Free network security audit with Fortinet. Part 2
In the previous article, we covered the topic of network security auditing with Fortinet ( Part 1 ). We discussed the main features and reviewed the sample report. Now we will look directly at installation and configuration. We agreed that we will use FortiGate VM and FortiAnalyzer virtual solutions for auditing. Those. first you need to request these images and demo licenses. Unfortunately we can not provide a direct link to the images (licensing restrictions). The implementation scheme looks pretty simple:
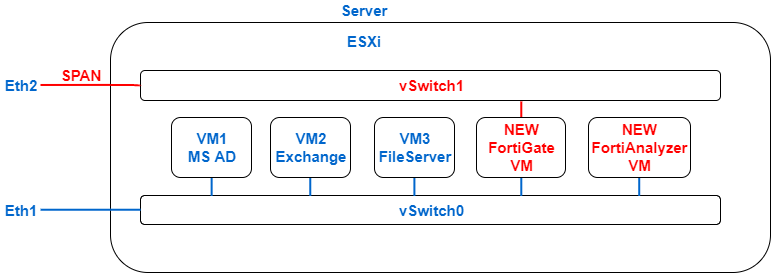
Those. on the existing virtualization server, two virtual machines are “raised”. In our case, we will use ESXi, but there is support for Hyper-V and KVM. FortiGate VM with one adapter is connected to a common network (vSwitch0). This link will be used to manage and access the Internet. The second interface connects to another vSwitch1, which in turn is connected to the server’s free physical port (eth2). It is on this port that the traffic should be mirrored for analysis. Note that Promiscuous mode (Accept) must be enabled for the vSwitch1 switch. More details can be found here .
Nearby, FortiAnalyzer is also installed, which is sufficient to connect only one interface to your network (vSwitch0).
')
As you understand, the first thing you need to import images. They are delivered in the form of ovf, so no problems should arise.
Import FortiGate VM:

Now you need to select a file. There are several of them in the archive, but we just need FortiGate-VM64.ovf :

Further, when configuring the interfaces, you need to select the VM Network for the first adapter (which corresponds to the network management - vSwitch0), and for the second - the VM Network 2 (which corresponds to the SPAN port - vSwitch1). The rest of the ports can be left by default:

By default, 1 GB of RAM and 1 core are set in the virtual machine properties. Do not try to change these parameters, otherwise the trial license is not activated and you will not be able to connect to this device. We'll fix it later.
The FortiAnalyzer virtual machine is imported in the same way. You must select the FortiAnalyzer-VM64.ovf file :

When setting up a network, it is enough to enable the first interface in the VM Network (i.e. network management):

This virtual machine has 4GB of RAM and 2 cores by default. As a rule, these parameters are always enough.
After successful import of images, you can start both "machines". First of all, we need to configure the ip-address and default route so that you can connect to the devices already through the web-interface.
The login is admin, and the password is empty (just press enter):

The ip address setting is performed using the following commands:
Setting the default gateway:

To check the settings, you can use the following commands:
show system interface (output port settings)
show router static (display of router settings)
Settings for FortiAnalyzer are similar:
The configuration of the gateway is slightly different:
After configuring the interfaces, it is very important to check that the Internet is available on the devices, otherwise the licenses are not activated. To verify, use the execute ping command.

After configuration, we can connect via the web-interface and activate the licenses that your partner should provide. Let's start with FortiAnalyzer:

Login admin and empty password. After logging in, the start page will open:

We are interested in System Settings:
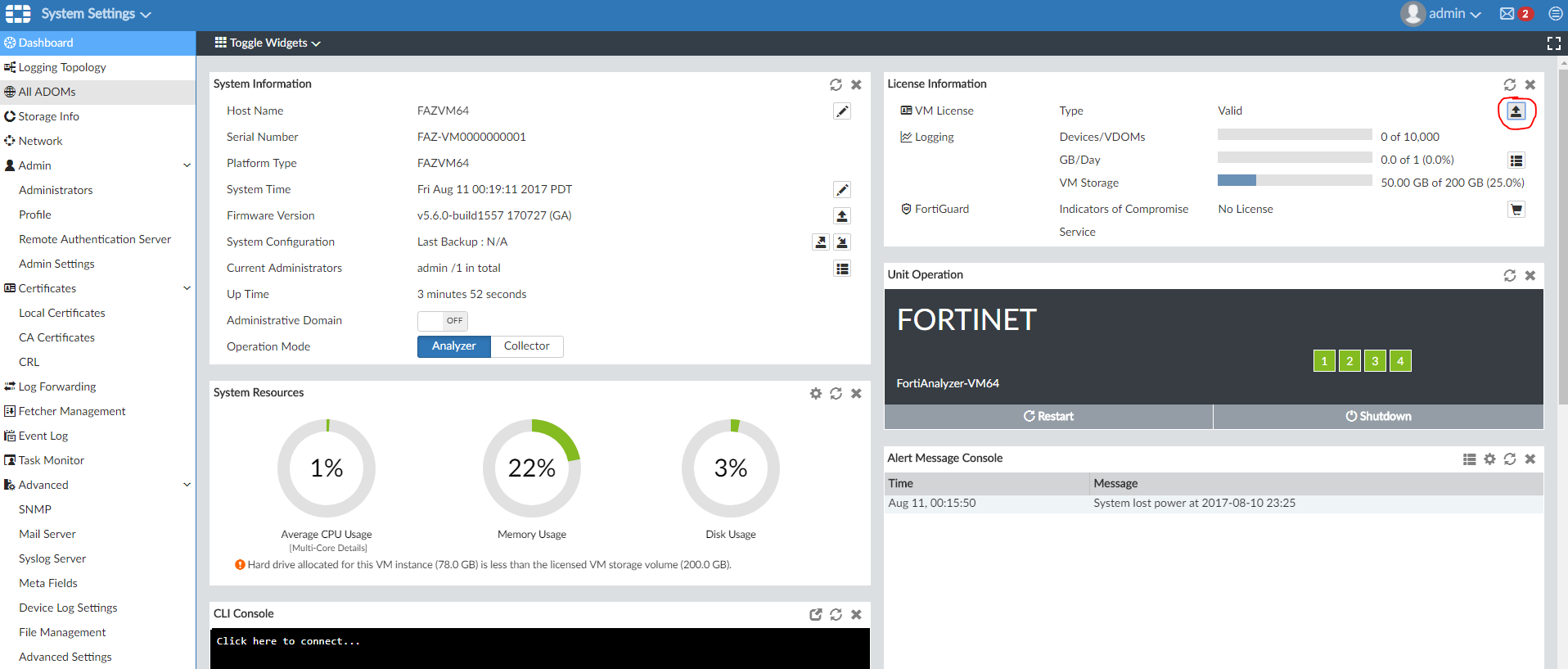
In the upper right corner we will see the license information. Currently the trial version is active, but we will add a new one by clicking on the Upload License. After that, the device will reboot with a new license.
FortiGate is a similar procedure. When connecting, please note that the http version of the portal will open, and if you try to connect via https, the browser will generate an error ERR_SSL_VERSION_OR_CIPHER_MISMATCH. This is a normal situation due to the trial mode. After the license is activated, we will be able to connect via HTTPS. The login window looks like this:

