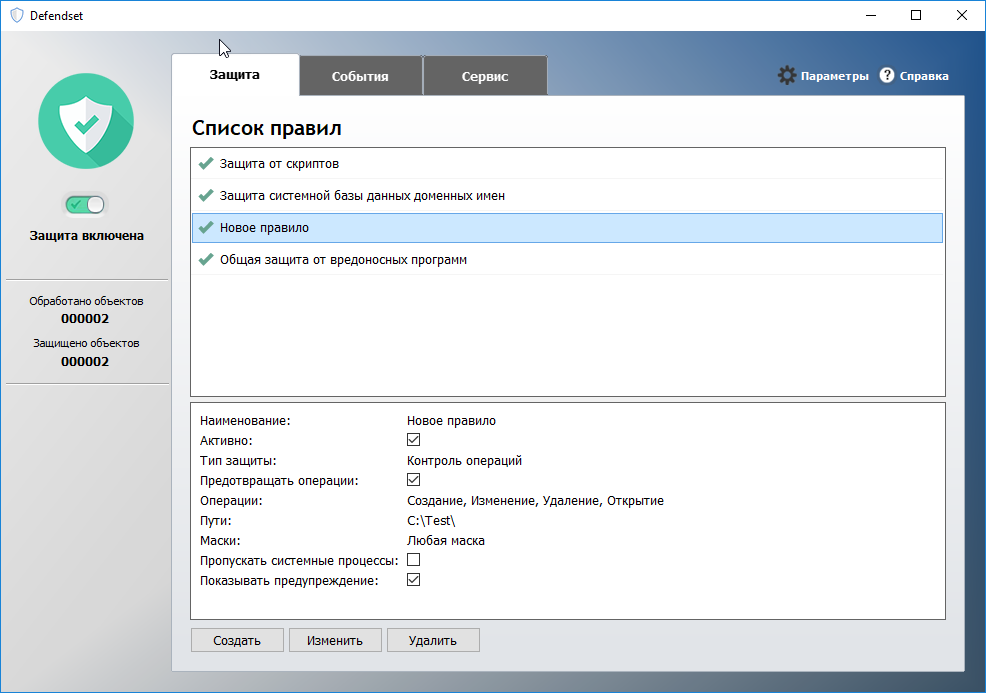

I try to create a new Word document in Test - the action is blocked, the program writes that this is the creation of a new file in the protected zone.
Lock file creation

Copying a previously downloaded browser to the test folder is also safely prevented.
Copy lock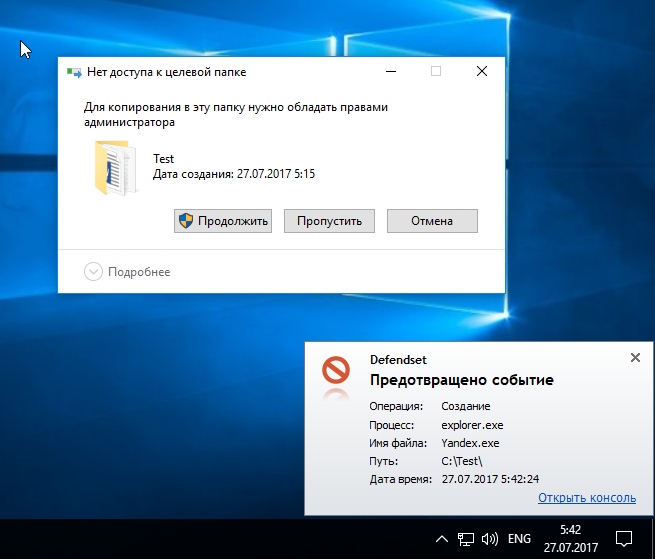

For further experiments, temporarily disable the protection and create a Test Word document in Test. Again activate the Defendset and try to open the file.
Opening lock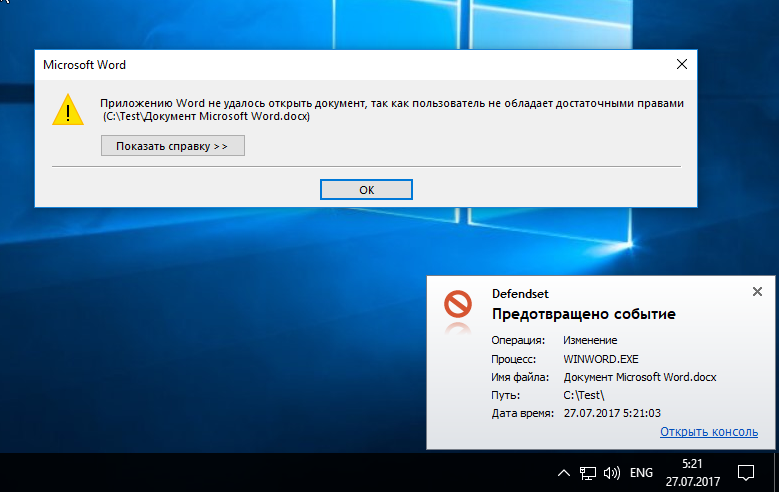

