Autonomous way to bypass DPI and effective way to bypass site blocking by IP address
Providers of the Russian Federation, for the most part, use the system of deep traffic analysis (DPI, Deep Packet Inspection) to block sites that are listed in the registry of prohibited. There is no single standard on DPI, there is a large number of implementations from different suppliers of DPI solutions that differ in connection type and type of work.
There are two common types of DPI connections: passive and active.
')
We try to enter the blocked site:
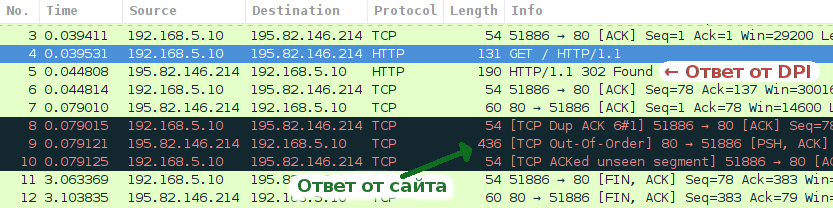
We see that the packet comes first from DPI, with the HTTP redirect code 302, and then the real response from the site. The response from the site is regarded as a retransmission and discarded by the operating system. The browser follows the link specified in the DPI response, and we see the blocking page.
Consider a package from DPI in more detail:
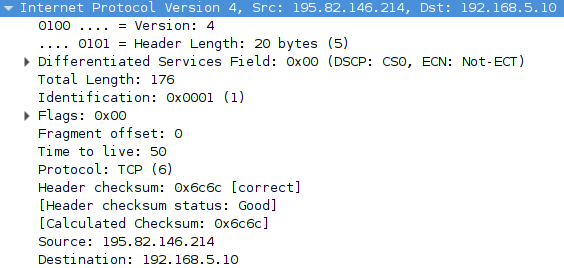
DPI «Don't Fragment», Identification 1. «Don't Fragment», . DPI, , HTTP- 302, iptables, :
? u32 iptables 4- . 0x4 2- Indentification, 1- Flags Fragment Offset.
0x60 (HTTP- Location).
Identification = 1, Flags = 0, Fragment Offset = 0, 0x60 = «warn», 0x64 = «ing.», 0x68 = «rt.ru», , .
HTTPS-, DPI TCP Reset-, Identification = 1 Flags = 0.
DPI , , , .
HTTP-, , , , CRLF.
, .
HTTP/1.1 2014 . RFC 7230, HTTP- , ( ).
OWS — , SP — , HTAB — , CRLF — (\r\n).
, , -, :
, - , , .
, RFC 2616, - , HTTP- , :
TCP- 1460, , .
TCP Window Size = 2 SYN/ACK- ( ), HTTP- :
1:
URI, "Host: " . «Host» «hoSt» , .
DPI . DPI HTTP- , TCP- . DPI «» , TCP Window Size.
, DPI , . , DPI , . .
DPI, Host hoSt, Host, «» HTTP HTTPS- ( TCP Window Size), HTTP- .
, : , .
, , . :
, , Yota, HTTP, .
ReQrypt -: ReQrypt , ReQrypt IP- , , ReQrypt.

NAT, ReQrypt . , .. NAT IP-.
«» NAT, ReQrypt TCP- , TTL = 3. NAT- , .
- , . IP- DNS, NNTP , - . - , . .
Linux — zapret.
ReQrypt, IP-.
Blockcheck. DPI , , « DPI», GoodbyeDPI . , ReQrypt.
.
There are two common types of DPI connections: passive and active.
Passive DPI
Passive DPI - a DPI connected to the provider network in parallel (not in a section) either through a passive optical splitter or using traffic mirroring from users. Such a connection does not slow down the speed of the provider’s network in case of insufficient DPI performance, which is why it is used by large providers. A DPI with this type of connection can technically only detect an attempt to request prohibited content, but not suppress it. To circumvent this restriction and block access to a banned site, the DPI sends the user who requests a blocked URL a specially crafted HTTP packet with redirection to the provider stub page, as if the response was sent by the requested resource itself (spoofing the sender's IP address and TCP sequence). Due to the fact that DPI is physically located closer to the user than the requested site, the forged response reaches the user's device faster than the real response from the site.')
Detect and block passive DPI packets
Fake packets generated by DPI can be easily detected by a traffic analyzer, for example, Wireshark.We try to enter the blocked site:

