"Tips for engineers": a review of Huawei S5720-52X-PWR-SI V2R9SPC500

Hi, Habr! Huawei blog is back in touch!
In the air the next issue of the heading "Tips for engineers".
And today our guest is the honored switch of China, the holder of the honorary title “Worthy Replacement of the Cisco 2960S-24-PWR Model”, the leader of the Huawei line in the “functional / price” ratio - the Huawei S5720-52X-PWR-SI switch V2R9SPC500.
')
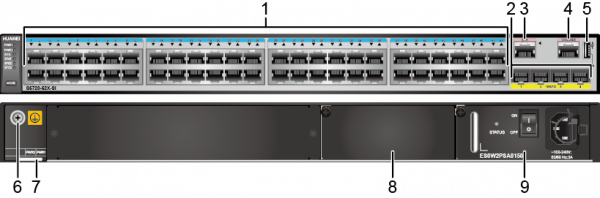
Short dossier on our hero:
48GE PoE +, 4 * 10GE ports.
SI version supports L3 routing, including RIP and OSPF.
Software version V200R009C00SPC500.
Power supply 500W, for PoE 370 is available.
Stacking is possible through 1 / 10GE Uplinks.
The 10GE interfaces support almost any transceiver, including SNR.
It supports web-based management and CLI (telnet, ssh v2), SNMP v2c / v3, centralized via eSight.
And today we will talk about our experience of using the S5720 as an access switch for connecting workstations and IP phones.
Initially, we laid a certain redundancy, because For this task, a cheaper S5700-LI switch line is sufficient, but with an eye to future use, this model was taken, and this was justified - by the end of testing, routing was suddenly needed.
But, let's get to the point - what did you manage to find out about the S5720 and test it in practice?
First experience. VLAN
Created VLAN for office network and for phones. Configured "trunks" and user ports. LLDP enabled.
For Voice VLAN operation, ports are configured in the hybrid mode. Yealink IP phones have the ability to receive settings via LLDP, which we successfully used.
After configuration, user traffic remained in the office network, and voice traffic moved to the Voice VLAN. At the same time, additional configuration of telephones and jobs was not required, which is very convenient during migration.
The inclusion of LLDP allows you to allocate PoE in accordance with the requirements of the connected device and economically consumes the power budget of the switch.
There were no questions when setting up routing - everything works. Basic routing settings:
router id 192.168.30.4
#
ospf 1
area 0.0.0.0
network 10.0.50.0 0.0.0.255
#
interface Vlanif50
mtu 9198
ospf timer hello 1
ospf timer dead 3Peer authentication was not verified. In order to accelerate convergence, non-standard timings were set up (the so-called “LAN-based design”). ASA5512 is successfully used as a “neighbor” - it works.
Not without nuances: despite the fact that the SI series supports dynamic routing, it is possible only between Vlan interfaces (Vlanif). Those. the port cannot be switched to L3 mode and assign it an IP address. This is only possible for the EI, HI series.
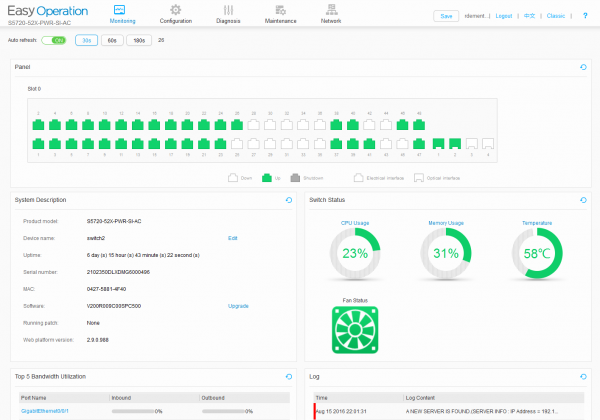
Experience the second. Security
As a protection against the most common types of threats, we configured DHCP snooping, IP Source Guard, ARP security - all together, this avoids some types of attacks that are most common in the office network, including unintended ones.
It is no secret that for administrators it becomes a headache that an illegal DHCP server appears on the network. DHCP snooping is designed to solve this problem because distribution of addresses in this case is possible only from a trusted port, on the rest it is blocked.
On the basis of DHCP snooping, IP Source Guard and ARP security functions that protect against IP and MAC falsification. Here the essence is that work is possible only with the address obtained by DHCP, and the link “port — IP — MAC” is created and checked automatically.
This setting will save us if someone wants to use someone else's IP-MAC, or to organize an attack such as MITM-attack ("Man-in-the-Middle").
The third type of possible threat is an attack on STP. Here, BPDU filtering is enabled as protection on user ports (that is, no STP frames are sent to the user or accepted from it).
In addition, control of the appearance of extraneous BPDU stp bpdu-protection is carried out, which is possible when another switch is connected or an attack on stp root is launched.
The activated “stp edge-port enable” option excludes the port from STP calculation, reducing convergence time and load on the switch.
The combination of stp bpdu-protection and stp edge-port enable, is similar to Cisco spanning-tree portfast.