Login - admin , password - empty. After logging in we will see the FortiGate main page:

You need to activate the license by clicking on FGVMEV License and then throw a new one:

After that, the license activation process will begin, which may take some time:

After activation, the gateway will reboot. Now for a virtual machine, you can set 2 cores and 4 GB of RAM (depending on the license that you generated). As a result, you should see something like the following:
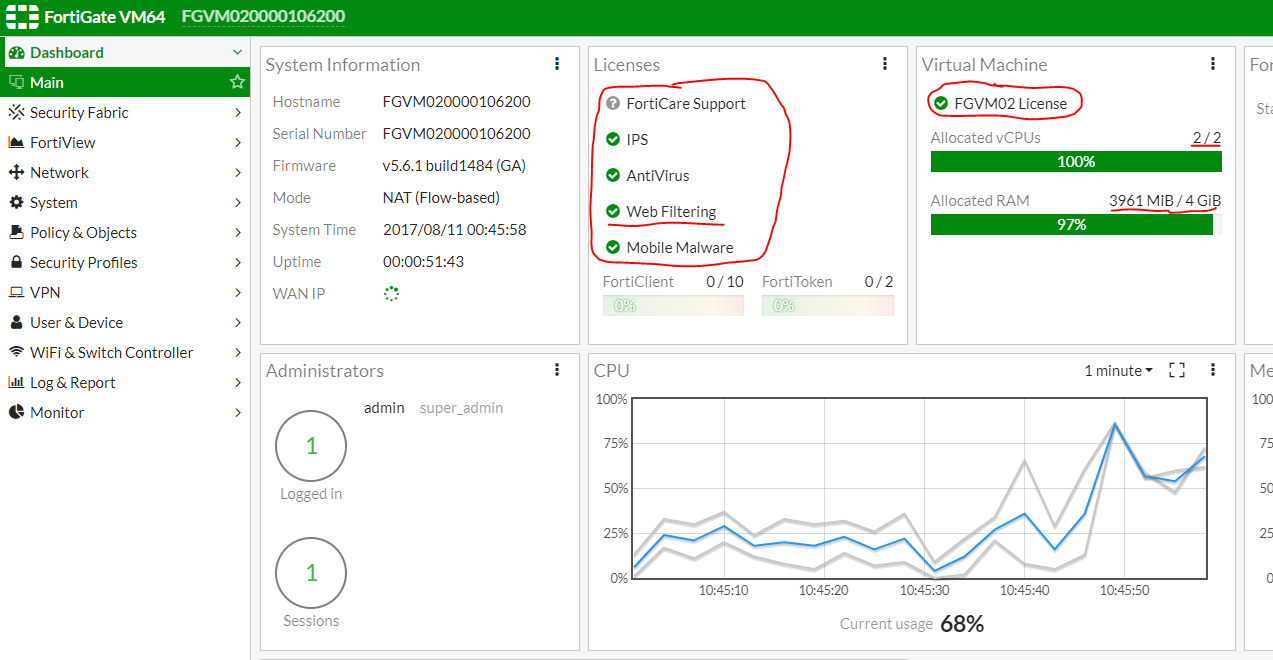