We see that the packet comes first from DPI, with the HTTP redirect code 302, and then the real response from the site. The response from the site is regarded as a retransmission and discarded by the operating system. The browser follows the link specified in the DPI response, and we see the blocking page.
Consider a package from DPI in more detail:

HTTP/1.1 302 Found
Connection: close
Location: http://warning.rt.ru/?id=17&st=0&dt=195.82.146.214&rs=http%3A%2F%2Frutracker.org%2FDPI «Don't Fragment», Identification 1. «Don't Fragment», . DPI, , HTTP- 302, iptables, :
# iptables -A FORWARD -p tcp --sport 80 -m u32 --u32 "0x4=0x10000 && 0x60=0x7761726e && 0x64=0x696e672e && 0x68=0x72742e72" -m comment --comment "Rostelecom HTTP" -j DROP? u32 iptables 4- . 0x4 2- Indentification, 1- Flags Fragment Offset.
0x60 (HTTP- Location).
Identification = 1, Flags = 0, Fragment Offset = 0, 0x60 = «warn», 0x64 = «ing.», 0x68 = «rt.ru», , .
HTTPS-, DPI TCP Reset-, Identification = 1 Flags = 0.
DPI
DPI — DPI, , . , DPI IP- , DPI . DPI , , , DPI , .DPI , , , .
HTTP
HTTP- :GET / HTTP/1.1
Host: habrahabr.ru
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:49.0) Gecko/20100101 Firefox/50.0
Accept-Encoding: gzip, deflate, br
Connection: keep-aliveHTTP-, , , , CRLF.
, .
HTTP/1.1 2014 . RFC 7230, HTTP- , ( ).
Each header field consists of a case-insensitive field name followed
by a colon (":"), optional leading whitespace, the field value, and
optional trailing whitespace.
header-field = field-name ":" OWS field-value OWS
field-name = token
field-value = *( field-content / obs-fold )
field-content = field-vchar [ 1*( SP / HTAB ) field-vchar ]
field-vchar = VCHAR / obs-text
obs-fold = CRLF 1*( SP / HTAB )
; obsolete line foldingOWS — , SP — , HTAB — , CRLF — (\r\n).
, , -, :
GET / HTTP/1.1
hoSt:habrahabr.ru
user-agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:49.0) Gecko/20100101 Firefox/50.0
Accept-Encoding: gzip, deflate, br
coNNecTion: keep-alive ← , - , , .
, RFC 2616, - , HTTP- , :
Clients SHOULD be tolerant in parsing the Status-Line and servers tolerant when parsing the Request-Line. In particular, they SHOULD accept any amount of SP or HT characters between fields, even though only a single SP is required.-. - .
TCP
TCP SYN- SYN/ACK-. , , TCP- (TCP Window Size) — , . . MTU 1500, 1460 TCP-.TCP- 1460, , .
TCP Window Size = 2 SYN/ACK- ( ), HTTP- :
1:
GET / HTTP/1.1
Host: habrahabr.ru
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:49.0) Gecko/20100101 Firefox/50.0
Accept-Encoding: gzip, deflate, br
Connection: keep-aliveHTTP TCP DPI
DPI .URI, "Host: " . «Host» «hoSt» , .
DPI . DPI HTTP- , TCP- . DPI «» , TCP Window Size.
, DPI , . , DPI , . .
DPI
DPI Windows: GoodbyeDPI.DPI, Host hoSt, Host, «» HTTP HTTPS- ( TCP Window Size), HTTP- .
, : , .
, , . :
goodbyedpi.exe -1 -a-2 HTTPS-. , -3 -4 ( )., , Yota, HTTP, .
-3 -aIP
IP-, IP- , .ReQrypt -: ReQrypt , ReQrypt IP- , , ReQrypt.

NAT, ReQrypt . , .. NAT IP-.
«» NAT, ReQrypt TCP- , TTL = 3. NAT- , .
- , . IP- DNS, NNTP , - . - , . .
TL;DR
GoodbyeDPI — Windows, DPI. , .Linux — zapret.
ReQrypt, IP-.
Blockcheck. DPI , , « DPI», GoodbyeDPI . , ReQrypt.
.
Source: https://habr.com/ru/post/335436/
All Articles