Word can not open the file, the operation is blocked. The same thing happens when you try to run the installation package.
Startup lock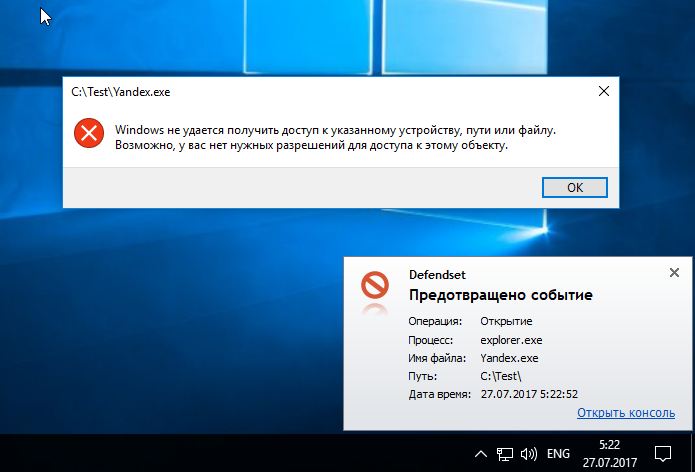

Any change (editing, renaming, moving) and deleting a file with protection enabled is also impossible.
Lock delete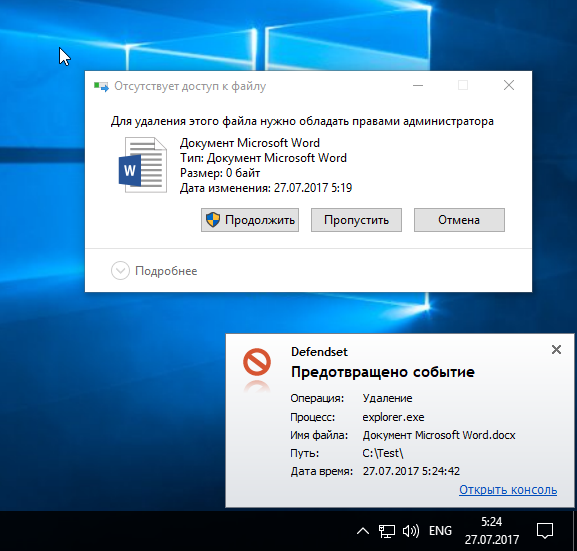

All blocking information is logged.
The event log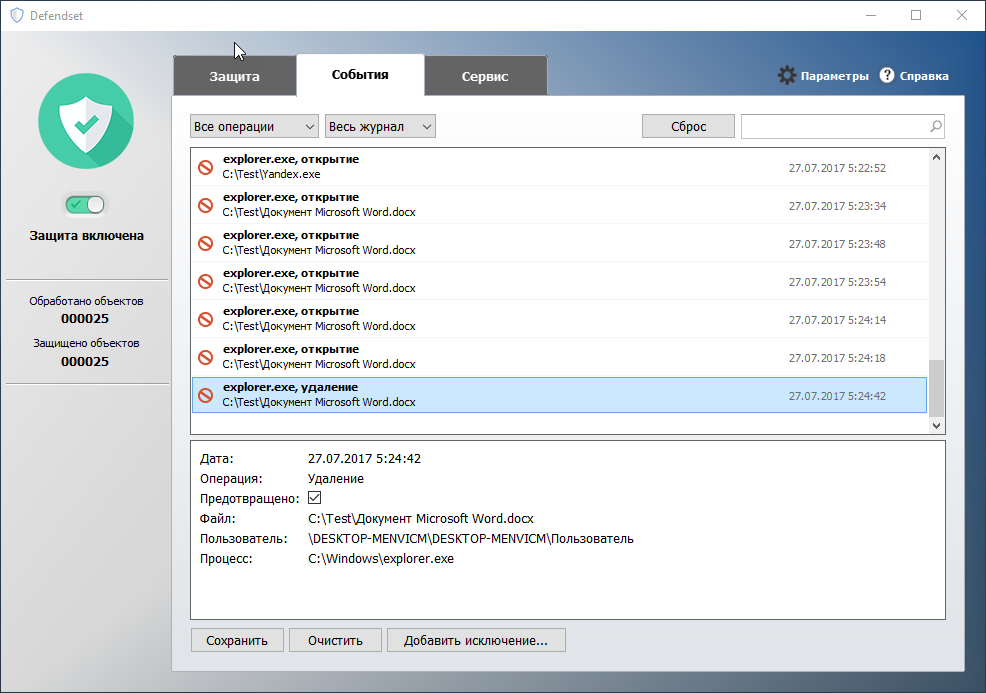