Please note that IPS, Anti-Virus, Web-filtering services may not be activated immediately, but after a while.
Now you can proceed directly to setting up a One-Arm Sniffer. To do this, open the interface settings:
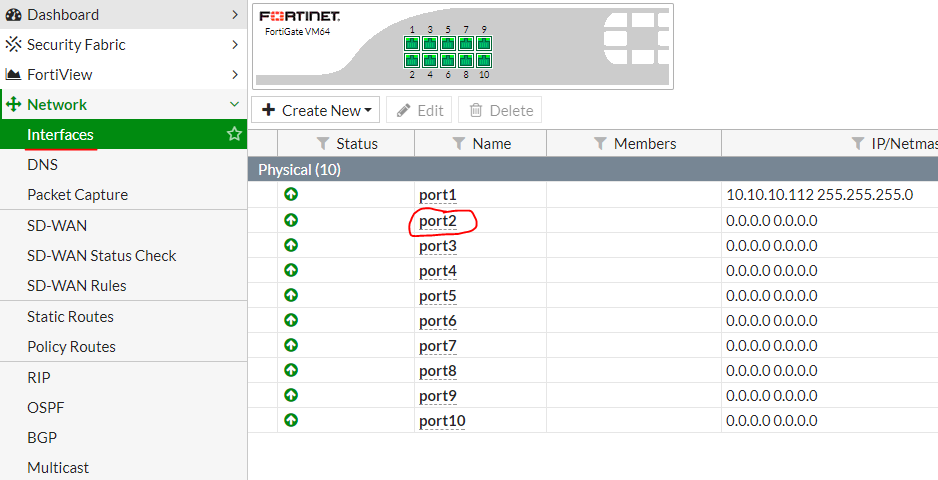
We are interested in port2 , because it is he who is connected to the SPAN port. Double click on its properties and set the settings as in the picture below:
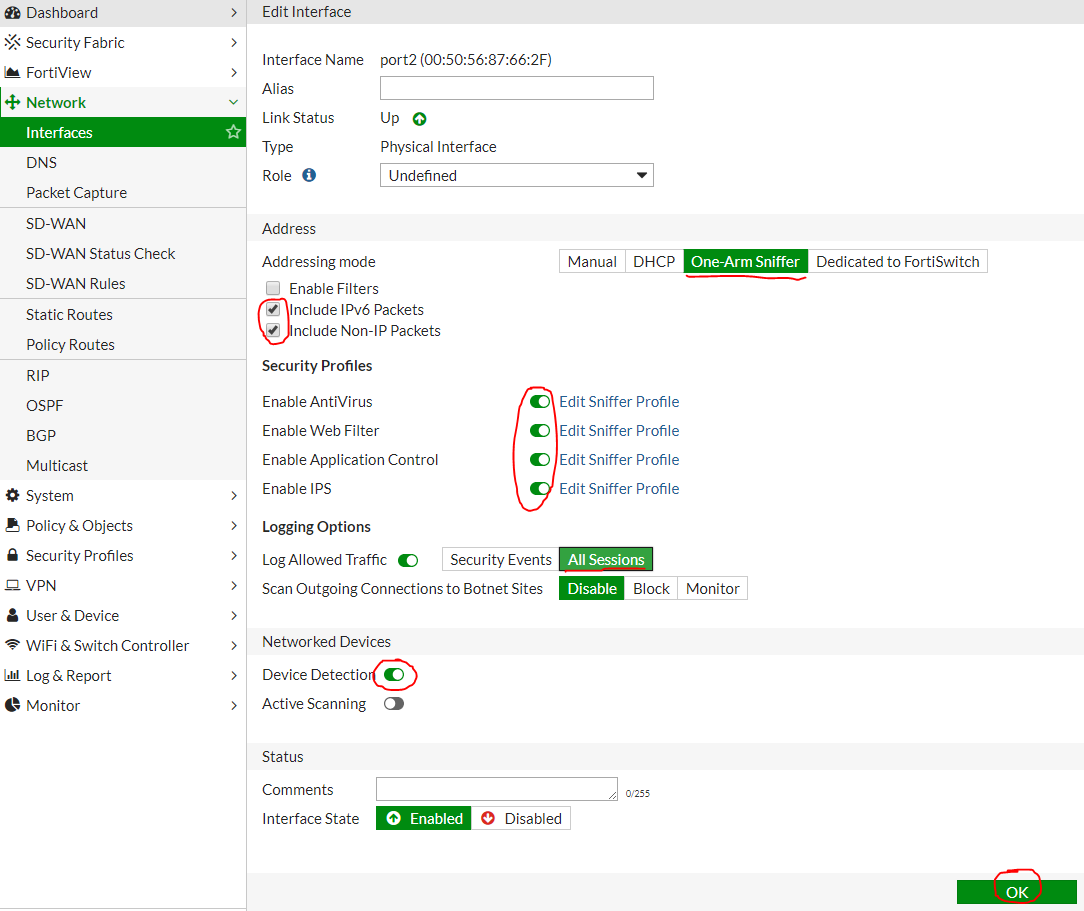
It is important to remember to click OK to apply the settings. After that, you