Sites online stores and industrial companies are most vulnerable to hacker attacks
More than half of modern websites contain critically dangerous vulnerabilities that allow attackers to conduct various attacks, including denial of service and theft of personal data. Such conclusions are contained in the study of Positive Technologies based on the work on the analysis of the security of web applications for 2016.
As follows from the report, almost all of the studied web applications (94%) allow attacks on users, and it is not surprising - half of the vulnerabilities that are among the ten most common are used for such attacks. Access to personal data was obtained in 20% of applications processing such data (including the websites of banks and government organizations).
')
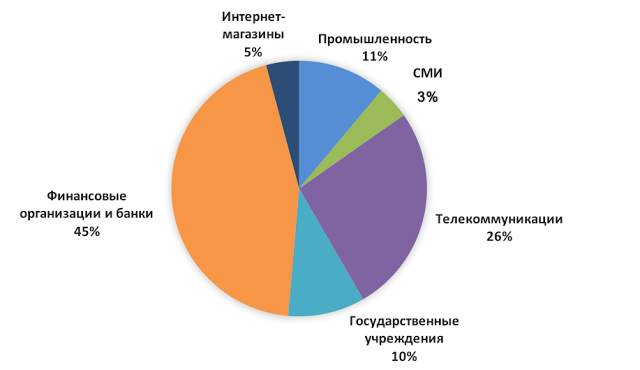
Most web applications with high-risk vulnerabilities were found among telecommunication company sites (74%). If we assess the level of security depending on the possible consequences, then the worst situation is in the industry (43% of sites have an extremely low degree of security) and in e-commerce (34%).
The researchers note that the vulnerabilities of public sites are still a popular way to penetrate the company's internal infrastructure: every fourth web application allows for such attacks. In addition, a quarter of web applications contain vulnerabilities that allow an outside attacker to gain access to databases.
Another important observation is that web applications that are in the process of operation turned out to be more vulnerable than test ones: critical vulnerabilities were detected in 55% of productive systems and in 50% of test systems. This indicates that it is necessary to carry out a security analysis not only during the development process, but also after its commissioning. To protect applications that are already in use, it is recommended to use web application firewalls.
The study also presents a comparison of the effectiveness of various methods of analyzing application security (the white box versus the black box) and provides examples of the detection of vulnerabilities by the automated PT Application Inspector code analyzer. Analysis of the source code shows much higher results than security research without access to the application code. In addition, testing the source code in the development process can significantly improve the security of the final application. For analyzing the source code at various stages of development, it is advisable to use automated tools, since this allows you to identify the maximum number of errors in the shortest possible time.
Full version of the study: blog.ptsecurity.ru/2017/08/web-attacks.html
Source: https://habr.com/ru/post/335186/
All Articles