Now let's see how the program will function in the monitoring mode - this is when I do what I want, but all actions are recorded in the log. Select the “Allow operations” rule in the settings, the icon changes to a yellow shield with an exclamation mark.
Monitoring setup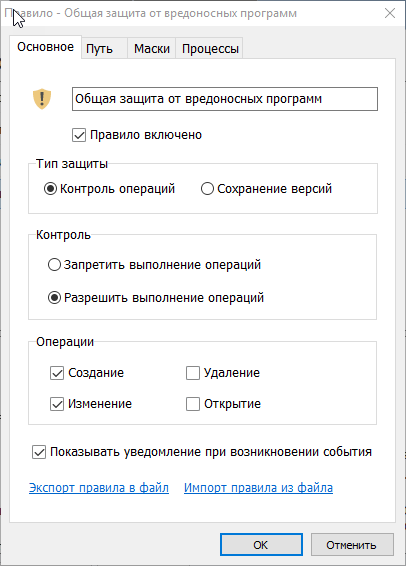

The attempt to copy Yandex.exe to the desktop is successful, but a notification of the operation is displayed, and a corresponding entry appears in the event log, the notification icon is the same as in the rule.
Event Notification

Another feature of the program is versioning, when a copy of the document is saved in a special directory when the document is written. In the settings, you can set the save interval — after how much time to create a new version (for example, no more than once per hour), this is convenient from littering the catalog with frequent saves. The size of the file is also regulated, in case that copies of large files do not take up too much disk space.
Versioning setup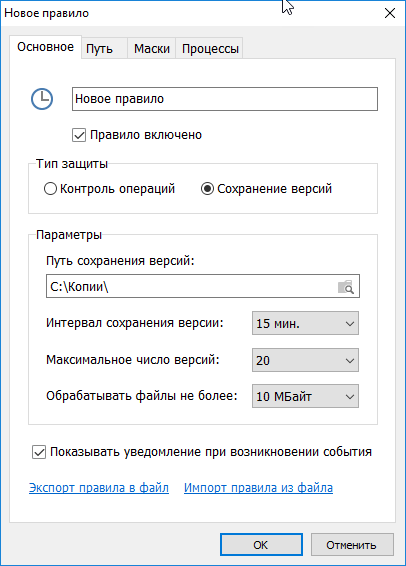

To test this great feature, I created a rule that backed up files from the Test folder to the root Copies folder.
Rule for saving versions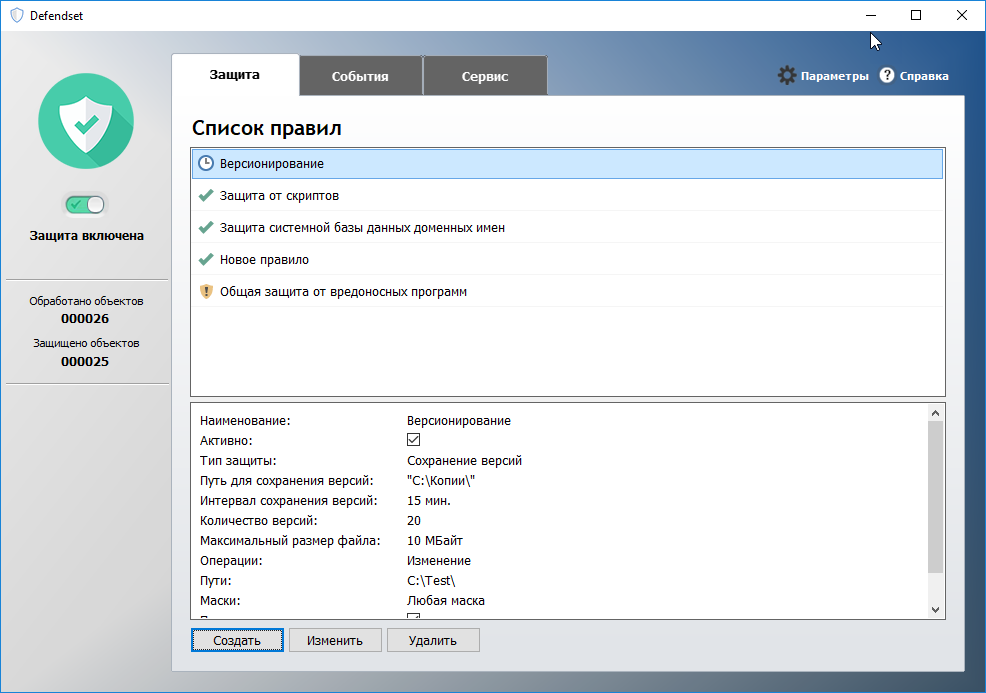