need to go into the port2 settings again , and in turn open the settings of the AntiVirus, Web Filter, Application Control and IPS profiles.
Let's start with AntiVirus ( Edit Sniffer Profile ). The settings should look like this:
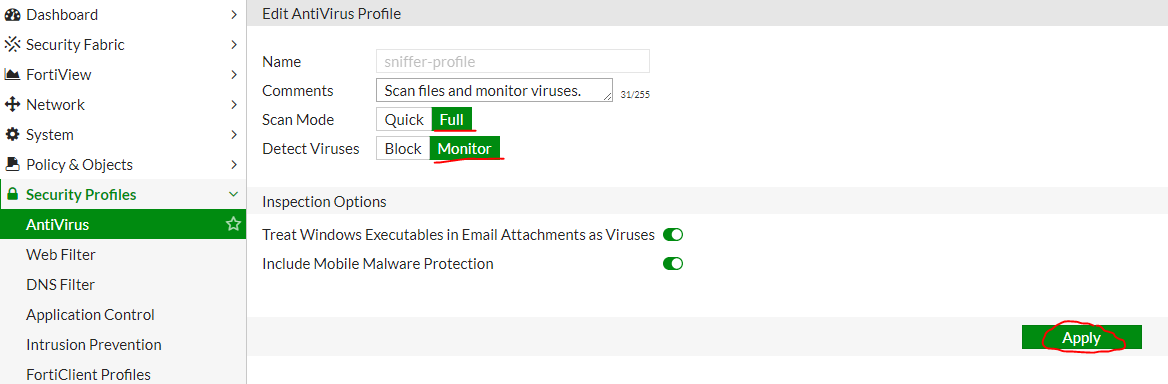
Do not forget to click Apply . Web Filter Settings ( Edit Sniffer Profile ):
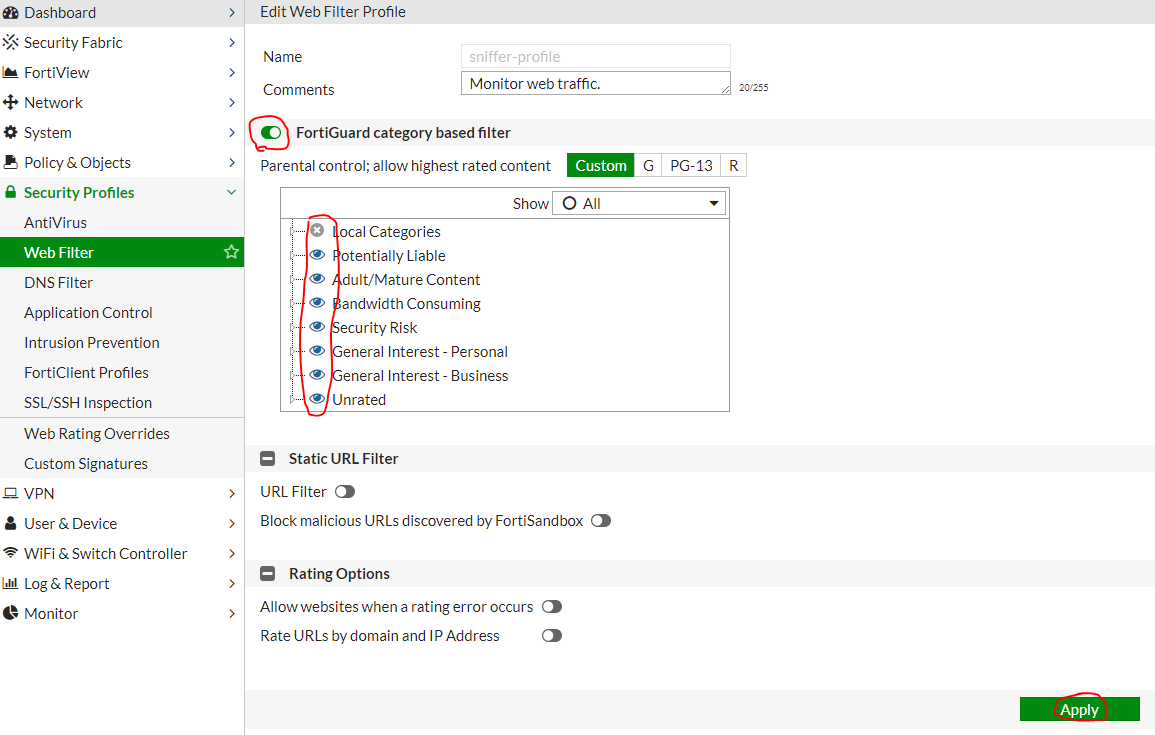
Settings Application Control ( Edit Sniffer Profile ):
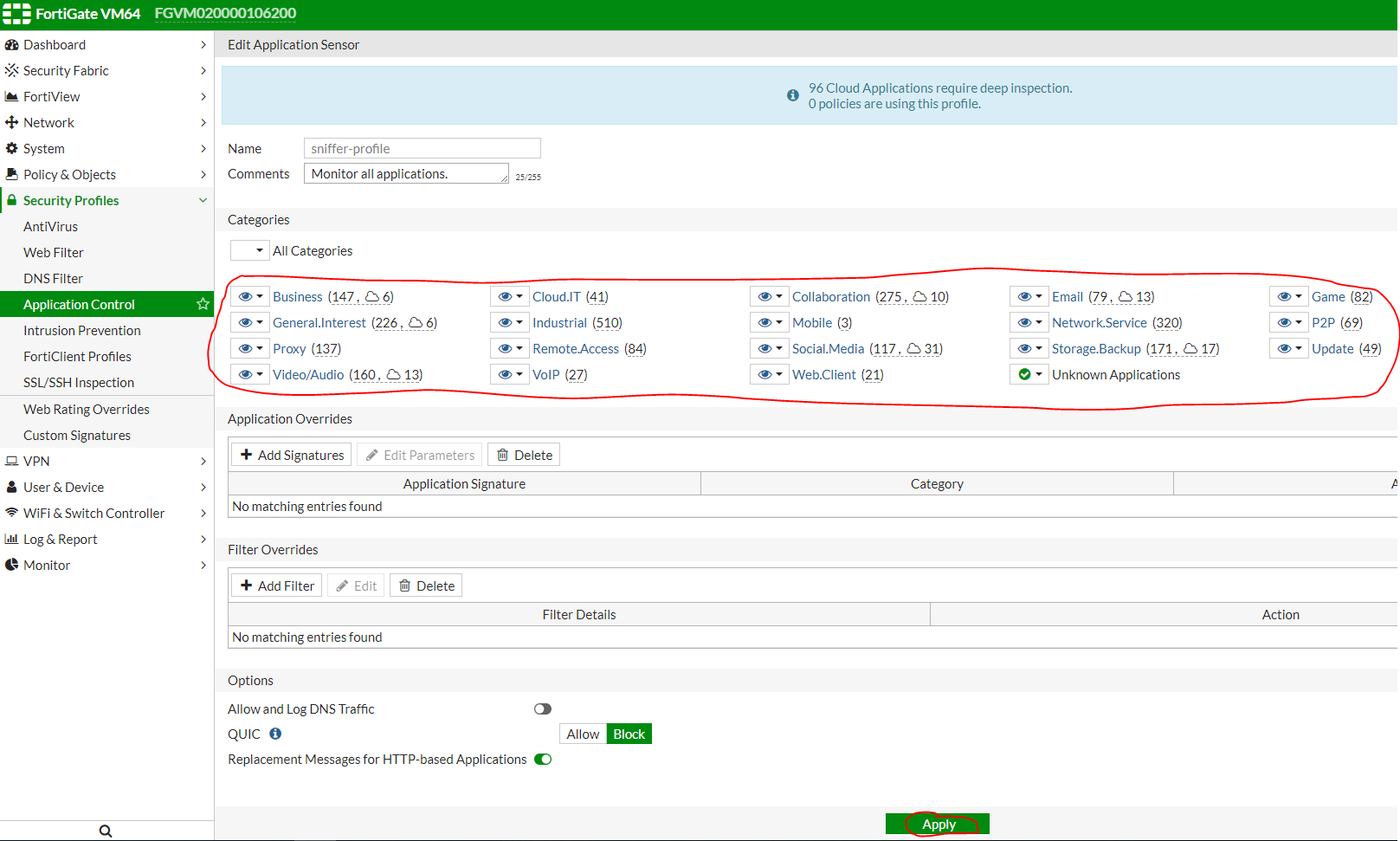
IPS settings ( Edit Sniffer Profile ):