Actually, configuration examples:
dhcp enable
#
dhcp snooping enable
dhcp snooping alarm dhcp-rate enable
dhcp snooping user-bind autosave flash:/dhcp-bind.tbl write-delay 6000
arp dhcp-snooping-detect enable
dhcp server detect
vlan 2
name office
dhcp snooping enable
dhcp snooping check dhcp-request enable
dhcp snooping check dhcp-rate enable
arp anti-attack check user-bind enable
ip source check user-bind enable
vlan 3
name guest
dhcp snooping enable
dhcp snooping check dhcp-request enable
dhcp snooping check dhcp-rate enable
arp anti-attack check user-bind enable
ip source check user-bind enable
vlan 4
name voice
dhcp snooping enable
dhcp snooping check dhcp-request enable
dhcp snooping check dhcp-rate enable
arp anti-attack check user-bind enable
ip source check user-bind enable
interface GigabitEthernet0/0/1
port link-type hybrid
voice-vlan 4 enable
port hybrid pvid vlan 2
port hybrid tagged vlan 4
port hybrid untagged vlan 2
stp root-protection
stp bpdu-filter enable
stp edged-port enable
trust dscp
stp instance 0 root primary
stp bpdu-protectionExperience the third. Administration
You have configured the administrative part, which includes NTP, SNMP, AAA, Radius.
It turned out that you can activate up to 16 lines of VTY, while the default is only 5.
And, in fact, some convenience of administration.
user-interface maximum-vty 15
user-interface con 0
authentication-mode aaa
history-command max-size 20
screen-length 40
user-interface vty 0 14
authentication-mode aaa
history-command max-size 20
idle-timeout 30 0
screen-length 40What is important to note more?
For SSH access, it is necessary to add SSH users, except for the user in the AAA section.
RSA keys have already been generated, but if you change the name and domain on the switch, we recommend that you generate the keys again.
By default, ssh v1 is disabled, but you can enable it if necessary (although we do not recommend doing this).
stelnet server enable
[HUAWEI] aaa
[HUAWEI-aaa] local-user admin123 password irreversible-cipher Huawei@123
[HUAWEI-aaa] local-user admin123 service-type ssh
[HUAWEI-aaa] local-user admin123 privilege level 15
[HUAWEI-aaa] quit
[HUAWEI] ssh user admin123 authentication-type passwordWe also managed to set up authentication of administrators through Radius.
It should be noted that for administrators use a scheme called domain default_admin!
domain default_admin
authentication-scheme default
accounting-scheme Radius
service-scheme Admin
radius-server RadiusExperience the fourth. Replacing the device certificate with a valid one
"To the heap" we decided to replace the factory self-signed certificate with a valid one (the benefit is our valid certificate for signing).
The certificate can be imported only from the CLI.
Faced with the fact that the keys and the certificate must be separate, despite the fact that the "pfx" format allows you to export the private key as part of the certificate.
Moreover, if you are trying to import a chain of certificates, then the device certificate must be recorded first, and then all the others (for example, intermediate CAs).
With standard export to pem, first in the file are CA certificates and only at the end the device certificate.
For the import to work, the certificate files on the device must be placed in the security folder on the flash. This default folder is missing it needs to be created.
We present to your attention a step-by-step algorithm:
1. Generate a certificate on an external CA.
2. Export a separate certificate or chain and private key.
3. If this is a chain, open the certificate file with a notepad and transfer the last block (device certificate) to the beginning of the file, save.
4. On the switch, create a folder mkdir flash: / security
5. Put the certificate file and the tftp 192.168.0.1 key in the folder. Chain-servercert.pem /security/chain-servercert.pem
After that, according to the instructions, create a policy and perform the import.
system view
[HUAWEI] ssl policy http_server
[HUAWEI-ssl-policy-http_server] certificate load pfx-cert servercert.pfx key-pair rsa key-file serverkey.pfx auth-code cipher 123456
# Load a PEM certificate chain for the SSL policy.
system view
[HUAWEI] ssl policy http_server
[HUAWEI-ssl-policy-http_server] certificate load pem-chain chain-servercert.pem key-pair rsa key-file chain-servercertkey.pem auth-code cipher 123456
To apply the policy, you must restart the https server, but it will not restart separately. Therefore, it is necessary to restart the entire web service.
http server disable
http server enable
As a result, the export was successful, and the web-interface uses a valid certificate.
Summing up
As a result - a few figures and conclusions:
- The switch CPU load even at idle is about 20%, and in periods increases to 30%. Effects on traffic not seen.
CPU utilization for five seconds: 25%: one minute: 25%: five minutes: 24%
TaskName CPU Runtime (CPU Tick High / Tick Low) Task Explanation
VIDL 75% 2 / 187119ff DOPRA IDLE
OS 12% 0 / 55d4a7fe Operation System
POE 4% 0 / 204e4380 POE Power Over Ethernet
- When migrating virtual machines between connected ESX, the load on the interface was 804 Mbit / s and 999 Mbit / s, without packet loss.
Input peak rate 804556024 bits / sec, Record time: 2016-08-15 15:09:17
Output peak rate 999957528 bits / sec, Record time: 2016-08-12 12:20:09
- One of the phones refused to connect at a speed of 1000 Mbit / s, only at 100 Mbit / s. AUTO settings on both sides. Direct connection to the switch 1m patch cord, switch port change did not help. At the same time, the Cisco 2960 phone was connected to 1G stably. This is one of 20 similar phones. The issue has not been resolved.
- Very modest web interface, the most basic functions are available.
PS See you in the next issues, gentlemen, Engineers!
Source: https://habr.com/ru/post/334910/
All Articles