I create a text file with the word Hello inside. Writing notification says that the copy was successfully created.
Record of the first version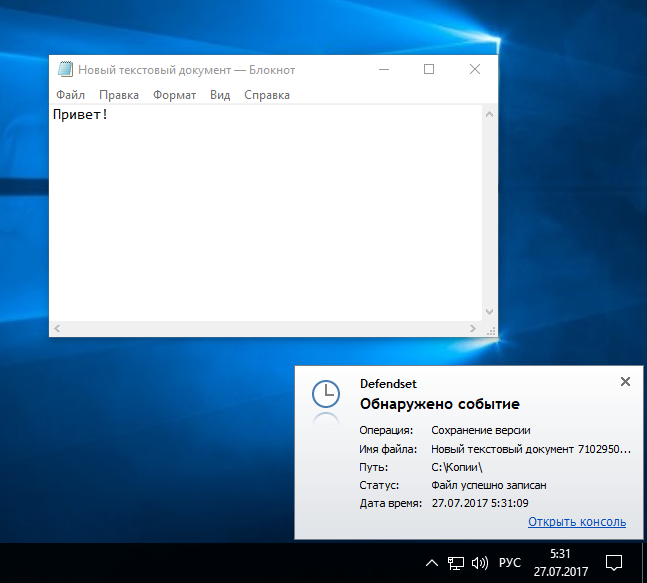

I add a line and write it down again.
Record second version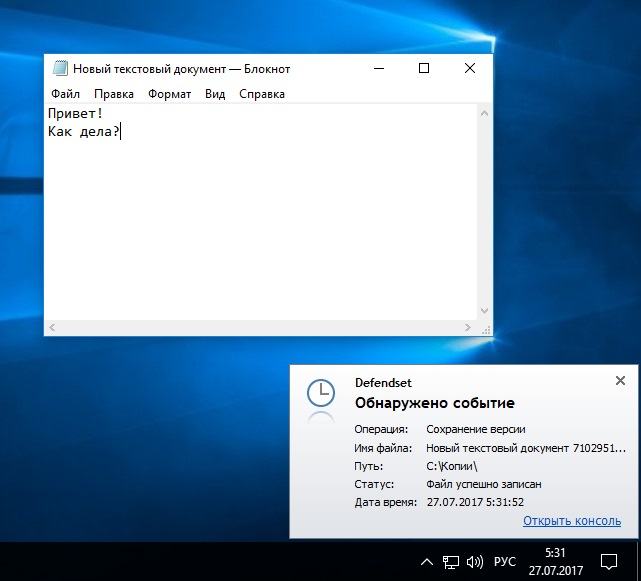