As you can see, the profile includes signatures with the importance level Critical and High by default. You need to add Medium :

Also for this profile as an action you need to install the Monitor :

Do not forget to save the settings by clicking Apply .
This completes the configuration of the One-Arm Sniffer and then you need to configure the integration with FortiAnalyzer.
To integrate with FortiAnalyzer, you need to properly configure logging. Go to Log Settings :
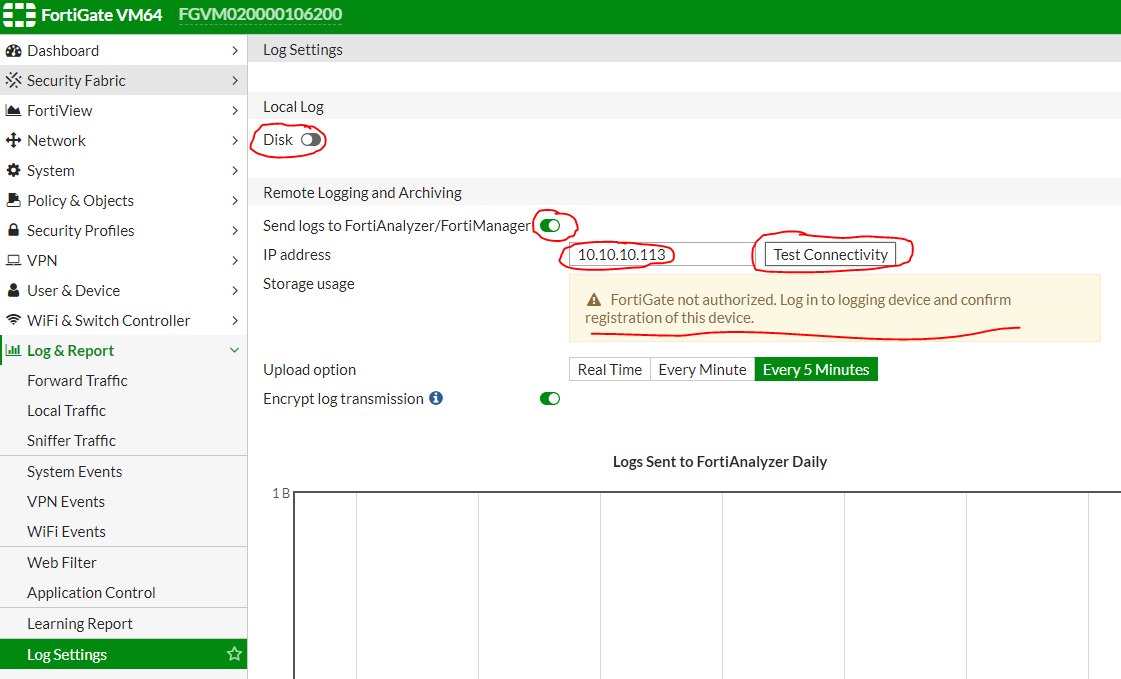
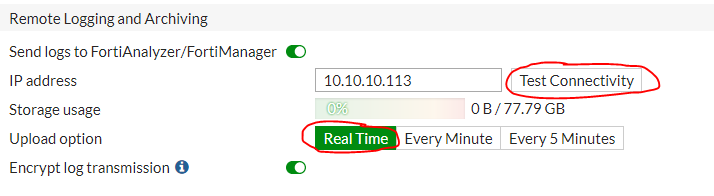
Logging to Disk can be turned off and specify the ip-address of our FortiAnalyzer, as in the figure above. Clicking on Test Connectivity we will see that the device needs to be registered on FortiAnalyzer. Click Apply and go to the FortiAnalyzer settings in the Device Manager section:
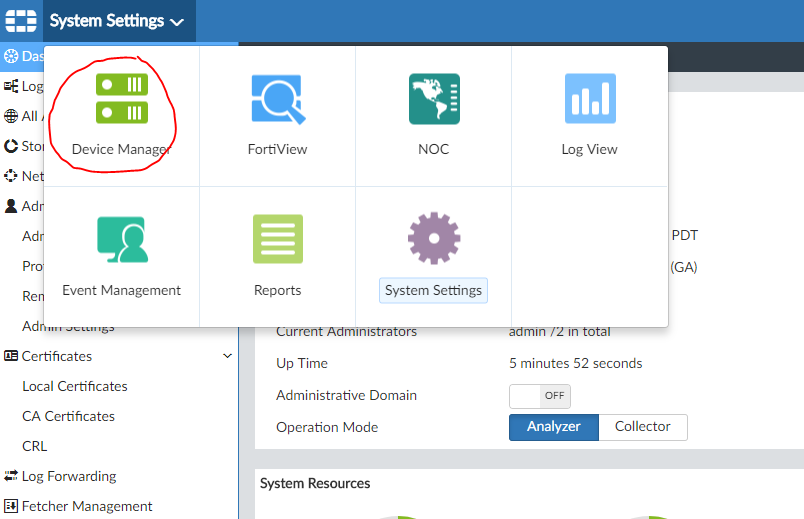
Go to the section Unregistered :
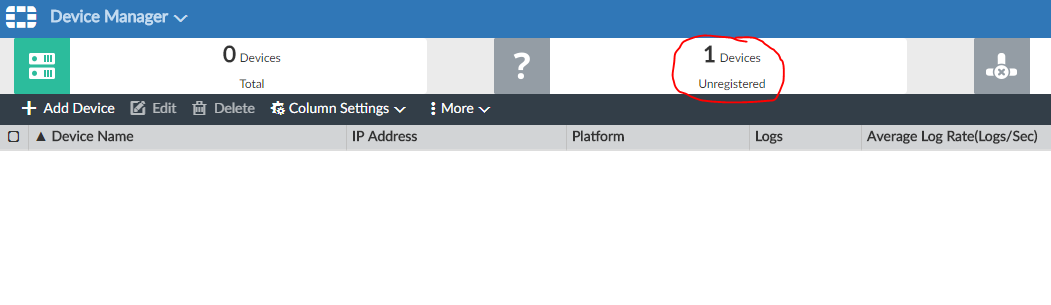
Here we will see our FortiGate. Select it and click Add :
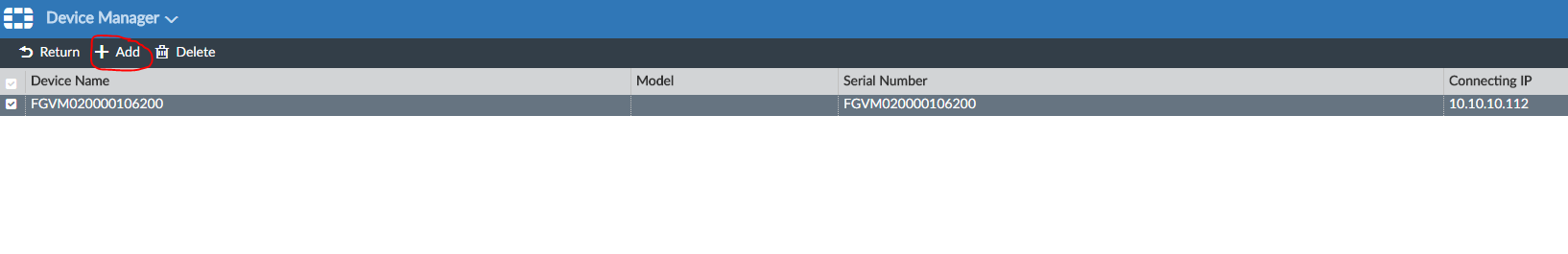
Click OK :
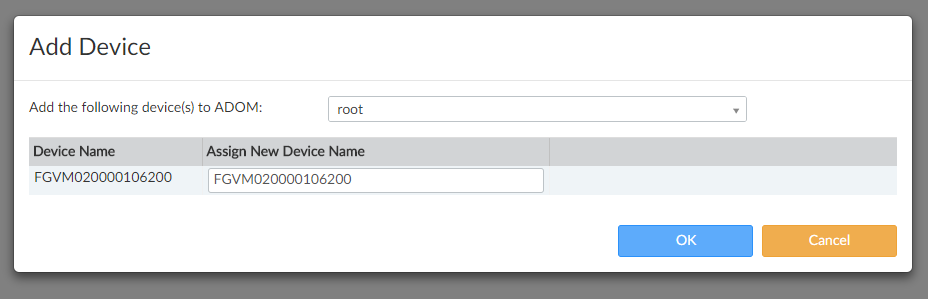
From this point on, FortiGate is registered:
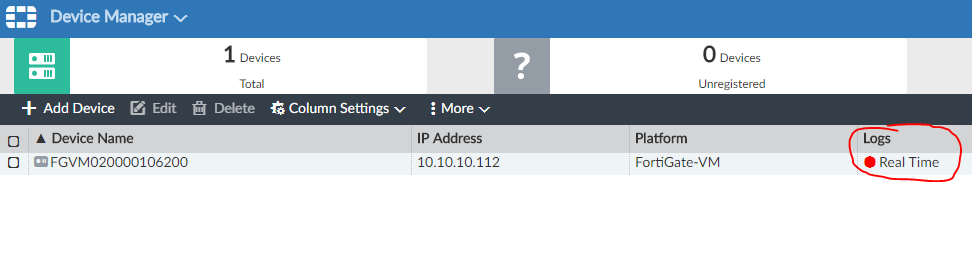
We return to the FortiGate settings in Log Settings . Check the Test Connectivity again and set the Upload option to Real Time :
For Event Logging, we set All , and in the Display Logs field, set FortiAnalyzer :
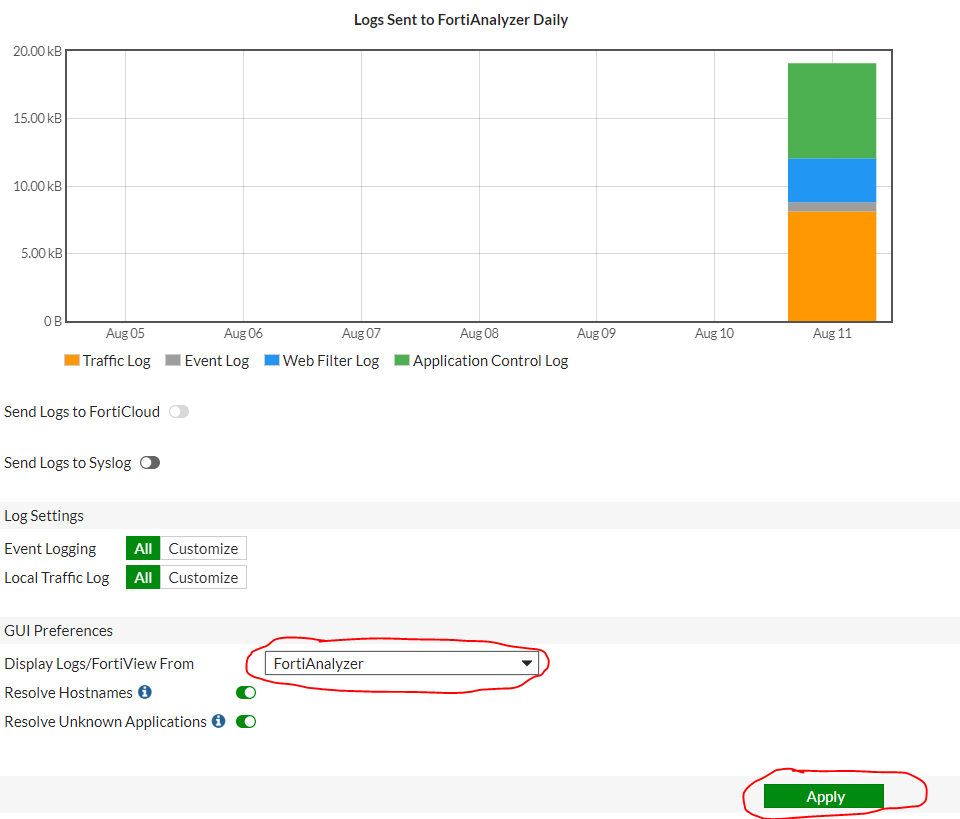
Do not forget to apply the setting ( Apply ). But this setting FortiGate and FortiAnalyzer is fully completed.
Before generating the report, you need to make sure that the logs actually come to FortiAnalyzer. To do this, go to the Log View :
You should see the FortiGate logs:
Logs come. Now for the collection of statistics it takes a long time ( preferably 2-4 weeks ). However, you can generate reports at any time. To do this, go to the Reports section:
A large number of reports are available here, but we are interested in Cyber Threat Assessment . Select it and click Run Report :