Now we go to the Copies folder and see that there appeared two files with different contents.
Created versions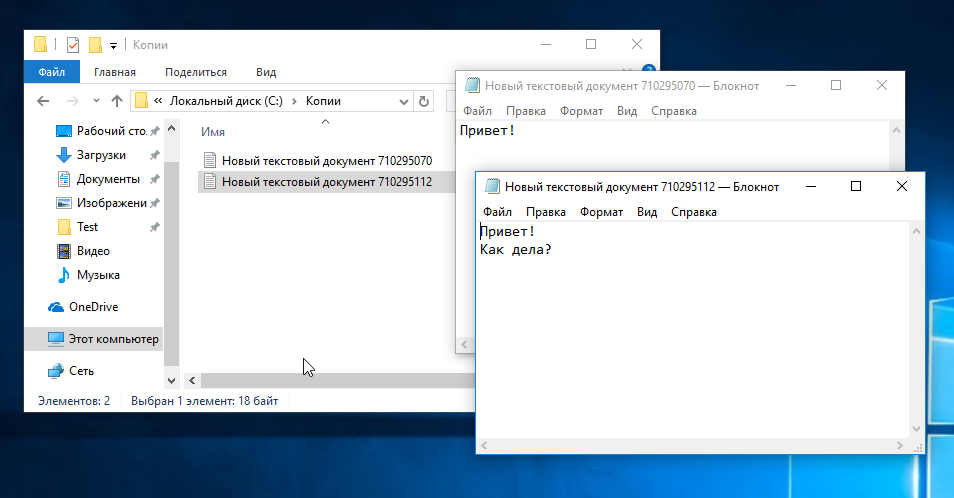

This function can be used as an alternative protection against changes by copying versions of files into a shared folder on the server, if the encrypter encrypts the local file, then the working copy will remain there. It can also be useful when editing files (articles, scripts, html pages, etc.) when you need to return a version with the necessary text fragment or a piece of code.
Records of all operations appear in the event log, however, event logging can be turned off for any of the rules by simply unchecking the checkbox of events.
The event log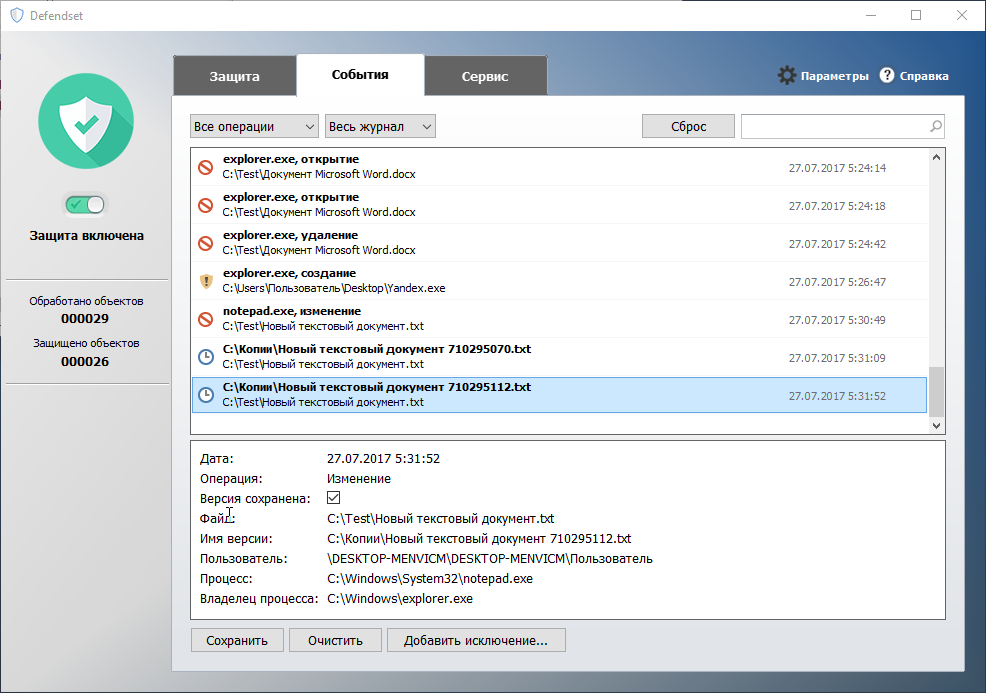

Defendset, both in terms of functionality and ease of use, deserves a positive evaluation. In general, I liked the program.
In addition, developers can be counted thoughtful concise interface. I would also note extremely simple operation - after installation, the program immediately starts to perform its functions, without requiring any training from the user and without asking obscure questions, but still you should not rely completely on protection for one application, so it would be better to use it in tandem with antivirus.
findings
Summing up, I want to say that the development of anti-virus protection does not stand still, new ideas and solutions appear, and developers who do not want to integrate them into their products will be forced to remain in the rearguard. In my opinion, blocking unauthorized operations today is very promising, interesting and, as practice shows, a rather viable protection mechanism. I hope that something like this tool in its arsenal will soon have all the leading anti-virus products.
Source: https://habr.com/ru/post/335448/
All Articles