The finished report will be found in the Generated Reports section:
Before generating the report, it is recommended to wait at least one hour in order to gain at least some statistics. An example of the report can be found here .
Although the procedure is simple (it takes a maximum of 30 minutes of time) there are quite a few pictures. Perhaps somewhere not entirely obvious are our actions. That is why in the near future we will publish small video tutorials , where, step by step, we will go through the whole setup procedure.
As we already wrote in the first part , this audit is a good opportunity to analyze the current state of its network. The reports are very detailed and informative. And given the simplicity of the whole process, everyone can do it.
More information on Fortinet can be found here .
If you are interested in such a “pilot” project, you can feel free to contact us for licenses and images or simply for help with Fortinet products. Thank.
PS I would like to thank Yuri Zakharov (Fortinet system engineer) for help in preparing this article.

Those. on the existing virtualization server, two virtual machines are “raised”. In our case, we will use ESXi, but there is support for Hyper-V and KVM. FortiGate VM with one adapter is connected to a common network (vSwitch0). This link will be used to manage and access the Internet. The second interface connects to another vSwitch1, which in turn is connected to the server’s free physical port (eth2). It is on this port that the traffic should be mirrored for analysis. Note that Promiscuous mode (Accept) must be enabled for the vSwitch1 switch. More details can be found here .
Nearby, FortiAnalyzer is also installed, which is sufficient to connect only one interface to your network (vSwitch0).
')
Import Images
As you understand, the first thing you need to import images. They are delivered in the form of ovf, so no problems should arise.
Import FortiGate VM:

Now you need to select a file. There are several of them in the archive, but we just need FortiGate-VM64.ovf :

Further, when configuring the interfaces, you need to select the VM Network for the first adapter (which corresponds to the network management - vSwitch0), and for the second - the VM Network 2 (which corresponds to the SPAN port - vSwitch1). The rest of the ports can be left by default:

By default, 1 GB of RAM and 1 core are set in the virtual machine properties. Do not try to change these parameters, otherwise the trial license is not activated and you will not be able to connect to this device. We'll fix it later.
The FortiAnalyzer virtual machine is imported in the same way. You must select the FortiAnalyzer-VM64.ovf file :

When setting up a network, it is enough to enable the first interface in the VM Network (i.e. network management):

This virtual machine has 4GB of RAM and 2 cores by default. As a rule, these parameters are always enough.
Startup and initial setup
After successful import of images, you can start both "machines". First of all, we need to configure the ip-address and default route so that you can connect to the devices already through the web-interface.
The login is admin, and the password is empty (just press enter):

The ip address setting is performed using the following commands:
config system interface
edit port1 //
set ip 10.10.10.112/24 //IP
endSetting the default gateway:
config router static
edit 1 //
set gateway 10.10.10.254
set device port1
end
To check the settings, you can use the following commands:
show system interface (output port settings)
show router static (display of router settings)
Settings for FortiAnalyzer are similar:
config system interface
edit port1 //
set ip 10.10.10.113/24 //IP
endThe configuration of the gateway is slightly different:
config system route
edit 1 //
set gateway 10.10.10.254
set device port1
endAfter configuring the interfaces, it is very important to check that the Internet is available on the devices, otherwise the licenses are not activated. To verify, use the execute ping command.

Connect and activate licenses
After configuration, we can connect via the web-interface and activate the licenses that your partner should provide. Let's start with FortiAnalyzer:
Login admin and empty password. After logging in, the start page will open:
We are interested in System Settings:
In the upper right corner we will see the license information. Currently the trial version is active, but we will add a new one by clicking on the Upload License. After that, the device will reboot with a new license.
FortiGate is a similar procedure. When connecting, please note that the http version of the portal will open, and if you try to connect via https, the browser will generate an error ERR_SSL_VERSION_OR_CIPHER_MISMATCH. This is a normal situation due to the trial mode. After the license is activated, we will be able to connect via HTTPS. The login window looks like this:

Login - admin , password - empty. After logging in we will see the FortiGate main page:

You need to activate the license by clicking on FGVMEV License and then throw a new one:

After that, the license activation process will begin, which may take some time:

After activation, the gateway will reboot. Now for a virtual machine, you can set 2 cores and 4 GB of RAM (depending on the license that you generated). As a result, you should see something like the following:
Please note that IPS, Anti-Virus, Web-filtering services may not be activated immediately, but after a while.
Configure One-Arm Sniffer
Now you can proceed directly to setting up a One-Arm Sniffer. To do this, open the interface settings:
We are interested in port2 , because it is he who is connected to the SPAN port. Double click on its properties and set the settings as in the picture below:
It is important to remember to click OK to apply the settings. After that, you need to go into the port2 settings again , and in turn open the settings of the AntiVirus, Web Filter, Application Control and IPS profiles.
Let's start with AntiVirus ( Edit Sniffer Profile ). The settings should look like this:
Do not forget to click Apply . Web Filter Settings ( Edit Sniffer Profile ):
Settings Application Control ( Edit Sniffer Profile ):
IPS settings ( Edit Sniffer Profile ):

As you can see, the profile includes signatures with the importance level Critical and High by default. You need to add Medium :

Also for this profile as an action you need to install the Monitor :

Do not forget to save the settings by clicking Apply .
This completes the configuration of the One-Arm Sniffer and then you need to configure the integration with FortiAnalyzer.
Integration with FortiAnalyzer
To integrate with FortiAnalyzer, you need to properly configure logging. Go to Log Settings :
Logging to Disk can be turned off and specify the ip-address of our FortiAnalyzer, as in the figure above. Clicking on Test Connectivity we will see that the device needs to be registered on FortiAnalyzer. Click Apply and go to the FortiAnalyzer settings in the Device Manager section:
Go to the section Unregistered :
Here we will see our FortiGate. Select it and click Add :
Click OK :
From this point on, FortiGate is registered:
We return to the FortiGate settings in Log Settings . Check the Test Connectivity again and set the Upload option to Real Time :
For Event Logging, we set All , and in the Display Logs field, set FortiAnalyzer :
Do not forget to apply the setting ( Apply ). But this setting FortiGate and FortiAnalyzer is fully completed.
Report generation
Before generating the report, you need to make sure that the logs actually come to FortiAnalyzer. To do this, go to the Log View :
You should see the FortiGate logs:
Logs come. Now for the collection of statistics it takes a long time ( preferably 2-4 weeks ). However, you can generate reports at any time. To do this, go to the Reports section:
A large number of reports are available here, but we are interested in Cyber Threat Assessment . Select it and click Run Report :
The finished report will be found in the Generated Reports section:
Before generating the report, it is recommended to wait at least one hour in order to gain at least some statistics. An example of the report can be found here .
Conclusion
Although the procedure is simple (it takes a maximum of 30 minutes of time) there are quite a few pictures. Perhaps somewhere not entirely obvious are our actions. That is why in the near future we will publish small video tutorials , where, step by step, we will go through the whole setup procedure.
As we already wrote in the first part , this audit is a good opportunity to analyze the current state of its network. The reports are very detailed and informative. And given the simplicity of the whole process, everyone can do it.
More information on Fortinet can be found here .
If you are interested in such a “pilot” project, you can feel free to contact us for licenses and images or simply for help with Fortinet products. Thank.
PS I would like to thank Yuri Zakharov (Fortinet system engineer) for help in preparing this article.
Source: https://habr.com/ru/post/335402/
All Articles